Working-Dog.com Data Leak Exposes 4 Billion Records in Unsecured Server: Full Report

➤Summary
The Working-Dog.com data leak has sent shockwaves through both the dog-breeding community and the cybersecurity world 🐾. In a startling discovery, the Kaduu cybersecurity team uncovered an unsecured server exposure tied to Working-Dog.com, a popular global platform for breeders, trainers, and animal enthusiasts. The exposed database—indexed on Shodan—contained over 4.18 billion documents and more than 493 GB of unprotected data, including user information, animal records, and payment details.
Discovered during a routine dark web and deep web monitoring operation, Kaduu analysts found the server accessible to anyone online—no password, no firewall, and no encryption. The server, located at IP address 5.75.210.229, exposed years of sensitive records, sparking urgent discussions on data privacy, cyber hygiene, and the critical role of dark web intelligence platforms like DarknetSearch.com in modern cybersecurity defense.
The Discovery by the Kaduu Team 🔍
Kaduu’s discovery of the Working-Dog.com unsecured server leak came during an ongoing monitoring campaign targeting misconfigured cloud databases. While reviewing Shodan results, analysts identified a publicly exposed Elasticsearch cluster belonging to the platform. Upon safe verification, the team found multiple indices, each storing millions of detailed records.
These datasets included:
- Users — containing personal details, contact info, and account metadata
- Payments — recording payment modes, dates, and linked user IDs
- Animal Records — storing breeder, ownership, and pedigree information
Total Size: 493.21 GB
Total Documents: 4,180,195,013
The server was fully open, indexed on Shodan, and accessible through a standard browser—an alarming lapse in security for a platform handling personal and financial data.
What Data Was Compromised 💾
The Working-Dog.com data leak involved three major indices, revealing just how much data the platform stored about its global user base. Kaduu researchers analyzed the structure and confirmed multiple categories of personal and transactional information.
- User Records
Fields identified included:
- id, created, updated
- firstname, lastname, gender, birthday
- address (zip, street, city, country_code_iso)
- email, role_name, state_name
- profile_visits, contact_count, results_count
🖼️ [Image 2: Users index structure example]
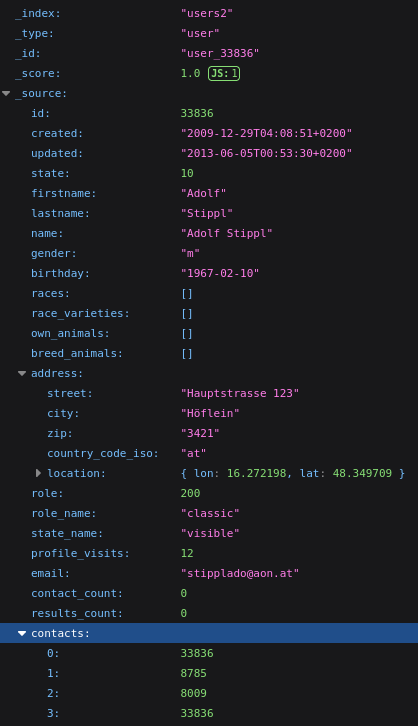
This dataset exposed personal identities, geographic details, and communication statistics—potentially linking breeders, owners, and competitors worldwide.
- Payment Information
Fields included:
- id, pay_date, amount_int, amount_float
- months, pay_type_string, pay_mode_string
- Linked user.id
🖼️ [Payment Information image]
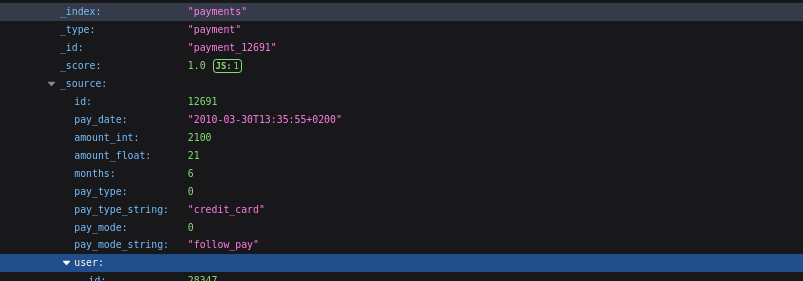
Although no full credit card numbers were seen, transaction metadata still presents high risks of phishing, fraud, or financial profiling.
