French Ministry of Agriculture Database Revealed: 7 Key Impacts of the 60GB Leak

➤Summary
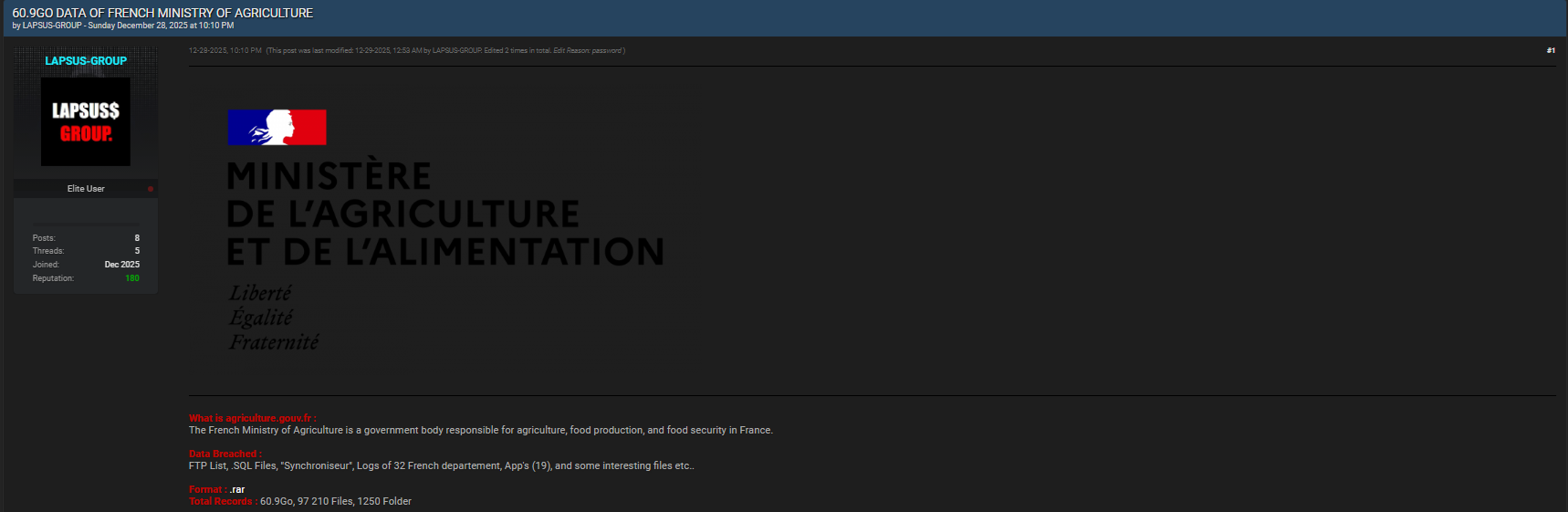
The French Ministry of Agriculture Database has become the focus of intense scrutiny after a major leak allegedly exposed 60GB of sensitive material on underground forums. Reported by Dark Web Informer, the breach was attributed to the threat actor LAPSUS-GROUP and published on 28.12.2025 on Breachforums.bf. This incident highlights how public-sector databases remain prime targets for cybercriminals seeking operational intelligence, credentials, and application data. Beyond the immediate technical fallout, the leak raises strategic questions about visibility, response, and prevention in a world where underground marketplaces move faster than traditional defenses.
In this article, we analyze what was exposed, why it matters, and how organizations can learn from this case to strengthen their security posture 🔎💡.
Overview of the Alleged Breach
According to forum posts, the French Ministry of Agriculture Database leak included FTP lists, .SQL files, a “Synchroniseur” tool, logs covering 32 French departments, 19 applications, and additional files described as “interesting” by the actor. Such a combination suggests not a single data dump but a broad snapshot of internal operations. When attackers access structured databases alongside logs and synchronization tools, they gain contextual knowledge that can enable further exploitation. The publication date and attribution indicate a coordinated disclosure strategy designed to attract attention and potential buyers 💥.
