Universidad Autonoma de Sinaloa Data Breach Exposes Records

➤Summary
Universidad Autonoma de Sinaloa data breach allegations have surfaced after a threat actor published claims of compromised academic records on an underground forum. The post, shared on Darkforums.st on 03 February 2026 by a user identified as “Straightonumberone,” describes extensive student and professor databases allegedly extracted from institutional systems. According to the listing, the exposed information includes personal identifiers, academic details, and contact information tied to multiple campuses and regional units. Incidents affecting educational institutions are particularly concerning because they involve long-term identity data and sensitive employment records, increasing the likelihood of downstream fraud and targeted abuse 🎓. This darknetsearch.com article examines what data was reportedly compromised, why it matters, and how organizations can respond effectively.
Overview of the Alleged UAS Data Exposure
The Universidad Autonoma de Sinaloa data breach centers on claims that both student and faculty records were accessed and shared without authorization. The forum post outlines structured datasets, suggesting direct access to internal databases rather than scraped public sources. While official confirmation was not included in the forum listing, the level of detail provided mirrors previous verified education-sector breaches.
Such incidents often result in prolonged exposure because academic data remains valid for years, unlike passwords that can be reset quickly ⚠️.
Student Records Reportedly Compromised
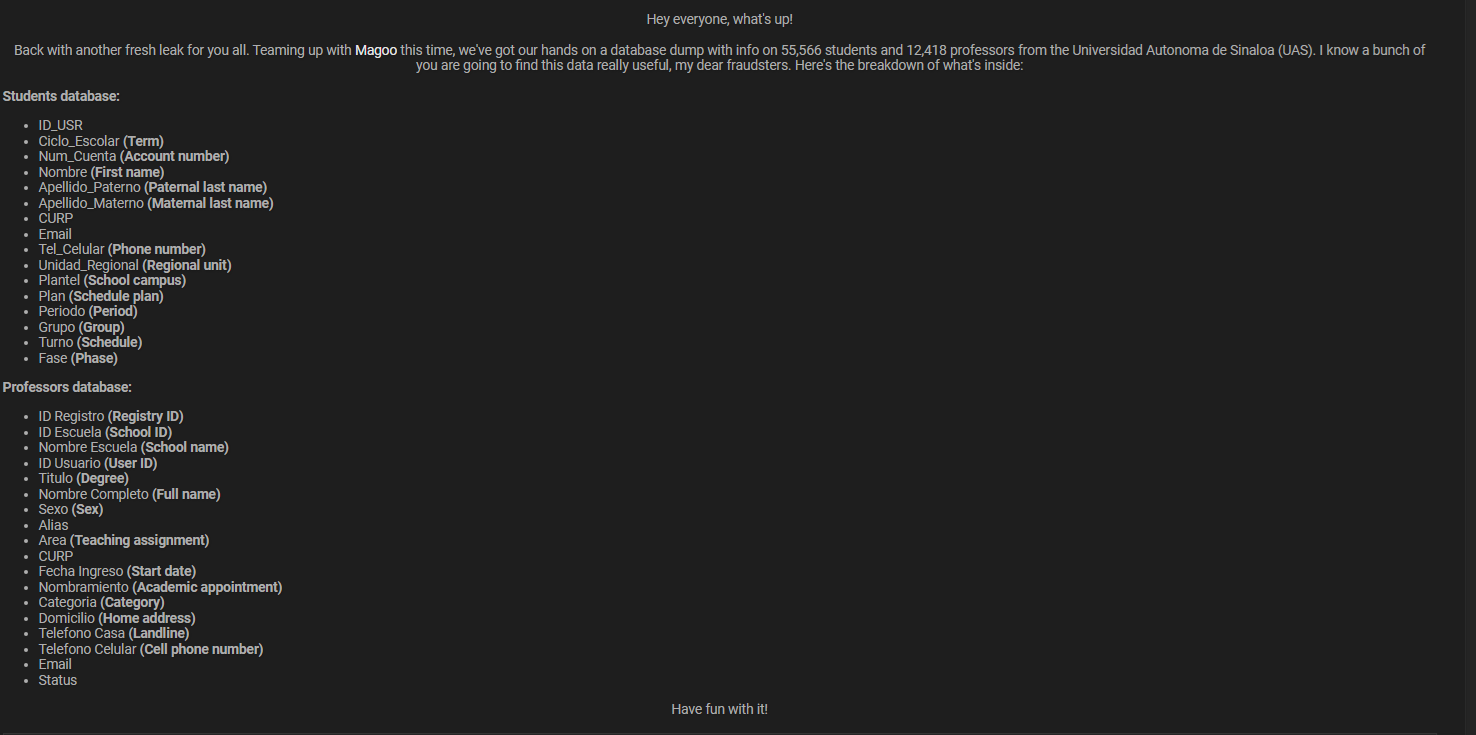
According to the threat actor, the student database contains a wide range of academic and personal fields. These include account numbers, enrollment terms, full names, CURP identifiers, email addresses, and mobile phone numbers. Additional attributes such as regional unit, campus, schedule plans, academic periods, groups, and phases were also listed. When combined, these data points can be exploited for identity fraud, targeted phishing, or impersonation schemes 📧. Education records are especially attractive to criminals because they enable believable social engineering.
