Monedas.com Data Breach Revealed: 7 Key Risks for Users

➤Summary
The Monedas.com data breach has quickly become a major talking point across cybersecurity and cryptocurrency communities after an alleged leak was shared on Breachforums.as on 19 February 2026. According to the forum post authored by Wadjet, sensitive user information tied to Monedas.com and three related domains may have been exposed, raising urgent questions about user safety, operational security, and trust in crypto platforms. This incident highlights how quickly threat actors can exploit weak points and why proactive monitoring, data breach detection, and a modern dark web solution are no longer optional for digital finance businesses. In this darknetsearch.com article, we break down what happened, what data was compromised, which domains were involved, and what users and organizations should do next to reduce risk and prevent further damage. 🚨
What Is the Alleged Monedas.com Data Breach?
The Monedas.com data breach refers to an alleged database leak publicly advertised on the underground forum Breachforums.as. The post claims that attackers accessed backend systems and extracted user records linked to Monedas.com and its multilingual counterparts. While the company has not yet issued a public confirmation at the time of writing, the structured nature of the data suggests a direct compromise rather than simple scraping.
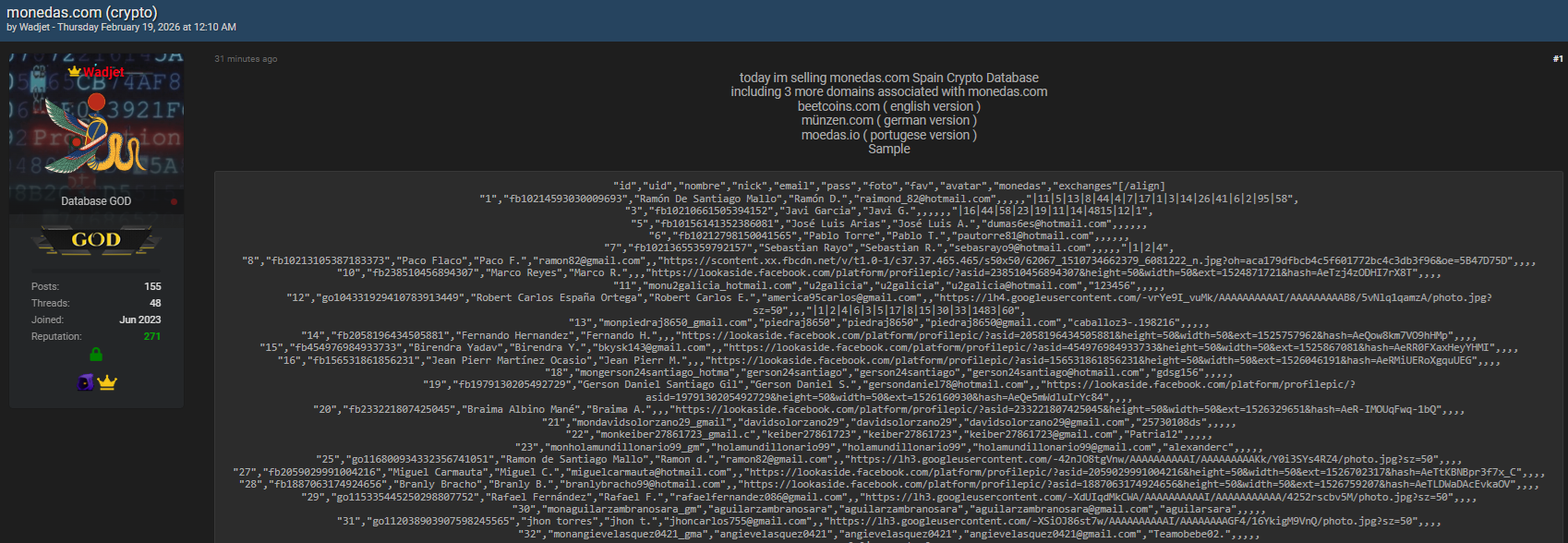
Incidents like this are often the result of credential abuse, misconfigured servers, or outdated security controls, all common issues in fast-growing crypto services. 🔍
Compromised Data: What Information Was Exposed?
