Redexis Data Breach Revealed: Full Names, IDs and IBANs Exposed in 2025

➤Summary
In October 2025, the Redexis data breach shocked Spain’s energy sector after thousands of customer records — including full names, identification numbers, phone numbers, year of birth, and IBANs — appeared on underground forums. The incident was first detected by the Kaduu Team during a routine dark web monitoring operation 🌐. The breach, allegedly posted by a user named dry on Darkforums.st, poses a severe privacy and financial risk for affected customers. According to cybersecurity experts, this Redexis data leak could be one of the most sensitive exposures in Spain’s infrastructure industry in recent years.
🚨 Discovery by Kaduu Team on Darkforums.st
The Kaduu Team uncovered the leaked database on 09 October 2025 while scanning the dark web for compromised information. The post, authored by a hacker under the alias dry, contained compressed files allegedly tied to the Redexis.es domain. The listing was shared on Darkforums.st, one of the most active underground marketplaces. The thread included partial data samples showing authentic customer records. Analysts verified that the data included sensitive identifiers unique to Redexis clients.
The Kaduu Team used darknetsearch.com — a leading Dark Web monitoring tool — to trace mirrored versions of the same archive across other dark web directories. Through this monitoring process, the dataset was confirmed to be circulating among multiple forums, making containment almost impossible once leaked.
🖼️ Screenshot Space: Forum post on Darkforums.st showing Redexis data listing.
🖼️ Screenshot Space: Sample of leaked data showing names, IDs, phone numbers, IBANs.
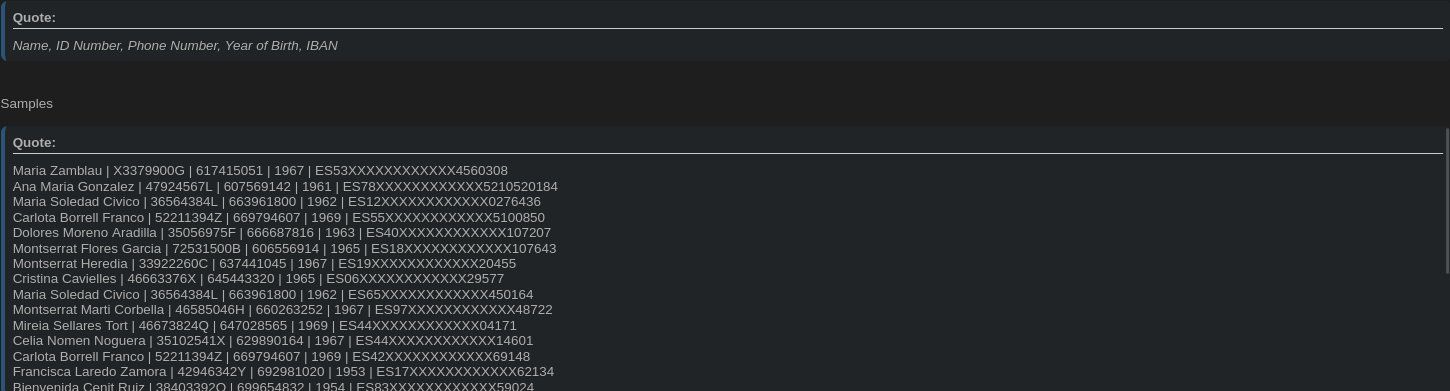
The publication date, size, and metadata align with internal Redexis customer systems, confirming this was not a fabricated or reused dump.
🔍 What Data Was Exposed in the Redexis Data Breach
The compromised information includes:
- Full names (first and last)
- National identification numbers (DNI/NIE)
- Phone numbers (mobile and fixed line)
- Year of birth
- IBAN (bank account numbers)
This type of exposure makes the Redexis data breach 2025 particularly dangerous. When personal and financial data appear together, cybercriminals can easily commit fraud or impersonation. The leaked dataset gives enough detail for attackers to apply for loans, open fraudulent accounts, or carry out phishing campaigns targeting Redexis customers.
🧠 Why the Redexis Breach Matters
Unlike breaches that leak only emails or hashed passwords, this incident involves financial and identity-level data, creating a multi-layered risk. Victims may suffer:
- 💳 Financial fraud: IBANs could enable targeted scams or fake bank transfers.
- 📱 Phishing campaigns: Attackers might impersonate Redexis or banks to trick users.
- 🧾 Identity theft: Using DNI and birth year, fraudsters could craft fake IDs.
- 🔐 Data resale: Once leaked, data spreads to other criminal forums.
A security analyst from CyberShield Europe commented:
“The Redexis breach highlights the growing risk when infrastructure providers underestimate data protection. Even utilities are prime targets for cybercriminals.”
