Technical Analysis: The Challenges of Credential Monitoring

➤Summary
Introduction
Credential leaks represent a critical security challenge affecting millions of users and thousands of companies globally. This report leverages actual darknet forum leak data collected in our monitoring infrastructure to examine the scale of the problem, technical challenges involved in credential monitoring, the motivations behind the widespread publication of credentials by hackers, and the intrinsic value of leaked data for organizations.
How Do We Find Data Leaks?
Our team of full-time analysts conducts daily monitoring of various platforms, including hacker forums on the surface web, darknet, and Telegram channels. Each analyst is assigned a clearly defined area of focus, ensuring comprehensive coverage across different sources.
When we discover a data breach being offered for free, we promptly download and thoroughly investigate it. For breaches listed for sale, we acquire sample data whenever possible to notify our clients if their sensitive information might be at risk of exposure.
All collected information that could hold value for our clients is meticulously indexed. This includes a variety of formats, such as database files (e.g., SQL dumps), physical documents (e.g., Word, Excel, PDF), or text-based leak data (e.g., CSV or TXT files). Each breach undergoes a strict internal verification process by our team to confirm its authenticity and relevance.
Once verified, we enrich the data with metadata to provide essential context. Metadata includes details such as the source of the leak, the date of the breach, the type of data involved, and other relevant information. After this process, the verified and indexed data is uploaded to our system, making it searchable and accessible to all clients for further investigation.
Additionally, we employ automated scrapers designed specifically to parse data from Telegram channels and forums, allowing rapid identification and collection of potentially valuable leaks in real-time.
Overview of Credential Leaks Data in Kaduu
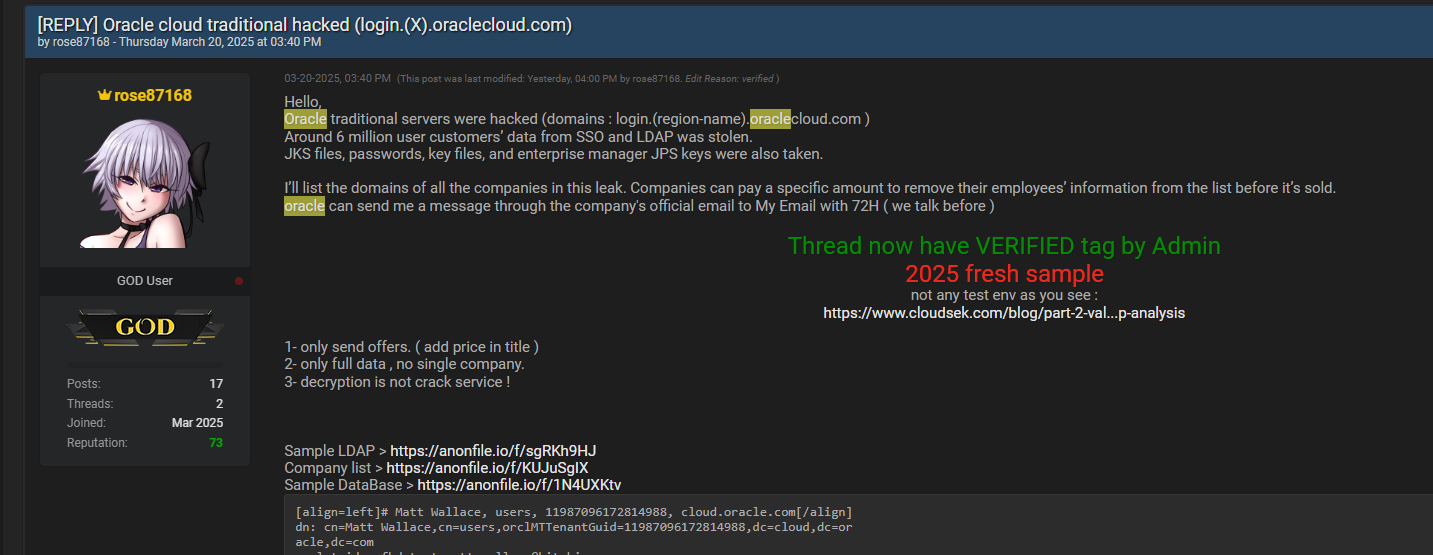
The dataset extracted from darknet forums showcases substantial credential leaks, regularly updated, exemplified by days like March 26, 2025, where 3.5 billion credentials were leaked in a single day, totaling 261 gigabytes.
