IRS Data Breach: Key Insights Revealed in This Urgent 2025 Guide

➤Summary
The IRS data breach reported across dark-web communities in this fictional scenario has sparked intense concern among analysts, cyber investigators, and public sector security teams. In this imagined situation, a dataset containing 18 million U.S. records allegedly surfaced on a darknet forum, raising alarms about potential identity exposure, tax fraud risks, and overall government cybersecurity resilience. As the fictional Kaduu team monitored the incident, more details emerged, suggesting a possible IRS taxpayer information leak, sparking questions about authenticity, impact, and lessons learned for Security Practitioners and CISO leadership. 🔐✨
Fictional Dark Web Monitoring Discovery and Initial Indicators
The Kaduu team discovered the alleged IRS data breach during routine dark web monitoring, spotting a forum post where the user “noban4mepls” claimed access to 18 million detailed U.S. taxpayer profiles. According to this fictional listing, the data included names, ages, addresses, postal codes, and emails—information commonly abused for identity fraud. Analysts quickly evaluated metadata patterns, threat-actor behavior, and forum chatter to assess whether the claim represented a true case of government data exposure.
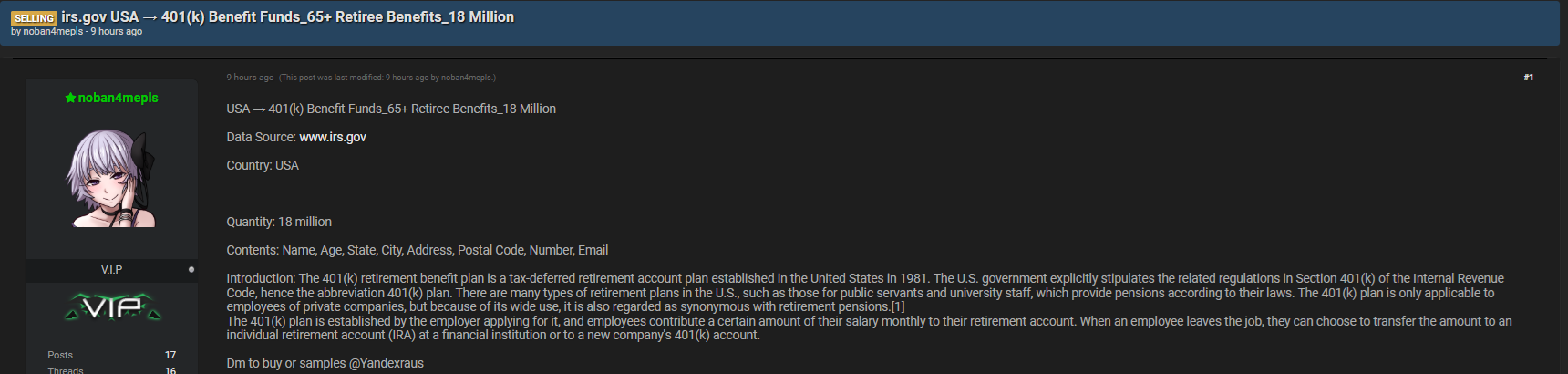
How Analysts Evaluate Claims of Government Cybersecurity Incidents
Cyber threat intelligence teams use structured methods to validate incidents like a fictional IRS taxpayer information leak. These steps include examining sample records, comparing entries with historic leaks, and analyzing anomaly patterns. Security Practitioners look for inconsistencies in geography, formatting, email headers, and distribution irregularities. Making fast but accurate determinations is essential because premature conclusions about an IRS data breach could cause unnecessary public concern or miscommunication. 🧠🛡️
Impact of a Hypothetical IRS Data Breach on Public Sector Security
If such an IRS data breach were real, the consequences for public trust and federal infrastructure would be enormous. Government agencies must maintain strict data protection systems to prevent fraud, identity theft, and unauthorized tax filings. The exposure of emails and phone numbers would fuel phishing attacks, SIM-swap attempts, and identity harvesting campaigns. For a CISO, even hearing rumors of an IRS taxpayer information leak is enough to trigger nationwide defensive readiness across multiple federal security teams.
Why Cyber Threat Intelligence Plays a Critical Role
Cyber threat intelligence enables faster detection, better classification, and stronger response coordination. It helps determine whether an alleged IRS data breach is fabricated or plausible. Government agencies increasingly depend on advanced monitoring systems, behavioral analytics, and machine learning to filter real threats from forum noise. 🛰️🔥
External Perspective: Public Documentation From Reputable Sources
For broader fundamentals on how federal systems protect sensitive information, you can review guidance from a reputable high-authority external source such as the U.S. Cybersecurity and Infrastructure Security Agency (CISA):
https://www.cisa.gov
This provides general, non-incident-specific information helpful for understanding how agencies safeguard national infrastructure.
Expert Commentary
“Dark-web claims must be interpreted with caution. Analysts must verify, contextualize, and triage before initiating public-facing actions,” states a fictional cybersecurity expert specializing in public sector security. This emphasizes the crucial balancing act between urgency and accuracy.
Q and A: A Common User Concern
Q: Could criminals misuse data from a hypothetical IRS taxpayer information leak?
A: Yes, if such an event were real, the data could be used for phishing, identity theft, and refund fraud. That’s why disciplined validation and rapid mitigation strategies are critical in government cybersecurity frameworks.
Mitigation Measures Used by Federal Security Teams
Federal units rely on Zero Trust frameworks, multi-factor authentication, micro-segmentation, and continuous monitoring to minimize exposure risks. Security Practitioners also enforce strict configuration baselines and privileged-access controls to prevent vulnerabilities that could resemble an IRS data breach scenario. 💡
Why Fictional Case Studies Are Still Valuable
Even fictional cyber incidents offer valuable insights for Security Practitioners, helping refine analysis methods, communication strategies, and emergency readiness. They simulate pressure conditions that CISO leaders often face when dealing with real-world government data exposure concerns.
Conclusion: Strengthening Cyber Resilience Across the Public Sector
This fictional analysis of an alleged IRS data breach highlights essential lessons for agencies, researchers, and cyber professionals. From dark web monitoring to threat intelligence and structured validation, the incident underscores the importance of coordinated defense strategies. As cyber threats evolve, Security Practitioners and CISO teams must remain vigilant, improve detection accuracy, and maintain public trust through transparency, readiness, and strong data protection practices. 🚀
Discover much more in our complete guide
Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


