TRAXNYC Data Breach Alert: 182K Customer Records Exposed – Full Report & Key Facts

➤Summary
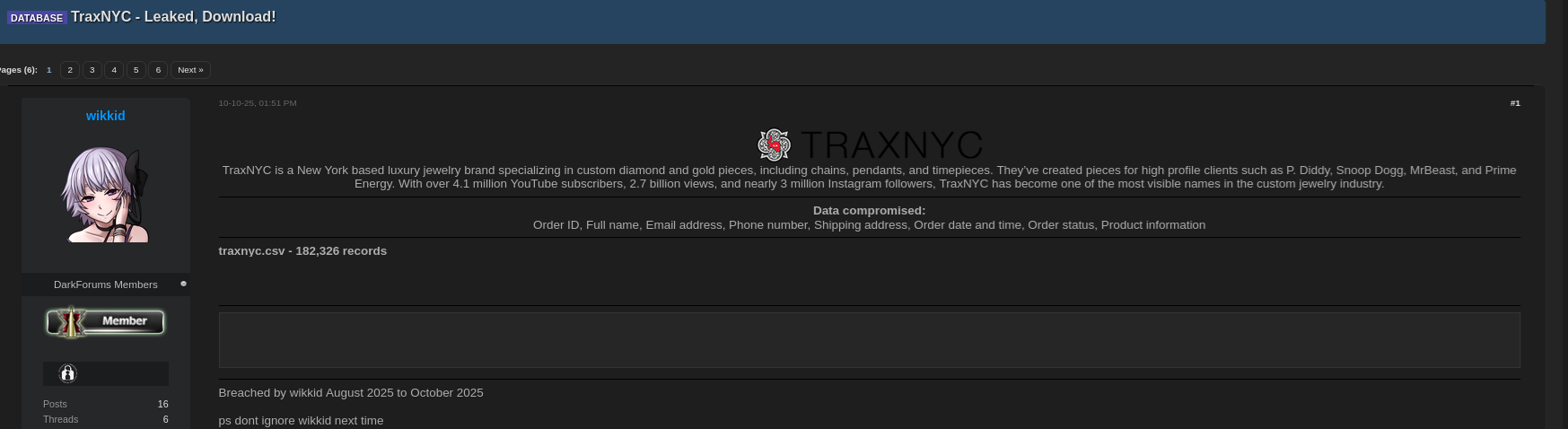
The shocking TRAXNYC data breach has sent alarm bells across the digital security world 🧠. Between August and October 2025, an alleged hacker known as “wikkid” claimed responsibility for leaking over 182,000 customer records from TRAXNYC, a major jewelry retailer. The exposed file, titled traxnyc.csv, reportedly includes sensitive information such as full names, emails, phone numbers, shipping addresses, and order details.
This alleged incident, posted on Darkforums.st, has quickly spread across cybersecurity channels and even surfaced on X (formerly Twitter). According to the post, the breach was a direct response to the company “ignoring” the hacker’s warnings — sparking serious debate about corporate data protection practices and consumer safety in the digital marketplace.
How the TRAXNYC Data Breach Unfolded
On Darkforums.st, the threat actor wikkid shared a thread titled DATABASE – TRAXNYC Leaked Download. The post, which has gained traction through reposts on social media and cybersecurity feeds, includes the line:
“traxnyc.csv – 182,326 records, ps don’t ignore wikkid next time.”
💻 The attacker also provided what appeared to be proof screenshots — one showing a list of data fields and another displaying sample entries with customer order information. These images, shared by @DarkEye_Team on X, quickly drew attention from dark web monitoring analysts and data protection specialists.
Date Range of Breach: August 2025 – October 2025
Forum: Darkforums.st
Claimed File: traxnyc.csv
Records Affected: 182,326
🖼️ Forum Post Proof Screenshot Placeholder
🖼️ Sample Data Screenshot Placeholder

What Data Was Allegedly Compromised
According to multiple cybersecurity observers, the dataset contains:
| Data Field | Description |
| Order ID | Unique transaction identifier |
| Full Name | First and last name of customers |
| Email Address | Contact email used for orders |
| Phone Number | Personal or business contact |
| Shipping Address | Physical delivery address |
| Order Date & Time | Timestamp of purchases |
| Order Status | “Shipped,” “Processing,” etc. |
| Product Information | Items purchased or viewed |
This mix of personal and transactional data makes the TRAXNYC data breach particularly dangerous. Attackers can easily combine these fields for phishing attacks, identity theft, or even fraudulent purchases.
Alleged Actor “wikkid” and Their Message
The author of the leak, known only as “wikkid”, is believed to have ties to various dark web communities. The tone of their message implies that Traxnyc was warned before the attack, though there’s no confirmation that such contact occurred.
