Arkansas Department of Health data breach: 7 Key Impacts Revealed

➤Summary
The Arkansas Department of Health data breach has quickly become one of the most discussed healthcare cyber incidents of late 2025, raising urgent concerns about exposure of professional and personal data. According to posts attributed to the author Tanaka on Breachforums.bf, an alleged database linked to SERV, the Arkansas Department of Health’s volunteer and emergency response system, was leaked and advertised online.
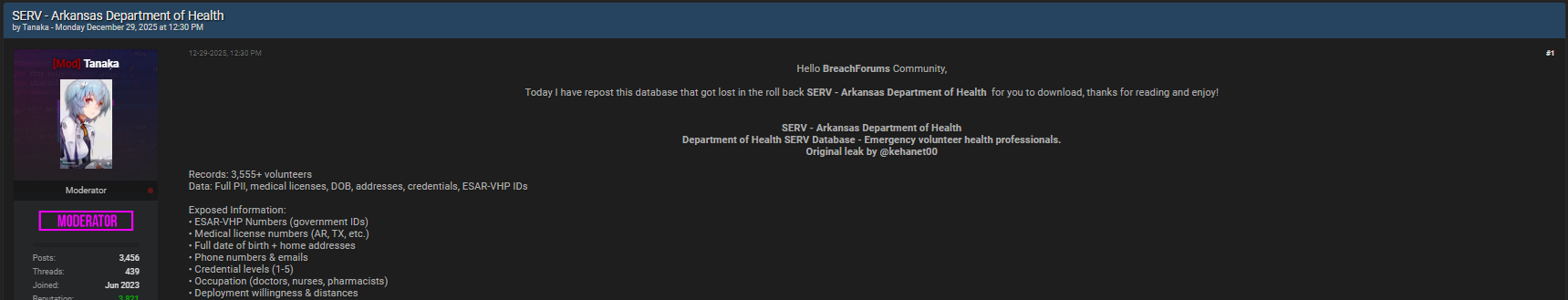
This Arkansas Department of Health data breach is not just another technical mishap; it highlights systemic risks facing public health institutions and the professionals who support them. As healthcare data breaches continue to rise, understanding what happened, what data was exposed, and how organizations can respond is critical for both compliance and trust 🛡️.
What Is SERV and Why It Matters
SERV is a system associated with the Arkansas Department of Health that manages information about healthcare professionals and volunteers, particularly those willing to deploy during emergencies. The Arkansas Department of Health data breach is significant because SERV stores sensitive identifiers that go beyond basic contact details. In emergency contexts, this data enables rapid mobilization of doctors, nurses, pharmacists, and other licensed professionals. When such systems are compromised, the impact extends far beyond inconvenience, affecting public safety, workforce integrity, and confidence in state healthcare infrastructure 🚑. The breach allegedly surfaced on Breachforums, a well-known underground forum often monitored by cybersecurity analysts and dark web monitoring services.
Timeline and Disclosure of the Incident
Based on the forum post dated 29 December 2025, the actor known as Tanaka claimed access to a database tied to SERV. The Arkansas Department of Health data breach was later referenced by independent breach alert platforms, which analyzed samples allegedly offered for sale or distribution. While official confirmation from the Arkansas Department of Health was still pending at the time of publication, the circulation of screenshots and field lists intensified scrutiny. This pattern is consistent with many modern healthcare data breach events, where third-party disclosures precede formal statements ⏳. Dark web monitoring are often used by analysts to track such early indicators.
Exposed Information and Data Categories
One of the most alarming aspects of the Arkansas Department of Health data breach is the breadth of exposed information. According to the forum listing, the compromised dataset allegedly included:
• ESAR-VHP numbers used as government-issued identifiers
• Medical license numbers across states such as Arkansas and Texas
• Full dates of birth combined with home addresses
• Phone numbers and email addresses
• Credential levels ranging from 1 to 5
• Occupation details including doctors, nurses, and pharmacists
• Deployment willingness and maximum travel distances
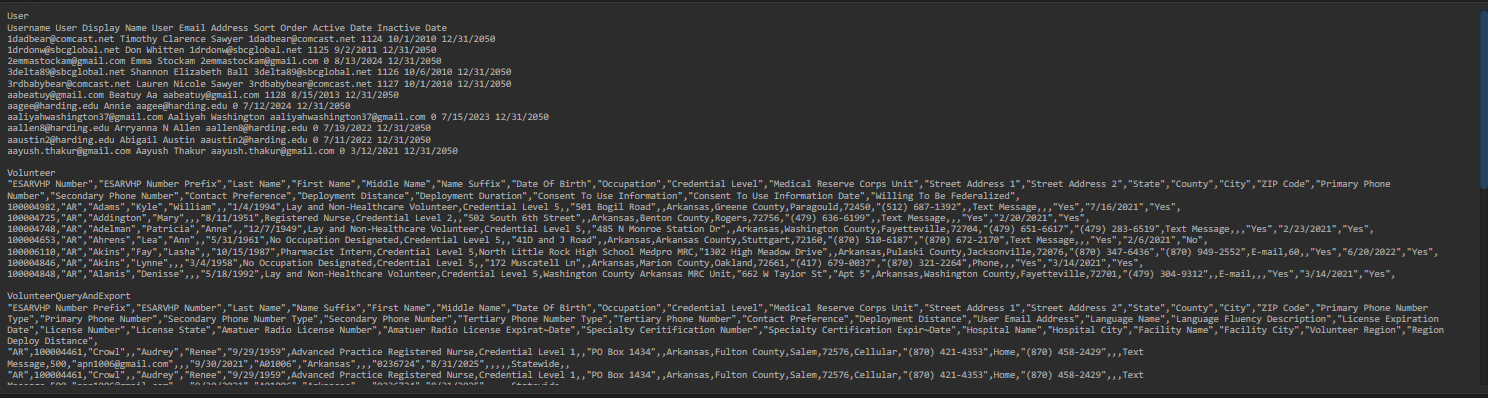
This combination of personal and professional data significantly elevates identity theft and targeted phishing risks 📧. For threat actors, such enriched datasets are far more valuable than isolated records.
