WoundTech Breach Revealed: 160K Patients Exposed in Medical Leak

➤Summary
WoundTech breach allegations have emerged following a disturbing disclosure posted on a dark web forum, raising serious concerns about healthcare data protection and patient privacy. According to a post published on 01 February 2026 on Darkforums.st by an author using the alias “FulcrumSec,” an enormous volume of sensitive medical data allegedly belonging to WoundTech was accessed and partially released as a preview. The WoundTech breach reportedly affects more than 160,000 identified patients and close to a million individuals with partial identifiers, exposing deeply sensitive protected health information. Healthcare breaches carry unique consequences because medical data is permanent, intimate, and highly exploitable. This article breaks down what was exposed, why the impact is so severe, and what organizations and patients should understand moving forward 🏥.
Overview of the Alleged WoundTech Incident
The WoundTech breach centers on claims that attackers accessed approximately 650GB of data from a total inventory exceeding 3.8TB. The author describes this exposure as one of the most disturbing medical data incidents encountered, citing both scale and sensitivity. Unlike many breach claims that involve limited datasets, this incident allegedly includes full medical records, clinical imagery, and backend credentials.
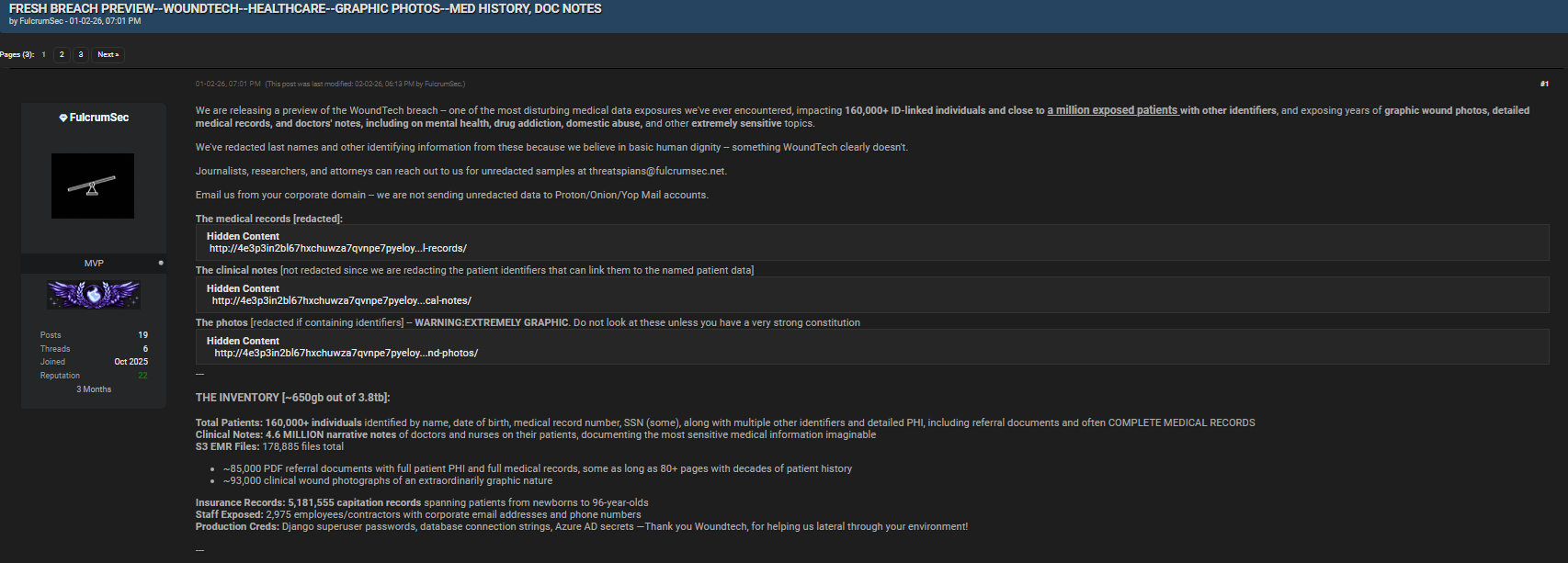
If validated, the WoundTech breach would represent a systemic failure across data storage, access controls, and credential management ⚠️.
