Threat Intelligence Report: Suspected Oracle Breach – Sample Leak Analysis
➤Summary
Overview
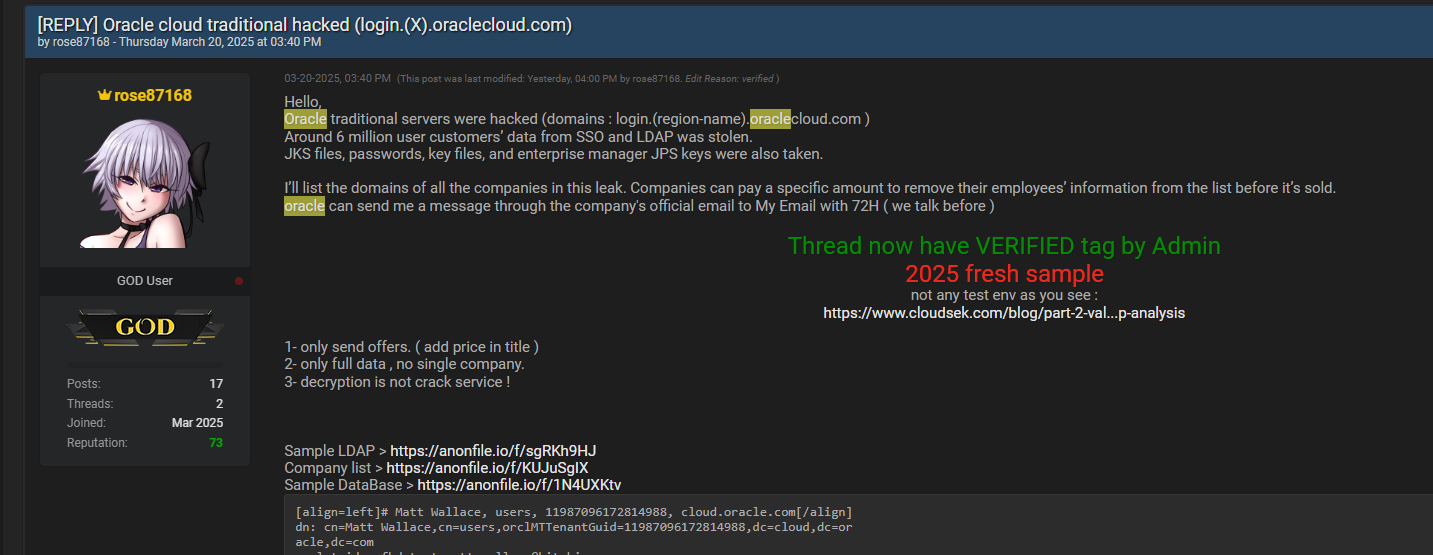
A sample allegedly from a breach of Oracle Cloud infrastructure has surfaced on BreachForums. The leaked material includes an LDAP directory export containing sensitive user information tied to Oracle’s multi-tenant architecture. Here are the samples companies mentioned:
This analysis examines the structure, contents, and implications of the leak, identifies potential attack surfaces, and maps the scope using associated organizational data.
Leak Structure & Content Breakdown
1. Source File: Sample_LDAP.txt
The file includes structured LDAP entries for users in an Oracle Cloud identity store, with attributes consistent with Oracle Identity Management and Fusion Middleware environments.
Key Attributes Extracted:
dn: Distinguished name indicating tenant structure indc=cloud,dc=oracle,dc=comorclmttenantguid: Same across all users —11987096172814988— suggests a single compromised tenantobjectclass: Includes sensitive Oracle IAM schema classes (orclIDXPerson,oblixOrgPerson)authpassword;oid: Multiple hashed password formats (SASL/MD5, MD5-DN, MD5-U)userpassword::: Base64 encoded, obfuscated passwordobpasswordexpirydate: Indicates old credentials (2018-05-24)tenantadmin,userreadprivilegeuc,userwriteprivilegeuc: Access role information for internal IAM groups
User Info Examples:
yamlCopyEditName: Pa****ck D*dd
Email: pa*ck_d**d@h**er.com
Tenant: efkd-test
Role: TenantAdminGroup
yamlCopyEditName: Li**a F**s
Email: li**a.f**us@f**p.com
Tenant: efkd-test
Role: Full IAM privileges
More than five users are included, each with similar attributes — implying a test or development environment, but with real user identities.
