APT36 Malware Campaign Revealed: Golang-Based DeskRAT Attack on Indian Government [2025 Report]
![APT36 Malware Campaign Revealed: Golang-Based DeskRAT Attack on Indian Government [2025 Report]](https://blog.darknetsearch.com/wp-content/uploads/2025/10/APT36-malware.jpg)
➤Summary
The APT36 malware campaign has once again shaken the cybersecurity landscape of South Asia. In its latest operation, the Pakistan-linked threat group, also known as Transparent Tribe, launched a Golang-based DeskRAT campaign targeting the Indian government and defense networks. According to recent reports from The Hacker News, the attackers employed sophisticated social engineering and cross-platform malware to infiltrate critical systems—marking a major escalation in ongoing cyber espionage activity across the region. 😈
This detailed analysis by the Kaduu cyber threat intelligence team examines how this state-sponsored attack works, what risks it poses to Indian cybersecurity, and how organizations can leverage leak detection software tools like darknetsearch.com to detect data leaks before it’s too late.
The Anatomy of the APT36 Malware Campaign 🧠
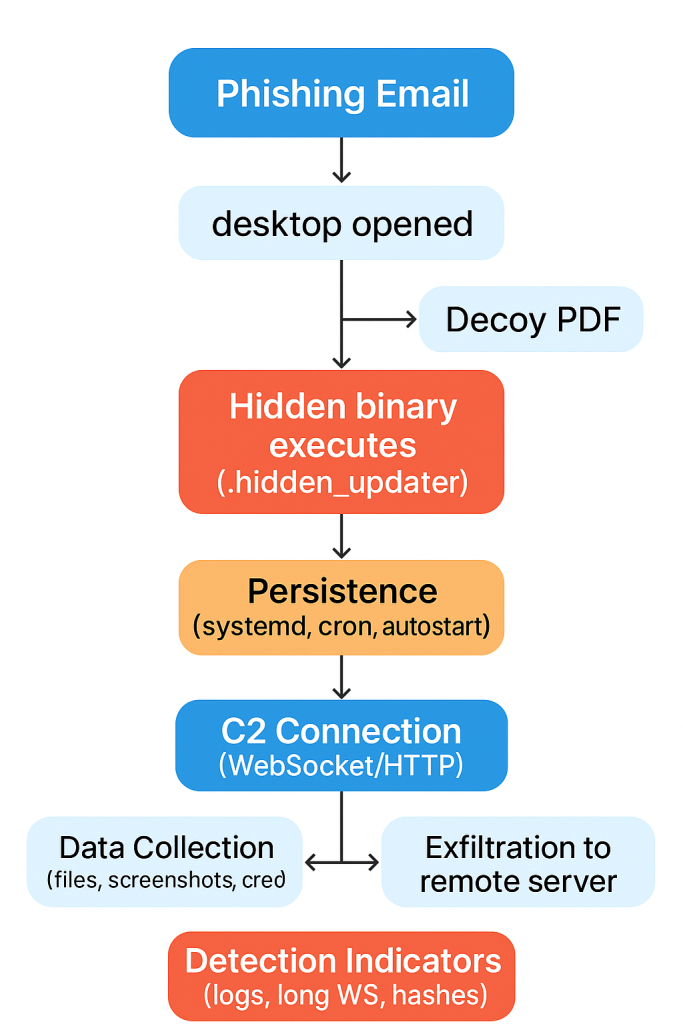
The APT36 malware campaign begins with a classic spear-phishing email—crafted to appear as an official communication from Indian defense or government departments. Attached to these emails are ZIP archives containing .desktop files that execute malicious code when opened. The attackers cleverly use decoy PDFs titled with defense or government keywords to distract users, while DeskRAT silently installs in the background. This tactic blends phishing campaigns with deep technical deception, making detection harder.
Once executed, DeskRAT (developed in Golang) connects to remote command-and-control servers through HTTP or WebSocket channels. It then begins stealth operations: collecting sensitive files, capturing screenshots, listing directories, and maintaining persistence through cron jobs or systemd services.
Practical Tip 💡: Always inspect .desktop files before execution. These can run hidden commands even if they appear harmless.
Why Golang-Based DeskRAT Is So Dangerous ⚙️
The choice of Golang isn’t accidental. Unlike traditional RATs built on C++ or Python, Golang-based DeskRAT produces self-contained binaries that are cross-platform and difficult to analyze. Golang’s memory safety and obfuscation make malware detection by standard antivirus engines more challenging.
DeskRAT’s features include:
- File exfiltration and command execution
- Screenshot and process collection
- Auto-start persistence
- Upload and execute additional payloads
These functions give attackers total remote control, effectively turning infected machines into spy nodes within government networks. What makes it more concerning is that Golang allows rapid development—APT36 can easily adapt DeskRAT for Windows, macOS, or Linux, expanding its malware arsenal exponentially.
