ArtistsAndClients Data Breach: 2025 Dark Web Leak Revealed by Kaduu Team

➤Summary
The Artists&Clients data breach has raised new concerns across the creative freelance community after a massive database containing sensitive user information surfaced on dark web forums in late August 2025. The breach, reportedly discovered by the Kaduu Cyber Threat Intelligence Team during routine monitoring, was shared on the underground forum Breachsta.rs around September 1, 2025. Early analysis suggests that thousands of artists and commissioners may have been affected, with personal data and account credentials now circulating online 😟.
This Artists&Clients data breach is yet another reminder that digital creative platforms—though often small in scale—remain high-value targets for cybercriminals.
How the Artists&Clients Data Breach Was Discovered
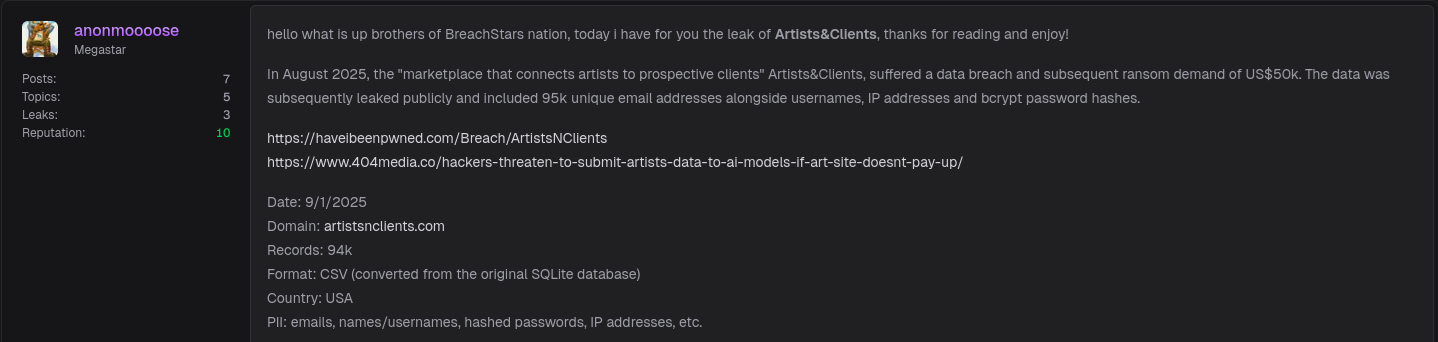
According to researchers, the Artists&Clients database leak August 2025 came to light during automated scanning of dark web and deep web sources. The dark web leak was traced to a post shared on Breachsta.rs, a known marketplace for stolen databases. The post included sample files and database metadata hinting at thousands of user profiles.
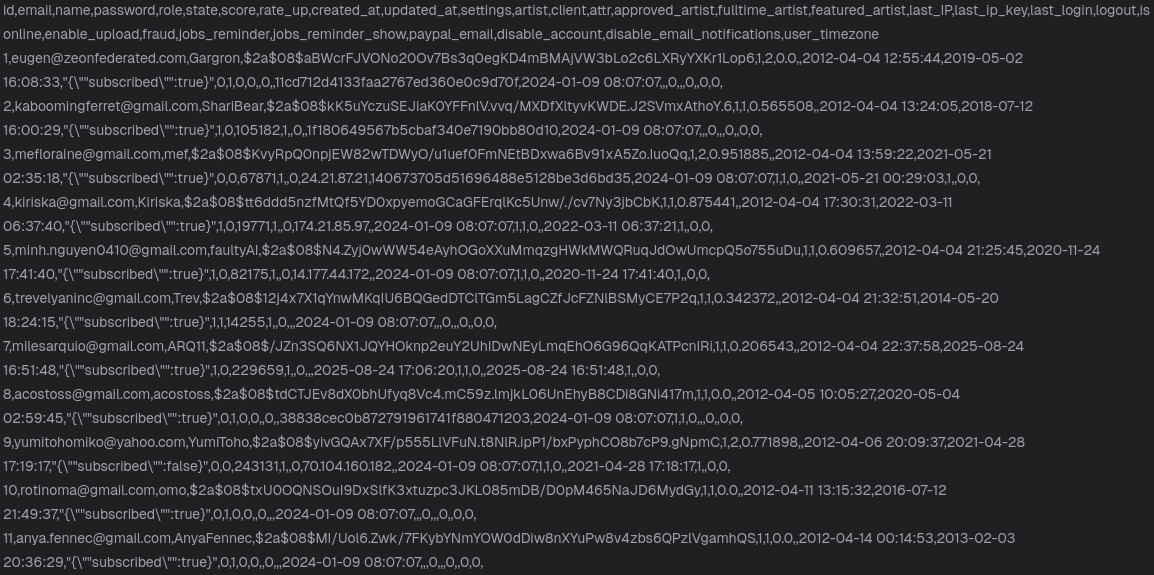
Security analysts confirmed that the leaked data matched the structure of Artists&Clients’ production systems. The compromised information included usernames, email addresses, password hashes (bcrypt and SHA-1), registration timestamps, and optional user details such as country or commission preferences.
🔍 Quote from Kaduu spokesperson:
“Our team found a dataset referencing Artists&Clients while monitoring Breachsta.rs. The leak appears genuine and includes over 100,000 unique email records. We have shared our findings with the appropriate authorities and data-breach notification services.”
For validation, Kaduu cross-referenced the data with Have I Been Pwned, which has since listed the incident in its public breach database.
Scope of the Data Exposure
Preliminary forensic evaluation shows that the Artists&Clients data breach may have exposed the following categories of data:
| Type of Data | Description | Risk Level |
| Email addresses | Contact information of users | High |
| Password hashes | Encrypted (bcrypt + SHA-1) | High |
| Display names | Public user handles | Moderate |
