Loozap Data Breach Revealed: 7 Key Impacts of the LAPSUS Leak

➤Summary
Loozap data breach revelations have sent shockwaves across the classifieds and marketplace ecosystem, raising urgent questions about data protection, cybercriminal sophistication, and user safety. The incident, allegedly linked to the LAPSUS$ Group, involves a massive .RAR dump estimated at nearly 10GB of uncompressed data, reportedly exposing highly sensitive personal and financial information. This Loozap data breach is especially concerning given claims that the leak contains records tied to 7,000 different African IP ranges, suggesting a broad geographic impact 🌍. As digital marketplaces expand rapidly across emerging markets, this event highlights critical vulnerabilities in online platforms handling user identities, wallets, and payments.
In this Darknetsearch article, we break down what happened, what data was allegedly compromised, who may be affected, and what organizations and users should do next to reduce risk and regain trust 🔐.
What Is Loozap and Why the Breach Matters
Loozap is an online classifieds and e-commerce marketplace operating via loozap.com, connecting buyers and sellers across multiple regions. Platforms like Loozap rely heavily on user trust, as they process personal profiles, contact details, and sometimes payment-related data. The Loozap data breach matters because it allegedly exposed not only basic user information but also wallet details and payment data, increasing the risk of fraud, identity theft, and financial exploitation 💳.
In digital marketplaces, a single breach can trigger cascading effects: loss of credibility, regulatory scrutiny, and long-term user attrition. This incident also adds to a growing list of marketplace security failures discussed in dark web reports that track underground data trading activity.
Timeline and Source of the Leak
According to claims shared publicly on LinkedIn by Dark Web Informer, the LAPSUS$ Group allegedly released the Loozap data breach archive in a compressed .RAR format. The threat actor is known for high-profile attacks and aggressive extortion tactics, often publicizing breaches to gain attention or leverage. While Loozap has not publicly confirmed all details, the existence of the dump has been referenced within multiple monitoring communities and forums. One question many ask is: Is this leak verified? The clear answer is that while independent verification is ongoing, multiple indicators such as sample data consistency and actor reputation increase the credibility of the claims 🕵️.
Allegedly Exposed Data Types
The scope of the Loozap data breach is alarming due to the diversity of data allegedly included.
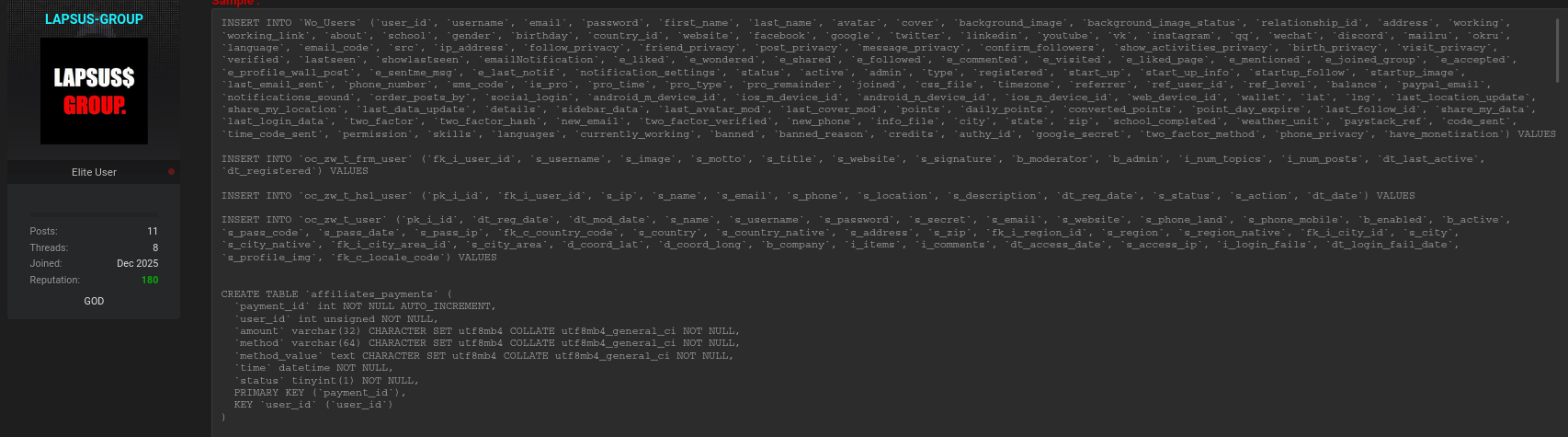
Below is a structured overview suitable for quick reference and featured snippets:
| Data Category | Examples |
| Personal Identifiers | Full names, first and last names, dates of birth |
| Contact Details | Emails, phone numbers, addresses |
| Financial Information | Wallet details, payment data |
| Demographic Data | School information, additional profile fields |
| Technical Metadata | User metadata, IP-related indicators |
| Such a combination enables advanced social engineering, phishing, and account takeover campaigns 😟. The inclusion of school information and dates of birth further elevates identity theft risks, particularly for younger users. |
The Role of the LAPSUS$ Group
The LAPSUS$ Group has built a reputation as a disruptive cybercrime collective targeting tech companies, telecoms, and online services. Their methods often rely on credential theft, insider access, and social engineering rather than purely technical exploits. In the context of the Loozap data breach, their alleged involvement suggests a targeted operation rather than an automated scan. Security analysts frequently cite LAPSUS$ activities in compare dark web monitoring discussions because of the group’s tendency to leak data publicly instead of quietly selling it, amplifying reputational damage 🚨.
