Jamendo data breach: 6 key facts on 6.5M user emails

➤Summary
The Jamendo data breach has drawn attention across cybersecurity communities after an alleged scrape involving more than 6.5 million user records was shared on Breachforums.bf in February 2026. Jamendo, widely known as a music-sharing and licensing platform, hosts millions of artists and listeners worldwide, which makes even limited data exposure relevant at scale. According to the forum post published by the author “pine,” the incident centers primarily on user email addresses linked to platform profiles. While the author downplays the sensitivity of the data, the Jamendo data breach still raises important questions about user privacy, reuse of scraped data, and how such datasets are leveraged within underground ecosystems. This darknetsearch.com article explains what happened, what data was involved, why it matters despite limitations, and how users and organizations should respond 🎧
Overview of the alleged Jamendo.com incident
The Jamendo data breach refers to an alleged scraping operation rather than a confirmed system intrusion. Scraping typically involves automated collection of publicly accessible or weakly protected data, which can still violate platform policies and user expectations. The dataset allegedly contains 6,555,206 Jamendo user entries, though the author notes that only around 4 million records actually include email addresses. The remaining profiles reportedly lack meaningful personal data, reducing their standalone value. However, even partial datasets at this scale can become powerful when combined with other leaks.

The Jamendo data breach highlights how music platforms, often viewed as low-risk, can still contribute to broader exposure chains 🎶
Timeline, forum source, and disclosure context
According to the disclosure, the dataset was shared on Breachforums.bf on 08 February 2026. The author “pine” described the scrape openly, emphasizing that it was not particularly “interesting” due to the limited depth of personal information. Despite this framing, cybersecurity professionals monitor such disclosures closely because scraped data often resurfaces in phishing campaigns months or even years later. The Jamendo data breach fits a familiar pattern: a niche platform becomes part of a much larger data aggregation ecosystem. Once published, scraped databases tend to spread quickly across private channels and mirrored repositories ⚠️
What data was compromised
The compromised fields in the Jamendo data breach include user ID, display name, email address (where available), gender, biography, managedArtistIds, and a superAdmin flag. No passwords, payment data, or direct authentication secrets were reported. The author also notes that Jamendo’s registration process autofills the display name using the email username, meaning many profiles reveal little beyond an email-derived alias.
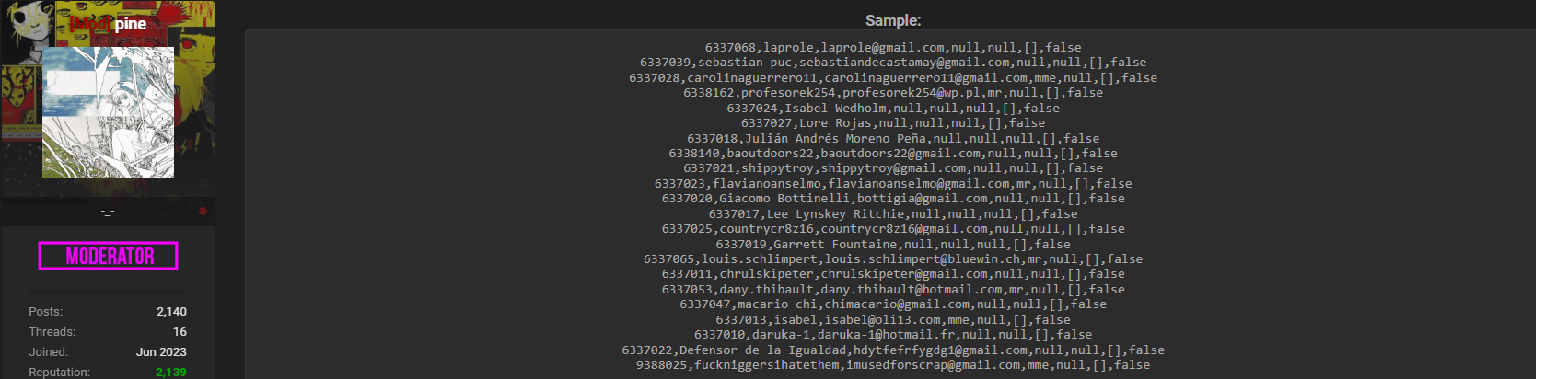
Does this make the leak harmless? Not entirely. Email addresses remain one of the most valuable identifiers in cybercrime because they enable direct contact and correlation with other breaches. The Jamendo data breach therefore still presents measurable risk 📩
Why email-only scrapes still matter
Even when datasets appear “low value,” the Jamendo data breach demonstrates why email-focused scrapes are actively traded. Email addresses act as universal keys across platforms. Attackers can cross-reference them with other breaches to build richer profiles, launch credential-stuffing attacks, or design convincing phishing messages. In many cases, scraped emails are bundled with unrelated leaks to increase resale value. The Jamendo data breach may not expose sensitive identity documents, but it still feeds into a larger underground data economy that thrives on aggregation 🔗
Realistic risk assessment for users
A common question is: if only emails were exposed, should users be worried? The clear answer is yes, but proportionally. The Jamendo data breach does not suggest immediate account takeover risk by itself. However, affected users may experience increased spam, targeted phishing referencing music interests, or fake Jamendo-branded messages. For artists managing multiple platforms, the exposure could also enable impersonation attempts. Understanding the realistic scope of risk helps users respond calmly rather than ignore the issue entirely 🎯
