Dark Web Monitoring Reveals Major Colombia Immigration Database Breach 2025

➤Summary
In a startling discovery, dark web monitoring has uncovered an alleged cyber incident exposing sensitive information from Colombia’s national immigration system. This case — known as the Colombia immigration database breach 2025 — involves nearly 1.5 million personal records reportedly leaked on a dark web forum named breachsta.rs. The post, authored by a user called koko, appeared on 11 October 2025 and quickly drew the attention of cybersecurity professionals worldwide 🌎.
The dataset allegedly contains personal information such as full names, physical addresses, national ID (DNI), phone numbers, email addresses, gender, nationality, migration status, and even entry dates. The Kaduu team, recognized for its expertise in cyber threat intelligence, discovered this leak during one of its routine sweeps across deep and dark web platforms.
With rising cyber threats targeting government databases, this discovery reinforces how essential deep web monitoring has become for detecting hidden risks before they escalate.
Screenshot – Proof of Forum post
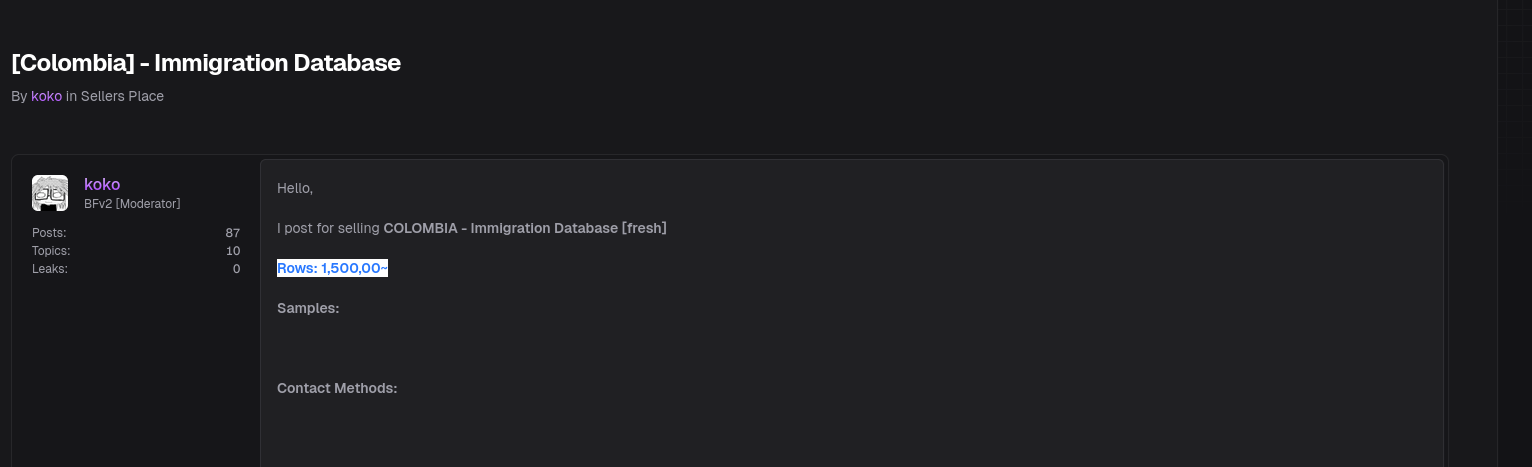
🔍 Discovery and Initial Findings
During a standard surveillance cycle across underground forums, Kaduu’s analysts stumbled upon a listing titled “COLOMBIA IMMIGRATION DATABASE — 1.5M ROWS — FULL INFO.” The listing appeared on breachsta.rs — a relatively new but increasingly active dark web forum.
Kaduu’s cyber threat intelligence analysts quickly began investigating. Early analysis revealed that the dataset structure resembled SQL export files containing fields typical of immigration systems. The post claimed the data originated from a live Colombian immigration database, and samples were offered as proof to potential buyers.
💡 Practical Tip: Organizations should implement continuous dark web and deep web monitoring to detect when employee or system credentials appear online. Early detection reduces breach impact dramatically.
