Neighbourly.co.nz Data Breach Revealed: 9 Key Facts

➤Summary
The Neighbourly.co.nz data breach has emerged as one of the most significant alleged community-platform leaks of early 2026, drawing attention from cybersecurity analysts and everyday users alike. Shared publicly on Breachforums.as, the disclosure claims that a massive dataset connected to Neighbourly.co.nz was compromised, exposing deeply personal user information at unprecedented scale. With more than 213 million lines of data and roughly 150 GB reportedly leaked, this incident raises serious concerns about privacy, trust, and long-term digital risk. As online neighborhood platforms increasingly store sensitive personal interactions, incidents like this highlight the growing importance of proactive monitoring, rapid response, and user awareness. This darknetsearch.com article explores what is known so far, what data may be at risk, and how individuals and organizations can protect themselves moving forward. 🚨
What Is the Alleged Neighbourly.co.nz Data Breach?
The Neighbourly.co.nz data breach refers to an alleged unauthorized extraction of user data from the Neighbourly.co.nz platform, a popular New Zealand-based online community network. According to the forum post by Spirigatito, attackers gained access to backend systems and exfiltrated a vast volume of records tied to user accounts and interactions. While the alleged breach remains unconfirmed by the company at the time of publication, the level of detail and sheer size of the dataset suggest a serious security lapse rather than a superficial scrape.

Such incidents often stem from misconfigured databases, vulnerable APIs, or compromised administrator credentials. 🔍
Scope and Scale of the Alleged Data Leak
One of the most alarming aspects of this Neighbourly data leak is its reported magnitude. The forum post claims:
- 213,391,325 lines of data
- Approximately 150 GB in total size
This scale places the incident among the largest community-platform breaches in recent years. Large datasets increase the likelihood that historical, inactive, and sensitive records are included, expanding the risk window for affected users. From a cybersecurity perspective, this emphasizes why continuous monitoring of infrastructure and exposed asset discovery are essential for platforms handling long-term user data. 📊
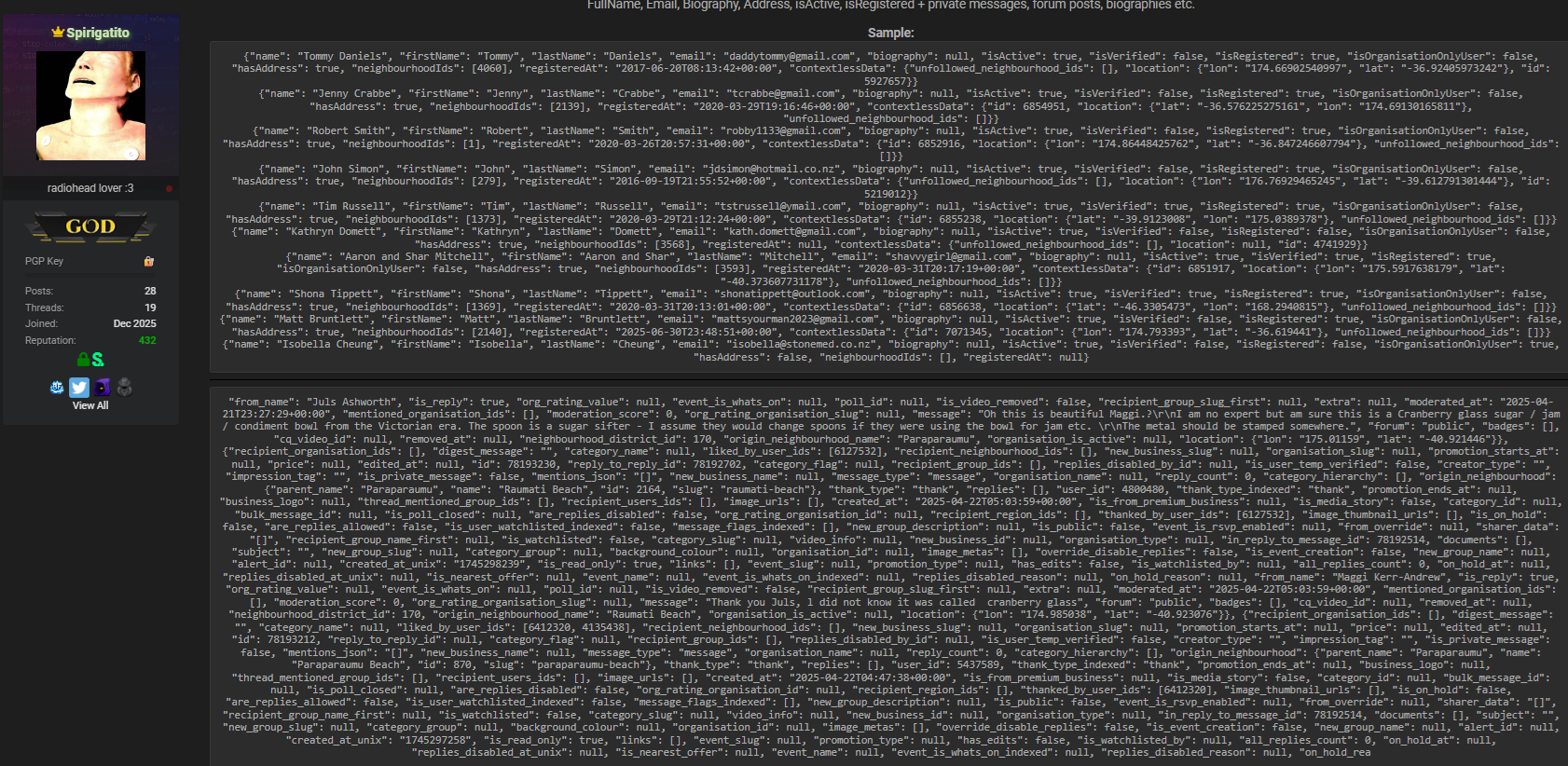
Types of Compromised Data Reportedly Included
According to the disclosure, the leaked dataset allegedly contains a wide range of personal and behavioral information, including:
- FullName
- Biography
- Address
- isActive
- isRegistered
- Private messages
- Forum posts
- User biographies and profile content
The inclusion of private messages and forum posts significantly elevates the severity of the Neighbourly.co.nz data breach. Unlike basic contact data, conversational content can reveal relationships, routines, opinions, and even security-related discussions, making targeted social engineering attacks far more effective. ⚠️
Why This Neighbourly.co.nz Data Breach Is Especially Concerning
A Neighbourly.co.nz data breach is particularly sensitive because the platform is designed to foster trust within local communities. Users often share addresses, daily habits, and neighborhood concerns under the assumption of a semi-private environment. When such data is exposed, attackers can exploit it for phishing, impersonation, or even offline crimes. This incident underscores how community-focused platforms can become high-value targets due to the richness of their data. 🧠
The Role of Breachforums.as in Leak Disclosure
Breachforums.as has become a well-known marketplace and announcement board for leaked databases. Threat actors use it to showcase data, build credibility, and attract buyers. Security researchers frequently cross-reference posts from Breachforums.as with intelligence indexed on platforms like darknetsearch.com to assess authenticity and impact. Monitoring these spaces is a core element of modern cyber threat intelligence and effective data breach detection strategies. 🕵️♀️
