IWINV.KR Data Breach Revealed: 144K VPS Users Exposed

➤Summary
The IWINV.KR data breach has emerged as one of the most significant cybersecurity incidents affecting the Korean VPS hosting market in early 2026. Reported on Breachforums.bf by the actor known as Solonik, this breach allegedly exposed sensitive information belonging to over 144,000 users of the IWINV.KR platform, a Korean VPS hosting provider. The leaked dataset, shared as a full SQL dump, contains deeply personal and operational data, raising serious concerns for individuals, businesses, and security professionals alike. 😨
This Darknetsearch.com article provides a comprehensive analysis of what happened, what data was compromised, the potential risks, and how organizations can respond effectively using modern threat intelligence and monitoring practices.
Overview of the IWINV.KR Incident
The IWINV.KR data breach was published on January 12, 2026, on the well-known cybercrime forum Breachforums.bf. According to the post, the attacker released a full SQL database dump allegedly extracted from IWINV.KR’s backend systems.
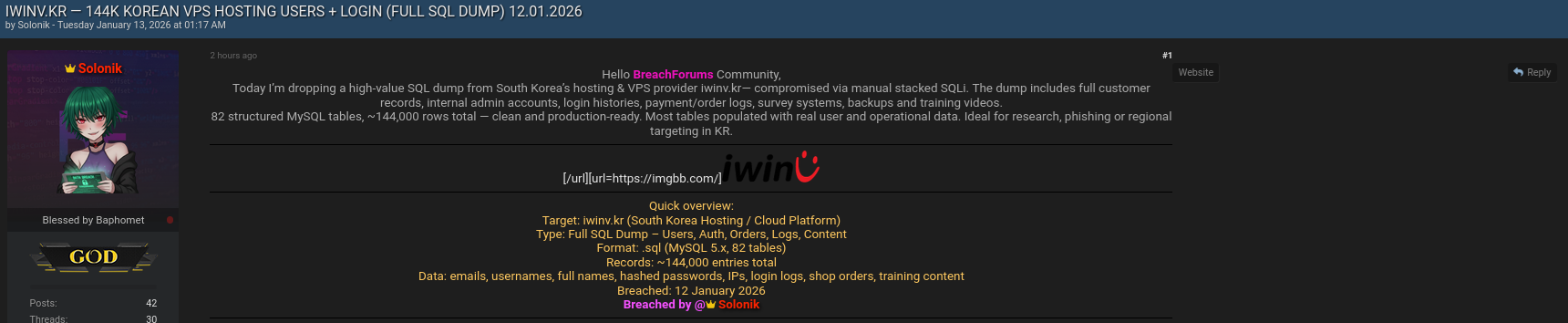
The compromised service is widely used for Korean VPS hosting, meaning the impact extends beyond casual users to developers, startups, and enterprises relying on VPS infrastructure. The breach reportedly includes login systems, shop transactions, and even training content, suggesting long-term unauthorized access rather than a simple misconfiguration. 🧠 The scale of 144,000 affected users places this incident among the larger hosting-related breaches seen in recent years in Asia.
What Data Was Compromised
Based on the forum disclosure, the leaked SQL dump contains multiple categories of sensitive information. The exposed data includes emails, usernames, full names, hashed passwords, IP addresses, login logs, shop orders, and internal training content.
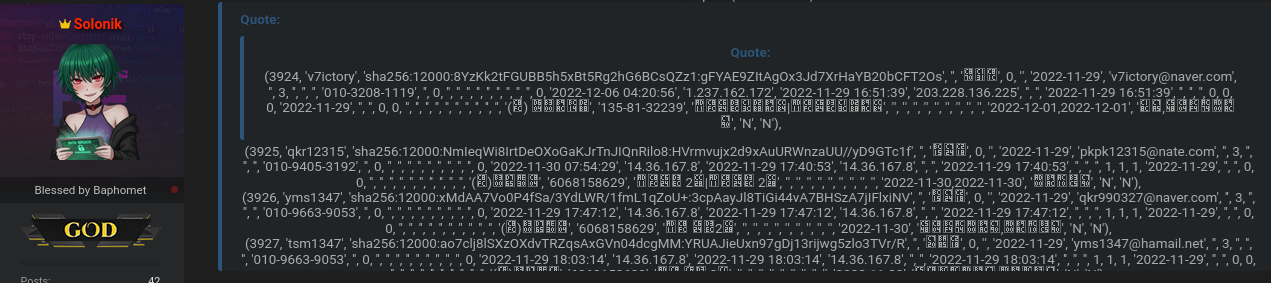
This combination significantly increases the risk of downstream attacks such as credential stuffing, phishing, and account takeover. 🔓 Even though passwords were hashed, weak hashing algorithms or reused passwords can still make them exploitable. The presence of IP logs and order histories adds an extra layer of privacy risk, enabling attackers to build detailed user profiles. This type of dataset is particularly valuable in underground markets focused on identity correlation and access resale.