Why Healthcare Data Is a Prime Target
Healthcare data breaches are especially lucrative because medical and licensing data is difficult to change once exposed. The Arkansas Department of Health data breach underscores this reality. Unlike passwords, a medical license number or date of birth cannot be easily reset. Criminal groups frequenting underground marketplaces know this and actively seek healthcare-related datasets. Analysts who compare dark web monitoring tools often note that healthcare entities appear repeatedly due to legacy systems and complex access requirements 🧠. This case also functions as a case study dark web monitoring professionals can analyze to refine detection and response strategies.
The Role of Dark Web Intelligence
Early awareness of incidents like the Arkansas Department of Health data breach often comes from proactive monitoring of underground forums. Platforms that provide dark web solutions and structured alerts can detect mentions of organizations before data is widely abused. A comprehensive dark web report typically includes context about the actor, forum reputation, and validation of sample data. For example, intelligence teams may cross-reference findings with darknetsearch to validate whether similar datasets are being reshared or discussed elsewhere 🔍. This kind of data breach detection is increasingly essential for public sector organizations with limited internal resources.
Key Risks for Affected Individuals
What does this mean for healthcare professionals listed in SERV? The Arkansas Department of Health data breach exposes them to several concrete risks. Identity fraud is the most immediate, especially with ESAR-VHP numbers and full birthdates involved. There is also a heightened risk of spear-phishing, where attackers tailor messages using accurate occupational and deployment details. Could this data be misused to impersonate licensed professionals? Yes, because license numbers combined with contact details can be exploited for fraudulent credential verification attempts. Awareness and vigilance are therefore essential 👀.
Practical Checklist for Organizations
To reduce exposure and respond effectively to incidents like the Arkansas Department of Health data breach, organizations should follow a clear checklist:
- Monitor underground forums continuously using trusted intelligence sources
- Validate alleged leaks with sample analysis and metadata review
- Notify potentially affected individuals promptly and transparently
- Enforce multi-factor authentication on all administrative systems
- Conduct regular access reviews for volunteer and emergency platforms
- Document findings and lessons learned for compliance audits
This structured approach supports faster containment and helps restore trust 🤝.
Expert Insight on Public Health Cybersecurity
“Public health databases are uniquely sensitive because they blend personal identity with professional authority,” notes a cybersecurity analyst specializing in government systems. “When breaches occur, as in the Arkansas Department of Health data breach, the downstream impact can affect emergency readiness itself.” This insight reinforces why state agencies must prioritize threat intelligence and incident response maturity, not just perimeter defenses.
How This Breach Fits a Larger Pattern
The Arkansas Department of Health data breach is not an isolated event. Similar healthcare data breach incidents have affected hospitals, insurers, and public agencies worldwide. Attackers increasingly target systems designed for coordination and trust, knowing the data inside is both rich and operationally critical. Analysts reviewing trends on https://darknetsearch.com/ often observe that once a dataset appears on Breachforums, it may resurface months later on other marketplaces, compounding harm over time 🔁.
Strengthening Future Defenses
Preventing future incidents requires more than patching vulnerabilities. Organizations should invest in staff training, regular penetration testing, and intelligence-driven security programs. Integrating alerts from underground sources with internal security operations centers enables faster triage. While no system is immune, reducing dwell time and improving visibility can dramatically lower impact. The Arkansas Department of Health data breach serves as a reminder that preparedness is an ongoing process, not a one-time project 🚀.
Conclusion
The alleged SERV incident highlights how quickly sensitive healthcare data can be exposed and exploited. The Arkansas Department of Health data breach illustrates the importance of proactive monitoring, transparent communication, and continuous improvement in cybersecurity posture. Public health agencies and private organizations alike must treat such events as catalysts for stronger defenses and smarter intelligence use. Discover much more in our complete guide and Request a demo NOW to see how advanced monitoring can help protect your organization before the next breach occurs.
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourselfsssss.


