GCash Data Breach 2025 Revealed: Key Facts, Risks & Proof from the Dark Web

➤Summary
The GCash data breach has sent shockwaves across the Philippine fintech community, raising concerns among millions of mobile wallet users. Reports surfaced on October 25, 2025, claiming that sensitive GCash KYC data—including eKYC records, linked bank accounts, and personal information—has been put up for sale on a dark web forum. The alleged leak, reportedly spanning 2019 to 2025, could expose up to 7–8 million users 🧨.
Cybersecurity analysts and regulators are now racing to confirm whether the breach is genuine or another dark web exaggeration. Still, experts warn: if the claims hold true, this could be one of the largest Philippine data exposures to date.
[Forum Post Evidence]

According to the listing on Darkforums.st, the vendor “Oversleep8351” offered the GCash database for sale, describing bundles of 10,000 unique users each, priced at $700 per 20,000 records. Buyers purchasing 10 bundles (200,000 users) could pay $500 each, while a full buyout for all records (estimated 7–8 million users) was offered for $25,000—a suspiciously low price for such valuable data 💸.
What’s inside the alleged GCash leak?
The post lists multiple categories of compromised data:
- Merchant and basic user profiles
- G-Xchange/GCash account numbers
- Linked accounts (mostly virtual cards and bank connections)
- Full eKYC records: names, addresses, national IDs, employment info
The seller’s “Important Read” notice adds that the eKYC files are not organized, requiring sorting by buyers. The vendor also warns that sample proofs are “available only to existing buyers,” citing privacy of previous dark-web transactions and verification by “code name.” All payments are accepted via Monero (XMR), and escrow is optional through a trusted mediator.
These hallmarks—tiered pricing, anonymity emphasis, and Monero use—are standard for dark-web marketplaces. They lend some plausibility, though not confirmation, to the claim.
[Sample Proof]
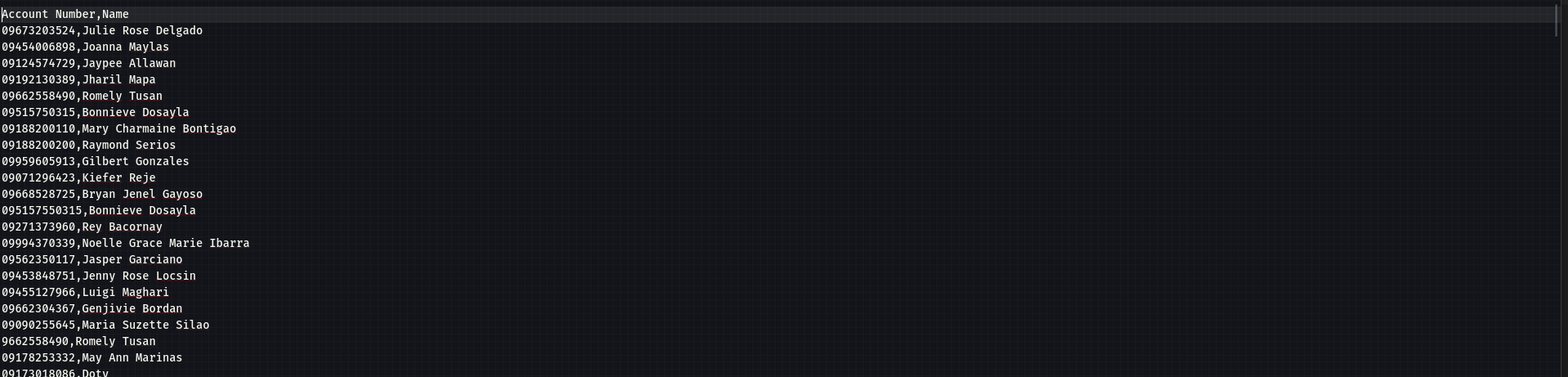
Why this GCash data breach is alarming
If authentic, the GCash data breach would be catastrophic for Filipino digital-payment users. Leaked GCash KYC data means criminals could possess verified government IDs, full names, and account numbers tied to virtual cards and linked banks 😨. The risks include:
- Identity theft: attackers could open fraudulent loans or credit lines.
- Financial fraud: scammers might exploit linked cards or phishing campaigns.
- Synthetic identities: real KYC elements may be recombined into new, fake identities for laundering.
- Permanent exposure: unlike passwords, national-ID images cannot simply be changed.
