LOTUSLITE Malware Attack: 7 Key Mustang Panda Insights

➤Summary
LOTUSLITE malware has become a prominent cyber threat after researchers uncovered how the Mustang Panda threat group exploited Venezuela-related news to distribute this stealthy backdoor 🦠. The campaign relied on targeted spear-phishing emails crafted to appear as legitimate geopolitical updates, luring victims into opening malicious attachments.
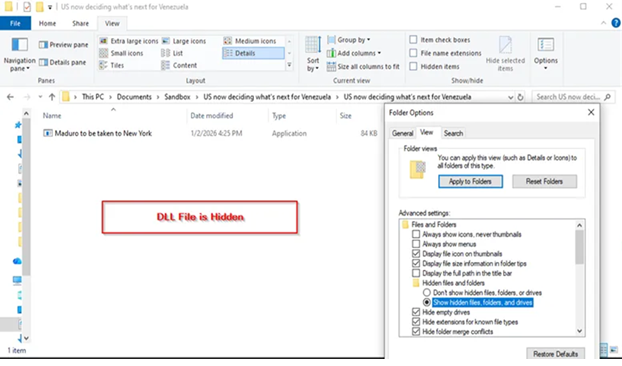
The spear phishing archive named US now deciding what’s next for Venezuela.zip and the malicious files are clearly visible (Source: Acronis)
This approach demonstrates how modern threat actors blend current events with technical tradecraft to bypass security controls. The LOTUSLITE malware operation highlights the increasing sophistication of state-aligned cyber campaigns and reinforces why organizations must focus on proactive detection, behavioral analysis, and user awareness. Understanding how this malware works is essential for reducing exposure and preventing long-term compromise.
Who Is Mustang Panda and Why This Campaign Matters
Mustang Panda is a well-known advanced persistent threat group linked to long-running cyber-espionage operations. Unlike financially motivated attackers, this group focuses on intelligence collection, strategic access, and persistence. Their use of LOTUSLITE malware reflects a preference for low-noise, high-success techniques rather than flashy exploits. By embedding malicious payloads inside news-themed documents, they increase credibility and victim engagement 🎯. This campaign matters because it shows how threat actors continue to weaponize trust, relevance, and curiosity to gain initial access.
How Venezuela News Was Used as the Infection Vector
The infection chain begins with spear-phishing emails referencing Venezuela-related political developments. These emails contain ZIP attachments designed to look like policy briefings or diplomatic reports. Once opened, the archive reveals a legitimate-looking executable paired with a hidden malicious DLL. This tactic exploits user expectations and lowers suspicion 📩. Because the content aligns with real-world events, recipients are more likely to interact with the attachment, allowing the malware to execute without triggering immediate alarms.
How LOTUSLITE Malware Works Step by Step
LOTUSLITE malware relies on DLL sideloading to bypass endpoint defenses. A legitimate executable is abused to load a malicious DLL placed in the same directory. When launched, the malware establishes persistence by modifying registry keys and silently initiates communication with its command-and-control server. From there, attackers can execute commands, collect system information, access files, and exfiltrate data 📡. This design prioritizes reliability and stealth, making detection difficult without behavioral monitoring.
Why DLL Sideloading Is Effective in This Attack
DLL sideloading remains effective because many security tools trust signed or legitimate executables. By hijacking this trust model, LOTUSLITE malware avoids immediate detection. The technique requires no exploit and works on fully patched systems, which makes it attractive to advanced attackers. This is why defenders must look beyond signature-based detection and focus on execution context and abnormal behavior ⚙️.
Impact on Targeted Organizations
The impact of the LOTUSLITE malware campaign extends beyond individual infections. Once inside a network, attackers can maintain long-term access, collect sensitive communications, and pivot laterally. This can result in data exposure, operational disruption, and strategic intelligence loss. In some cases, compromised systems may later be leveraged for additional campaigns, compounding the damage. Organizations involved in government, policy, or international affairs face elevated risk due to their relevance to geopolitical intelligence gathering 🚨.
Detection and Mitigation Strategies
Defending against LOTUSLITE malware requires layered controls and awareness:
• Monitor for abnormal DLL loading behavior
• Restrict execution from temporary and user directories
• Inspect ZIP attachments with contextual analysis
• Track outbound connections to unfamiliar domains
• Educate users on geopolitical phishing lures
Integrating threat intelligence into security workflows helps teams recognize emerging tactics early and respond before attackers establish persistence.
Practical Checklist for Security Teams
Use this checklist to reduce exposure to similar malware campaigns:
- Block or sandbox ZIP attachments with political themes
- Enable application allow-listing on critical systems
- Log registry changes linked to startup persistence
- Correlate endpoint telemetry with network traffic
- Conduct targeted phishing simulations for high-risk teams
This approach improves readiness and limits dwell time if compromise occurs ✅.
Role of Threat Intelligence in Early Detection
Advanced monitoring plays a critical role in identifying campaigns like LOTUSLITE before they escalate. Leveraging a Darknet Threat Intelligence Solution alongside curated dark web monitoring documentation allows organizations to track threat actor behavior and emerging tools. Reviewing dark web monitoring reports can reveal early indicators of targeted attacks, helping defenders adapt controls quickly. This intelligence-led model supports faster response, reduced exposure, and stronger overall resilience 📊.
Is This a One-Time Campaign or a Growing Trend?
Question: Is LOTUSLITE malware an isolated attack?
Answer: No. This campaign reflects a broader trend where attackers exploit current events to enhance phishing credibility. Similar tactics will continue to evolve, making awareness and adaptive defenses essential for long-term protection 🔍.
Further Reading and Trusted Resources
For in-depth technical analysis of this campaign, refer to this authoritative report:
External source: https://hackread.com/mastang-panda-venezuela-news-lotuslite-malware/
For ongoing research into threat actor activity and underground intelligence, explore:
https://darknetsearch.com/threat-analysis
https://darknetsearch.com/reports
Conclusion
The LOTUSLITE malware campaign illustrates how threat actors like Mustang Panda combine geopolitical relevance with stealthy malware delivery to achieve persistent access. By understanding how these attacks work and implementing intelligence-driven defenses, organizations can significantly reduce risk. Stay informed, strengthen detection, and prioritize awareness to counter evolving threats.
Discover much more in our complete guide
Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.

