Vietiso Database Leak: 209K Records and 2026 Impact

➤Summary
The Vietiso database leak has emerged as one of the most concerning cybersecurity incidents affecting Vietnam’s travel sector in 2026. Reportedly published on Breachforums.bf on 13 January 2026 by a threat actor known as Solonik, this exposure involves more than 209,000 Vietnamese travel clients linked to vietiso.com, a travel CRM platform. The leak allegedly contains highly sensitive personal and KYC (Know-Your-Customer) information, placing thousands of individuals at potential risk of identity misuse and fraud 🚨. As digital travel platforms increasingly store large volumes of personal data, incidents like this highlight the urgent need for stronger data protection practices and awareness.
This darknetsearch.com article provides a clear, in-depth analysis of what happened, what data was exposed, why it matters, and how users and businesses can respond effectively.
What Is the Vietiso Database Leak?
The Vietiso database leak refers to the unauthorized disclosure of a customer database allegedly belonging to vietiso.com, a Vietnam-based travel CRM used for managing client bookings and records. According to the forum post, the dataset was shared in Excel (.xlsx) UTF-8 format and contains 209,759 individual records from 2026 📊. Each record reportedly includes full name, Vietnamese national ID number (CCCD), phone number, date of birth, and full residential address.
This combination qualifies as full KYC data, making the exposure particularly serious. The dataset’s appearance on Breachforums.bf suggests intentional distribution rather than accidental disclosure, raising questions about internal security controls and third-party access.
Leak Source and Publication Context
The database was allegedly published on Breachforums.bf, a well-known underground forum associated with multiple global data exposure cases. The author, using the alias Solonik, shared details indicating the target as vietiso.com and categorized the incident as a customer database breach 🕵️. While forum claims always require independent verification, similar disclosures have historically proven accurate. Cybersecurity analysts often monitor such forums alongside Dark web monitoring platforms to assess credibility and potential downstream misuse. The timing in early 2026 coincides with increased targeting of travel-related platforms as tourism rebounds and data volumes grow.
What Data Was Exposed?
Based on the leak description, the exposed information includes a wide range of personally identifiable information. Below is a simplified breakdown for clarity:
| Data Type | Description |
| Full Name | Customer first and last names |
| CCCD | Vietnamese national ID number |
| Phone Number | Personal mobile contact |
| Date of Birth | Full DOB |
| Address | Complete residential address |
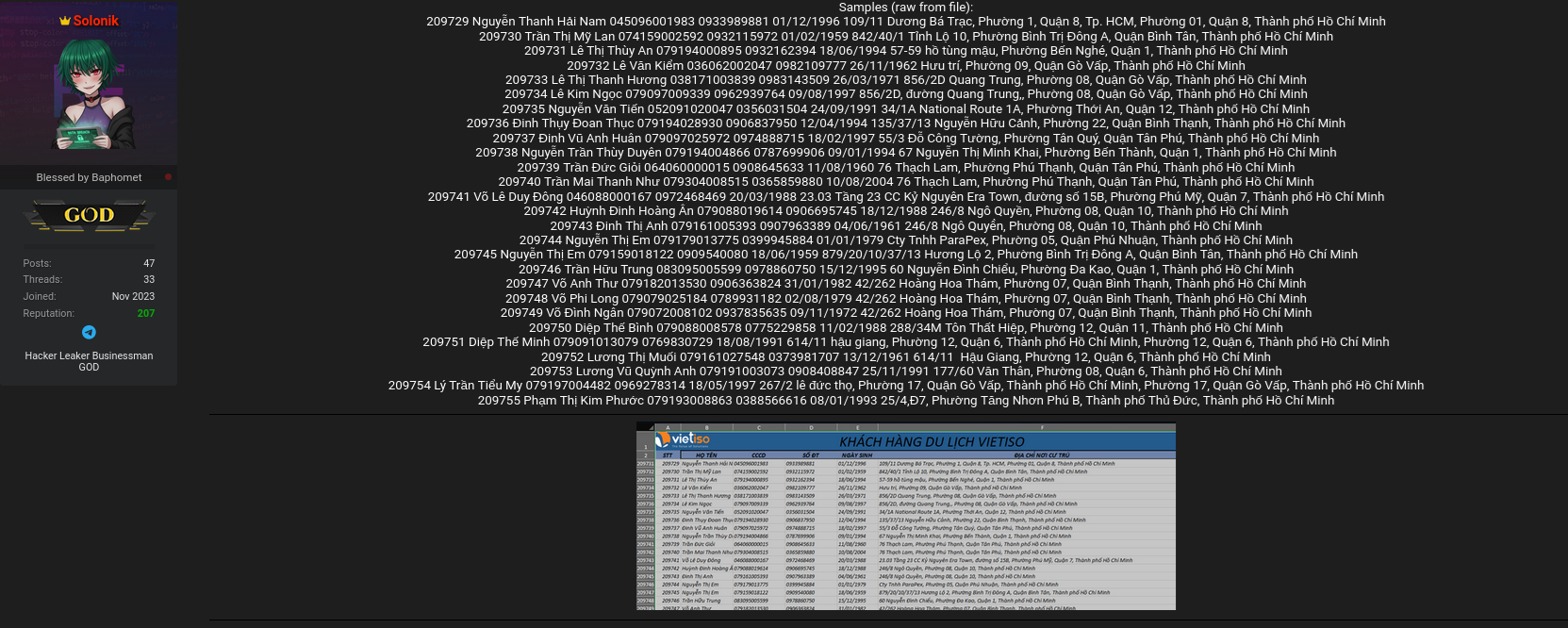
This level of detail significantly increases the risk profile for affected users ⚠️. Unlike partial leaks, full KYC data can be used to bypass verification checks in financial and telecom services.
