Kintecktong breach in Singapore: 7 key facts

➤Summary
Singapore data breach disclosures continue to highlight critical weaknesses in healthcare cybersecurity, and the recent exposure linked to kintecktong.com.sg is a stark reminder of what is at stake. The Singapore data breach surfaced on BreachForums.bf, where an actor known as “lulzintel” published details on 07.01.2026, claiming access to approximately 150,000 patient records. This incident involves deeply sensitive personal and medical information, placing it among the most serious healthcare-related leaks in the region.

As Singapore maintains one of Asia’s most advanced digital health ecosystems, breaches of this nature raise urgent concerns around trust, regulatory compliance, and long-term patient safety. Understanding the scope, implications, and defensive lessons from this event is essential for healthcare providers and security teams alike. ⚠️
Overview of the Kintecktong Incident
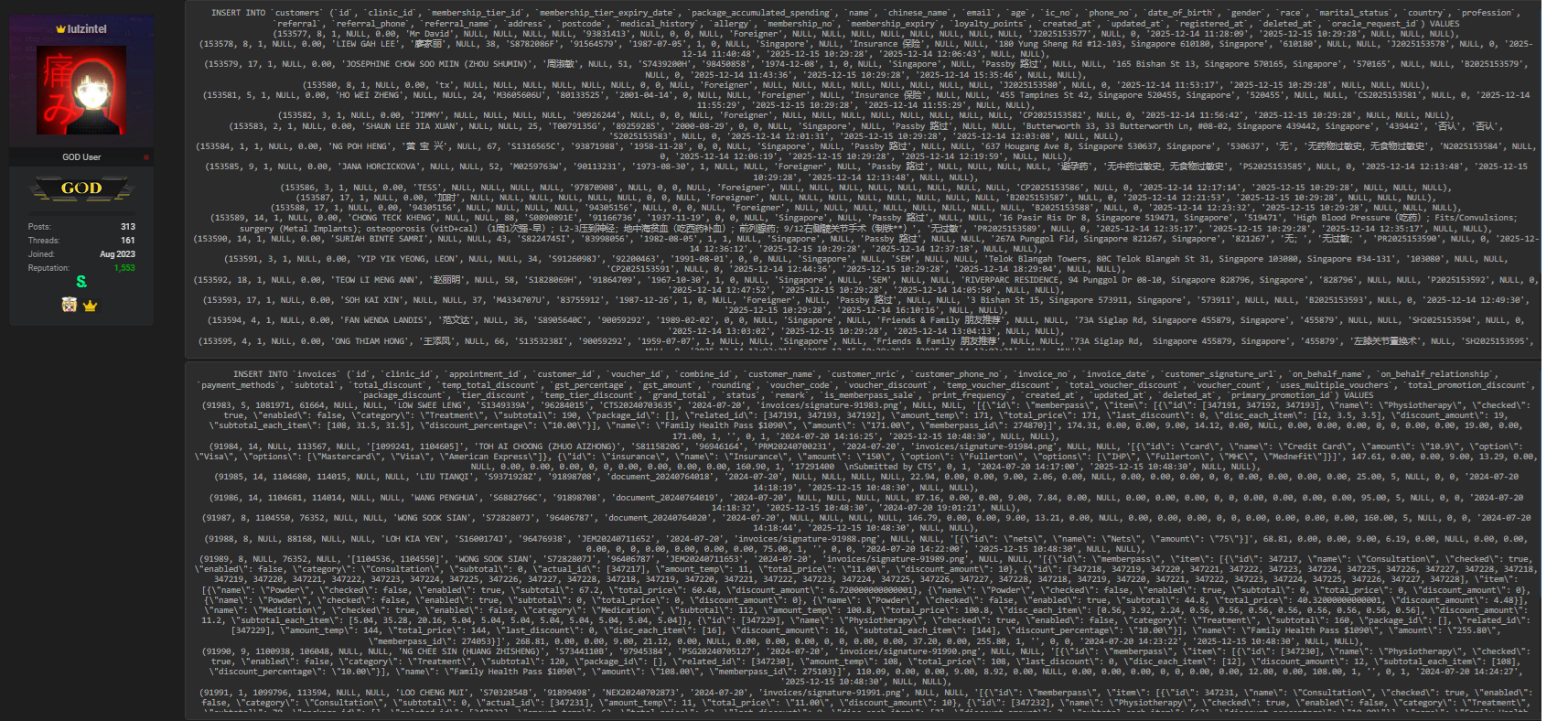
The alleged compromise targets kintecktong.com.sg, a Singapore-based healthcare service provider. According to the forum post, the dataset includes structured SQL-style tables such as customers and invoices, indicating backend database access rather than a superficial scrape. The Singapore data breach narrative points to unauthorized extraction of records tied to clinics, appointments, billing, and membership systems. This structure mirrors previous healthcare incidents where attackers monetized access by leaking full relational datasets. The publication on BreachForums.bf suggests intent to distribute or sell the data within underground communities. 🗂️
What Data Was Exposed in the Breach
The compromised records reportedly include names, Chinese names, email addresses, phone numbers, NRIC/IC numbers, dates of birth, addresses, and detailed medical information such as medical history and allergies. Financial and transactional data appear in the invoices table, including invoice numbers, payment methods, discounts, and customer signatures. This combination of identity, contact, medical, and billing data dramatically increases risk. In a Singapore data breach of this scale, the exposure is not limited to privacy violations but extends to identity fraud, medical fraud, and targeted scams. 📄
Why Healthcare Breaches Carry Higher Risk
Healthcare data is uniquely sensitive because it cannot be easily changed or reissued. Unlike passwords, medical histories and identity numbers remain static over a lifetime. A single breach can therefore have long-term consequences for patients. In Singapore, where digital health records are widely integrated, such leaks undermine confidence in healthcare digitization. This is why healthcare data breach detection is treated as a top priority by regulators and security leaders. Attackers understand this value, making clinics and medical platforms high-value targets. 🏥
BreachForums and Underground Data Distribution
BreachForums.bf has emerged as a central hub for announcing and validating data leaks. Threat actors often publish samples or database schemas to prove authenticity. Monitoring these platforms allows defenders to compare dark web monitoring approaches and assess how quickly sensitive data spreads. Once posted, datasets are frequently mirrored, repackaged, or bundled with other leaks. This makes early detection critical, as response time directly influences impact. Analysts rely on dark web solutions to track such activity and correlate it with internal alerts. 🌐
Correlation With Regional Healthcare Breaches