| Date | Size (GB) | 10-day Avg. Size (GB) | Account Count | 10-day Avg. Accounts |
|---|---|---|---|---|
| 2025-03-27 | 15.37 | 60.53 | 235,869,237 | 678,572,097 |
| 2025-03-26 | 261.23 | 63.21 | 3,547,979,024 | 703,772,435 |
| 2025-03-25 | 26.37 | 37.69 | 1,515,202 | 349,713,331 |
| 2025-03-23 | 94.90 | 35.32 | 1,389,937,883 | 350,076,868 |
| 2025-03-21 | 5.14 | 26.39 | 10,410,135 | 211,270,698 |
| 2025-03-20 | 1.64 | 32.42 | 1,580,247 | 210,328,704 |
| 2025-03-19 | 8.19 | 39.21 | 3,340,624 | 248,832,766 |
| 2025-03-18 | 41.66 | 41.64 | 280,101,876 | 250,357,795 |
| 2025-03-17 | 26.05 | 37.84 | 264,015,800 | 222,621,414 |
| 2025-03-14 | 124.75 | 37.13 | 1,050,970,942 | 222,084,212 |
Why are There so Many Credentials?
Credential leaks primarily stem from widespread cyber-attacks, vulnerabilities exploited in software applications, poor password practices, and the aggregation of credentials from smaller leaks. Several key factors contributing to their vast numbers:
1. Frequency and Scale of Data Breaches
Data breaches have become increasingly common, exposing vast amounts of user credentials. In 2021, the U.S. experienced a record 1,862 data breaches, a 68% increase from the previous year. Such breaches often result from exploited vulnerabilities, unpatched systems, or weak security practices, leading to unauthorized access to sensitive information.
2. Password Reuse and Weak Password Practices
A significant contributor to credential leaks is the prevalent reuse of passwords across multiple platforms. Studies indicate that two-thirds of Americans use the same password for multiple accounts, and 13% use the same password for every account. This practice means that a single compromised password can grant unauthorized access to multiple accounts, amplifying the impact of a breach.
3. Advanced Cyberattack Techniques
Cybercriminals employ sophisticated methods to harvest credentials:
- Phishing Attacks: Deceptive communications trick individuals into revealing login information.
- Malware: Malicious software, such as keyloggers, captures user inputs, including passwords.
- Credential Stuffing: Automated tools test stolen credentials across various sites, exploiting password reuse.
4. Insider Threats and Misconfigurations
Insider actions, whether intentional or accidental, can lead to credential exposure. Employees may leak credentials for personal gain or due to negligence. Additionally, misconfigurations, such as unsecured databases or exposed APIs, can inadvertently expose login details.
5. Aggregation and Compilation of Leaked Data
Over time, cybercriminals compile credentials from multiple breaches into massive databases. Notable examples include the “RockYou2024” leak, containing nearly 10 billion unique plaintext passwords. Such compilations increase the availability of credentials for malicious activities.
6. Human Element in Security Breaches
Human error remains a significant factor in security incidents. In 2023, 74% of all breaches involved the human element, including errors, misuse, or social engineering attacks.
7. Growing Digital Footprint
As individuals and organizations expand their online presence, the number of digital accounts increases, elevating the potential points of compromise and contributing to the surge in leaked credentials.
Technical and Infrastructure Challenges
Credential leak processing involves extensive text analysis to extract useful information such as usernames, passwords, servers, URLs, IP addresses, and cookies. Practically, each line of leaked data must undergo evaluation against numerous regular expressions (regex).
For instance, we maintain more than 50 regex patterns to account for different credential structures. Examples include:
- Basic format:
user;password;https://server^(?P<User>[^;\s]+)\s*;\s*(?P<Password>[^;\s]+)\s*;\s*"?(?P<Server>(https?|ttps|ttp|tps|tp|ps|s|p|oid)://[^"\s;]+)"?$ - Complex structured format:
https://server|user|password^"?(?P<Server>(https?|ttps|ttp|tps|tp|ps|s|p|oid)://[^"\s|;]+)"?\s*\|\s*(?P<User>[^|]*)\s*\|\s*(?P<Password>[^\s]*)$
Each regex pattern must run sequentially against every individual line, significantly impacting processing speed and CPU resources. For example, processing the 261 GB dataset (over several billion lines of credentials) from March 26, 2025, could easily exceed several hours even when distributed across multiple CPU-intensive nodes. This scenario escalates infrastructure and cloud computing costs significantly.
