Menulux Data Breach Revealed: 7 Urgent Facts and Risks

➤Summary
Menulux, a technology and software company established in 2013, specializing in cloud-based POS systems and digital ordering solutions for the restaurant and café industry – data breach has become a growing concern after sensitive customer records were allegedly published on an underground forum, raising questions about data security and consumer privacy. According to information shared on breachforums.st by an actor identified as “888” on 21 January 2026, the exposed dataset includes full names, phone numbers, and physical addresses. The Menulux data breach highlights how even limited personal data can be exploited for fraud, scams, and targeted social engineering if it falls into the wrong hands 😟. As digital platforms expand their customer reach, incidents like this show why continuous monitoring and early detection are critical for both organizations and individuals.
Incident Disclosure and Forum Source Details
The Menulux data breach was first disclosed on breachforums.st, a well-known platform where threat actors often advertise or leak stolen datasets. The forum post claimed unauthorized access to Menulux customer records and included samples to support authenticity. While Menulux has not yet released an official confirmation, the structure and consistency of the shared data strongly suggest a genuine compromise rather than fabricated content.
Such disclosures typically follow a pattern of access, extraction, and publication, allowing other actors to reuse or resell the information ⚠️. This method of exposure significantly accelerates the spread of compromised data across underground networks.
What Information Was Compromised
Understanding the scope of the Menulux data breach is essential for assessing risk. Based on the forum disclosure, the compromised data includes:
• Full customer names
• Phone numbers
• Residential addresses
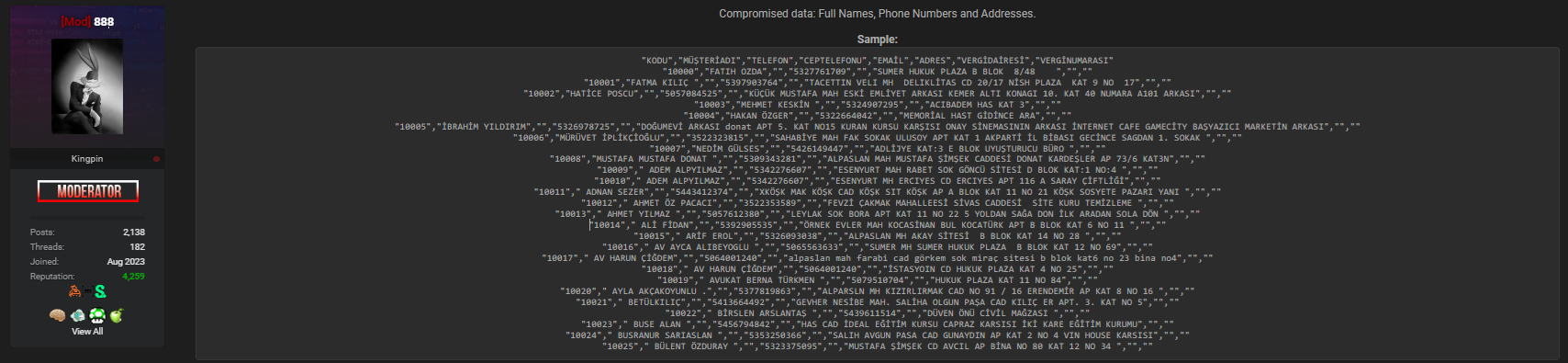
Although no payment details or credentials were mentioned, this combination of personal information can still be highly valuable to cybercriminals. When names and contact details are paired with addresses, attackers can conduct convincing impersonation attempts, fake delivery scams, or targeted phishing campaigns 📩. Even without financial data, such exposure can lead to real-world consequences for affected individuals.
Why This Type of Data Exposure Is Dangerous
The Menulux data breach demonstrates that not all breaches need credit card data to be harmful. Personal contact information is often used as a foundation for more advanced attacks. Criminals can cross-reference leaked names and phone numbers with other datasets to build detailed profiles. This enables scams that appear legitimate and personalized, increasing success rates 🎯. Over time, repeated misuse of exposed data can result in identity abuse, harassment, or loss of trust in the affected brand.
How Breach Data Spreads Beyond Initial Forums
Once published, data from the Menulux data breach may circulate far beyond its original source. Underground forums act as hubs where datasets are copied, traded, and repackaged. Analysts reviewing dark web monitoring reports often find that even small leaks quickly propagate across multiple marketplaces. This rapid spread makes timely detection crucial. Without visibility into these channels, organizations may remain unaware of exposure until customers report suspicious activity 🚨.
SEO-Focused Risk Analysis for Businesses
From a business perspective, the Menulux data breach illustrates reputational and operational risks tied to personal data exposure. Customers increasingly expect transparency and strong safeguards for their information. Failing to detect and respond quickly can amplify brand damage and regulatory scrutiny. Solutions such as Domain Spoofing Detection also become important after a breach, as attackers may impersonate the affected brand to exploit leaked contact details. Proactive monitoring and clear communication are essential to maintaining customer confidence 🔍.
Practical Checklist for Affected Users
If you believe your information may be included in the Menulux data breach, consider the following steps:
- Be cautious of unsolicited calls or messages claiming to represent Menulux.
- Avoid sharing additional personal information over the phone or email.
- Monitor for unusual delivery notices or verification requests.
- Report suspicious activity to local authorities or consumer protection agencies.
- Consider registering for identity monitoring services.
This checklist helps reduce the likelihood of secondary exploitation and improves personal security posture ✅.
How Organizations Can Strengthen Detection and Response
Organizations can reduce exposure by adopting intelligence-led security strategies. Using a Darknet Threat Intelligence Solution enables teams to identify leaked datasets early and assess potential impact before widespread abuse occurs. Reviewing dark web monitoring documentation also helps security teams understand how and where data is traded. Continuous monitoring, access controls, and regular audits are critical components of effective defense 📊.
Frequently Asked Question About This Incident
Is the Menulux data breach confirmed?
At the time of writing, Menulux has not issued a public statement confirming the breach. However, the credible nature of the forum disclosure suggests that customers should remain vigilant and take precautionary measures until further clarification is provided.
Expert Insight on Personal Data Leaks
A cybersecurity analyst noted, “Even basic personal data like names and phone numbers can fuel highly targeted scams when aggregated with other leaks.” This insight aligns with the risks associated with the Menulux data breach and reinforces why early detection and user awareness are so important in limiting damage.
Internal and External Resources for Deeper Understanding
For ongoing research into underground data exposure and breach trends, readers can explore resources at Darknetsearch.com. For authoritative guidance on data protection and breach response, consult the National Institute of Standards and Technology, a trusted global authority on cybersecurity standards.
The Broader Impact on Consumer Trust
Incidents like the Menulux data breach affect more than just immediate victims. They erode trust across digital ecosystems, making users hesitant to share information online. Rebuilding that trust requires transparency, improved controls, and demonstrated commitment to security. Companies that invest in monitoring, rapid response, and customer education are better positioned to recover after an incident 🔐.
Conclusion and Call to Action
The Menulux data breach serves as a clear reminder that personal information, even without financial details, carries significant risk when exposed. By understanding how such breaches occur and how data spreads, both consumers and organizations can take proactive steps to reduce harm. Stay informed, remain cautious, and prioritize security awareness in an increasingly connected world. Discover much more in our complete guide and strengthen your understanding of modern breach risks. Request a demo NOW to see how advanced monitoring can help protect your organization before the next incident strikes 🚀
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.