- Animal Data
Fields included:
- id, name, sex, birthdate, weight
- breeders, owners, contact_info
- federation, healthresults, certificationresults
🖼️ [Animal records sample images]
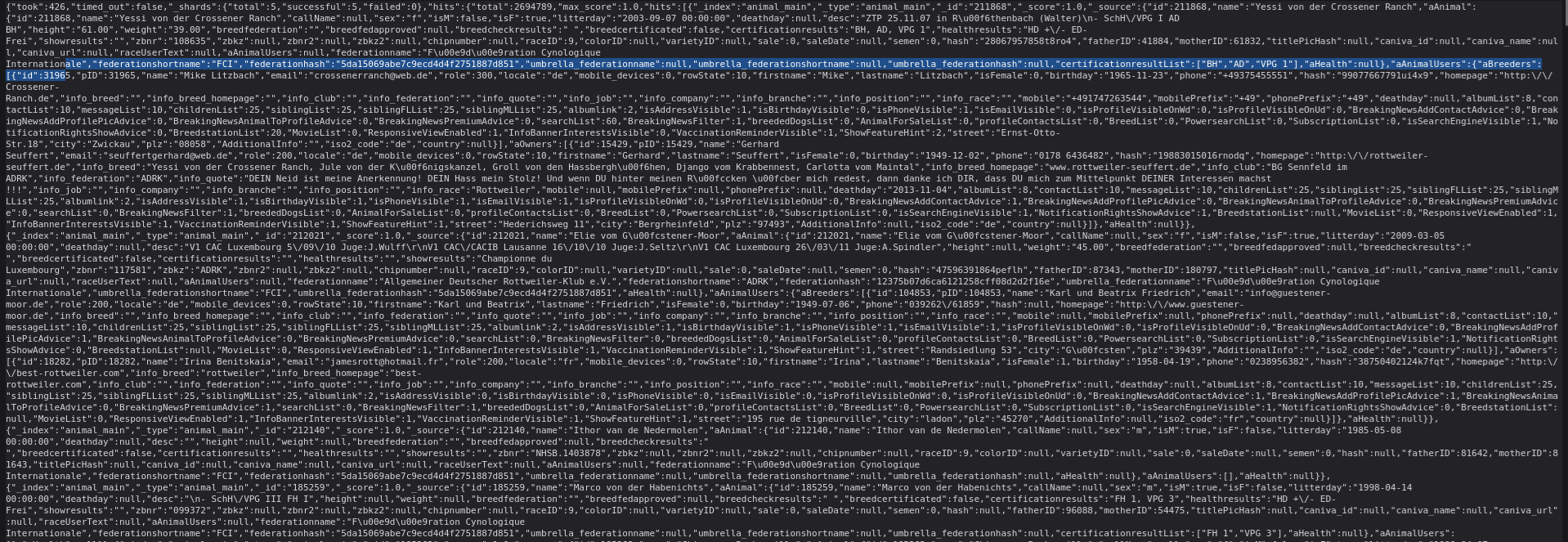
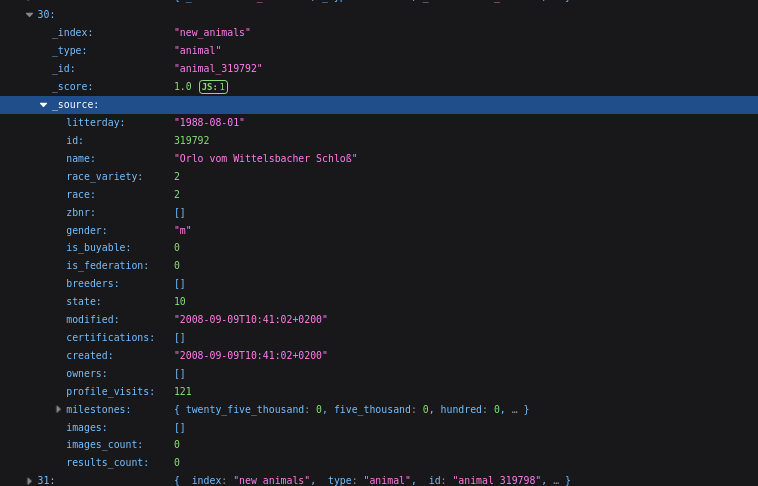
These records exposed breeder details, emails, phone numbers, and addresses, linking people directly to animals and kennel operations.
The Scale of the Exposure 📊
This unsecured server exposure ranks among the largest publicly discovered in 2025. The dataset spanned over 15 years, containing entries from 2009 through 2024, indicating long-term archival data left unprotected.
Experts confirmed that the server ran an Elasticsearch instance with no authentication layer, making it directly visible to the internet and indexed by Shodan. Any user who knew the IP could browse the data freely.
Such a setup suggests either misconfigured backup storage or abandoned infrastructure, highlighting the risks of poor lifecycle management in cloud environments.
Expert Insight 🧩
According to Dr. Lena Hoffmann, cybersecurity researcher and author of Data Exposure by Default, “Open Elasticsearch clusters remain one of the biggest causes of major data breaches today. The Working-Dog.com case is yet another reminder that configuration mistakes can have devastating consequences.”
Kaduu spokesperson Andrej Kovač emphasized, “The most concerning aspect is the exposure of breeder and owner personal details. Unlike passwords, you can’t change your home address or date of birth once it’s leaked.”
Risk and Impact 🧨
The Working-Dog.com unsecured server leak discovered by Kaduu potentially impacts:
- Dog breeders, owners, and kennel managers
- Registered platform members and event participants
- Users with payment or membership history
Key risks include:
- Identity Theft: Exposed names, birthdays, and locations can be cross-referenced in fraud schemes.
- Phishing & Social Engineering: Attackers may impersonate Working-Dog.com support to steal credentials.