| Profile info | Optional, such as country or commission notes | Low |
| Registration details | Account creation dates | Low |
While no direct financial information such as PayPal or credit-card details has been confirmed in the dump, cybersecurity experts emphasize that the exposure of email and password pairs can lead to credential-stuffing attacks, phishing, and identity theft.
Sample Proof 📂
Forum Post Proof 🧩
Expert Analysis on the Dark Web Leak
Cybersecurity experts classify this event as a targeted dark web leak rather than an accidental exposure. Breachsta.rs, the forum where it surfaced, has become notorious for hosting databases from freelance and e-commerce platforms due to their lucrative mix of creative professionals and small-business clients.
💬 Cyber analyst Laura Mendez from Darknet Search Labs explained:
“Attackers target niche platforms like Artists&Clients because their users often reuse passwords from main email or payment accounts. Even if financial data isn’t stolen, the login credentials have resale value on the underground market.”
Investigators suspect the compromise may have originated from a misconfigured API endpoint or a reused credential exploited through automated attacks.
User Impact and Risks ⚠️
For artists and commissioners, the Artists&Clients data breach could lead to several immediate threats:
- Phishing emails disguised as account recovery notices.
- Unauthorized logins to connected social-media or payment services.
- Loss of reputation for artists whose private commission records were exposed.
- Spam and targeted scams leveraging leaked email lists.
Users should treat all communication claiming to be from Artists&Clients with caution and verify authenticity before clicking any links.
How to Check if You Were Affected
Victims can verify their status using the trusted breach-notification service Have I Been Pwned. Simply enter your email address to confirm whether it appears in the leaked dataset.
Additionally, DarknetSearch.com provides guidance on how to monitor dark web marketplaces and remove personal information from compromised sources. (Visit DarknetSearch.com for detailed threat-tracking resources.)
Practical Tip 💡
If your information appears in this dark web leak, act immediately:
- Reset your password on Artists&Clients and any site where it was reused.