Who Is LAPSUS-GROUP and Why Attribution Matters
LAPSUS-GROUP is known for high-impact leaks targeting large organizations, often focusing on operational data rather than just personal records. Attribution matters because it helps defenders anticipate tactics, techniques, and procedures. In this case, the group’s history suggests an emphasis on visibility and reputational pressure rather than silent exploitation. Understanding the actor profile helps analysts prioritize response actions and informs broader data breach detection strategies used by governments and enterprises alike 🧠.
What Data Types Were Exposed and Their Risks
The exposed materials reportedly included:
- FTP credentials and directory listings
- SQL database files containing structured records
- Synchronization utilities used for internal data flow
- Application binaries and configuration files
- Logs spanning 32 administrative departments
Each category carries distinct risks. SQL files may contain sensitive records, while logs often reveal internal IPs, user behaviors, and system architecture. Applications and synchronization tools can be reverse-engineered to find vulnerabilities. Combined, these elements can enable lateral movement or future attacks even after initial containment 📂⚠️.
Impact on Public Institutions and Citizens
The immediate impact of a breach involving the French Ministry of Agriculture Database extends beyond IT teams. Public trust can erode when citizens learn that administrative data may be circulating on illicit forums. Operationally, ministries may face downtime, audits, and regulatory scrutiny. Strategically, such incidents fuel debates about budget allocation for cybersecurity and the need to compare dark web monitoring tools that can provide early warning of leaks before they escalate 📊.
Why Dark Web Visibility Is Critical
Dark web forums act as early indicators of compromise. The faster an organization identifies mentions of its assets, the quicker it can respond. This incident serves as a case study dark web monitoring example where timely intelligence could reduce damage. Modern dark web solutions aggregate forum posts, marketplaces, and paste sites to flag relevant exposures. A single question often arises: Can monitoring really make a difference? The answer is yes—early alerts enable faster takedowns, password resets, and communication strategies, limiting downstream harm 🚨.
Practical Checklist for Security Teams
To translate lessons into action, consider this checklist:
- Map all externally accessible services and FTP endpoints
- Regularly audit application logs and synchronization tools
- Implement continuous monitoring of underground forums
- Integrate alerts into incident response workflows
- Conduct tabletop exercises simulating public-sector leaks
This practical tip section aligns with featured snippet requirements and provides clear, actionable guidance for defenders seeking to reduce exposure risk ✅.
The Role of Reporting and Transparency
Publishing a clear dark web report after incidents helps stakeholders understand scope and response. Transparency does not mean revealing sensitive details; it means communicating facts, mitigation steps, and timelines. As one cybersecurity analyst noted, “Silence creates speculation, while structured reporting builds resilience.” Linking intelligence findings to executive decisions strengthens organizational maturity 📘.
Learning from the French Ministry Case
The French Ministry of Agriculture Database incident underscores recurring themes: legacy systems, broad access privileges, and limited underground visibility. It also shows why internal teams often rely on external intelligence sources. Dark web monitoring tools provide contextual insights into forums and markets, helping analysts validate claims and prioritize actions. Leveraging such resources alongside internal telemetry enhances overall data breach detection capabilities 🔗.
Broader Implications for Government Cybersecurity
Government agencies worldwide face similar challenges. Decentralized departments, varied applications, and aging infrastructure create uneven security baselines. The exposure of logs from 32 departments illustrates how one weak link can cascade. Proactive intelligence gathering, including underground monitoring, is increasingly seen as essential rather than optional.
Conclusion
The alleged leak of the French Ministry of Agriculture Database is a reminder that sensitive operational data remains a valuable commodity on underground forums. From FTP lists to application logs, each exposed element increases long-term risk if not addressed holistically. Organizations that invest in intelligence-led defenses, structured reporting, and continuous monitoring are better positioned to respond decisively. Discover much more in our complete guide and strengthen your understanding of modern threat intelligence. Request a demo NOW to see how proactive monitoring can transform your security posture 🚀
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourselfsssss.