Role of underground monitoring and intelligence
Once datasets like the Jamendo data breach appear on forums, they are often indexed, categorized, and redistributed. This is why organizations rely on data breach detection, dark web search, dark web monitoring platform and other information to identify when brand-related data surfaces outside official channels. One of the services of dark web monitoring platforms provide visibility into breach forums, marketplaces, and paste sites where scraped data circulates. Monitoring does not prevent scraping, but it dramatically reduces response time and allows for early warnings to users 🔍
How this fits broader scraping trends
The Jamendo data breach is part of a broader trend where attackers increasingly rely on scraping rather than traditional hacking. Scraping is cheaper, lower risk, and harder to prosecute, especially when data is partially public. Platforms that allow profile visibility or API access without strict rate limiting are particularly exposed. Over time, scraped datasets accumulate, and their combined value can rival that of deeper breaches. This trend challenges the assumption that only “hacked” data is dangerous 📈
Practical checklist for affected users
If you believe your data may be included in the Jamendo data breach, follow these practical steps:
• Be cautious with emails claiming to be from Jamendo
• Avoid clicking links requesting account verification
• Use unique passwords across platforms
• Monitor inboxes for unusual activity
• Stay informed via reputable intelligence sources like Darknetsearch.com.
This checklist helps reduce the likelihood that scraped data will be successfully exploited 🛡️
Platform responsibility and transparency
While scraping differs from hacking, platforms still play a critical role in prevention. Rate limiting, bot detection, and API controls significantly reduce scraping feasibility. The Jamendo data breach raises broader questions about how music platforms balance openness with security. Transparency also matters. Even when incidents are low severity, clear communication helps maintain trust. According to guidance from high-authority sources such as https://www.cisa.gov, early acknowledgment and user education are key elements of effective incident management 📢
Expert insight on low-severity leaks
Cybersecurity analysts often stress that “low-sensitivity leaks become high-impact when repeated.” Applied to the Jamendo data breach, this means that even limited datasets should not be dismissed outright. Over time, repeated scrapes from different services can fully de-anonymize users. This perspective explains why professionals track even modest incidents closely and advise users to stay vigilant 👀
The bigger picture for digital platforms
The Jamendo data breach illustrates how modern data risk is cumulative. One scrape alone may seem insignificant, but combined with others, it becomes powerful. For platforms, this reinforces the need for proactive security controls. For users, it highlights the importance of minimizing data reuse and monitoring exposure. Scraping is unlikely to disappear, but awareness significantly reduces its impact 🔄
Conclusion and next steps
The alleged Jamendo data breach may not rank among the most severe incidents of recent years, but it remains relevant due to its scale and the enduring value of email data. Understanding what was exposed, how scraped data circulates, and how attackers use aggregation helps users and organizations make informed decisions. Staying aware, cautious, and proactive is the best defense in an environment where even music platforms can become part of the breach ecosystem. Discover much more in our complete guide and stay ahead of emerging threats. Request a demo NOW to see how continuous monitoring can protect your digital footprint 🚀
*Disclaimer: DarknetSearch reports on publicly available threat-intelligence sources. Inclusion of an organization in an article does not imply confirmed compromise. All claims are attributed to external sources unless explicitly verified.
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


