Hopeful.co.th Database Breach: 7 Key Impacts and Risks

➤Summary
Hopeful.co.th Database breach has emerged as a critical cybersecurity incident after sensitive records allegedly surfaced on a notorious underground forum. According to posts published on breachforums.bf by an actor using the alias “888” on 20 January 2026, the compromised dataset contains order information, transaction dates, payment methods, phone numbers, customer IDs, customer names, and shipping addresses. This event has triggered significant concern among consumers and security professionals alike because it highlights how exposed e-commerce platforms can be when threat actors gain access to poorly secured databases 😟. The Hopeful.co.th Database breach is not just a local issue; it reflects a growing global trend where online retailers become prime targets for data exfiltration and resale across illicit marketplaces.
Incident Background and Forum Disclosure Details
The Hopeful.co.th Database breach was first revealed through a detailed forum post on breachforums.bf, a platform often used to trade and publicize stolen data. The author “888” claimed responsibility for accessing and listing the database, providing samples to validate authenticity. Such disclosures typically follow a familiar pattern: initial access, data extraction, and eventual monetization through underground channels 💻. Researchers monitoring these forums confirmed that the dataset appeared structured and consistent with real transaction logs.

While Hopeful.co.th has not yet publicly confirmed the breach, the presence of realistic fields such as shipping addresses and transaction dates suggests a credible compromise rather than fabricated information.
What Types of Data Were Compromised
Understanding the scope of exposed information is essential when assessing the real-world impact of the Hopeful.co.th Database breach. Based on the forum disclosure, the compromised data includes:
• Order information and purchase histories
• Transaction dates linked to customer activity
• Payment methods (non-PCI but still sensitive metadata)
• Phone numbers and customer IDs
• Full customer names and shipping addresses
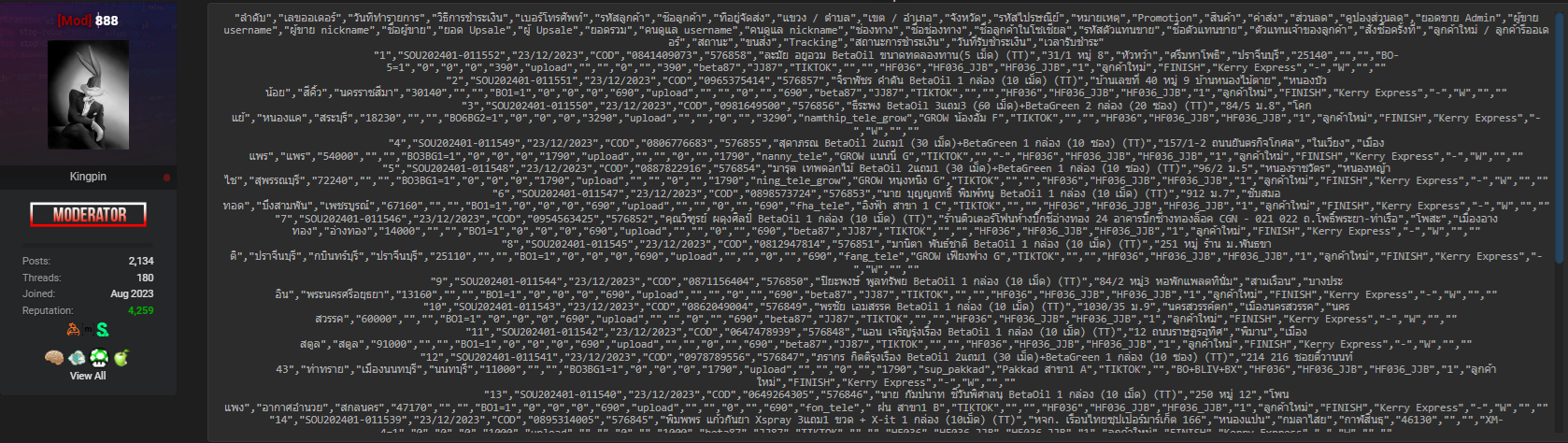
This combination of personal and transactional data significantly raises the risk of identity fraud, phishing campaigns, and social engineering attacks 🎯. When attackers can correlate names, phone numbers, and order histories, they can craft highly convincing scams that are difficult for victims to detect.
