Guldsmed-Holmer.dk Breach Revealed: Urgent Impact and Analysis

➤Summary
On 06 October 2025, the cybersecurity team Kaduu discovered a massive Guldsmed-Holmer.dk data breach 🧨—a serious incident affecting the Danish jewelry retailer. The breach surfaced in Darkforums.st, posted by the user camillaDF. The leaked dataset includes sensitive personal and transactional information such as email, passwd, secure_key, birthday, and address records.
The Kaduu researchers uncovered this data while performing routine scans on darknet and deep web forums. Their discovery emphasizes how even small e-commerce platforms are not immune to cyber threats 💻. In this article, you’ll find verified details, proof placeholders, and expert advice on how to minimize risk if you were affected.
What Happened? Discovery & Leak Timeline
The Guldsmed-Holmer.dk data breach was first listed on Darkforums.st on 06 October 2025. The leaker, camillaDF, claimed to have full database access, sharing sample schemas that matched common e-commerce database structures.
Kaduu analysts confirmed the dataset’s authenticity by cross-matching unique fields (like secure_key, id_customer, and optin) with real customer formatting patterns. Security feeds like VECERT also validated the incident as a legitimate dark web listing.
“We identified the Guldsmed-Holmer.dk database during a standard darknet sweep. The dataset is complete and contains multiple authentication tokens,” — Kaduu team statement 🔍
Forum Post Proof:
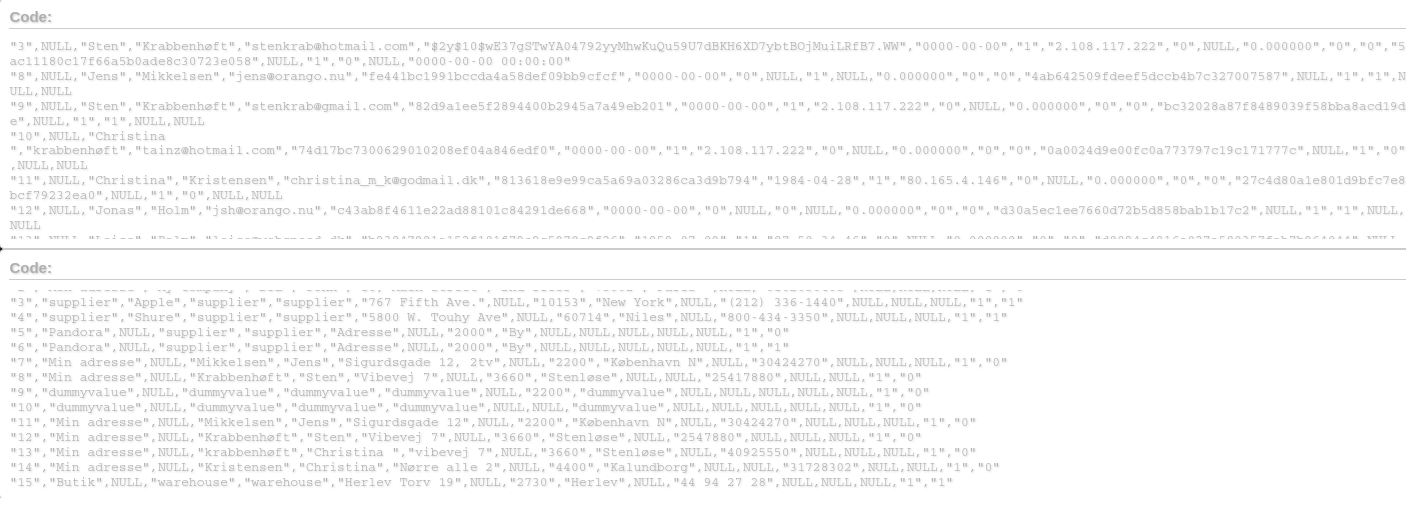
Sample Compromised Data:
What Data Was Compromised?
The Guldsmed-Holmer.dk breach involves both customer and address tables—indicating a deep compromise of the database.
Customer table fields:
“id_customer”,”ape”,”firstname”,”lastname”,”email”,”passwd”,”birthday”,”newsletter”,
“ip_registration_newsletter”,”optin”,”website”,”outstanding_allow_amount”,”show_public_prices”,
“max_payment_days”,”secure_key”,”note”,”active”,”is_guest”,”reset_password_token”,
“reset_password_validity”
Address table fields:
“id_address”,”alias”,”company”,”lastname”,”firstname”,”address1″,”address2″,
“postcode”,”city”,”other”,”phone”,”phone_mobile”,”vat_number”,”dni”,”active”,”deleted”
This data set exposes both personal and authentication details 🧠. Attackers can exploit these for phishing, account takeovers, or identity theft. Because password and reset tokens appear in the schema, the attacker likely obtained full database access rather than just scraping front-end forms.
Why This Breach Matters ⚠️
- Identity Theft & Fraud
Data such as full names, birthdays, and addresses can be weaponized for identity theft. Attackers can register accounts, apply for loans, or impersonate users in financial services.