African IP Ranges and Regional Impact
One of the most striking claims is the presence of data linked to 7,000 African IP ranges. This suggests that a significant portion of affected users may be located across African markets, where digital adoption is rising rapidly but cybersecurity resources may be uneven. The Loozap data breach could therefore have disproportionate consequences, including increased mobile fraud, SIM swapping, and financial scams. Marketplaces operating in these regions must now reassess their security posture, especially around user verification and transaction monitoring.
Risks for Users and Businesses
The immediate risks stemming from the Loozap data breach include phishing campaigns, fraudulent wallet transactions, and impersonation scams. For businesses, secondary risks include brand abuse, fake listings, and spoofed domains. Attackers often combine leaked data with Domain Spoofing Detection failures to create convincing fake portals that harvest additional credentials. Over time, such breaches erode consumer confidence and invite regulatory penalties under data protection laws ⚠️. Monitoring forums like those indexed on Darknetsearch.com can help identify early signs of leaked data misuse.
How Dark Web Intelligence Tracks Such Leaks
Cyber intelligence teams rely on dark web solutions to identify, validate, and contextualize leaked datasets. These platforms scan underground forums, encrypted channels, and leak sites for indicators tied to specific brands or domains. In the case of the Loozap data breach, analysts monitor chatter, sample files, and actor communications to assess authenticity. This process often becomes a case study dark web monitoring example, demonstrating how early detection can reduce downstream harm. Dark web monitoring platforms provide visibility into marketplaces and forums where such data may circulate 🧠.
Practical Checklist for Affected Users
If you suspect your data may be included in the Loozap data breach, follow this practical checklist:
- Change passwords on Loozap and any reused accounts immediately
- Enable two-factor authentication where available
- Monitor bank statements and digital wallets for suspicious activity
- Be cautious of unsolicited emails or calls using personal details
- Consider credit monitoring or identity protection services
This proactive approach can significantly reduce the likelihood of successful exploitation ✅.
Lessons for Marketplace Operators
For online marketplaces, the Loozap data breach underscores the need for layered security controls. Encryption of sensitive fields, strict access management, employee security training, and continuous threat monitoring are essential. Integrating insights from dark web reports into security operations allows companies to respond faster when data appears in underground channels. Regular audits and incident response drills also help organizations prepare for the inevitable reality of cyber threats 🔄.
External Verification and Community Awareness
The original disclosure reference shared on LinkedIn serves as an external data point supporting the claims around the Loozap data breach. High-authority platforms play a role in spreading awareness while allowing independent researchers to scrutinize evidence. Transparency and timely communication from affected companies remain critical in maintaining trust during such incidents 📢.
Conclusion and Call to Action
The Loozap data breach is a stark reminder that no digital marketplace is immune to cyber threats, regardless of size or region. Allegations involving the LAPSUS$ Group, extensive personal and financial data, and wide African exposure elevate this incident to a serious security event. Users must remain vigilant, and organizations must invest in intelligence-driven defenses to detect leaks early and respond decisively. To deepen your understanding of how such breaches unfold and how to defend against them, explore expert resources and monitoring tools today. Discover much more in our complete guide and Request a demo NOW 🚀.
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourselfsssss.


