Apple.com Data Breach 2025: 9GB Leak Revealed with Backups, APIs & More

➤Summary
The Apple.com data breach has shaken the cybersecurity community. On October 3, 2025, an underground forum listing claimed that 9GB of internal Apple data was stolen and is now being sold for $5,000 in deep web. The archive allegedly contains compiled Java files, JSON APIs, and critical backups. Apple, known for its strong privacy and data security measures, has not confirmed the breach, but the incident has already raised questions about infrastructure leaks, corporate protection, and potential risks. 🛑
The post, discovered by the Kaduu threat intelligence team during routine darknet monitoring, highlights how even tech giants remain attractive targets. This article breaks down what happened, what was allegedly stolen, why the claim is controversial, and what it means for businesses worldwide.
Key Facts from the Darknet Forum
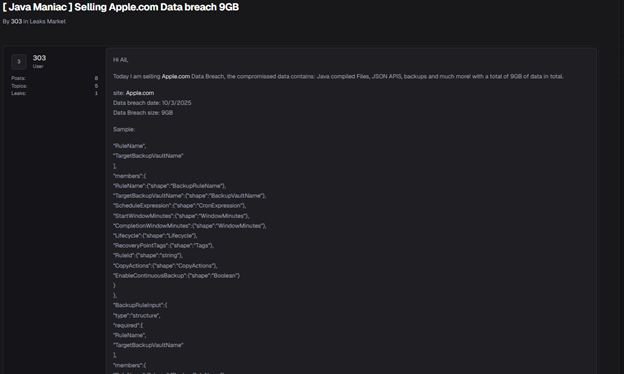
The leak was published by a user known as 303 (alias Java Maniac) on BreachStars, a darknet marketplace for stolen data. Below are the main details:
| Attribute | Claimed Value |
| Author / Seller | 303 (aka Java Maniac) |
| Forum | BreachStars |
| Target | Apple.com |
| Breach Date | October 3, 2025 |
| Size of Data | 9GB |
| Price | $5,000 |
| Claimed Content | Java compiled files, JSON APIs, backups |
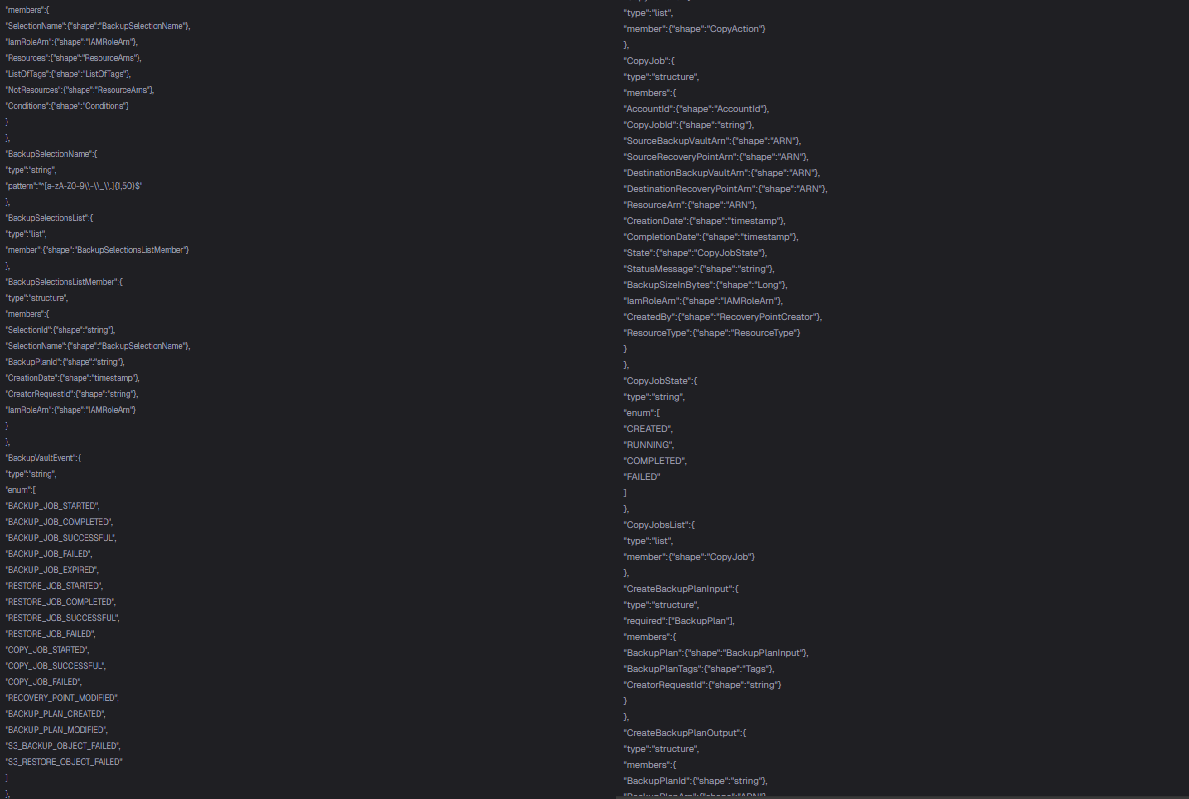
The forum post included a snippet of JSON code referencing backup rules and vault names, suggesting internal infrastructure data. According to the seller:
“Today I am selling Apple.com Data Breach. The compromissed data contains: Java compiled Files, JSON APIS, backups and much more!”