🧾 What Data Was Allegedly Exposed
According to reports from analysts and early sample reviews, the compromised data fields include:
- 🧍 Full names
- 🏠 Physical addresses
- ☎️ Phone numbers
- 🪪 DNI / National identification numbers
- 🎂 Dates of birth
- ⚧ Gender
- 🌍 Nationality
- 📧 Email addresses
- 🛂 Migration status
- 📅 Entry or travel dates
Such detailed datasets can be exploited for identity theft, phishing attacks, social engineering, and even illegal migration assistance. The leak’s depth makes it potentially catastrophic if verified.
Screenshot – Sample Database
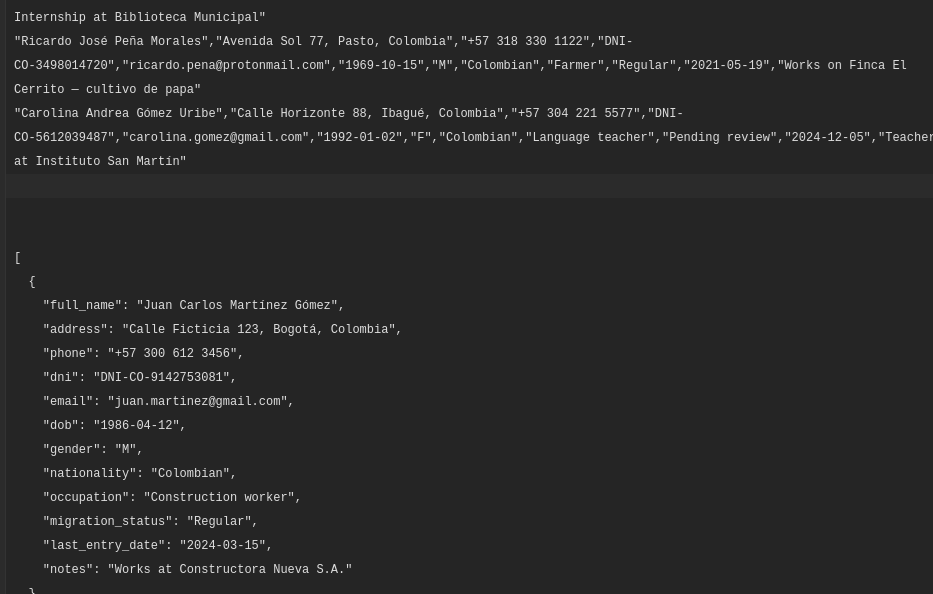
🕵️ Who Discovered It: The Role of Kaduu
The Kaduu Threat Intelligence Team — a regional cybersecurity collective known for its advanced cyber threat intelligence operations — identified the listing as part of their continuous watch of high-risk darknet channels. Their alert allowed government partners and private-sector analysts to begin verification immediately.
The discovery shows how valuable deep web monitoring has become to national cybersecurity defenses. Instead of waiting for breaches to surface in public media, analysts can identify underground chatter, file listings, and proof-of-concept attacks before they escalate into active exploitation.
“Monitoring the deep web isn’t about curiosity — it’s about protection. Hidden forums are where breaches begin their life cycle,” says María Castaño, Senior Analyst at Kaduu.
💻 Verification Efforts and Authenticity Status
At the time of writing, the authenticity of the Colombia immigration database breach 2025 remains under investigation. Independent analysts are reviewing:
- Metadata and file structures within leaked samples
- Field consistency with known government database formats
- Cross-checks with previously leaked or public data sources
- Evidence of live connections or outdated data
Some experts believe portions of the dataset might have been aggregated from older or open data breaches. However, others note the inclusion of highly specific “migration status” and “entry date” fields — suggesting at least partial access to genuine administrative systems.
If verified, this would mark one of the largest government-related information leaks in Latin America’s recent history.