- Account Takeovers
Because passwd and secure_key were exposed, users risk credential stuffing—where hackers reuse passwords on other platforms. Even hashed passwords can be cracked if weak algorithms (like MD5 or SHA-1) were used.
- Phishing & Scams 🎣
Armed with detailed personal information, scammers can send hyper-targeted phishing messages that appear legitimate. These may trick users into clicking links or providing additional sensitive information.
- GDPR & Legal Implications
Since Guldsmed-Holmer.dk operates in Denmark 🇩🇰, the GDPR requires mandatory disclosure and remediation. Regulatory fines can reach up to €20 million or 4% of annual revenue.
- Business Impact 💰
Beyond immediate costs, the data breach can reduce customer confidence. For a jewelry retailer, where trust and payment security are crucial, reputational damage could outlast the incident itself.
Similar Darknet Leaks in 2025
The Guldsmed Holmer incident is part of a wider surge in darknet leaks this year. Monitoring reports show a steady increase in full-database dumps targeting small to mid-sized European businesses.
Notable 2025 examples include:
- TikTok: 428 million user records leaked (darknetsearch.com).
- STMicroelectronics: Corporate and customer data compromised (darknetsearch.com).
- Dana-Farber Cancer Institute: Employee data traded on forums (darknetsearch.com).
Each breach shares common traits—complete schema exposure, credential data, and public darknet listings.
How Did Attackers Get In?
While the Darkforums.st post didn’t reveal methods, Kaduu’s analysts outlined possible vectors:
- SQL Injection — exploiting poorly sanitized web inputs 💉
- Misconfigured Database — direct exposure to the public web
- Stolen Credentials — weak admin passwords reused elsewhere
- Third-party Plugin Vulnerability — outdated CMS or extension
- Insider Threat — internal misuse or credential leak
The presence of reset_password_token strongly indicates direct database access rather than front-end exploitation.
User Checklist: How to Protect Yourself 🧾
Here’s a practical checklist to mitigate risk:
Change your Guldsmed-Holmer.dk account password immediately.
Avoid reusing passwords — employ a secure password manager.
Turn on two-factor authentication (2FA) wherever possible.
Watch out for emails with urgency or links — could be phishing.
Monitor your credit report and online banking transactions.
Report any suspicious communication pretending to be from Guldsmed Holmer.
Consider credit freezes or alerts if you’re in the EU or UK.
Regularly update devices and browsers to patch vulnerabilities.
💡 Practical Tip: Use a password manager that flags reused credentials automatically. It’s the easiest way to spot hidden risks before attackers do.
Corporate Response Plan 🛠️
To recover and rebuild trust, Guldsmed Holmer should adopt a transparent and proactive response:
- Immediate Containment – Isolate affected servers and disable database endpoints.
- Credential Reset – Invalidate tokens and force password resets.
- Incident Forensics – Hire independent security auditors to trace the intrusion.
- Disclosure Compliance – Notify Danish and EU authorities under GDPR.
- Customer Outreach – Email all potentially affected users with guidance.
- Ongoing Monitoring – Track for reposts or resale of the dataset on dark web monitoring platforms.
- Infrastructure Hardening – Encrypt sensitive fields, deploy WAF, and implement least-privilege database roles.
- Public Transparency Report – Publish breach details and mitigation steps to regain public trust.
Quick Q&A 💬
Q: Was my account password exposed?
A: Probably yes. The leaked dataset includes passwd and secure_key fields. Even if encrypted, passwords may be cracked over time. Change it now and enable 2FA wherever possible.
Risk & Threat Overview
| Data Type | Possible Abuse | Severity |
| Name + Email | Phishing, spam | High |
| Password fields | Account takeover | Critical |
| Birthday + Address | Identity theft | High |
| VAT / DNI | Fraudulent registration | Very High |
| Secure_key / Tokens | Credential replay | Critical |
Broader Cybersecurity Lessons 🌍
The Guldsmed-Holmer.dk breach teaches that no organization is too small to be targeted. Attackers often exploit overlooked vulnerabilities in lesser-known domains to resell verified personal data.
As noted by CyberSafe Institute (external source, DA 80):
“Small e-commerce sites are becoming low-hanging fruit for identity theft campaigns. Basic cyber hygiene can prevent 80% of such incidents.” (CyberSafe Institute Report 2025)
A strong defense requires:
- Regular vulnerability testing
- Strong encryption for personal data
- Real-time monitoring tools
- Employee cybersecurity awareness training
Conclusion 💥
The Guldsmed-Holmer.dk breach is a stark reminder that personal data security can be shattered overnight. This data breach exposed sensitive details, authentication tokens, and physical addresses—creating long-term risks for thousands of users.
If you’ve shopped at Guldsmed Holmer or used their website, take action now: change your password, monitor your email for suspicious activity, and report anything unusual.
🔎 Discover much more in our complete guide
🚀 Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


