RG Electric Data Breach Revealed: 500GB Database Listed for $15k

➤Summary
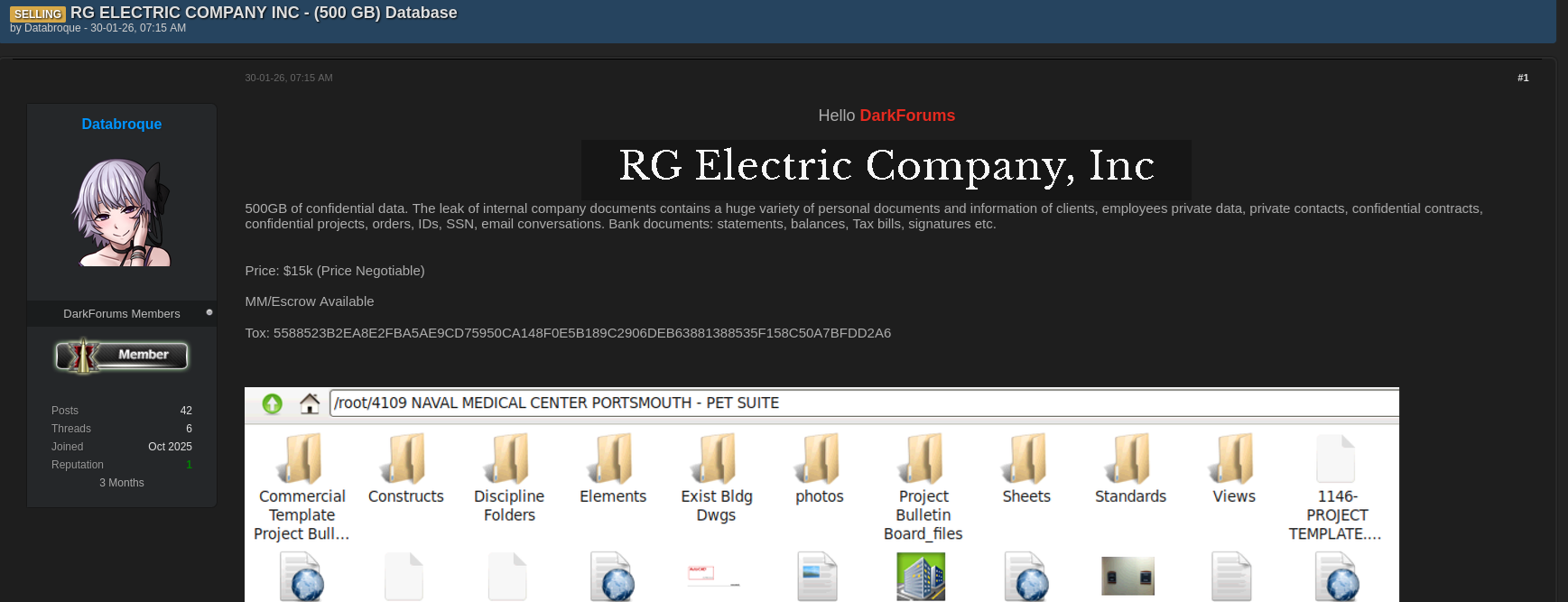
RG Electric data breach reports have surfaced after a threat actor claimed to be selling a massive database allegedly belonging to RG Electric Company Inc on a dark web forum. According to the listing, 500GB of highly sensitive corporate and personal data is being offered for $15,000, with the price marked as negotiable. The post, published on 30 January 2026 by a user known as “Databroque” on Darkforums.st, describes a wide-ranging collection of internal company documents, employee and client records, and detailed financial information. Incidents like this highlight how quickly confidential business data can be weaponized once it enters underground marketplaces, exposing organizations to financial loss, regulatory penalties, and long-term reputational damage 😟. Below is a structured analysis of the alleged incident, its potential impact, and the defensive steps organizations should take right now.
Overview of the Alleged RG Electric Database Sale
The RG Electric data breach allegation centers on a single forum post advertising what is described as a full internal database dump. The seller claims the archive contains approximately 500GB of data extracted from internal systems. While independent verification is ongoing, the level of detail outlined in the sales description mirrors previous confirmed corporate leaks. The RG Electric Company Inc database sale is being marketed directly to cybercriminal buyers seeking high-value financial and identity data 💾.
Such listings often precede fraud campaigns, identity theft operations, or extortion attempts.