According to the forum disclosure, the compromised dataset reportedly includes the following fields:
- id
- uid
- nombre
- nick
- pass
- foto
- fav
- avatar
- monedas
- exchanges
This combination of identifiers, contact details, and account-related metadata significantly increases the risk of account takeover, phishing campaigns, and identity fraud. Even if passwords are hashed, attackers often attempt credential stuffing across other platforms, making this crypto platform breach especially dangerous for users who reuse passwords. ⚠️
Domains Allegedly Affected by the Breach
Beyond the primary site, the leak allegedly covers three additional domains associated with the Monedas.com ecosystem:
- beetcoins.com (English version)
- münzen.com (German version)
- moedas.io (Portuguese version)
Multi-domain exposure amplifies the attack surface and suggests shared infrastructure or databases. From a security standpoint, this underlines the importance of segmented environments and exposed asset discovery to prevent lateral movement once attackers gain initial access. 🌐
Why This Monedas.com Data Breach Matters
A Monedas.com data breach is not just another headline; it has real-world consequences. Crypto users are frequent targets for social engineering because of the irreversible nature of blockchain transactions. When emails, usernames, and account preferences are leaked together, attackers can craft highly convincing scams. This is why many analysts stress continuous monitoring of underground forums and marketplaces. Resources like darknetsearch.com regularly track breach disclosures and emerging threat trends, helping organizations respond faster. 🧠
How Breachforums.as Plays a Role
Breachforums.as has become a central hub for sharing and monetizing leaked databases. Threat actors use it to validate their reputation and attract buyers. Monitoring such platforms is a core component of effective cyber threat intelligence. Analysts often correlate posts from Breachforums with reports indexed on Dark web monitoring platforms to assess credibility and scope. This ecosystem shows how quickly an unverified claim can evolve into widespread exploitation if ignored. 🕵️♂️
Are Users at Immediate Risk?
Question: Are users affected by the Monedas.com data breach in immediate danger?
Answer: Yes, if the data is authentic and current, affected users face heightened risks of phishing, account compromise, and fraud. The presence of email and password fields makes rapid defensive action critical. Users should change passwords, enable multi-factor authentication, and monitor accounts for suspicious activity without delay. 🔐
Practical Security Checklist After a Crypto Platform Breach
To reduce exposure following a crypto service data leak, consider this checklist:
- Change passwords on Monedas.com and any reused accounts
- Enable two-factor authentication everywhere possible
- Watch for phishing emails referencing crypto balances
- Use a password manager with unique credentials
- Monitor breach alerts and dark web monitoring reports
Security teams should also invest in continuous data breach detection and underground monitoring to identify leaks before they escalate. ✅
Industry Perspective and Expert Insight
Cybersecurity experts consistently warn that crypto platforms are high-value targets. According to guidance from organizations like https://www.ncsc.gov.uk/, layered defenses, rapid incident response, and user education are essential to limit fallout from breaches. An expert quote often repeated in the industry states, “The cost of monitoring is always lower than the cost of recovery,” a principle clearly illustrated by incidents like this alleged Monedas.com data breach. 📊
The Bigger Picture: Trust and Crypto Security
Every crypto exchange breach chips away at user confidence. Even unconfirmed leaks can trigger reputational damage and user churn. This is why proactive threat intelligence, continuous monitoring of dark web forums, and investment in modern dark web solution platforms are now standard for serious operators. Visibility into leaked credentials and infrastructure weaknesses enables faster remediation and protects both users and brand value. 🚀
Conclusion and Next Steps
The alleged Monedas.com data breach serves as a stark reminder of how exposed digital assets can become without constant vigilance. From compromised user records to multiple affected domains, the potential impact is significant for both individuals and organizations. Staying informed through trusted resources like https://darknetsearch.com/ and adopting proactive security strategies can make the difference between early containment and large-scale fallout. Discover much more in our complete guide and take control of your digital risk posture today. Request a demo NOW to see how advanced monitoring can protect your assets before attackers strike again.
Disclaimer: DarknetSearch reports on publicly available threat-intelligence sources. Inclusion of an organization in an article does not imply confirmed compromise. All claims are attributed to external sources unless explicitly verified.
Discover how CISOs, SOC teams, and risk leaders use our platform to detect leaks, monitor the dark web, and prevent account takeover.
🚀Explore use cases →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


