Micro.fuse.co.id Data Breach: 7 Key Impacts Revealed

➤Summary
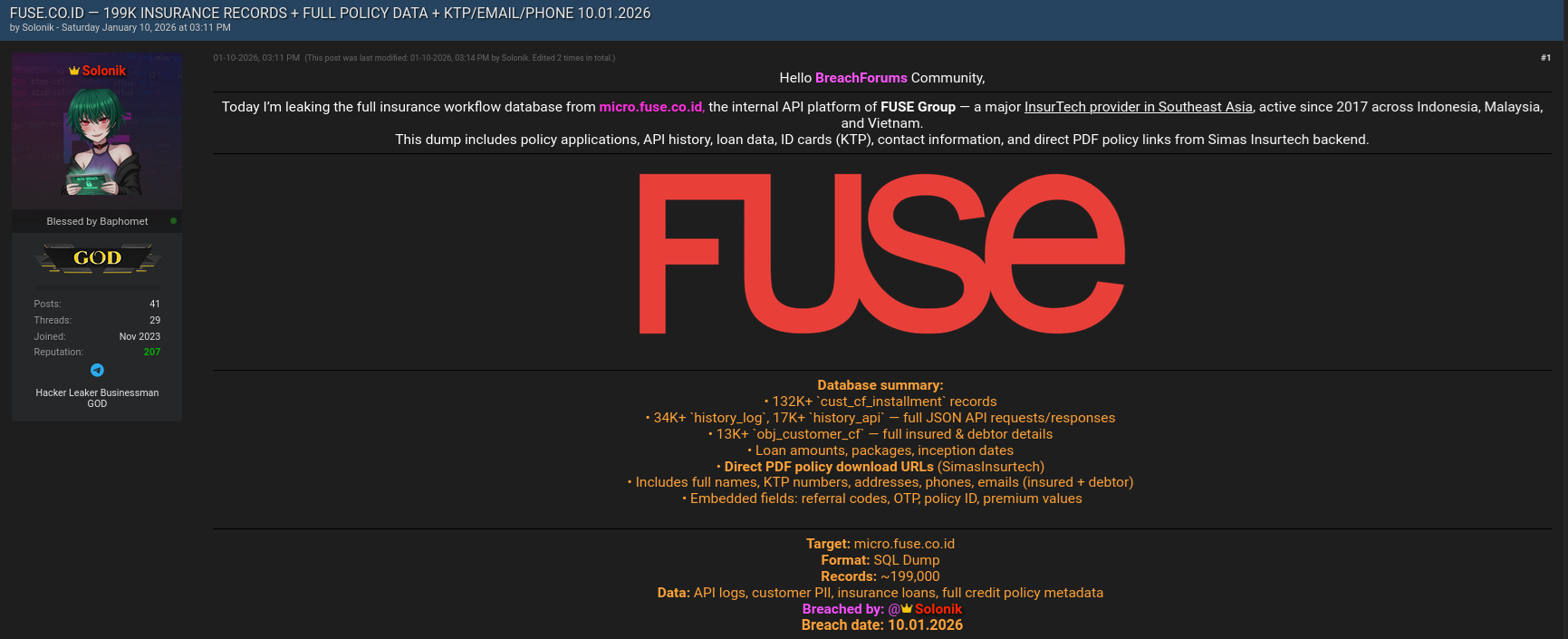
The micro.fuse.co.id data breach has emerged as one of the most concerning cyber incidents affecting Indonesia’s digital lending and insurance ecosystem in early 2026. First disclosed on Breachforums.bf by the threat actor Solonik, the incident reportedly occurred on 10.01.2026 and involved the exposure of nearly 199,000 records in SQL dump format. This micro.fuse.co.id data breach is not just another data leak; it reveals systemic weaknesses in API security, customer data handling, and third-party insurance integrations. With sensitive personal and financial information now circulating in underground communities, the incident underscores the urgent need for financial platforms to strengthen financial sector cybersecurity by adopting proactive data breach detection capabilities and maintaining continuous threat intelligence programs.