Professor and Staff Database Details
The listing also claims access to a professors database containing registry IDs, school identifiers, academic titles, teaching assignments, and full contact details. Highly sensitive elements such as CURP numbers, home addresses, landline and mobile phone numbers, and employment status were included. Exposure of this depth places faculty members at risk of harassment, financial fraud, and credential abuse 🏠. It also raises concerns about institutional security controls protecting employee data.
Why Education Sector Breaches Are High Impact
A Universidad Autonoma de Sinaloa data breach is not just a technical issue; it is a trust issue. Universities hold lifelong identifiers tied to students and staff, often shared with government agencies and partners. Once leaked, this information cannot be easily changed. Threat actors frequently monetize such datasets repeatedly, reselling them across multiple underground channels, which amplifies harm over time 📉.
Is the Breach Confirmed?
Is this breach officially confirmed?
As of now, the claims are based on a dark forum post rather than a public disclosure. However, credible underground listings with detailed schemas often indicate real compromises. Institutions should treat such intelligence as an early warning rather than waiting for formal confirmation.
Dark Forum Activity and Threat Actor Behavior
The post was published on Darkforums.st, a known venue for data leak claims. The author “Straightonumberone” presented the datasets in an organized manner, suggesting familiarity with database structures. This behavior aligns with actors who specialize in education and public-sector targets. Monitoring these patterns helps analysts assess credibility and urgency 🔍.
Risks to Students, Faculty, and the Institution
For students, exposed identifiers can lead to identity theft, fraudulent account creation, and long-term privacy loss. Faculty members face similar risks, compounded by employment data that can be weaponized for extortion. For the institution, consequences may include regulatory scrutiny, reputational damage, and operational disruption. Legal obligations around data protection may also be triggered depending on jurisdiction 📜.
Practical Response Checklist for Universities
Educational institutions should follow a structured response when facing potential exposure:
- Validate the dataset through internal forensic review
- Secure affected systems and rotate credentials
- Notify legal and compliance teams immediately
- Prepare clear communications for students and staff
- Implement continuous threat intelligence monitoring 🧩
This checklist helps reduce uncertainty and demonstrates responsible governance.
The Role of Proactive Threat Intelligence
Early detection of underground activity is critical. Leveraging dark web monitoring allows institutions to identify mentions of their organization before data is widely abused. Intelligence drawn from dark web monitoring reports often guides rapid response decisions and risk prioritization. A scalable dark web monitoring solution supports ongoing visibility, while Dark Web Monitoring for MSSP services enables managed providers to protect multiple education clients efficiently 🚀.
Learning from Similar Academic Incidents
Past university breaches show that secondary attacks often follow initial exposure. Criminals reuse student data for phishing campaigns months later, especially during enrollment or exam periods. Continuous monitoring and awareness training are therefore essential components of long-term defense.
Trusted Resources for Ongoing Awareness
Analysts and security teams can stay informed through dedicated intelligence platforms. Ongoing research and breach analyses are available at dark web monitoring platforms📚. For independent investigative reporting on breaches, BleepingComputer is one external source with focus in cybersecurity news.
Conclusion: Turning Early Warnings into Action
The alleged Universidad Autonoma de Sinaloa data breach highlights how vulnerable educational institutions remain to unauthorized access and data leakage. Whether confirmed or still under investigation, credible underground claims demand immediate attention. By combining structured incident response, transparent communication, and proactive intelligence-driven monitoring, universities can reduce long-term harm and protect their communities 🔐.
Discover much more in our complete guide
Request a demo NOW
*Disclaimer: DarknetSearch reports on publicly available threat-intelligence sources. Inclusion of an organization in an article does not imply confirmed compromise. All claims are attributed to external sources unless explicitly verified.
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