What Data Is Allegedly Exposed
According to the forum post, the leaked archive contains a broad range of sensitive information. This includes internal corporate documents, confidential contracts, private project files, and order records. More concerning is the alleged exposure of personally identifiable information belonging to employees and clients, including IDs, Social Security numbers, private contact details, and email conversations 📧. Financial records are also listed, such as bank statements, balances, tax bills, and signed documents. In past incidents, similar datasets have been used to enable business email compromise, tax fraud, and synthetic identity creation.
Why Dark Web Forum Sales Are So Dangerous
A dark web forum sale transforms stolen data into a commodity. Once listed, information can be copied, resold, or bundled with other leaks. The RG Electric data breach, if validated, would not be a single-point event but a long-term exposure risk. Even if the original listing is removed, copies may persist indefinitely. Underground buyers often specialize, meaning financial data can be sold to one group while identity records go to another, amplifying the damage 📉.
Timeline and Threat Actor Profile
The post advertising the data was published on 30 January 2026 by the user “Databroque.” While aliases change frequently, sellers who provide detailed inventories and flexible pricing often signal confidence in the dataset’s authenticity. This pattern has been observed in multiple corporate breach cases over the past few years. The use of a well-known underground forum increases visibility and buyer trust, accelerating potential misuse ⏱️.
Key Risks for RG Electric and Affected Individuals
The consequences of an RG Electric data breach extend far beyond immediate remediation costs. Affected individuals face heightened risks of identity theft, fraudulent account creation, and targeted phishing. For the company, exposure can trigger regulatory scrutiny, civil litigation, and contractual disputes with partners. Operational disruption is also likely if attackers leverage internal documents to plan follow-on attacks or extortion attempts ⚠️.
Is This Confirmed and What Should Be Done Now?
Is the data breach confirmed?
At the time of writing, the listing represents an alleged breach based on a forum advertisement, not an official disclosure. However, history shows that detailed listings on underground markets often correlate with real incidents. Organizations should act on credible indicators rather than wait for confirmation. Early investigation and containment can significantly reduce downstream damage.
How Threat Intelligence Teams Track These Listings
Security teams increasingly rely on structured intelligence collection to detect underground activity early. Monitoring dark web forum sale patterns allows analysts to correlate new listings with known victims. This is where dark web monitoring plays a critical role, enabling rapid identification of exposed brand names or proprietary data mentions 🔍. Insights derived from dark web monitoring reports often inform incident response decisions before attackers act. Integrating a scalable dark web solution helps organizations move from reactive to proactive defense, while Dark Web Monitoring for MSSP providers supports managed detection at scale.
Practical Checklist for Incident Response
Organizations facing a potential data exposure should follow a clear response framework:
- Initiate an internal investigation to validate the dataset
- Preserve logs and forensic evidence immediately
- Reset credentials and review access controls
- Notify legal and compliance teams to assess obligations
- Prepare transparent communications for stakeholders 🧩
This checklist can help limit escalation and demonstrate due diligence.
Regulatory and Legal Implications
If confirmed, the RG Electric data breach could trigger reporting requirements under data protection laws, depending on jurisdiction. Exposure of SSNs and financial records typically falls under high-risk categories, increasing the likelihood of mandatory notifications and penalties. Regulatory bodies often evaluate response speed and transparency when determining enforcement actions 📜.
Learning from Similar Cases
Historical analysis shows that companies affected by underground data sales often experience secondary attacks months later. Criminals reuse archived data for credential stuffing or targeted social engineering. Continuous monitoring and long-term mitigation strategies are therefore essential, not optional.
Resources for Ongoing Threat Awareness
Staying informed about underground activity helps organizations prepare. Analysts regularly publish research and alerts on dark web intelligence platforms including case studies on corporate leaks and marketplace trends. You can also explore intelligence briefings, incident analyses and to understand how similar cases unfolded in dark web monitoring platforms 📚. For broader investigative context, Krebs on Security remains a highly reputable external resource for breach analysis and threat reporting.
Conclusion: Turning Intelligence into Action
The alleged sale of a 500GB corporate archive underscores how quickly sensitive data can surface in criminal marketplaces. The RG Electric data breach case illustrates the cascading risks that follow when internal documents, personal identities, and financial records are exposed. Whether confirmed or not, credible underground listings demand immediate attention. By combining early intelligence, structured response, and continuous monitoring, organizations can reduce impact and protect stakeholders. Don’t wait for official confirmation to act—preparedness is the strongest defense 🛡️.
Discover much more in our complete guide
Request a demo NOW
Disclaimer: DarknetSearch reports on publicly available threat-intelligence sources. Inclusion of an organization in an article does not imply confirmed compromise. All claims are attributed to external sources unless explicitly verified.
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