Understanding what happened, what data was compromised, and how similar risks can be mitigated is critical for organizations and users alike 🔐💥
What Happened in the micro.fuse.co.id Incident
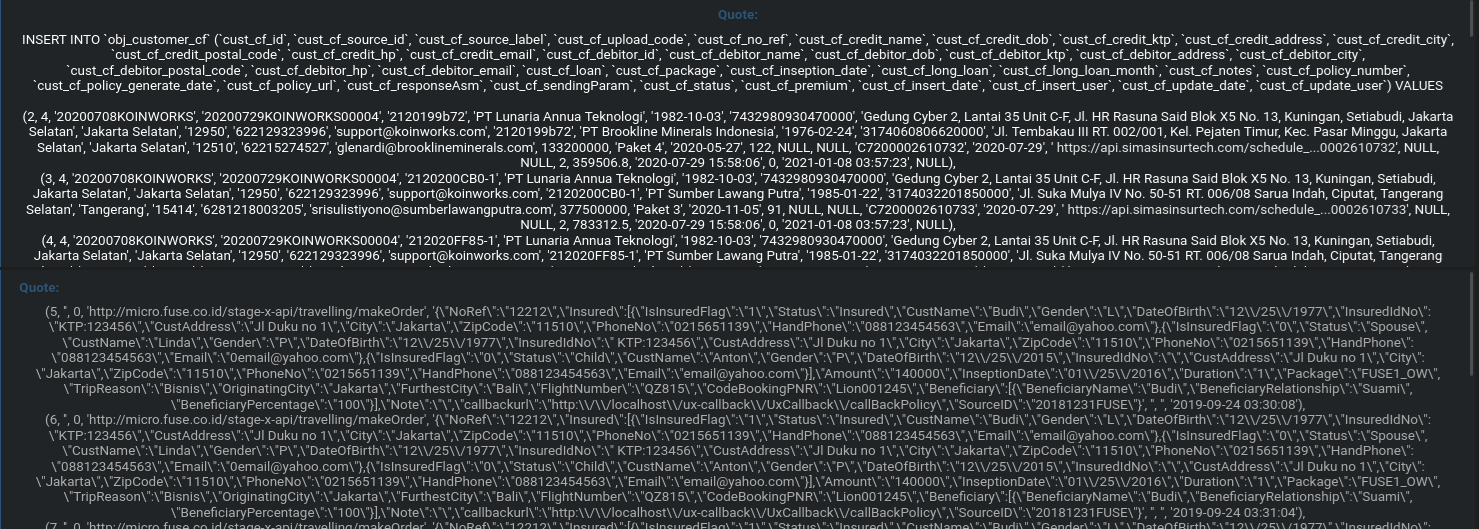
According to forum disclosures, the attacker gained access to backend databases linked to micro.fuse.co.id, a platform associated with microfinance and insurance-linked loan services. The compromised assets were shared as an SQL dump, making them easy to parse and reuse. This micro.fuse.co.id data breach allegedly originated from insecure API endpoints, as evidenced by the exposure of full JSON request and response logs. Such logs often contain authentication tokens, referral identifiers, and operational metadata, which significantly amplify the impact of a breach 😟
Scope of the Compromised Data
The scale of the incident is substantial and well-documented by the database summary released alongside the leak. A total of approximately 199,000 records were exposed, spanning multiple tables and functional datasets. The compromised data includes:
• 132,000+ cust_cf_installment records detailing customer installment schedules
• 34,000 history_log entries and 17,000 history_api records containing raw API traffic
• 13,000 obj_customer_cf entries with full insured and debtor profiles
• Loan amounts, insurance packages, inception dates, and premium values
• Direct PDF policy download URLs linked to SimasInsurtech
• Embedded fields such as OTP values, referral codes, policy IDs, and contact metadata
This breadth of information makes the micro.fuse.co.id data breach particularly dangerous because it combines financial, identity, and insurance data in one dataset 📄⚠️
Why API Logs and SQL Dumps Are High Risk
One critical lesson from this incident is the risk associated with storing verbose API logs. Full JSON request and response data often contain personally identifiable information (PII), session identifiers, and operational secrets. When such logs are left unencrypted or exposed through misconfigured access controls, attackers can reconstruct user journeys, abuse endpoints, and perform large-scale fraud. In this case, the SQL dump format lowered the barrier for exploitation, enabling quick indexing and resale across multiple forums. This pattern has been observed in other financial sector leaks tracked in dark web reports 🧠
Types of Personal Data Exposed
The micro.fuse.co.id data breach exposed highly sensitive PII, including full names, Indonesian KTP numbers, residential addresses, phone numbers, and email addresses for both insured parties and debtors. Combined with loan and policy metadata, this information can be weaponized for phishing, identity theft, account takeover, and social engineering attacks. The presence of direct policy PDF URLs further escalates the threat, as attackers can access official documents that appear legitimate to victims. This raises a crucial question: can affected users be targeted even if their financial accounts remain secure? The answer is yes—document-based fraud often bypasses traditional security controls 📌
Connection to Breachforums and the Underground Market
The publication of this leak on Breachforums.bf signals a high likelihood of redistribution. Historically, datasets first shared on such forums are quickly mirrored, repackaged, and sold in private channels. Analysts who compare dark web monitoring feeds often observe that financial service leaks gain traction faster due to their monetization potential. Once indexed, the data becomes difficult to contain, underscoring the need for rapid incident response and transparent disclosure. Dark web monitoring platforms regularly track similar forum-based exposures to help organizations understand threat actor behavior 🔎
