Cisco ThousandEyes: Urgent Guide — 7 Key Risks of a Listed “Full Access” Sale (2025)

➤Summary
Cisco ThousandEyes is a powerful network and digital-experience monitoring platform that offers deep visibility into global internet performance. When a hacker claims to be selling full access to Cisco ThousandEyes system, it represents a serious cybersecurity threat that could expose sensitive telemetry, API tokens, and infrastructure data. Recently, on Breachsta.rs, a post appeared advertising full access to a company’s ThousandEyes environment — and it has caught the attention of cybersecurity experts and deep web monitoring teams worldwide. 🚨🔍
Breachsta.rs listing summary: what happened?
On 01 October 2025, a seller known as rider published a thread on the dark-web forum Breachsta.rs titled:
[SELLING] Full Access Thousandeyes-Corporate /RDP/ API Tokens.
According to the author, the sale includes remote access to a private company’s Cisco ThousandEyes platform, the ability to create and edit agents and tests, and active API tokens with data export enabled. The asking price? $20,000. 💸
The post states that the company name will only be shared privately to avoid attention from the target’s CTI team. This secrecy is typical of dark-web access brokers who want to attract buyers while evading takedowns.
What is Cisco ThousandEyes? (Understanding the system)
Cisco ThousandEyes is a cloud-based network intelligence and digital-experience monitoring platform that helps organizations visualize, test, and analyze the performance of their internal and external networks. It can measure latency, packet loss, DNS resolution, and HTTP performance, and it also integrates with BGP data to show routing changes across the internet.
The system uses distributed agents — deployed in data centers, endpoints, or cloud regions — to simulate real user experiences and detect issues. Through its APIs, ThousandEyes lets companies export test results, automate configuration, and feed telemetry into other systems. This power and visibility make it a prized target for cybercriminals. ⚙️📡
If unauthorized actors gain admin-level access, they can see network maps, vendor dependencies, and internal IP data. That’s why selling full access to Cisco ThousandEyes system is a red flag for any enterprise’s security team.
Why full access is dangerous: 7 main risks ⚠️
- Exposure of internal telemetry: Hackers could view network paths, internal DNS entries, and routing details.
- Manipulation of monitoring: By editing or disabling tests, they could hide malicious activity.
- API token misuse: Active tokens allow API-level automation, data extraction, and agent control.
- Data exfiltration: Exported telemetry might contain confidential metrics or partner details.
- Operational disruption: Flooding the network with fake agents could slow down diagnostics.
- Third-party compromise: ThousandEyes reveals supplier connections — a gateway for supply-chain attacks.
- Dark-web resale and escalation: Once sold, access often fuels ransomware and follow-on intrusions. 🧭🔥
“Unauthorized access to monitoring infrastructure offers attackers the same visibility defenders rely on — making it doubly dangerous,” says a senior analyst from DarknetSearch’s dark web monitoring division.
Proof of post (for documentation):
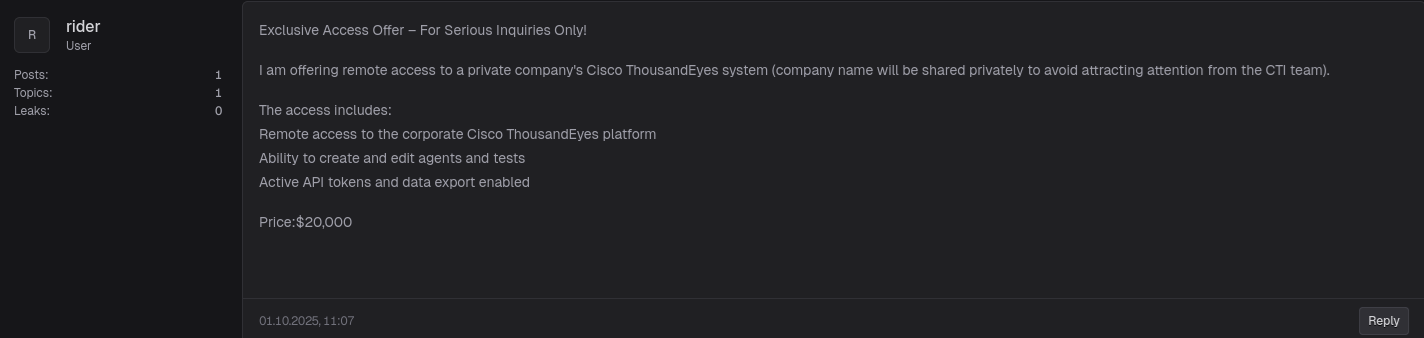
“I am offering remote access to a private company’s Cisco ThousandEyes system (company name will be shared privately to avoid attracting attention from the CTI team). The access includes remote access to the corporate Cisco ThousandEyes platform, ability to create and edit agents and tests, and active API tokens with data export enabled.” — rider, Breachsta.rs, 01 Oct 2025.
