Neotel.us data breach: 7 key facts on 773K records

➤Summary
The neotel.us data breach has emerged as an alleged exposure of more than 773,000 records, following a post published on the Breachforums.bf forum by the threat actor known as Shenron. According to the disclosure, the breach itself dates back to 2025, while the data leak was reportedly released publicly in 2026. Although the dataset does not appear to include passwords or direct financial credentials, the neotel.us data breach is still relevant due to the structured nature of the information involved and the operational insights it may reveal. This darknetsearch.com article provides a clear and objective breakdown of what is known so far, what data was compromised, why this type of leak still matters, and how organizations can reduce long-term exposure risks 🔐
Overview of the alleged Neotel.us incident
The neotel.us data breach refers to a dataset allegedly sourced from systems linked to the neotel.us domain and later shared within an underground forum environment. Rather than a traditional credential leak, this incident appears to involve internal records tied to customer accounts, payment responsibility, and account status. At scale, even non-authentication data can be valuable. Security researchers emphasize that large datasets often gain value through correlation. The neotel.us data breach fits this pattern, where context and structure matter as much as raw sensitivity ⚠️
Timeline, forum source, and attribution
Based on the forum post, the breach is said to have occurred in 2025, with the leaked data surfacing publicly in 2026. The platform cited, Breachforums.bf, is widely monitored by cybersecurity analysts due to its role in distributing and discussing compromised datasets. The author, Shenron, has previously been associated with multiple alleged disclosures, lending credibility to the claim even in the absence of official confirmation. For the neotel.us data breach, the delay between breach and release suggests the data may have circulated privately before becoming widely visible ⏳
Scope and structure of compromised data
The dataset connected to the neotel.us data breach reportedly contains 773,757 rows and a wide range of structured fields. These include internal identifiers, client references, DNI values, phone numbers, SMS contact fields, payment responsibility indicators, validation status, account opening dates, delinquency days, portfolio assignments, financial totals, agreement states, and internal user actions. Names and phone-related information appear within the records, which increases their potential usefulness.
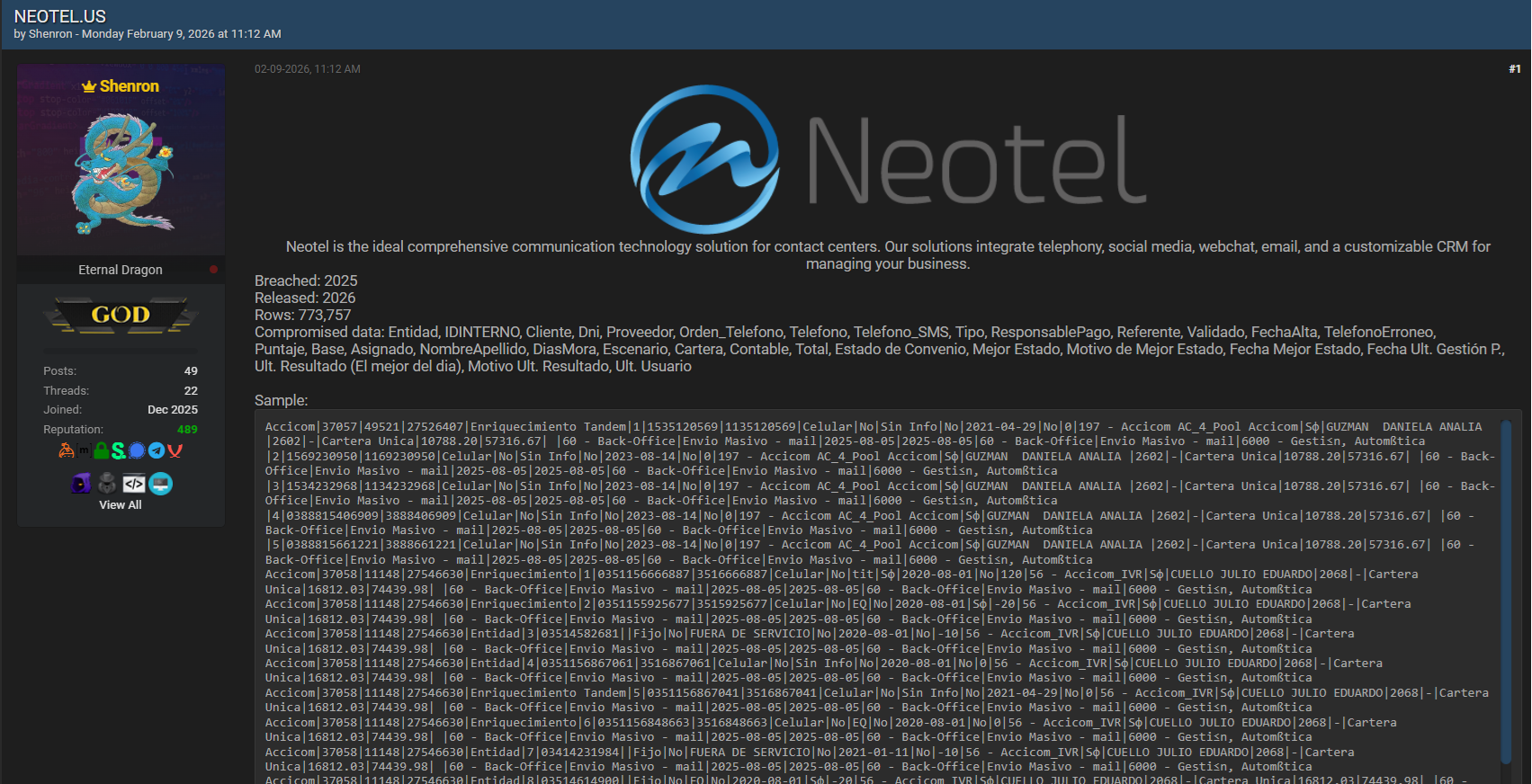
While not catastrophic on its own, the neotel.us data breach involves enough contextual data to warrant attention 📊
Why structured operational leaks are still risky
A frequent question is whether breaches without passwords truly matter. The clear answer is yes. The neotel.us data breach shows how operational and administrative data can enable social engineering, targeted scams, or internal process abuse. Attackers can use payment status, delinquency indicators, or account history to impersonate legitimate agents convincingly. Even partial datasets can support fraud when combined with other sources. The neotel.us data breach illustrates how risk often lies in aggregation rather than any single field 🔗
Realistic risk assessment for affected parties
The immediate risk level associated with the neotel.us data breach is best described as moderate. There is no indication of direct account takeover capability, but exposure of names, phone numbers, and internal account details can lead to targeted outreach or impersonation attempts. Organizations may also face reputational concerns or regulatory scrutiny depending on jurisdiction. Understanding proportional risk helps prevent both panic and inaction. The neotel.us data breach should be treated as a warning signal rather than dismissed outright 🎯
