SMS Marketing Data Breach: 2.8M Textitute Records Exposed

➤Summary
SMS marketing data breach incidents are escalating rapidly as communication platforms continue to store massive volumes of consumer and business data. The latest case involving Textitute.com demonstrates how marketing and push notification systems have become lucrative targets for threat actors. On 13 January 2026, a major SMS marketing data breach was disclosed on BreachForums, allegedly exposing more than 2.8 million records from Textitute’s client and contact databases. The leak includes SMS leads, user accounts, API tokens, password reset data, and expired demo records, placing businesses and consumers at significant risk 📱. This darknetsearch.com article provides a comprehensive breakdown of what happened, what data was exposed, and why this breach matters in the broader cybersecurity and data protection landscape.
What Happened in the Textitute Data Exposure
The breach was published on BreachForums.bf by the actor known as “Solonik,” a name frequently associated with large-scale database leaks. According to the disclosure, the attacker gained access to textitute.com and a co-hosted MySQL environment containing ten separate databases.
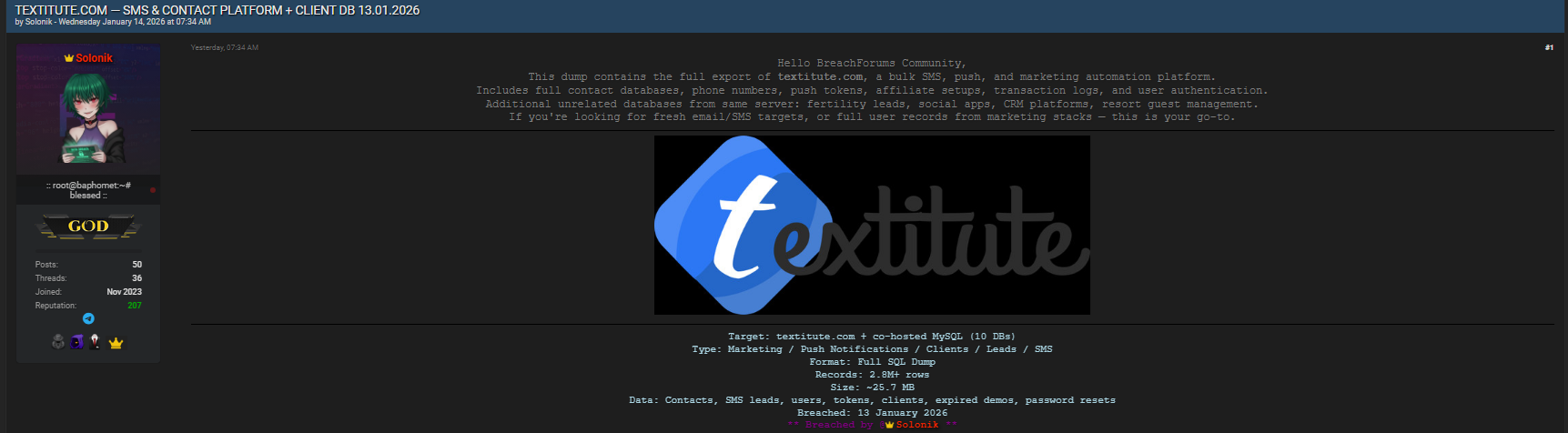
The compromised data was shared as a full SQL dump, totaling approximately 25.7 MB in size. Although smaller in file size compared to government breaches, this SMS marketing data breach is highly impactful due to the concentration of direct contact information and authentication-related data ⚠️.
Overview of the Compromised Platform
Textitute operates as an SMS and contact management platform used for marketing campaigns, push notifications, lead generation, and customer engagement. Platforms of this nature typically integrate with CRM systems, marketing automation tools, and API-based messaging services. As a result, a single SMS marketing data breach can expose not only raw contact lists but also campaign metadata, messaging tokens, and internal operational details used by businesses for outreach and customer retention 📊.
Scale and Structure of the Leaked Data
The leaked archive reportedly contains more than 2.8 million rows spread across ten MySQL databases. While the dataset size is modest, the value lies in the quality and usability of the records. SQL dumps preserve table relationships, making it easier for attackers to correlate users with phone numbers, message history, and authentication tokens. This makes the Textitute incident a textbook example of how marketing database leaks can quickly translate into real-world abuse 🚨.
