Wired Data Breach Revealed: 2.3M Records from Wired.com Exposed

➤Summary
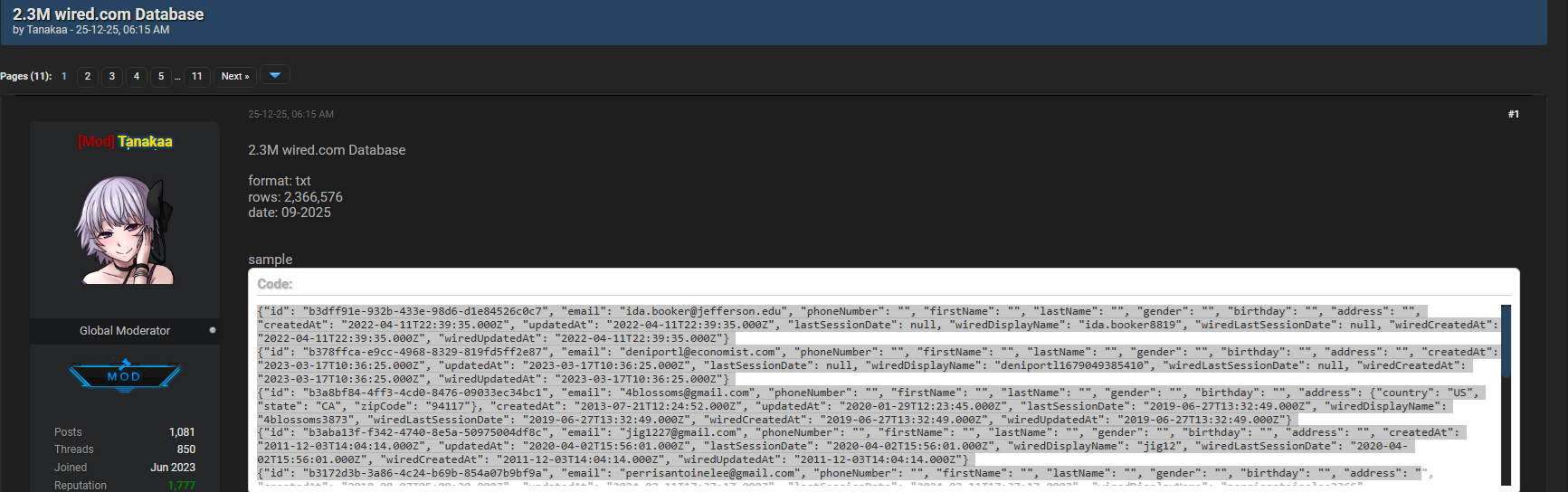
Wired data breach discussions intensified in late December 2025 after a dataset allegedly containing 2.3 million Wired.com-related records surfaced on underground forums. According to claims published on Darkforums.st by the author Tanakaa, the leaked Wired.com database includes primarily internal identification numbers and email addresses, with varying levels of additional personal data. This Wired data breach event highlights how media platforms, even those focused on technology and security awareness, remain attractive targets for cybercriminals.
The exposure has sparked renewed conversations around data breach detection, digital trust, and how organizations monitor illicit data circulation across hidden networks 🌐.
Overview of the 2.3M Wired.com Database Leak
The leaked Wired.com dataset reportedly appeared on Darkforums.st on December 25, 2025, immediately drawing attention from threat analysts and researchers. The Wired data breach involves approximately 2.3 million records, though the completeness of each record varies significantly. Most entries reportedly contain only an internal ID and an email address, while a smaller subset includes names, physical addresses, phone numbers, or dates of birth. This uneven structure suggests aggregation from multiple sources or partial system access rather than a single, fully compromised database. Analysts following Wired data breach patterns note that such variability is common when attackers extract user tables over time rather than in one attack vector 🔍.
What Kind of Personal Data Is Included?
Understanding the exposed data types is critical for assessing real-world risk. In this Wired data breach, the majority of records are relatively minimal, which lowers immediate identity theft risk but still creates phishing and social engineering opportunities. Some records, however, combine multiple identifiers, increasing sensitivity. According to the forum post, only a small fraction of entries includes full profiles, but even limited data can be weaponized at scale. Threat actors often enrich these datasets with information from other breaches, turning partial data into complete digital identities. This is why Wired data breach analysis often focuses on downstream misuse rather than just the initial exposure ⚠️.