Investigations and official responses
Historically, GCash and the National Privacy Commission (NPC) have swiftly investigated such claims. The NPC has previously concluded that earlier reports (in 2023 and 2024) were tied to phishing, not system hacking (privacy.gov.ph). In 2024, GCash reiterated there was “no evidence of a data breach,” though internal security reviews were intensified.
As of October 2025, no official confirmation from GCash or the NPC has validated this specific dataset. However, cybersecurity threat intelligence team from the Kaduu team say they discovered the listing during dark-web monitoring.
Pricing table of the alleged dataset
| Bundle Size | Price (USD) | Users per Bundle | Notes |
| 20,000 users | $700 | 20,000 | Standard bundle |
| 200,000 users | $500 each | 10 × 20,000 | Bulk discount |
| 7–8 million users | $25,000 total | Full dataset | “First-come, first-served” sale |
The role of DarknetSearch.com in breach detection
Platforms such as DarknetSearch.com play a critical role when leaks like the GCash data breach 2025 deep web emerge. Unlike Google, they scan Tor, I2P, and closed darknet spaces for new posts, cross-matching file fingerprints and metadata. Their algorithms:
- Detect repeated keywords like “GCash,” “G-Xchange,” and “KYC.”
- Track sellers’ reputations and previous listings.
- Generate alerts for corporate security teams.
DarknetSearch.com also enables financial institutions and regulators to monitor real-time chatter, helping them react faster, validate claims, and contact affected companies directly 🛰️.
Expert commentary
“Whenever a major e-wallet or fintech platform is mentioned on the dark web, even unverified, organizations must act as if it’s real until proven otherwise,” says cybersecurity analyst Marco Reyes from CyberPH Watch. “DarknetSearch-type monitoring gives critical early warning. Waiting for confirmation could mean millions of users already compromised.”
User impact & response checklist 💡
If you use GCash, here’s a practical checklist you should act on immediately:
✅ Change your MPIN and app passwords.
✅ Enable biometric or two-factor authentication.
✅ Disconnect unnecessary linked accounts (especially virtual cards).
✅ Avoid clicking on suspicious SMS or emails claiming “data verification.”
✅ Regularly review your transaction history and report irregularities.
✅ If you believe your ID is compromised, file a report with the NPC and your local bank.
These proactive steps can reduce personal risk even if the leak later proves genuine.
Broader cybersecurity implications
The GCash KYC data leak claim highlights a recurring problem in Southeast Asia’s fintech landscape: e-wallets collect vast verified user datasets, yet centralized security remains uneven. With 90 million+ e-money accounts nationwide, even partial exposure can undermine public trust in the cashless ecosystem 🔐.
Furthermore, as dark-web cybercriminals trade verified ID sets, regional fraud rings grow more sophisticated—reusing data across borders for scams and money-laundering schemes.
The unanswered question
Could this GCash data breach have been an inside job or a third-party system exposure? Investigators haven’t ruled out either. Insider leaks and unsecured vendor APIs have become common vectors for large KYC-data thefts. Until digital-identity systems decentralize or encrypt user IDs individually, these mass leaks will remain lucrative targets.
How law enforcement could intervene
Once verified, local authorities (NPC and DICT) can compel G-Xchange Inc. to notify affected users and perform system audits. Under Philippine Data Privacy Act (2012), failure to secure personal data can result in civil and criminal penalties, including fines and imprisonment for negligent handling. Regulators may also mandate independent third-party audits for e-wallet systems.
Dark web commerce behind the breach
The GCash forum post uses language consistent with illicit marketplaces: technical disclaimers, escrow options, and Monero-only payments. These methods conceal seller identities and make law-enforcement tracking difficult. According to Kaduu researchers, the seller’s alias “Oversleep8351” has prior activity linked to Southeast Asian financial-data trades. If accurate, this strengthens the possibility that the breach stems from insider or scraped database access.
Checklist for companies to prevent similar leaks
🔹 Conduct regular dark-web sweeps using tools like DarknetSearch.com.
🔹 Encrypt KYC files both at rest and in transit.
🔹 Enforce least-privilege access controls.
🔹 Implement security audits for third-party partners.
🔹 Require mandatory security awareness training for employees.
Adopting these measures can dramatically reduce breach probability and impact.
Conclusion 🚨
The alleged GCash data breach remains under investigation, but it serves as a wake-up call for Philippine fintech security. Millions of records, if verified, could mean severe reputational and financial fallout for both the company and its users. Whether you’re a consumer or a fintech provider, vigilance and real-time dark-web intelligence are your best defenses.
Stay alert, update your security settings, and keep monitoring trusted cybersecurity channels.
Discover much more in our complete guide.
Request a demo NOW.
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