📊 Impact and Potential Consequences
The potential impacts of this alleged breach span individuals, government agencies, and international partners.
| Group Affected | Potential Consequence |
| Citizens & Foreign Residents | Identity theft, blackmail, targeted scams |
| Government Agencies | Reputational damage, regulatory violations |
| International Stakeholders | Compromised border and visa data |
| Cybersecurity Community | Need for heightened defense strategies |
The breach, if authentic, could lead to cross-border misuse of travel records and increased criminal activity targeting individuals whose data has been exposed.
🧠 Expert Insight: Why Deep Web Investigation Matters
Deep web and dark web forums often act as the first points of data exchange for cybercriminals. By performing continuous deep web monitoring, organizations can intercept sensitive information as soon as it appears online.
Checklist: Effective Dark Web Monitoring Steps
✅ Automate scanning of dark web and paste sites
✅ Monitor for organizational and domain keywords
✅ Integrate threat alerts with SIEM tools
✅ Collaborate with law enforcement for takedowns
✅ Review results daily with a cyber intelligence team
This proactive defense strategy bridges the gap between a breach occurring and public awareness. As Diego Hernández, a cybersecurity strategist at CyberWatch Global, notes:
“Without deep web monitoring, organizations operate blindfolded in the most dangerous layer of the internet.”
🌎 The Broader Context: Data Breaches in Latin America
The alleged Colombian case aligns with an increasing pattern of attacks targeting Latin American government systems. Between 2024 and 2025, numerous public-sector breaches were reported in Mexico, Argentina, and Brazil — all involving sensitive citizen databases.
Analysts suggest these patterns reveal a trend of state-sponsored and criminal hybrid operations focusing on identity systems and immigration platforms. This may indicate either geopolitical motivations or profit-driven data resale strategies on dark web marketplaces.
Resources such as DarkNetSearch.com now track over 200 regional data breaches involving national ID and migration data, highlighting the scale of risk facing developing digital infrastructures.
🔐 Preventive Measures for Individuals and Institutions
If you believe your data could be involved in the Colombia immigration database breach 2025, or if you handle sensitive citizen information, the following steps are crucial:
For Individuals:
- Enable multi-factor authentication (MFA) on all accounts.
- Be cautious of messages claiming to be from immigration authorities.
- Avoid sharing private details over email or phone.
- Regularly monitor bank and credit records.
- Report suspicious immigration communications to the authorities.
For Organizations & Government Agencies:
- Conduct full infrastructure audits and privilege reviews.
- Deploy real-time network segmentation for database protection.
- Apply data encryption at rest and in transit.
- Implement an incident response playbook for rapid action.
- Partner with specialized firms offering deep web monitoring and response services.
💬 Question & Answer
Why does deep web monitoring matter in cybersecurity?
Because most leaks and attacks begin in hidden communities before surfacing publicly. With real-time monitoring, organizations gain visibility into stolen credentials, planned attacks, or exposed datasets — allowing immediate mitigation before widespread harm occurs.
🧰 Practical Tip: Building a Threat Intelligence Strategy
Creating a sustainable cyber threat intelligence program involves more than collecting data — it requires correlation, automation, and context. Organizations should:
- Build a centralized data lake for threat indicators.
- Correlate results from deep web sources with internal logs.
- Share intelligence with sector-specific ISACs.
- Update employee training on data handling and social engineering defense.
By linking cyber threat intelligence with cyber exposure monitoring, agencies and enterprises gain predictive power rather than reactive defense — transforming how they respond to digital threats.
🚨 Conclusion
The alleged Colombia immigration database breach 2025 underscores a critical message: security is no longer limited to what you can see. The dark web holds the earliest clues to emerging threats, and deep web monitoring is now indispensable for any institution responsible for citizen or client data.
While the authenticity of this breach remains under verification, its potential implications for identity protection and national security are undeniable. Government agencies and private sectors must enhance collaboration, transparency, and public communication to mitigate the next inevitable incident.
🌐 Explore related analysis at DarkNetSearch, where ongoing updates about regional breaches are published in real time.
For background, see the high-authority reference KrebsOnSecurity for comparisons to similar global government leaks.
🔹 Discover much more in our complete guide on threat monitoring and data breach response at DarkNetSearch.com.
🔹 Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