- Targeted Scams: High-value breeders could be tricked into fake sales or “premium listing” scams.
- Reputational Damage: Public exposure of breeder and kennel data undermines professional credibility.
The breach illustrates how unsecured cloud infrastructure can endanger not only data but also entire online communities built on trust and transparency.
Practical Tip 💡
If you have ever used Working-Dog.com, take immediate action:
✅ Change your password and avoid reusing it on other sites.
✅ Be cautious of emails claiming to be from Working-Dog.com.
✅ Use two-factor authentication wherever possible.
✅ Monitor your digital footprint for any signs of exposure.
✅ Consider using dark web scanning tools for early alerts.
Why DarknetSearch.com Is Crucial for Dark Web Monitoring 🌐
In modern cybersecurity, cyber threat intelligence is not optional — it’s essential 🛡️. As the Working-Dog.com data leak proves, once data is exposed, it can appear on darknet marketplaces or hacking forums within hours.
That’s where DarknetSearch.com becomes indispensable. It’s not just a dark web search tool—it’s a specialized intelligence platform that continuously scans deep web, darknet, and breach databases to identify leaked credentials, stolen records, or personal data.
Unlike traditional search engines, DarknetSearch.com focuses exclusively on hidden networks like Tor and I2P, where stolen information often surfaces first. By tracking these environments, it helps organizations detect threats before attackers exploit them 🚨.
Real-Time Threat Detection
DarknetSearch.com monitors underground sources in real time. When new data matching your email, domain, or organization appears, it instantly alerts you. This early detection allows for proactive mitigation, stopping breaches before they spread.
Identity & Brand Protection
For companies like Working-Dog.com, brand reputation is everything. DarknetSearch.com provides brand intelligence and visibility into leaked data connected to a business, helping protect both the platform and its users from impersonation or fraud attempts.
Compliance & Legal Readiness ⚖️
Under frameworks like GDPR and NIS2, ongoing monitoring of leaked data is part of due diligence. Tools like DarknetSearch.com demonstrate that organizations are actively protecting user data—a vital factor in reducing penalties after incidents.
Early Warning Against Data Misuse
Once stolen, data rarely stays in one place. DarknetSearch.com tracks reused credentials and cloned entries, ensuring security teams know if compromised data resurfaces on other platforms.
In short, DarknetSearch.com gives you eyes where attackers operate. It transforms dark web chaos into actionable intelligence—a critical capability in today’s threat landscape.
Why Dark Web Monitoring Is Non-Negotiable 🚫
Many businesses wrongly assume they’re “too small to be targeted.” In reality, automated scanning tools identify unsecured databases like Working-Dog.com’s within hours.
Even non-financial data—like email addresses or location metadata—can lead to:
- Credential stuffing attacks
- Phishing and scam campaigns
- Blackmail attempts
- Identity correlation across platforms
Without dark web visibility, organizations are blind to active risks. Platforms like DarknetSearch.com turn that blind spot into clarity, providing actionable data to protect users and brands before the fallout.
Cybersecurity strategist Elena Dobrev summarizes it perfectly:
“Ignoring dark web monitoring is like locking your front door but leaving the back wide open. You need to know what’s happening in the shadows.”
Could the Leak Have Been Prevented? 🔐
Yes — easily. This breach resulted from basic security oversights. To prevent similar incidents:
- Enable authentication for all Elasticsearch servers.
- Restrict IP access using firewall rules.
- Disable public indexing in Shodan.
- Regularly audit exposed endpoints.
- Monitor cloud assets continuously.
Had these been implemented, the Working-Dog.com data leak might never have occurred.
Company Response
As of publication, Working-Dog.com has not issued an official statement. Under GDPR, organizations must notify users and regulators of significant breaches. The absence of public acknowledgment may raise questions about incident response and transparency obligations.
Community Reaction 🐕🦺
Users expressed frustration on forums and social media, calling the exposure “irresponsible” and “unacceptable.” Some breeders reported receiving phishing emails related to dog sales or event registrations shortly after the incident—suggesting that attackers may already be weaponizing leaked data.
Final Analysis & Takeaway 💬
The Working-Dog.com unsecured server leak discovered by Kaduu stands as a wake-up call for every organization managing sensitive information online. Misconfigured databases are not harmless—they are open invitations for exploitation.
At the same time, tools like DarknetSearch.com prove why brand protection dark web monitoring is no longer optional. With stolen data instantly circulating across hidden networks, having visibility into the dark web is now a baseline requirement for digital safety.
💡 Dark web intelligence is the new firewall. Without it, even the most secure systems can’t detect post-breach exposure.
Conclusion ✳️
The Working-Dog.com data leak underscores the urgent need for stronger data governance, responsible disclosure, and constant vigilance. From unprotected databases to overlooked backups, small missteps can lead to global consequences.
Every company—large or small—must integrate dark web monitoring, secure configuration, and continuous risk assessment into their cybersecurity frameworks.
Protect your data. Stay informed. Act fast.
👉 Discover much more in our complete guide at DarknetSearch.com
👉 Request a demo NOW.
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