Underground circulation and monitoring insights
Once a dataset like the neotel.us data breach appears on an underground forum, it rarely remains isolated. Copies are often redistributed, indexed, and bundled with other leaks. This is why organizations rely on data breach detection and other dark web solution and other information to track exposure beyond the initial disclosure. Dark web monitoring platforms help security teams understand where data resurfaces and how it evolves over time 🔍
Connection to broader data exposure trends
The neotel.us data breach aligns with a wider shift toward leaks involving internal business and collections-related systems. These datasets reveal workflows, financial states, and customer behavior, which attackers can exploit creatively. Over time, repeated exposures of this kind build detailed intelligence profiles. The neotel.us data breach should therefore be viewed as part of a cumulative risk environment rather than an isolated incident 📈
Practical checklist after potential exposure
If your organization or customers may be linked to the neotel.us data breach, consider the following steps:
• Confirm exposure using trusted intelligence sources like Darknetsearch.com
• Strengthen verification for phone-based or payment-related communications
• Brief staff on impersonation and social engineering risks
• Document actions taken for compliance and audit purposes
• Monitor for secondary misuse of exposed data
This checklist helps translate awareness into measurable risk reduction 🛡️
Platform responsibility and prevention measures
Even when breaches involve operational data rather than credentials, prevention still matters. Access controls, logging, anomaly detection, and data minimization reduce the impact of unauthorized extraction. Transparency is equally important. High-authority guidance from sources such as https://www.cisa.gov emphasizes early communication and user education as key elements of incident response. The neotel.us data breach reinforces the need for proactive governance across all data layers 📢
Expert insight on operational data leaks
Security analysts often note that “operational data reveals intent and opportunity.” In the context of the neotel.us data breach, fields related to payment status, delinquency days, and internal actions can guide attackers toward high-probability targets. Experts recommend treating such datasets seriously, even when headlines suggest limited sensitivity, because attackers focus on efficiency, not optics 👀
The bigger picture for organizations
The neotel.us data breach highlights how modern data risk is incremental. One dataset may seem manageable, but combined with others it becomes actionable intelligence. Organizations that classify, monitor, and limit exposure of all data—not just login credentials—are better positioned to manage this reality. Awareness and continuous monitoring now define resilience in a data-driven environment 🔄
Conclusion and next steps
The alleged neotel.us data breach may not represent the most severe exposure of recent years, but its scale and structured content make it relevant for security teams and affected stakeholders. Understanding what was leaked, how such data circulates, and how attackers reuse it enables smarter responses and better protection. Staying proactive, informed, and monitored is the most effective way to reduce long-term impact. Discover much more in our complete guide to data exposure intelligence. Request a demo NOW to see how continuous monitoring can protect your organization 🚀
Disclaimer: DarknetSearch reports on publicly available threat-intelligence sources. Inclusion of an organization in an article does not imply confirmed compromise. All claims are attributed to external sources unless explicitly verified.
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