Types of Data Allegedly Exposed
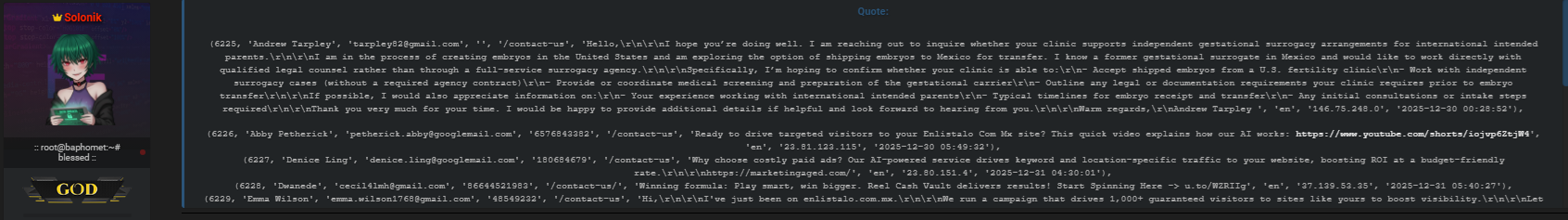
Based on the forum disclosure, the compromised dataset includes the following categories of information:
- Contact lists with phone numbers and lead metadata
- SMS campaign leads and message routing data
- User accounts and associated email addresses
- Authentication tokens and session-related values
- Client profiles and account configuration data
- Expired demo accounts with historical access
- Password reset records and timestamps
This combination significantly amplifies the risks associated with the SMS marketing data breach, as it enables both spam operations and account takeover attempts 🔐.
Why SMS and Marketing Platforms Are Prime Targets
Marketing platforms are attractive to attackers because they aggregate verified contact data at scale. Phone numbers and messaging tokens can be monetized quickly through spam campaigns, phishing attempts, and SIM-based fraud. Unlike generic credential leaks, an SMS marketing data breach provides immediate operational value, allowing attackers to launch campaigns with minimal setup. This explains the growing number of breaches targeting communication and push notification services 💡.
Risks to Businesses Using Textitute
Businesses relying on Textitute for customer communication may face several downstream consequences. Unauthorized access to SMS leads can damage brand trust and result in regulatory scrutiny. Compromised tokens could allow attackers to impersonate legitimate senders, while exposed user accounts increase the likelihood of credential reuse attacks. For companies operating in regulated markets, an SMS marketing data breach may also trigger contractual and compliance obligations 📉.
Risks to Individuals and End Users
For individuals whose phone numbers and contact details were exposed, the risks include increased spam, targeted phishing, and social engineering attacks. SMS-based scams are particularly effective due to their perceived legitimacy. If password reset data was included, attackers may attempt to map phone numbers to online accounts across other platforms. In short, this breach creates long-term exposure rather than a one-time inconvenience 📲.
How the Breach Was Shared on Underground Forums
The dataset was advertised and distributed via BreachForums, a well-known underground forum for data leaks and cybercrime activity. Such forums act as amplification points, allowing multiple threat actors to access and repurpose the same data. Dark web monitoring platforms frequently track these disclosures to help researchers and organizations understand emerging threats and leaked assets 🌐.
Legal and Compliance Implications
Depending on the geographic location of affected users, the Textitute breach may fall under multiple data protection frameworks, including GDPR, CCPA, and other privacy regulations. Marketing data is often subject to strict consent and retention requirements. A failure to adequately protect SMS leads and contact data can result in fines, audits, and mandatory breach notifications. Regulatory guidance on protecting personal data can be found via authoritative sources such as the European Commission’s GDPR portal.
Practical Checklist: What Organizations Should Do Next
If your organization used Textitute or similar SMS platforms, consider the following actions:
- Rotate API keys and revoke all active messaging tokens
- Reset passwords for all user accounts tied to the platform
- Review outbound SMS logs for unauthorized activity
- Notify customers about potential spam or phishing attempts
- Reassess third-party vendor security controls
Following this checklist can reduce the impact of an SMS marketing data breach and help restore operational integrity ✅.
One Key Question Answered
Can leaked SMS marketing data really be abused at scale?
Yes. Because the data includes verified phone numbers and messaging context, attackers can launch highly targeted campaigns with significantly higher success rates than random spam.
Expert Insight on Marketing Data Security
Cybersecurity professionals consistently warn that marketing systems are often overlooked in security audits. One industry analyst noted, “Communication platforms move fast and prioritize delivery and scale, but security controls frequently lag behind, making them ideal targets for data exfiltration.” This observation aligns closely with trends seen in recent SMS marketing data breach incidents 🧠.
Tracking Similar Breaches and Intelligence
To stay informed about similar leaks involving marketing platforms, CRM systems, and messaging services, readers can explore additional dak web reports and intelligence summaries on dark web monitoring platforms. Internal resources on darknetsearch.com also provide historical context and threat actor analysis related to BreachForums disclosures.
Key Takeaways from the Textitute Breach
The Textitute incident underscores how even mid-sized platforms can expose millions of records when security controls fail. An SMS marketing data breach has immediate operational consequences, enabling spam, fraud, and impersonation at scale. For businesses, this highlights the need to treat marketing infrastructure as critical systems rather than peripheral tools 🔎.
Conclusion and Call to Action
The exposure of over 2.8 million records from Textitute.com is a stark reminder that marketing and communication platforms are high-value targets in today’s threat landscape. An SMS marketing data breach can quickly evolve into widespread abuse if not addressed promptly. Staying informed, auditing vendors, and monitoring underground disclosures are essential steps for modern organizations. Discover much more in our complete guide. Request a demo NOW.
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