Scope of Patient Data Reportedly Exposed
According to the disclosure, more than 160,000 patients were identified by full name, date of birth, medical record number, and in some cases Social Security numbers. The dataset reportedly extends beyond identifiers to include referral documents and complete longitudinal medical histories. Such information can be abused for identity theft, medical fraud, or extortion, and it cannot simply be “reset” like a password.
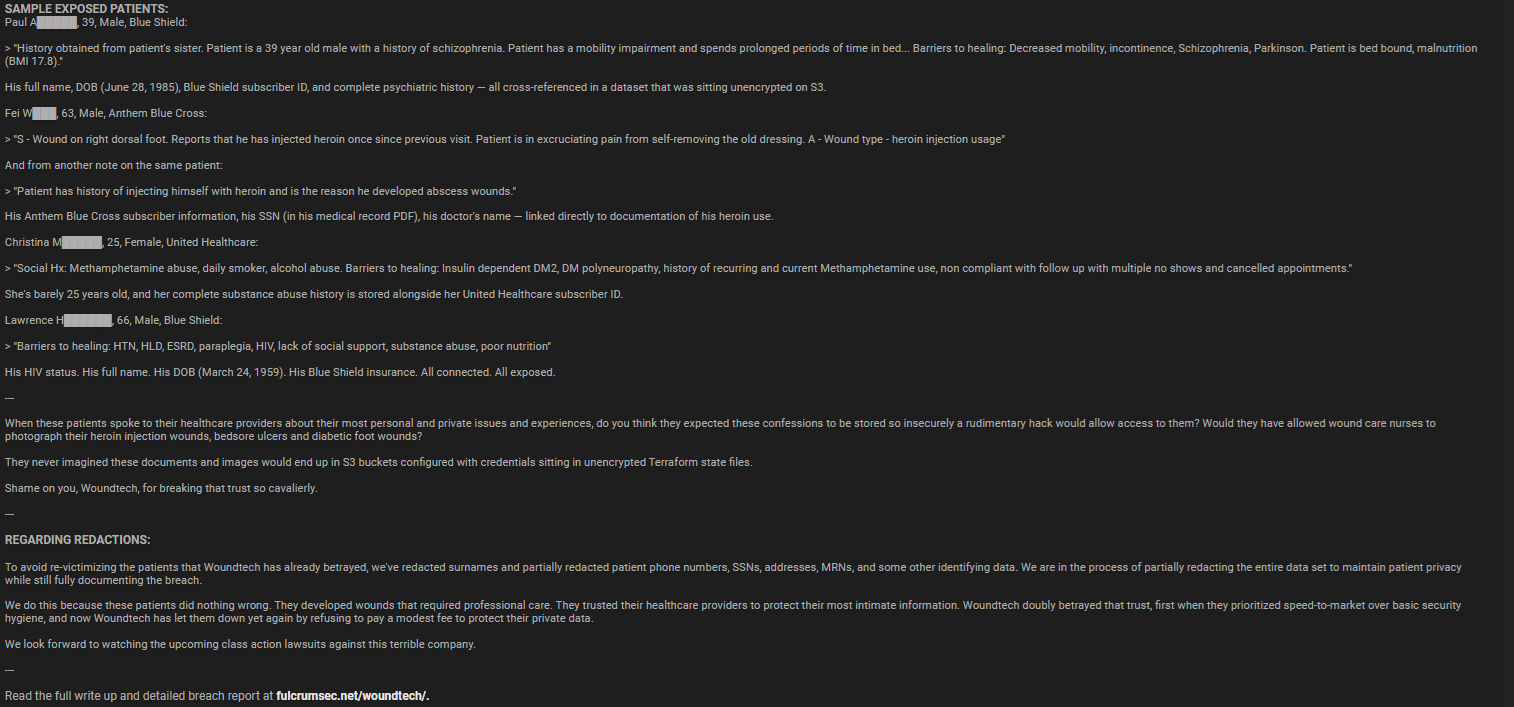
A healthcare data breach of this depth creates lifelong risk for affected individuals 📉.
Clinical Notes and Medical Narratives
One of the most alarming aspects of the WoundTech breach is the alleged exposure of 4.6 million clinical notes written by doctors and nurses. These narrative records document diagnoses, treatments, mental health conditions, substance abuse, domestic violence, and other highly sensitive topics. Clinical notes are among the most private forms of health information, and their exposure represents a profound violation of patient trust 🧠.