Business and Regulatory Impact
Beyond individual harm, the micro.fuse.co.id data breach carries significant business and regulatory implications. Financial platforms operating in Indonesia are subject to data protection and consumer privacy obligations. Exposure of national ID numbers and financial records can trigger regulatory scrutiny, reputational damage, and potential fines. According to guidance from reputable authorities such as the U.S. Federal Trade Commission, organizations handling sensitive financial data must implement reasonable security measures and breach notification procedures. Failure to do so can erode user trust and partner relationships at scale 📉
Practical Checklist: How Organizations Can Reduce Similar Risks
To prevent incidents like the micro.fuse.co.id data breach, organizations should implement a layered security approach:
- Audit all API endpoints for authentication and authorization flaws
- Minimize logging of sensitive fields such as OTPs and ID numbers
- Encrypt databases and backups, including SQL dumps
- Continuously monitor underground forums using dark web solutions
- Conduct regular penetration testing and configuration reviews
- Establish an incident response plan with clear communication steps
This checklist aligns with best practices observed in a case study dark web monitoring analysis of financial sector breaches 🛠️
The Role of Continuous Threat Intelligence
Modern cyber risk management goes beyond perimeter defense. By correlating leaked datasets, forum chatter, and credential exposure, security teams can identify threats earlier. Services that aggregate breach intelligence, such as those referenced on https://darknetsearch.com/, help teams track emerging risks and validate whether internal assets are being discussed or sold. As one security analyst noted, “Early visibility into underground activity often determines whether a breach becomes a crisis or a contained event.” This proactive stance is central to effective data breach detection 🧩
Lessons for Users and Customers
For individuals affected by the micro.fuse.co.id data breach, vigilance is key. Users should monitor for suspicious messages, avoid sharing verification codes, and be cautious of insurance or loan-related calls that reference accurate personal details. Even if no immediate fraud occurs, leaked data can resurface months later. Subscribing to identity monitoring services and staying informed through credible intelligence sources can reduce long-term risk. Reviewing educational resources and breach analyses on dark web monitoring platform can also help users understand evolving threat patterns 📚
Conclusion: Turning a Breach into a Wake-Up Call
The micro.fuse.co.id data breach serves as a stark reminder of how interconnected systems, APIs, and third-party services can amplify cyber risk. With nearly 199,000 records exposed—including financial, insurance, and identity data—the incident illustrates why security must be embedded at every layer of digital operations. Organizations that invest in continuous monitoring, rapid response, and user education are better positioned to withstand similar events. Don’t wait for the next leak to take action. Discover much more in our complete guide and Request a demo NOW 🚀
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourselfsssss.