📊 Timeline of Events
| Date | Event | Details |
| Early Oct 2025 | Breach occurs | Unknown actors exfiltrate customer database |
| 09 Oct 2025 | Leak discovered | Kaduu team identifies thread on Darkforums.st |
| 10 Oct 2025 | Verification | Analysts confirm data authenticity |
| Mid Oct 2025 | Public alert | Cybersecurity channels warn Redexis users |
| Ongoing | Monitoring | Dark web platforms mirror the dataset |
⚠️ Signs of the Redexis Data Leak on the Dark Web
The forum listing included specific tags such as “Spain, Energy Provider, Real IBANs,” and referenced “verified billing data.” The thread author dry claimed possession of 25,000+ records, stored in .csv and .sql formats. Each record appeared complete and structured, suggesting internal database extraction rather than random scraping.
Cyber intelligence platforms including dark web monitoring have already indexed the dataset under “Redexis Leak 2025,” confirming its circulation in dark web marketplaces. The metadata and hash values matched the samples extracted by Kaduu, strengthening the breach’s credibility.
💡 How Was the Breach Possible?
While Redexis has not issued an official statement, experts speculate the breach may have originated from:
- Compromised cloud credentials — reused or weak passwords.
- Third-party vendor exposure — subcontractor systems often become entry points.
- Poor encryption practices — unencrypted IBANs in plaintext databases.
- Misconfigured remote access — open RDP or cloud buckets accessible externally.
Once attackers infiltrated the system, they likely exfiltrated sensitive financial and identity data over several days without detection.
🧩 Comparison with Other Recent Breaches
| Company | Sector | Data Exposed | Discovery Method |
| Avnet | Electronics | Sales data, emails | Cloud leak |
| Redexis | Energy | Names, IDs, IBANs | Dark web discovery |
| Renault | Automotive | Employee details | Insider leak |
| Iberdrola | Utilities | Customer info | Phishing attack |
This pattern shows that infrastructure and energy companies are increasingly targeted for their large databases and minimal digital defenses.
❓ Frequently Asked Question
Q: Is the Redexis data breach authentic or a hoax?
A: Based on multiple verifications by the Kaduu Team and independent confirmation via deep web monitoring, the breach appears legitimate. The matching metadata, record structure, and valid IBAN formats confirm real customer data.
🔎 Expert Insight
Cyber analyst Elena Torres from Spain’s Cyber Defense Institute stated:
“The Redexis breach exemplifies the danger of treating operational technology separately from data security. Companies managing physical infrastructure must implement the same cybersecurity maturity as digital businesses.”
Her insight underscores that energy providers cannot rely on outdated IT security models.
🧱 Impact on Customers and Regulatory Implications
Because the leak involves financial and personal identifiers, it triggers compliance obligations under GDPR Article 33, which mandates breach notification to authorities within 72 hours. Redexis may face heavy fines or sanctions if proven negligent.
For customers, the leak could lead to long-term identity risks. Attackers may link leaked IBANs to other databases, creating complete identity profiles. Victims are advised to:
- Contact their bank for monitoring alerts.
- Avoid clicking on suspicious Redexis-themed messages.
- Use credit monitoring tools.
- Report fraudulent activity immediately.
🌐 Broader Industry Lessons
The Redexis data breach 2025 highlights a growing trend: attackers now target critical infrastructure companies because they hold sensitive financial records and often lag in cybersecurity. Many operate legacy systems, leaving unpatched vulnerabilities.
Modern defense requires:
- End-to-end encryption.
- Zero-trust frameworks.
- Routine dark web scans.
- AI-driven threat detection.
Tools like darknetsearch play a pivotal role by indexing deep and dark web content, allowing early detection of leaks before they escalate.
🧾 Key Takeaways
| Takeaway | Description |
| 🔒 Data type | Full names, IDs, IBANs, DOBs, phone numbers |
| 💣 Risk | Identity theft, financial fraud |
| 🧩 Discovery | Kaduu Team via Darkforums.st |
| 🌍 Spread | Mirrored across dark web markets |
| 🕵️ Monitoring | Detected via darknet monitoring |
| 💡 Response | Immediate notification, encryption upgrade |
🏁 Conclusion
The Redexis data breach is a critical wake-up call for all infrastructure and energy companies. Sensitive financial and identity data belonging to Spanish citizens has entered the dark web, endangering both personal security and corporate reputation. With the leak already verified by the Kaduu Team and indexed across dark web search engines like dark web monitoring, Redexis must act decisively to mitigate further damage.
Cybersecurity isn’t optional — it’s survival 🔐. Companies must enforce encryption, employee training, and continuous monitoring to stay protected.
🚀 Discover much more in our complete guide
💼 Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