Proof Presented by the Seller
The proof section showed JSON entries like:
“RuleName”: “BackupPolicy2025”,
“TargetBackupVaultName”: “APPL-INT-VLT”,
“BackupRuleInput”: {
“ScheduleExpression”: “cron(0 12 * * ? *)”,
“Lifecycle”: { “DeleteAfterDays”: 365 }
}
On the surface, this looks like backup scheduling data from a cloud environment. If genuine, it could expose how Apple structures its internal backups. But cybersecurity experts caution this may be fabricated or unrelated.
Screenshot of the post:
Why the Apple.com Breach Matters
Even without customer data, backups and APIs can be dangerous:
- Compiled Java files may reveal proprietary logic.
- APIs could expose hidden endpoints vulnerable to cyberattack.
- Backups might contain metadata, system logs, or even credentials.
- Vault identifiers can reveal internal infrastructure mapping.
As one analyst noted on DarknetSearch.com:
“Infrastructure leaks don’t make headlines like customer records, but they often cause the most long-term security damage.” ⚠️
Skepticism Around the Claim
Not everyone is convinced this breach is real:
- Apple has not confirmed the incident.
- $5,000 is unusually low for such data — similar leaks often sell for tens of thousands.
- Proof is weak, limited to a JSON snippet.
- No customer data was mentioned.
- Some sellers exaggerate to boost reputation.
Still, cybersecurity media like RedHotCyber have flagged the story as worth monitoring.
Apple as a Prime Target 🎯
Apple has a long history of facing cyber threats:
- 2014 iCloud breach exposed celebrity photos.
- 2017 iBoot leak revealed iOS bootloader code.
- 2021 warnings about supply chain attacks highlighted potential weak points.
This latest claim, whether true or not, shows how Apple remains in the crosshairs of hackers and underground data brokers.
Practical Tip for Businesses
If your company manages backups and APIs, take these immediate steps to avoid similar exposure:
✅ Encrypt backups end-to-end.
✅ Monitor API traffic for unusual patterns.
✅ Restrict access to infrastructure logs.
✅ Run regular penetration tests on internal systems.
Economic Side of Darknet Data Sales 💰
Why price such a breach at only $5,000? Possible reasons:
- Seller may lack credibility.
- Data may be partial or outdated.
- Lower prices attract quicker buyers.
- Law enforcement monitoring makes high-value sales risky.
On forums like DarknetSearch, many leaks are hyped but don’t always deliver. The pricing strategy itself is a clue for researchers to consider.
Expert Opinion
Cybersecurity researcher Luis Romero commented:
“The most dangerous leaks aren’t customer data but infrastructure blueprints. Even cron jobs and backup scripts can help hackers reverse-engineer enterprise defenses.”
This suggests that even if no personal Apple customer information is included, the breach could be exploited in advanced persistent threat campaigns.
Related Risks for Enterprises
If this Apple data breach claim proves true, other organizations should be alert for:
- Supply chain attacks targeting vendors.
- Credential harvesting from leaked backups.
- Reputational loss due to perceived vulnerability.
- Reverse engineering of code to find exploits.
Quick Checklist Before Dismissing a Breach 🚨
- Check if the company has responded publicly.
- Review the type of data claimed.
- Examine price vs. value.
- Look for past credibility of the seller.
- Monitor related darknet chatter.
This checklist can help security teams decide if an underground claim deserves immediate attention.
Conclusion
The Apple.com data breach story is still developing. While skepticism remains due to the low price and weak proof, the possibility of leaked APIs, backups, and compiled files should not be ignored. Apple has not confirmed any compromise, but the incident is a reminder that even the strongest tech firms can face security risks. 🕵️
For businesses, the lesson is clear: protect your infrastructure with the same rigor as your customer data. Attackers don’t always want credit cards — sometimes they want your architecture, your code, and your backups.
👉 Discover much more in our complete guide
👉 Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