APT36 Targets Indian Government: Timeline and Motives 🕵️♂️
The APT36 malware campaign has roots dating back to at least 2013, with documented intrusions against Indian military and diplomatic institutions. Over time, its methods evolved—from simple phishing websites to supply-chain infiltration and custom-built RATs like CrimsonRAT, Poseidon, and now DeskRAT.
According to cybersecurity experts, this state-sponsored attack seeks to steal government documents, defense strategies, and communication intelligence. The timing aligns with regional geopolitical tensions, suggesting strategic intent rather than financial gain. The campaign also targets BOSS Linux, an OS favored by Indian government departments—highlighting APT36’s awareness of India’s digital ecosystem.
Expert Insight 🗣️
“APT36’s consistent use of evolving cross-platform malware signifies a long-term espionage strategy rather than opportunistic attacks,” says cybersecurity analyst R. Mehta from Kaduu Threat Research. “Their reliance on Golang-based tools like DeskRAT proves their intent to outsmart conventional detection systems.”
This observation reinforces how Transparent Tribe adapts and experiments to maintain stealth in a region where cybersecurity defenses are improving rapidly.
Indicators of Compromise (IOCs) and Detection Checklist ✅
For teams handling cyber exposure monitoring and incident response, identifying DeskRAT infections early can save valuable time. Here’s a short checklist you can use:
| Indicator Type | Example | Detection Method |
| File | .desktop disguised as PDF shortcut | Email sandboxing, manual inspection |
| Domain | modgovindia[.]space | DNS traffic monitoring |
| Persistence | New systemd or cron job entries | Endpoint security audit |
| Behavior | WebSocket traffic on uncommon ports | Firewall and SIEM rules |
If any of these patterns are detected, isolate affected systems immediately and conduct a full forensic sweep.
Role of Dark Web Monitoring in APT Defense 🌐
Cybersecurity doesn’t end at the firewall. After a breach, stolen data often surfaces on the dark web—where attackers sell or leak information. This is where platforms like darknetsearch.com play a pivotal role. Their darknet threat detection capabilities allow governments and corporations to:
- Detect leaked credentials or sensitive files early
- Track data breaches related to national or corporate infrastructure
- Monitor underground forums for chatter about upcoming campaigns
- Map threat actor activity to existing intelligence
By using real-time threat monitoring, agencies gain proactive visibility into what’s happening beyond their networks—often catching clues of an APT36 malware campaign before it escalates.
Real-World Impact and Risks ⚠️
The DeskRAT attack doesn’t just compromise individual systems—it endangers national data sovereignty. Based on risk assessments, government departments that rely on Linux-based systems may assume lower cybersecurity risk, but APT36’s cross-platform approach proves otherwise. Once the malware infiltrates a workstation, it can pivot across the network, targeting classified databases, email archives, and communication servers.
For businesses contracting with public-sector bodies, this increases the risk of supply-chain compromise, spreading the impact beyond national boundaries. In fact, corporate data exposure firms have already detected variants of DeskRAT attempting to access contractor networks linked to infrastructure projects.
How to Strengthen Cybersecurity Defenses 🛡️
Here are key recommendations to protect against APT-level intrusions:
- Educate staff on phishing and suspicious attachments.
- Deploy EDR solutions capable of Linux monitoring.
- Audit system persistence mechanisms regularly.
- Block WebSocket traffic to untrusted domains.
- Integrate dark web intelligence from darknetsearch.com.
- Collaborate with national CERTs to share IOCs promptly.
Remember: APT36 targets Indian government, but the same tactics could target private entities tomorrow.
FAQ ❓
Q: How can organizations detect Golang-based DeskRAT infections quickly?
A: Implement network traffic monitoring for WebSocket anomalies, use EDR tools that support Linux endpoints, and check for suspicious .desktop or cron entries. Regular log audits and external threat feeds significantly improve early detection.
The Bigger Picture: State-Sponsored Cyber Espionage 🌍
The APT36 malware campaign is not an isolated event—it reflects a global trend of nation-backed hacking. With increasing digitization of governance and defense, malware analysis, cyber threat intelligence, and dark web monitoring are no longer optional—they are national priorities.
As cyber espionage grows more complex, understanding the enemy’s infrastructure is essential. APT36’s DeskRAT marks a turning point where offensive cyber operations blur the line between war and intelligence gathering.
Conclusion: Strengthening India’s Cyber Future 💪
The exposure of the APT36 malware campaign and its Golang-based DeskRAT variant is a wake-up call for every digital stakeholder in India. The threat landscape is evolving, but so are the defenses. Through proactive monitoring, awareness, and threat intelligence sharing, India can mitigate risks posed by state-sponsored attacks like those from Transparent Tribe.
Security is no longer just about technology—it’s about anticipation, speed, and intelligence. Platforms like darknetsearch.com empower defenders with exactly that visibility. 🔐
Discover much more in our complete guide
Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