Furthermore, an increasing number of regex patterns introduces potential conflicts and overlaps, leading to unintended matches, duplicated extraction, or missed credentials, thus compromising data quality.
Another significant technical challenge is the continuous evolution of leak formats. Hackers constantly devise new patterns or subtle variations to bypass automated detection, necessitating regular updates and refinements of existing regex rules. Keeping regex patterns up-to-date and accurate requires dedicated security analysts and continuous monitoring, substantially increasing operational complexity and maintenance efforts.
Challenges Summary
- Scalability and Storage: Handling terabytes of data demands distributed databases and robust storage solutions such as Apache Cassandra, Hadoop, or Elasticsearch clusters.
- Indexing Performance: Achieving real-time indexing necessitates optimization and tuning of platforms like Elasticsearch or Splunk, employing partitioning, sharding, and indexing optimization to manage the massive data influx.
- Hardware Requirements: Running extensive regex patterns against each data line is extremely CPU-intensive, significantly affecting processing speed and operational cost. For instance, storing and processing historical datasets and years of credential leaks would require substantial infrastructure, typically dozens of high-performance CPU nodes and multi-terabyte storage arrays.
- Regex Pattern Contradictions: Managing numerous regex patterns increases the risk of conflicting patterns, causing incorrect matches, duplication, or missed credentials. Such conflicts compromise the reliability of extracted data.
- Continuous Format Evolution: Hackers frequently introduce new credential formats, making comprehensive detection difficult. Regular adaptation and updating of regex patterns are critical, demanding ongoing research, validation, and iterative improvement by dedicated security teams. The rapidly evolving formats significantly increase operational complexity and resource allocation required for effective monitoring.
Motivations Behind Free Publication of Credentials
Despite potential commercial value, hackers often publish credentials freely for various reasons:
- Publicity and Reputation: Hackers publish leaks to demonstrate technical skills and build notoriety within the cybercriminal community.
- Diminishing Value: Credentials quickly lose market value. If data is outdated, previously exploited, or widely available, selling becomes less viable, leading to public release.
- Political/Ideological Motives: Some releases aim to damage specific companies or institutions out of ideological motivations rather than financial gain.
- Credential Stuffing: Wider circulation of credentials enables easier credential-stuffing attacks against numerous services.
Value of Credential Leak Data for Companies
Credential leak data offers substantial value to companies for security and preventive measures:
- Early Breach Detection: Companies proactively identify and react to breaches involving their employees or customers, mitigating risks.
- Password Hygiene and Compliance: Credential leak data encourages stronger security practices, mandatory password resets, multi-factor authentication, and regulatory compliance.
- Threat Intelligence: Companies integrate leak data into security systems to bolster defenses against credential-stuffing attacks and phishing.
- Customer Protection and Trust: Swift reaction to credential leaks maintains customer trust and reduces financial and reputational damages.
Data Accuracy, Timeliness, and Duplication Challenges
Our credential database is updated daily by a dedicated team of analysts who actively monitor hacker forums, Telegram channels, and darknet sources. The credentials available in our database search represent publicly leaked credentials, often released freely after hackers fail to sell them.
To access newer, actively traded credentials, users should utilize our live search tools or specialized hacker forum database searches on the deep web, providing real-time insights into fresh leaks.
Credential leaks often experience duplication, as data gets repackaged into multiple collections. Although our systems attempt to filter duplicates, users might still encounter repeated entries across breaches.
Additionally, due to dataset age, a significant portion—often exceeding 90%—may no longer be valid. Reasons include:
- Users changing passwords after breach exposure.
- Account deletions or suspensions by providers.
- Credentials becoming obsolete due to enhanced security protocols.
Consequently, older datasets have higher probabilities of outdated or inactive credential
Conclusion
Credential monitoring remains a technically challenging yet critical security practice. Infrastructure capable of storing, indexing, and analyzing vast, rapidly changing datasets is essential. Understanding hackers’ motivations further aids companies in adopting proactive cybersecurity measures. Continuous investment in robust infrastructure, efficient coding practices, and rigorous security standards is paramount to effectively manage and mitigate risks associated with credential leaks.
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.