Government Data Breach Exposes 98K Records in Argentina

➤Summary
Government data breach incidents continue to shape the global cybersecurity landscape, and the exposure tied to OSSESANJUAN.COM.AR in early 2026 stands as a critical example of how public sector systems can be compromised at scale. This case involves a leaked MySQL SQL dump allegedly shared on BreachForums, exposing sensitive records from an Argentine government-related website. With more than 98,000 rows across 127 tables and two schemas, the breach reveals risks tied to data exposure, credential logging, and document storage. 🛑
This article provides a clear, structured analysis of the incident, the type of data involved, the potential impact on citizens and institutions, and why this event matters for organizations monitoring dark web leak activity. It also connects the dots between public sector security failures and the need for proactive public sector threat intelligence to identify emerging threats early. 🔍
Overview of the OSSESANJUAN.COM.AR Leak
The incident centers on OSSESANJUAN.COM.AR, a government-associated platform in Argentina. According to forum disclosures, the dataset was published on BreachForums.bf by a user known as “Solonik” on January 11, 2026. The release is described as a government SQL dump leak, packaged in MySQL (.sql) format.
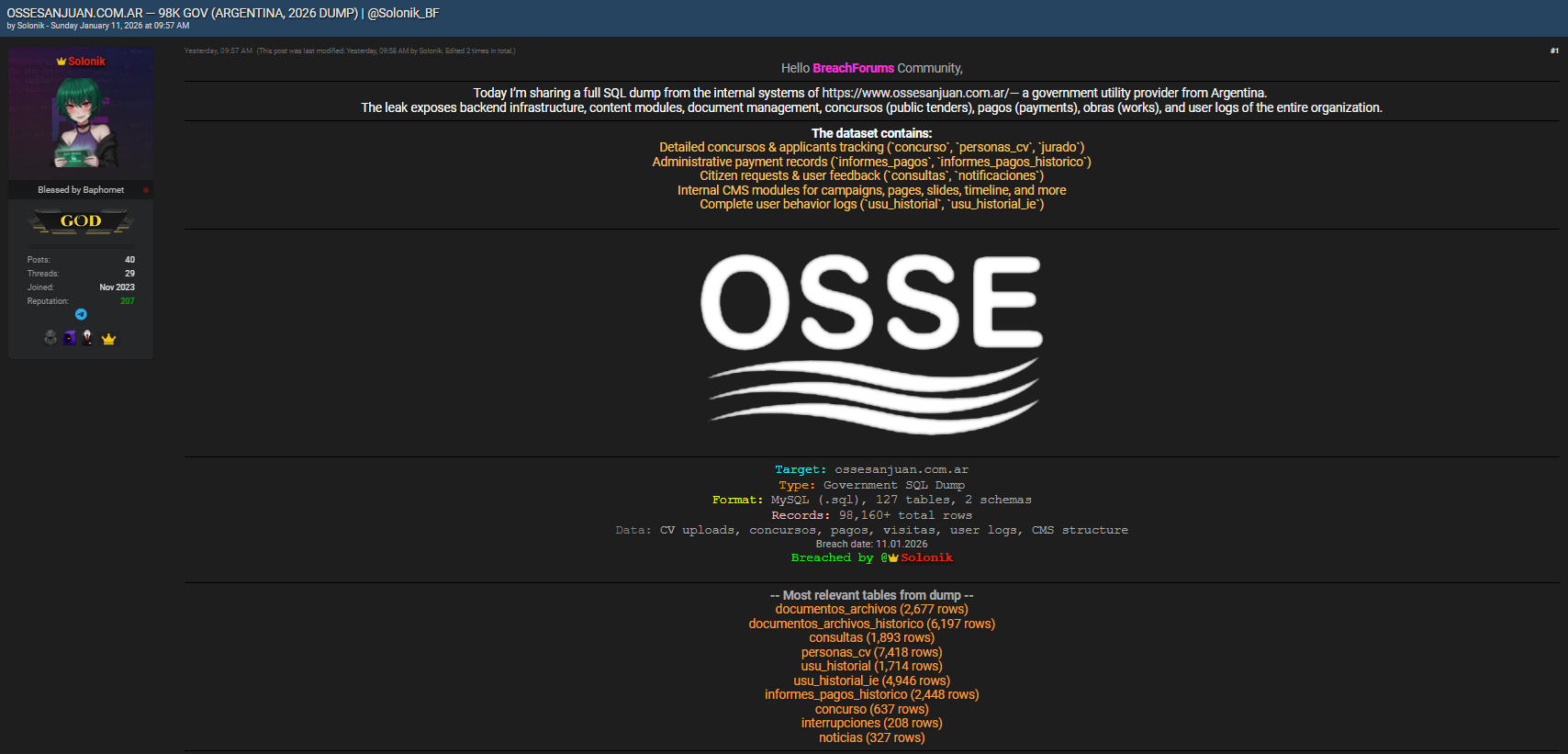
The exposed dataset reportedly includes 98,160+ total rows distributed across two schemas and 127 database tables. This places the event among notable public sector cybersecurity incidents due to both scale and data sensitivity. The compromised content spans operational systems, internal logs, and citizen-facing services, increasing the likelihood of misuse. 🚨
What Data Was Compromised
The leaked database appears to contain a wide range of structured information. Among the most relevant tables are documentos_archivos with 2,677 rows and documentos_archivos_historico holding 6,197 rows, suggesting long-term document retention. Additional tables include personas_cv with 7,418 rows, consultas with 1,893 rows, and multiple user activity logs such as usu_historial and usu_historial_ie.
Financial and administrative exposure is also evident through informes_pagos_historico, concurso entries, noticias, interrupciones, and CMS-related structures. This combination indicates a deep data exposure affecting operational continuity, personal records, and historical archives. 📂
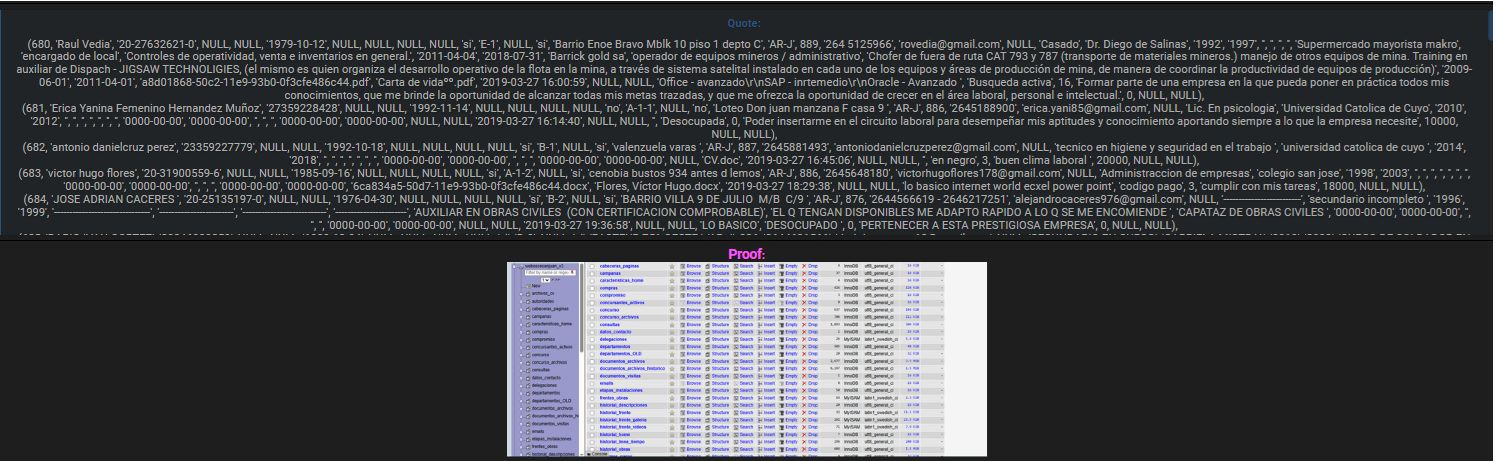
Such diversity of compromised information increases the potential for identity misuse, social engineering, and reputational damage.