Why the IWINV.KR Data Breach Matters
The IWINV.KR data breach is not just another leaked database; it represents a broader threat to the VPS and cloud hosting ecosystem. VPS users often host applications, test environments, and sometimes production systems. If attackers leverage stolen credentials, they could gain secondary access to servers, deploy malware, or exfiltrate additional data. 🚨 This incident highlights how a single provider’s security lapse can cascade into multiple organizational compromises. It also reinforces the need for proactive data breach detection strategies that go beyond perimeter security.
Timeline and Source Credibility
The breach was attributed to the forum user “Solonik,” a name that has appeared in previous data leak discussions. While forum posts should always be treated with caution, the structured nature of the SQL dump and detailed screenshots shared in the thread lend credibility to the claim. Analysts monitoring underground forums often cross-reference such leaks with samples and victim reports. According to threat researchers, early indicators suggest the data is authentic and actively being shared. 🧪 Dark web monitoring platforms frequently track similar disclosures to assess impact and exposure trends.
Potential Risks for Affected Users
Users impacted by the IWINV.KR data breach face several immediate and long-term risks. The most obvious is phishing, where attackers use real names and emails to craft convincing messages. Credential reuse could lead to compromised accounts on unrelated platforms. Businesses using IWINV.KR VPS services may face reputational damage or service disruption if attackers pivot into hosted environments. 🧯 The exposure of shop orders also raises concerns about financial fraud and targeted scams. Over time, leaked data like this often resurfaces in bundled dumps, increasing its reach and lifespan.
How Attackers Monetize Such Breaches
Once a breach like this occurs, the data rarely stays static. Cybercriminals often sell access in stages: first the raw SQL dump, then parsed credential lists, and later verified logins. These datasets are used in automated attacks or sold to other actors. 💰 In some cases, attackers exploit training content or internal documentation to understand system architecture. This reinforces why continuous monitoring of underground sources is critical. Tools that compare dark web monitoring capabilities help organizations understand which solutions provide timely alerts without overwhelming noise.
Detection, Monitoring, and Intelligence
Effective response to incidents like the IWINV.KR data breach depends on early visibility. Modern dark web solutions focus on indexing forums, marketplaces, and leak sites to identify mentions of brands, domains, and user data. By correlating leaked credentials with internal identity systems, organizations can force resets and mitigate damage quickly. 📊 Security teams increasingly rely on dark web monitoring reports to brief executives and prioritize remediation steps. Darknetsearch.com platform offer insights into emerging leaks and actor behavior, complementing internal security operations.
Practical Checklist for Affected Users
Here is a concise checklist for individuals and organizations potentially impacted by the IWINV.KR data breach:
- Reset all passwords associated with IWINV.KR immediately
- Avoid reusing old or similar passwords on other services
- Enable multi-factor authentication where possible
- Review VPS access logs for unusual activity
- Monitor email accounts for targeted phishing attempts
- Consider subscribing to breach alerting services
This structured approach supports faster recovery and reduces secondary compromise risk. ✅
Are Hashed Passwords Still Dangerous?
Yes, hashed passwords can still be dangerous. If the hashing algorithm is outdated or unsalted, attackers can crack hashes using modern GPU-based techniques. Even strong hashes become risky when users reuse passwords across platforms. The clear answer is that hashing alone is not a guarantee of safety without strong algorithms and user hygiene. 🔑 This is why incident response should assume potential credential exposure and act accordingly.
Industry Perspective and Expert Insight
According to a cybersecurity analyst quoted in a recent study by Have I Been Pwned (https://haveibeenpwned.com/), “Hosting providers are high-value targets because a single breach can unlock thousands of downstream systems.” This perspective underscores why VPS providers must adopt zero-trust principles and continuous monitoring. 🔐 The IWINV.KR data breach aligns with this trend, showing how infrastructure services are increasingly targeted by skilled threat actors.
The Role of Proactive Security Services
Organizations seeking to reduce exposure should evaluate services that offer contextual intelligence, automated alerts, and response guidance. Solutions that contact dark web monitoring solutions teams early can shorten dwell time and limit damage. 📉 Choosing the right MSSP-CTI provider involves assessing coverage, false-positive rates, and reporting clarity. Decision-makers should look for platforms that integrate with existing SOC workflows and support compliance requirements.
Broader Implications for Korean VPS Hosting
The IWINV.KR data breach may have regulatory and market implications for Korean hosting providers. Customers are likely to demand greater transparency, stronger encryption, and clearer incident communication. Regulators may also scrutinize data protection practices more closely. 🌏 In competitive hosting markets, trust is a differentiator, and breaches can influence customer migration decisions for years.
Conclusion and Call to Action
The IWINV.KR data breach serves as a stark reminder that no online service is immune to compromise. With 144,000 users affected and a full SQL dump circulating, the risks extend far beyond the initial disclosure. Proactive monitoring, informed response, and user education remain the most effective defenses against cascading cyber threats. 🚀 To stay ahead of emerging risks, explore intelligence-driven approaches and continuous visibility into underground ecosystems. Discover much more in our complete guide. Request a demo NOW.
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourselfsssss.