Why This Breach Poses Serious Risks to Consumers
The Hopeful.co.th Database breach poses more than theoretical risks. Criminals can weaponize this data for targeted fraud, fake delivery notifications, and account takeover attempts. For example, knowing recent transaction dates allows attackers to time phishing messages precisely when customers expect legitimate communications. This is where Darknet Threat Intelligence Solution platforms become essential, as they help organizations identify leaked datasets early and mitigate downstream damage. Consumers affected by the breach may experience increased spam, fraudulent calls, or even physical security risks if shipping addresses are misused 🚨.
Connection to Broader Cybercrime Ecosystems
Data from the Hopeful.co.th Database breach does not exist in isolation. Stolen records often circulate across multiple marketplaces, bundled with other leaks to increase value. Analysts reviewing dark web monitoring reports have noted that e-commerce databases are frequently combined with credential dumps to enhance resale potential. This interconnected ecosystem allows attackers to scale operations quickly, turning a single breach into thousands of downstream attacks. Monitoring these environments is now a core component of modern cyber defense strategies.
SEO-Focused Analysis: How Businesses Should Respond
From an organizational standpoint, the Hopeful.co.th Database breach underscores the importance of proactive defense measures. Companies should implement continuous surveillance using tools such as Domain Spoofing Detection to prevent attackers from impersonating official brands in phishing campaigns. In addition, reviewing dark web monitoring documentation helps security teams understand how leaked data is traded and what indicators to watch for 🔍. These practices are no longer optional; they are essential to maintaining customer trust and regulatory compliance.
Practical Checklist for Affected Users and Businesses
If you believe you may be impacted by the Hopeful.co.th Database breach, follow this practical checklist:
• Change passwords on related accounts immediately
• Monitor bank statements and transaction alerts
• Be cautious of unsolicited calls or delivery messages
• Enable two-factor authentication where possible
• Businesses should audit access logs and patch vulnerabilities
This checklist provides a simple but effective starting point for reducing exposure and preventing further damage ✅.
How Threat Intelligence Helps Prevent Repeat Incidents
One of the most important lessons from the Hopeful.co.th Database breach is the importance of intelligence-led security. By using specialized monitoring capabilities, organizations can identify early indicators of compromise before stolen data appears on public forums. In the e-commerce sector, this approach is especially effective for detecting loyalty account leaks, fraudulent account activity, and exposed customer records. Pattern recognition, anomaly detection, and continuous monitoring of underground sources allow businesses to respond faster, limit reputational damage, and significantly reduce financial losses 📊.
Internal and External Resources for Further Reading
For deeper insights into underground data markets and breach disclosures, readers can explore in-depth resources at Darknetsearch.com. These internal resources provide contextual analysis of breach trends and mitigation strategies. For authoritative external guidance on data breach response and cybersecurity frameworks, refer to the National Institute of Standards and Technology at https://www.nist.gov, a globally trusted authority in information security standards.
Frequently Asked Question About This Breach
Is the Hopeful.co.th Database breach confirmed by the company?
At the time of writing, there is no official public confirmation from Hopeful.co.th. However, the consistency and structure of the leaked data strongly suggest a genuine incident, and users should act with caution and assume exposure until proven otherwise.
Expert Insight on E-Commerce Breaches
A cybersecurity analyst recently noted, “E-commerce databases are attractive targets because they combine personal and transactional data in one place. Even partial leaks can have outsized impacts.” This observation aligns closely with the implications of the Hopeful.co.th Database breach and reinforces why rapid detection and response are critical.
Conclusion and Call to Action
The Hopeful.co.th Database breach serves as a stark reminder that digital commerce platforms must prioritize security at every layer. From leaked order information to exposed shipping addresses, the risks extend far beyond a single forum post. By investing in proactive monitoring, educating users, and responding swiftly to emerging threats, organizations can limit damage and rebuild trust. Discover much more in our complete guide and stay informed about evolving cyber risks. Request a demo NOW to see how advanced monitoring can protect your business before the next breach strikes 🔐
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


