Mobelaris United Kingdom Database Breach: Key Impacts

➤Summary
Mobelaris United Kingdom Database incidents have quickly become a critical topic in cybersecurity discussions, especially after sensitive commercial and customer information surfaced on underground forums. This Darknet article examines the breach in depth, explaining what happened, what data was compromised, and why this exposure matters for businesses and consumers alike. Understanding the scope of the Mobelaris United Kingdom Database compromise helps organizations improve data breach detection and strengthen their security posture before similar incidents occur. In today’s threat landscape, visibility into leaked databases is essential for informed risk management and proactive defense strategies 🔍
Overview of the Mobelaris United Kingdom Database Incident
The Mobelaris United Kingdom Database was reportedly advertised on Breachforums.bf, a well-known cybercrime discussion platform. According to the forum post, authored by a user named “Satanic” and published on 10 January 2026, the breach involved extensive order and customer records.
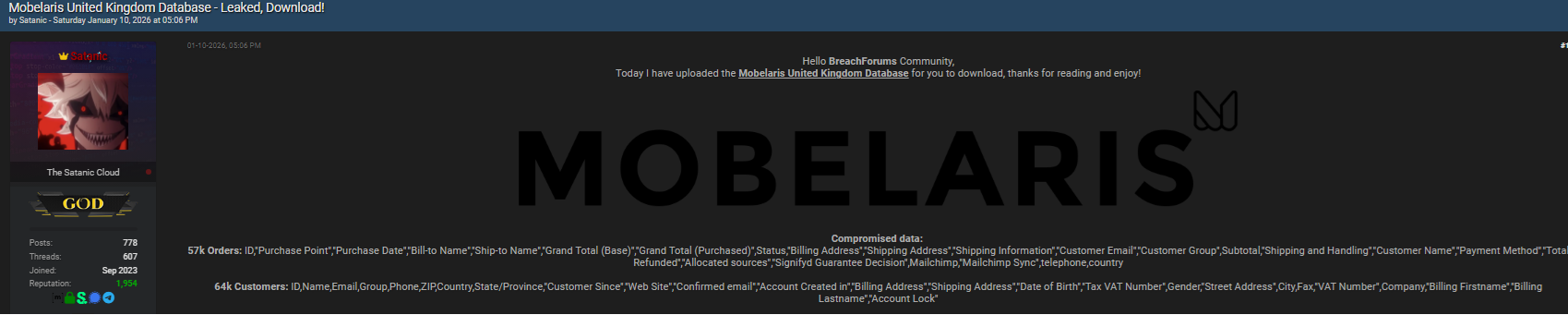
Such incidents highlight how e-commerce platforms remain lucrative targets for threat actors seeking monetizable data 💻 The Mobelaris United Kingdom Database exposure aligns with broader trends seen across retail-focused cyber incidents in recent years.
Source and Context of the Leak
Forum: Breachforums.bf
Author: Satanic
Published Date: 10 January 2026
This leak was shared within an underground community known for trading compromised databases. Monitoring sources like these is a common practice for security teams that compare dark web monitoring tools and intelligence feeds. Dark web monitoring platforms regularly document similar exposures, helping analysts track patterns across industries.
Compromised Orders Data Explained
The breach reportedly included approximately 57,000 order records. These entries contained detailed transactional data such as purchase dates, billing and shipping names, order totals, payment methods, and customer contact details. From a risk perspective, the presence of billing addresses and emails significantly increases the likelihood of phishing and social engineering campaigns 📧 The Mobelaris United Kingdom Database orders dataset also listed shipping information and refund data, which could be exploited for fraud or identity misuse.
Customer Records and Personal Information Exposure
Beyond orders, around 64,000 customer records were allegedly compromised. These included names, emails, phone numbers, addresses, dates of birth, VAT numbers, and account status fields. The depth of this dataset places the Mobelaris United Kingdom Database incident among higher-risk retail breaches. According to guidance from reputable sources like https://www.haveibeenpwned.com/, exposure of combined identity and contact data dramatically raises downstream attack potential.
Why This Breach Matters for Businesses
Why should organizations care about a single retail database leak? Because incidents like the Mobelaris United Kingdom Database breach demonstrate how aggregated customer data becomes a long-term liability once exposed. Attackers often resell or reuse such datasets months or even years later. This is why dark web reports and ongoing surveillance are now considered essential components of modern cybersecurity programs 🛡️
The Role of Dark Web Intelligence
Organizations increasingly rely on dark web solutions to detect early signs of compromise. By scanning underground forums and marketplaces, analysts can identify leaked assets before they are widely abused. A well-documented case study dark web monitoring approach shows that early detection can reduce response time and regulatory impact. Dark web monitoring platforms provide valuable insights into how leaked databases circulate within criminal ecosystems 🔐
Practical Tip: Breach Response Checklist
Here is a simple checklist businesses can apply after learning about incidents like the Mobelaris United Kingdom Database breach:
- Verify whether your organization or customers are affected
- Reset credentials associated with exposed emails
- Notify impacted users transparently
- Review payment fraud indicators
- Enhance monitoring for suspicious activity
This proactive response framework supports faster containment and recovery ✅
Regulatory and Compliance Considerations
Retail breaches involving UK data may trigger GDPR obligations, including breach notification and potential fines. The Mobelaris United Kingdom Database exposure underscores the importance of maintaining strong access controls and encryption. Regulators increasingly expect companies to demonstrate not only prevention but also continuous monitoring and incident readiness 📜
Expert Insight
“Data breaches are no longer isolated events; they are part of an ongoing threat cycle,” notes a cybersecurity analyst cited in multiple dark web reports. “Organizations that invest in continuous intelligence gain a measurable advantage in reducing breach impact.” This perspective reinforces why monitoring leaked databases is now a strategic necessity rather than an optional add-on.
How Consumers Can Protect Themselves
Affected customers should remain vigilant. Changing passwords, enabling multi-factor authentication, and monitoring financial statements are essential steps. Awareness of incidents like the Mobelaris United Kingdom Database breach empowers individuals to reduce personal risk and respond quickly if suspicious activity occurs 🔑
Conclusion and Call to Action
The Mobelaris United Kingdom Database breach serves as a clear reminder of how valuable and vulnerable customer data remains in the digital economy. By understanding what data was exposed, how it surfaced, and how similar threats evolve, organizations can better prepare for future incidents. Continuous intelligence, proactive monitoring, and informed response planning are no longer optional in today’s environment. Discover much more in our complete guide and Request a demo NOW to strengthen your organization’s visibility and resilience 🚀
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourselfsssss.