Immediate Risks for Affected Users
Question: Are users impacted by the Neighbourly.co.nz data breach at immediate risk?
Answer: Yes. If the leaked data is authentic, users face increased risks of phishing, identity theft, harassment, and targeted scams. The presence of addresses and private messages allows attackers to craft highly personalized attacks that are difficult to detect. Prompt defensive action is critical. 🔐
Practical Checklist for Users After a Community Platform Breach
If you believe your data may be included in the Neighbourly data leak, follow this practical checklist:
- Change your Neighbourly.co.nz password immediately
- Avoid reusing the same password on other platforms
- Be cautious of emails or messages referencing local issues
- Review privacy settings on all community platforms
- Monitor for suspicious activity or impersonation attempts
Organizations should complement user actions with proactive monitoring, underground intelligence, and a modern dark web solution to identify leaked data early. ✅
Broader Implications for Online Community Platforms
The Neighbourly.co.nz data breach highlights a broader issue facing community-driven websites worldwide. As platforms grow, legacy systems and rapid feature expansion can introduce vulnerabilities. Security experts increasingly stress the importance of regular audits, segmented databases, and least-privilege access models. Guidance from reputable authorities such as https://www.ncsc.govt.nz/ emphasizes that protecting user trust requires ongoing investment, not one-time fixes. 📚
Expert Insight on Community Data Security
Cybersecurity professionals often note that community platforms underestimate their appeal to attackers. One analyst remarked, “Data that maps real people to real places is among the most valuable assets on the dark web.” This perspective explains why breaches involving neighborhood and social platforms tend to have long-lasting consequences, even when financial data is not involved. 📌
Monitoring and Intelligence After the Leak
Following disclosures like this, analysts and organizations rely on resources such as https://darknetsearch.com/ to track secondary distribution of leaked datasets. Data posted once is often reshared, repackaged, and monetized repeatedly. Continuous intelligence gathering helps determine whether data is being actively exploited or sold, enabling faster response and user notification. 🌐
The Importance of Proactive Cyber Defense
Incidents like the alleged Neighbourly.co.nz data breach reinforce the need for layered cyber defense strategies. Beyond basic security controls, organizations must implement continuous monitoring, rapid incident response, and user education. Proactive approaches reduce dwell time for attackers and limit the scale of potential damage when breaches occur. 🚀
Conclusion and What to Do Next
The alleged Neighbourly.co.nz data breach serves as a powerful reminder that even trusted community platforms are not immune to large-scale cyber incidents. With hundreds of millions of records reportedly exposed, the potential impact on user privacy and safety is significant. Staying informed through reliable intelligence sources, practicing good personal security hygiene, and advocating for stronger platform protections are essential steps forward. Discover much more in our complete guide to understanding underground data exposure and digital risk. Request a demo NOW to see how advanced monitoring and intelligence can help protect users and organizations before the next breach unfolds.
Disclaimer: DarknetSearch reports on publicly available threat-intelligence sources. Inclusion of an organization in an article does not imply confirmed compromise. All claims are attributed to external sources unless explicitly verified.
Discover how CISOs, SOC teams, and risk leaders use our platform to detect leaks, monitor the dark web, and prevent account takeover.
🚀Explore use cases →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.