This incident echoes patterns seen in other Southeast Asian healthcare leaks. A recent case involving a regional hospital demonstrated how hundreds of thousands of medical records were exposed through inadequate access controls and later circulated underground. That event, analyzed in depth by industry researchers, showed how delayed detection amplified damage. The Singapore data breach at Kintecktong follows a similar trajectory: backend access, structured data extraction, and forum publication. These parallels highlight systemic challenges in healthcare cybersecurity across the region. 🔍
Regulatory and Compliance Implications in Singapore
Singapore enforces strict obligations under the Personal Data Protection Act (PDPA), particularly for organizations handling sensitive health information. A breach involving medical records can trigger investigations, financial penalties, and mandatory remediation. Beyond legal consequences, reputational damage can be severe. Patients expect confidentiality as a core component of care. Failure to protect it erodes trust and can lead to long-term loss of business. Regulators increasingly expect proactive monitoring and rapid disclosure once incidents are confirmed. 🏛️
How Detection and Monitoring Make a Difference
Early identification of underground exposure can significantly reduce harm. Effective data breach detection combines internal logging, anomaly detection, and external intelligence. Security teams that regularly review dark web reports can identify leaked assets before they are widely abused. Some organizations run simulations and tabletop exercises based on real incidents to refine response plans. These practices are no longer optional in healthcare environments with complex digital infrastructures. 🛡️
Practical Checklist for Healthcare Providers
To reduce the likelihood and impact of similar incidents, healthcare organizations should implement the following measures:
• Restrict database access using least-privilege principles
• Encrypt sensitive fields at rest and in transit
• Monitor for abnormal query volumes or export behavior
• Track underground forums and marketplaces for early warning signs
• Maintain an incident response plan aligned with regulatory requirements
This checklist supports resilience and demonstrates due diligence in protecting patient data. ✅
Expert Perspective on Healthcare Data Leaks
Cybersecurity specialists consistently warn that healthcare remains one of the most targeted sectors. One regional expert noted, “Attackers know that medical data carries high value and low tolerance for exposure, making it a powerful leverage point.” This insight explains why incidents like the Kintecktong case attract rapid attention underground. Dark web monitoring platforms provide contextual analysis that helps organizations understand how leaked healthcare data is traded and reused. 📊
Learning From the Kintecktong Data Breach
The Kintecktong incident underscores the importance of visibility beyond the perimeter. Once data appears on a forum, containment becomes exponentially harder. Continuous intelligence gathering enables organizations to respond with clarity rather than speculation. Reviewing similar breach case analyses and threat intelligence insights available at Darknetsearch.com helps teams benchmark response timelines and mitigation strategies. Awareness, preparation, and collaboration are key to reducing future risk. 🚀
Conclusion and Call to Action
This Singapore data breach involving Kintecktong is a powerful reminder that healthcare organizations must treat cybersecurity as a core component of patient care. By investing in monitoring, governance, and intelligence-driven defense, providers can better protect sensitive records and maintain public trust. Stay informed with reliable intelligence resources and strengthen your security posture against emerging threats. Discover much more in our complete guide. Request a demo NOW.
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourselfsssss.