Technical Assessment
Evidence of Real Oracle IAM Environment
- The LDAP schema includes
orclMTTenantGuid,orclUserWritePrefsPrivilegeGroup, and Oblix identity management classes — Oracle-specific internal IAM attributes, which are unlikely to be fabricated.
Passwords not in plaintext
- Although
authpassword;oidvalues are shown in hash formats (MD5-based), MD5 is deprecated, and depending on Oracle’s hashing salt strategy, these could potentially be cracked.
Stale Credentials?
- The password expiry dates suggest this environment has not been actively maintained since 2018, raising the possibility this is a legacy tenant or a data snapshot from a dev/test backup.
Cross-Mapping to Known Organizations
Affected Companies (Found in the Company List)
All email domains from the leaked LDAP sample do exist in the Oracle-related company list. These domains are:
hitchiner.comfngp.comfnst.com
This strongly suggests that all identified users are associated with companies known to Oracle, either as clients, partners, or test users. None of the LDAP domains are missing from the company list. This means no obvious fake/test-only domains like example.com, test.local, etc., appear in the sample.
Company Footprint Analysis
Total Data Scope
- Total entries: 140,621 domain mentions
- Unique companies affected: 128,466
- Duplicated domains: 11,310 domains appeared more than once — likely due to:
- Multiple user accounts
- Multi-tenant overlaps
- Repeated organizational listings in IAM systems
Top-Level Domain (TLD) Analysis
These are the most common domain zones in the breached data:
| TLD | Count | Region |
|---|---|---|
.com | 70,971 | Global / US-centric |
.br | 4,432 | Brazil |
.jp | 3,424 | Japan |
.net | 3,280 | Global |
.org | 2,876 | Non-profits, EDU |
.de | 2,349 | Germany |
.uk | 2,290 | United Kingdom |
.it | 1,808 | Italy |
.mx | 1,523 | Mexico |
.au | 1,497 | Australia |
Strong international spread — not just North America. This suggests the compromised Oracle environment was used by global clients.
Free & Personal Email Providers
Only 17 domains in the list belong to generic email services (e.g., Gmail, Hotmail, Yahoo, QQ):
Examples include:
gmail.com(8 mentions)hotmail.com(4 mentions)icloud.com,qq.com,163.com, etc.
📌 This shows the overwhelming majority of entries are enterprise/company emails, not personal accounts — reinforcing the enterprise nature of this breach.
Duplicate Domains (Sample)
Some companies appear multiple times in the breach list. A few examples:
| Domain | Mentions |
|---|---|
gmail.com | 8 |
nov.com | 4 |
ironmountain.com | 2 |
kp.org | 3 |
shelfdrilling.com | 3 |
These may indicate:
- IAM groups across departments or regions
- Multiple users tied to one org
- Possible test vs prod duplication inside Oracle’s infrastructure
Takeaways
- This was not a superficial scrape — the list is too broad, diverse, and enterprise-focused.
- Oracle’s IAM data breach affected a massive international client base across sectors (tech, logistics, education, healthcare, manufacturing, etc.).
- The presence of repeated entries and global spread suggests the source environment may have been a shared multi-tenant Oracle Cloud IAM instance or a misconfigured global reporting snapshot.
Additional Insights
- All users are part of the same tenant (
efkd-test) with the sameorclMTTenantGuid. This tenant may be a shared environment or demo account used for multiple client-facing roles or support scenarios. - The consistent use of
@hitchiner.com,@fngp.com, and@fnst.commight indicate these companies share a joint environment, or Oracle used these domains in QA/dev environments with real partner data. - The presence of
TenantAdminGroupand full IAM access roles in these user entries implies privileged access — possibly partner-admins or implementation teams.
Discover how CISOs, SOC teams, and risk leaders use our platform to detect leaks, monitor the dark web, and prevent account takeover.
🚀Explore use cases →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.