Cyber experts tracking the situation note that wikkid’s history includes prior appearances in small-scale database leaks, but this marks their most significant exposure yet. “This appears to be both a retaliatory act and a signal of capability,” one analyst from Darknetsearch.com explained.
🔐 Expert Quote:
“When hackers publicly taunt a company after a leak, it often means they want attention more than profit,” says cybersecurity researcher Alex M. Kline. “But that doesn’t reduce the danger — victims still face real risks.”
How the Leak Spread Across the Internet
Within 24 hours of posting on Darkforums.st, screenshots and mirror links appeared across multiple Telegram channels and Twitter accounts connected to data breach sharing. Analysts from Darknetsearch.com detected the first repost at 10:45 AM (UTC) the following day, confirming that the data was already being redistributed on illicit networks.
The TRAXNYC customer data leaked 2025 event is now part of a worrying trend: attackers moving from ransom-based tactics to public shaming leaks. Instead of demanding payment, some hackers simply publish stolen data to harm a brand’s reputation — a phenomenon experts call “leak-and-leave.”
Potential Impact of the TRAXNYC Data Breach
The exposure of over 182,000 detailed customer records could have wide-reaching consequences:
- 📧 Phishing and scams: Attackers can impersonate TRAXNYC or delivery companies to trick victims into clicking malicious links.
- 📞 Smishing threats: Leaked phone numbers can be used for SMS-based attacks or spam.
- 📦 Identity theft: Combined data points like names and addresses can facilitate fraud.
- 💳 Financial fraud: Though no payment data is confirmed leaked, email and shipping info can still aid criminals.
- 💔 Reputation loss: TRAXNYC may face severe customer trust issues and legal liabilities.
How to Know if You Were Affected
If you made any purchase through TRAXNYC between mid-2024 and October 2025, it’s best to assume your information could be at risk.
Quick Checklist to Protect Yourself:
- Change your TRAXNYC account password immediately.
- Enable two-factor authentication (2FA) wherever possible.
- Be alert for phishing emails referencing your order or shipment.
- Report suspicious messages or calls pretending to be from TRAXNYC.
- Consider subscribing to dark web monitoring services to detect if your data appears online.
💡 Practical Tip:
You can verify potential exposure by visiting trusted cybersecurity lookup sites such as Darknetsearch.com for breach detection tools.
TRAXNYC’s Response (So Far)
As of publication, TRAXNYC has not made an official public statement regarding the alleged breach. Multiple cybersecurity reporters have reached out for comment, but no confirmation or denial has been provided.
Experts emphasize that companies facing breaches must communicate transparently. The longer the silence, the higher the reputational risk. According to global cybersecurity consultancy CyberWatch, early acknowledgment reduces misinformation and reassures affected customers.
Expert Analysis: What Makes This Breach Different
- Scale & Specificity – Over 182K real-world customer records, not just emails.
- Data Type Variety – Combines PII (Personally Identifiable Information) with purchase metadata.
- Motivation – The leak appears punitive, not financially motivated.
- Public Amplification – Quickly spread through social media rather than dark marketplaces.
- Verification Complexity – Screenshots provide “proof,” but forensic analysis is needed to confirm.
🧩 These elements make the TRAXNYC customer data leaked 2025 story not just another incident, but a case study in the shifting motivations of modern cyber threats.
What Should TRAXNYC Do Next?
Companies facing breaches of this scale should follow a structured incident response:
Immediate Steps:
- Contain and isolate affected systems.
- Launch an independent forensic investigation.
- Notify law enforcement and privacy regulators.
- Inform customers transparently.
- Offer credit or identity monitoring services.
Long-Term Actions:
- Conduct third-party penetration testing.
- Regularly train employees on cybersecurity hygiene.
- Encrypt all customer data at rest and in transit.
- Implement zero-trust architecture principles.
Is Your Data Safe After This?
A common question arises: “Can I prevent my information from being sold once leaked?” Unfortunately, once data appears in dark web markets, total removal is nearly impossible. However, active dark web monitoring and credit alert systems can detect misuse early and help minimize damage.
🧠 The best defense is prevention — frequent password changes, MFA, and using disposable emails for online purchases.
Related Cybersecurity Context
This incident follows a growing trend of retail and e-commerce breaches in 2025. Experts warn that similar attacks are likely to target small-to-mid-scale merchants. For additional verified reports and security checks, users can consult:
Conclusion: Stay Alert, Stay Protected ⚡
The TRAXNYC data breach — allegedly carried out by hacker “wikkid” — underscores a crucial truth: no business, no matter how established, is immune to cyber threats. The exposure of 182,000 customer records is not only a wake-up call for TRAXNYC but a reminder for all consumers to take proactive data protection measures.
As investigations continue, both users and businesses must act with urgency — changing passwords, monitoring data, and employing advanced dark web monitoring tools to mitigate risks.
👉 Discover much more in our complete guide
👉 Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