- Enable two-factor authentication (2FA) for all important accounts.
- Avoid clicking links in unsolicited “security update” emails.
- Use a password manager to generate unique credentials.
Remember: even if passwords were hashed, weak ones can still be cracked using brute-force tools available on underground forums.
Checklist for Personal Security 🔐
- ✅ Change all passwords related to your Artists&Clients account.
- ✅ Enable 2FA on your primary email address.
- ✅ Check if your email appears on Have I Been Pwned.
- ✅ Monitor financial accounts for unusual transactions.
- ✅ Review privacy settings on social-media profiles.
These simple steps significantly reduce the potential damage from data exposure.
What Makes This Breach Significant
Unlike larger platforms with dedicated cybersecurity teams, smaller creative marketplaces often rely on outsourced hosting and third-party plugins. This increases the likelihood of unpatched vulnerabilities. The Artists&Clients data breach thus serves as a warning to niche online communities about the need for regular security audits.
Furthermore, the appearance of the database on Breachsta.rs highlights the growing commercialization of stolen data within artistic communities—a trend previously seen in 2024 with leaks from other commission-based services.
Company Response and Transparency
As of October 2025, Artists&Clients has not released an official public statement. However, internal sources suggest that an investigation is underway, and users have been urged via email to reset passwords. The platform’s support page briefly acknowledged “technical issues” but did not specify the nature of the breach.
Transparency advocates argue that timely disclosure is crucial for trust. According to global privacy regulations such as GDPR, companies are required to inform affected users within a reasonable period.
The Role of Threat Intelligence Teams
The discovery of this Artists&Clients data breach underscores the value of specialized intelligence groups such as Kaduu, whose analysts continuously monitor dark-web chatter, data-leak markets, and breach-sharing channels. Their early detection allowed cybersecurity communities to validate and classify the data before it was exploited on a larger scale.
💡 Expert insight:
“Real-time dark-web monitoring is no longer optional—it’s essential,” said Arjun Patel, cybersecurity researcher at Kaduu. “Platforms that proactively track breaches can contain the damage faster and alert users promptly.”
Broader Implications for the Creative Economy 🎨
This incident reveals a growing pattern: independent creative platforms have become soft targets. Artists depend on these marketplaces for income, often without realizing how their digital security can impact their livelihoods. Cybercriminals exploit this by selling databases to spam networks, ransomware operators, and phishing campaigns.
The dark web leak of Artists&Clients data also raises questions about third-party security standards. If small platforms outsource hosting or payment processing, vulnerabilities in those vendors could cascade into full-scale breaches.
Lessons for Platform Operators
To prevent similar breaches, platform owners should:
- Conduct penetration testing every quarter.
- Implement encryption at rest and in transit.
- Use bug-bounty programs to engage ethical hackers.
- Maintain regular backups and quick incident-response plans.
- Educate users about digital hygiene.
According to data from Cyber Trust Alliance 2025, 67 % of small web platforms lack formal incident-response frameworks—a key factor behind recurring data leaks.
Why Users Should Care Even If They’re Not Affected 🤔
You might wonder: What if I don’t have an Artists&Clients account? The answer is simple—data breaches anywhere affect user safety everywhere. Cybercriminals aggregate leaked datasets to build identity profiles that fuel future attacks. Even unrelated accounts can be compromised through cross-referenced information.
Being informed about breaches like this one helps all internet users recognize phishing patterns and maintain better password discipline.
Conclusion🚀
The Artists&Clients data breach discovered in August 2025 and posted to Breachsta.rs marks another wake-up call for online creative communities. Thanks to Kaduu’s vigilance, the leak was identified early, minimizing potential harm—but it still underscores the urgent need for better cybersecurity awareness among artists and clients alike.
Users are encouraged to stay alert, follow recommended protection steps, and report suspicious messages claiming to come from the platform.
Discover much more in our complete guide on digital-safety practices at DarknetSearch.com
Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