Why This Vietnam Travel Data Breach Matters
This Vietnam travel data breach is not just another statistic. Travel CRM systems aggregate data from bookings, payments, and identity verification processes. When compromised, they provide threat actors with a rich dataset that can be monetized or weaponized. Identity theft, SIM swapping, targeted phishing, and fraudulent loan applications are all plausible outcomes. According to cybersecurity reporting from Krebs on Security, breaches involving government-issued IDs have a much higher long-term impact compared to email-only leaks. For Vietnamese travelers, the exposure of CCCD numbers is especially sensitive due to their use across banking and public services.
Who Is Potentially Affected?
Anyone who booked travel services or had their details stored within vietiso.com’s CRM during the affected period may be impacted. This includes domestic travelers, tour participants, and possibly corporate clients whose employee details were processed ✈️. Businesses that partnered with the platform may also face reputational risks if customer trust erodes. Dark Web Monitoring tools and intelligence summaries available through Darknetsearch.com often show that such datasets can circulate for months, increasing cumulative harm.
Is This the First Travel CRM Breach?
No. Travel platforms worldwide have been frequent targets over the past decade. High transaction volumes, seasonal traffic spikes, and complex third-party integrations make them attractive to attackers. The Vietiso database leak fits a broader pattern of travel CRM breach incidents seen in Southeast Asia. A clear question arises: Are current security standards keeping pace with data growth? The answer is often no, especially for mid-sized platforms lacking dedicated security teams. This underscores the need for regular audits and encryption practices 🔐.
Practical Checklist for Affected Users
If you believe your data may be part of this exposure, consider the following steps:
• Monitor bank and mobile accounts for unusual activity
• Be cautious of unsolicited calls or messages using personal details
• Enable additional verification with service providers
• Replace compromised credentials where possible
• Follow breach intelligence updates from trusted dark web monitoring solutions.
This checklist cannot eliminate risk entirely but can significantly reduce potential damage ✅.
Legal and Regulatory Implications
Vietnam’s data protection regulations are evolving, with increasing emphasis on consent, storage limitation, and breach notification. Incidents like this Vietnam travel data breach may prompt stricter enforcement and higher penalties. Companies handling full KYC data are expected to implement safeguards aligned with international standards such as ISO/IEC 27001. Failure to do so could result in regulatory action and civil liability. As one regional cybersecurity expert noted, “Breaches involving identity data are no longer IT issues; they are corporate governance failures.”
Key Takeaways for Businesses
For organizations operating travel CRMs or similar platforms, the lesson is clear 📌:
• Minimize stored personal data
• Encrypt sensitive fields like ID numbers
• Restrict database access on a need-to-know basis
• Conduct regular penetration testing
• Prepare an incident response plan
Addressing these areas proactively is far less costly than responding after a leak occurs.
Conclusion and What to Do Next
The Vietiso database leak highlights the real-world consequences of inadequate data protection in the travel industry. With over 209,000 records reportedly exposed, the incident serves as a wake-up call for both users and service providers. Staying informed, adopting protective measures, and demanding transparency from platforms are essential steps moving forward 🌐. For deeper insights into similar incidents and evolving cyber threats, continue exploring trusted intelligence resources.
Discover much more in our complete guide
Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