Why This Government Data Breach Matters
A government data breach has implications far beyond a single website. When public institutions lose control of citizen data, trust erodes and regulatory scrutiny intensifies. In this case, CV uploads, payment histories, and internal logs could be exploited for targeted phishing or fraud.
Public sector systems often integrate multiple services, meaning one compromised database can serve as a pivot point for broader attacks. This incident highlights weaknesses in access controls, patch management, or monitoring processes. From a strategic viewpoint, it reinforces why public sector security must evolve alongside threat actor capabilities. 🧠
Connection to Dark Web Leak Ecosystems
BreachForums has become a central hub for sharing leaked databases, including government-related material. Once published, such datasets are indexed, mirrored, and resold across underground channels. Analysts who compare dark web monitoring approaches often note that early detection on forums like this can significantly reduce downstream damage.
Specialized dark web solutions focus on tracking these disclosures, correlating actor behavior, and validating leaked samples. This event serves as a case study dark web monitoring professionals reference when explaining how quickly public sector data can spread after initial publication. 🌐
Technical Characteristics of the SQL Dump
From a technical standpoint, the MySQL dump format suggests direct database access or successful exploitation of an application vulnerability. The presence of CMS structure tables indicates that the backend content management system may have been a key entry point.
The inclusion of user logs and historical tables implies insufficient segmentation between production data and audit records. This architecture increases the blast radius of any intrusion. For defenders, understanding these structural weaknesses is essential for improving data breach detection capabilities and preventing similar exposures in the future. ⚙️
Real-World Risks for Affected Individuals
What does this mean for citizens whose data may be included? The answer is straightforward: increased risk of targeted scams, credential stuffing, and identity fraud. CV data can be weaponized for social engineering, while payment histories add credibility to fraudulent communications.
Question: Can leaked government data be reused years later?
Answer: Yes, archived datasets often resurface repeatedly, making long-term monitoring critical. ⏳
Lessons for Public Sector Cybersecurity
This incident reinforces several lessons. First, routine security assessments and patching are non-negotiable. Second, logging systems should never be fully accessible from public-facing applications. Third, continuous monitoring of underground forums is essential to identify leaks before they escalate.
According to cybersecurity journalist Brian Krebs of KrebsOnSecurity, public sector organizations are increasingly targeted because attackers assume slower response times and outdated infrastructure. His analysis aligns with patterns seen in this Argentine breach. 🛡️
Practical Checklist for Organizations
To reduce exposure to similar incidents, consider the following practical checklist:
- Audit database access permissions regularly
- Isolate historical and log tables from live systems
- Encrypt sensitive fields such as CV documents and payment data
- Implement automated alerts for suspicious exports
- Review external intelligence sources and dark web reports for early warnings
- Conduct incident response simulations at least annually
This structured approach improves resilience and helps organizations respond faster when leaks occur. ✅
Strategic Impact and Industry Perspective
From an industry perspective, the OSSESANJUAN.COM.AR incident illustrates how a single SQL dump can trigger regulatory, legal, and reputational consequences. It also demonstrates why integrating proactive intelligence into security programs is no longer optional.
Security leaders increasingly rely on specialized monitoring to bridge the gap between internal defenses and external threat actor activity. Without this visibility, organizations may learn about breaches only after data is widely circulated. 🔎
Conclusion and Call to Action
The 2026 exposure of OSSESANJUAN.COM.AR data is a clear reminder that government data breach risks remain high, especially when legacy systems and limited monitoring converge. With over 98,000 records exposed, the incident underscores the importance of visibility, preparedness, and continuous intelligence gathering.
To stay ahead of emerging threats and understand how similar incidents unfold across underground ecosystems, proactive education is essential. 📢
Discover much more in our complete guide
Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourselfsssss.