Where the Leak Is Circulating and Why It Matters
The dataset was shared on Darkforums.st, a known marketplace-style forum where cybercriminals exchange compromised data. Such platforms are routinely indexed and tracked by monitoring services and researchers. The Wired data breach circulation on these forums increases the likelihood of resale, repackaging, or bundling with other leaks. Reports from monitoring teams referenced by platforms like https://darknetsearch.com/ show that media-related databases often resurface months later in new campaigns. The visibility of this dataset underscores the importance of continuous dark web solutions rather than one-time incident responses 🕵️♂️.
Source Verification and External Reporting
Independent reporting has reinforced the credibility of the claims. A detailed analysis published by Techzine examined the Wired.com dataset and confirmed its appearance on hacker forums . The article notes that while Wired has not publicly confirmed the breach at the time of writing, the dataset’s structure aligns with legitimate user databases. External verification from reputable outlets strengthens the assessment that this Wired data breach is not fabricated, which is a common concern in underground leak claims.
Risks for Users and Organizations
So, what does this mean for affected users? The short answer: increased exposure to targeted attacks. Email addresses tied to recognizable brands like Wired.com are valuable for spear-phishing campaigns. Attackers exploit brand trust to lure victims into credential theft or malware downloads. For organizations, the Wired data breach illustrates reputational damage risks and regulatory scrutiny. Even when only partial data is leaked, compliance obligations may still apply depending on jurisdiction. This scenario reinforces why data breach detection capabilities must extend beyond perimeter security into threat intelligence monitoring 📊.
How Dark Web Monitoring Detects Such Leaks
Dark web monitoring plays a central role in uncovering incidents like this one. Specialized tools continuously scan forums, marketplaces, and encrypted channels for brand mentions and data samples. Analysts then validate the data, assess scope, and notify affected parties. In many investigations, experts compare dark web monitoring tools to determine which platforms provide faster alerts and deeper coverage. Effective monitoring reduces dwell time between breach occurrence and response, limiting damage. This Wired data breach is often cited internally as a case study dark web monitoring teams use to demonstrate early-warning value.
Practical Checklist for Organizations
To improve resilience against similar incidents, organizations can follow this concise checklist:
- Audit user databases regularly for misconfigurations.
- Enforce encryption and access logging on sensitive tables.
- Subscribe to a reliable dark web report service for brand monitoring.
- Integrate alerts into incident response workflows.
- Educate users about phishing risks after public breach disclosures.
These steps are frequently recommended by analysts reviewing Wired data breach scenarios and similar media-industry exposures.
The Role of Intelligence Platforms
Threat intelligence platforms aggregate signals from multiple underground sources. By correlating mentions, file hashes, and seller reputations, they help teams prioritize credible threats. Many enterprises now adopt layered dark web solutions that combine automated crawling with human analysis. According to one security researcher, “The real value isn’t finding the data, it’s understanding how fast it spreads and who is buying it.” Resources like https://darknetsearch.com/ provide ongoing insights into leak trends and actor behavior, supporting proactive defense strategies 🧠.
Why This Wired Data Breach Is a Wake-Up Call
This incident raises an important question: Does limited data exposure still matter? Yes, because even minimal datasets can fuel large-scale abuse when combined with other breaches. The Wired data breach demonstrates how attackers monetize volume over depth. While no passwords or financial details were reported, the reputational impact and user trust erosion are significant. Media companies, often perceived as security-savvy, are not immune. Continuous monitoring, transparent communication, and rapid mitigation are now baseline expectations, not optional enhancements 🔐.
Conclusion and Next Steps
The 2.3M Wired.com database exposure underscores a broader reality: data leaks are no longer isolated events but part of an evolving ecosystem of cybercrime. The Wired data breach highlights the importance of early detection, contextual analysis, and user awareness. Organizations that invest in intelligence-driven monitoring and clear response plans are better positioned to protect trust and comply with regulations. Readers interested in strengthening their defenses should explore professional monitoring options and educational resources today. Discover much more in our complete guide. Request a demo NOW.
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourselfsssss.