The darknet economy behind such listings
Listings that sell RDP access or API tokens like this have become a growing trade on underground markets. Cybercriminals buy these access packages to move deeper into networks or resell them to ransomware affiliates.
Darknet intelligence teams like DarknetSearch monitor these forums daily. Their dark web monitoring service identifies leaked credentials, database sales, and suspicious access offers before they escalate into breaches.
A $20,000 listing indicates perceived value — suggesting privileged credentials or verified console access. Still, many such offers are fake or exaggerated, which is why monitoring and verification are essential.
Can hackers hide their activities through ThousandEyes?
Yes — if attackers have full administrative control, they can manipulate tests or alerts, effectively blinding security operations. By deleting or muting specific tests, they could make real network anomalies go unnoticed.
That’s why enterprises must protect monitoring and logging systems with the same rigor as production infrastructure. 🛡️
Practical tip and quick checklist ✅
Practical Tip:
If your organization uses Cisco ThousandEyes, implement strict RBAC policies and rotate all API tokens regularly.
Checklist for Security Teams:
• Rotate and revoke all active API tokens.
• Audit test and agent configurations for recent changes.
• Review export logs for abnormal download volumes.
• Check for unauthorized user sessions or new admins.
• Contact Cisco ThousandEyes Security Response Team for assistance.
• Report suspicious listings to law enforcement and dark-web monitoring providers.
Table: what compromised access means
| Possible Risk | Description |
| ✓Network exposure | Reveals internal IPs, DNS, and dependencies |
| ✓API abuse | Tokens could be used to manipulate monitoring |
| ✓Data theft | Exported telemetry may contain sensitive data |
| ✓Operational disruption | Misused tests can overwhelm infrastructure |
Expert insight 🗣️
According to Cisco documentation, ThousandEyes’ architecture was designed for visibility, not secrecy: “ThousandEyes provides insight into network paths and dependencies across multiple providers.” That same openness becomes a risk when access falls into the wrong hands.
Defensive response plan 🧩
- Contain: Immediately disable compromised accounts and revoke API keys.
- Investigate: Check audit trails for unusual test creation or deletion.
- Engage vendor: Open a case with Cisco’s security team.
- Harden: Enforce MFA and least-privilege permissions for all admins.
- Monitor: Set alerts for new agents or configuration changes.
- Report: Notify law enforcement, CERT, and threat-intel partners like DarknetSearch.
- Educate: Train teams to identify and respond to forum-based breach claims.
Legal & ethical reminder ⚖️
Buying or selling corporate access — including Cisco ThousandEyes credentials — violates cybersecurity laws worldwide. The purpose of this report is educational: to raise awareness and support defenders. Any discovery of such listings should be escalated to proper authorities.
Why continuous dark web monitoring matters 🌐
Organizations can’t stop underground postings, but they can detect them faster. Tools like DarknetSearch Dark Web Monitoring continuously scan hidden forums, Tor networks, and credential markets to alert companies of compromised data or impersonated assets.
Combined with API key rotation and user-access reviews, this proactive defense can reduce the time between exposure and response — a critical factor in minimizing damage.
Quick question to ask your SOC team
“If our ThousandEyes data or API tokens appeared for sale today, how quickly would we know?”
If the answer isn’t “immediately,” then it’s time to integrate automated dark web monitoring and credential-alert feeds into your threat-intelligence workflow.
Conclusion and next steps 🎯
The Breachsta.rs listing allegedly selling full access to Cisco ThousandEyes system shows how deep-web marketplaces are evolving — targeting monitoring and observability tools that give unparalleled insight into corporate infrastructure.
For defenders, awareness is power. Audit your ThousandEyes deployment, monitor for credential leaks, and engage trusted partners to protect your organization’s data.
✅ Discover much more in our complete guide
✅ Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