EMR Files, Referrals, and Graphic Images
The inventory also reportedly includes nearly 179,000 electronic medical record files and around 85,000 PDF referral documents, many spanning decades of patient history. In addition, approximately 93,000 clinical wound photographs were exposed, described as extraordinarily graphic in nature. Such content dramatically increases the ethical and psychological harm associated with the breach, especially if circulated or misused online 📸.
Insurance Records and Long-Term Exposure Risk
More than 5.1 million insurance capitation records were allegedly included, covering patients from newborns to individuals in their nineties. Insurance data can be exploited for billing fraud, false claims, and targeted scams. Combined with clinical data, it creates a comprehensive profile that criminals can monetize repeatedly over time. This elevates the WoundTech breach beyond a single incident into a long-term exposure scenario ⏳.
Staff and Credential Exposure
Beyond patient data, the breach allegedly exposed information linked to 2,975 employees and contractors, including corporate email addresses and phone numbers. More critically, the author claims access to production credentials such as Django superuser passwords, database connection strings, and Azure AD secrets. The disclosure even notes that these credentials enabled lateral movement through the environment, highlighting systemic security failures 🔑.
Author Statement and Ethical Claims
According to the author, a preview of the WoundTech breach was released with partial redaction of last names and other identifiers out of respect for human dignity. The statement argues that such care was absent in WoundTech’s handling of sensitive data. While motives can vary, this commentary underscores the reputational damage organizations face when trust in data stewardship is lost.
Is the WoundTech Breach Confirmed?
Is this breach officially confirmed?
At the time of writing, the claims are based on a detailed disclosure and preview release rather than an official notification from WoundTech. However, the specificity of the datasets, file counts, and credential details increases credibility. In healthcare, organizations should treat such disclosures as critical alerts and act immediately rather than waiting for confirmation.
Why Healthcare Breaches Are Especially Severe
A WoundTech breach has consequences that extend far beyond financial loss. Medical data is immutable and deeply personal. Exposure can lead to discrimination, emotional distress, and long-term exploitation. Regulatory scrutiny is also heightened, as healthcare organizations are subject to strict data protection requirements. The combination of PHI exposure and credential compromise places this incident among the most serious categories of healthcare data breach 🚑.
Practical Response Checklist for Healthcare Providers
Organizations facing a potential healthcare breach should follow a structured response approach:
- Immediately validate the scope of exposed systems and data
- Revoke and rotate all exposed credentials
- Engage forensic specialists to assess lateral movement
- Notify legal and compliance teams to assess obligations
- Prepare transparent communication plans for patients and staff 🧩
This checklist helps reduce chaos and demonstrates accountability.
The Role of Threat Intelligence and Monitoring
Early detection of underground disclosures is essential in incidents like the WoundTech breach. Proactive dark web monitoring allows organizations to identify mentions of proprietary data before widespread abuse occurs. Insights from dark web monitoring reports often guide incident response priorities and notification decisions. A comprehensive dark web monitoring solution supports continuous visibility, while Dark Web Monitoring for MSSP offerings enable managed providers to protect multiple healthcare clients efficiently 🔍.
Learning from Past Healthcare Incidents
Previous healthcare breaches show that secondary attacks often follow initial exposure, including phishing campaigns targeting patients and staff. Attackers may reuse medical data months or years later. Continuous monitoring, staff awareness, and long-term identity protection services are therefore critical components of post-breach strategy 🔄.
Trusted Sources and Further Reading
Security analysts and healthcare leaders can follow ongoing research and breach analysis through dedicated cyber intelligence platforms like Darknetsearch.com. The original disclosure details were published by the author at https://fulcrumsec.net/woundtech/, providing context on the nature of the alleged exposure.
Conclusion: A Wake-Up Call for Healthcare Security
The alleged WoundTech breach illustrates the devastating impact of inadequate security controls in healthcare environments. Exposure of complete medical records, graphic imagery, and production credentials represents a worst-case scenario for patient privacy and organizational trust. Whether confirmed or still under investigation, the warning signs demand immediate action. By investing in robust security practices, proactive intelligence, and transparent response strategies, healthcare organizations can reduce harm and rebuild confidence 🛡️.
Discover much more in our complete guide
Request a demo NOW
*Disclaimer: DarknetSearch reports on publicly available threat-intelligence sources. Inclusion of an organization in an article does not imply confirmed compromise. All claims are attributed to external sources unless explicitly verified.
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.

