Brsk data breach: Key Facts Revealed About the 2025 Incident

➤Summary
The Brsk data breach has become one of the most significant UK ISP cybersecurity incidents of 2025, sending shockwaves through the broadband community and raising serious concerns about customer privacy ⚠️.
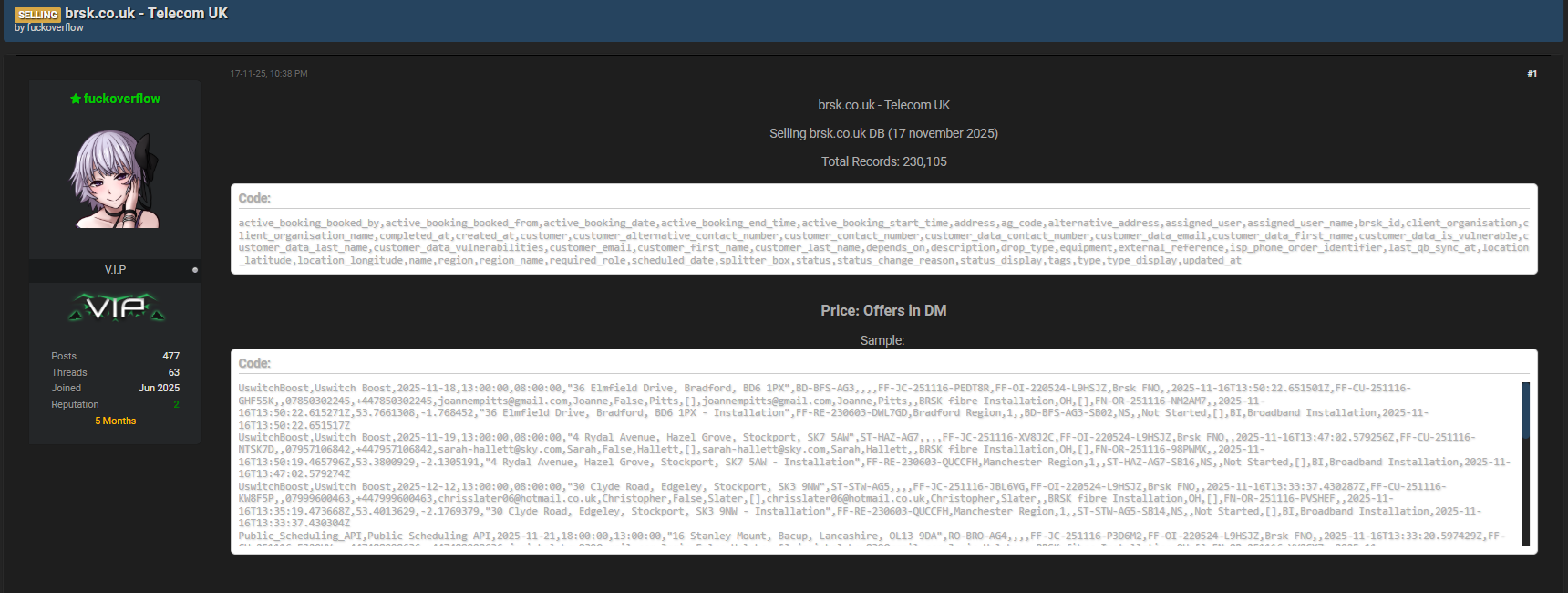
On 17 November 2025, a known threat actor using the handle fuckoverflow published a listing on Darkforums.st, claiming possession of the stolen database and marking it as “For Sale”. With extensive personal and operational details reportedly exposed — ranging from names and email addresses to geolocation coordinates and booking schedules — this UK ISP breach has triggered urgent discussions in the technology industry about data protection, transparency, and accountability.
The leak appears to involve tens of thousands of customer records, including details often collected under KYC (know you customer) procedures such as contact information, addresses, and booking histories. Early industry analysis, supported by external reporting, indicates that this brsk customer data leak affects multiple layers of operational and consumer data 📉. As subscribers struggle to understand their exposure, cybersecurity professionals, CISOs included, are already dissecting the incident to determine how attackers accessed the data and how the sector can prevent similar breaches in the future 😨.
Impact of the Breach on Customers and Industry Trust
The brsk data breach exposed many records that could be used to target subscribers through identity fraud, phishing, impersonation attempts, or engineered scams. Attackers, leveraging names, phone numbers, booking schedules, and address details, could craft convincing messages or calls pretending to be from support teams. For example, the inclusion of fields such as assigned_user, scheduled_date, drop_type, and equipment gives criminals unusual insight into the technical environment of service appointments 🎯. Such data may also enable social-engineering attacks mimicking technician visits or service changes.
Experts have noted that while no passwords or financial information appear in the exposed dataset, the presence of both location coordinates and vulnerability-related flags escalates the risk significantly. A cybersecurity analyst recently observed: “Even non-financial attributes can assemble a powerful identity footprint when combined — names, addresses, service data, location. For attackers, that’s OSINT gold.” This aligns with broader research showing that cross-referencing leaked data enables easier and more convincing targeted attacks.
Many customers are asking: “Can attackers use this information to access my broadband account or router?”
Answer: Not directly, in most cases. However, the combination of personal details, scheduling info, and contact numbers can absolutely increase the possibility of social-engineering attacks. Criminals often blend leaked info with publicly available details to impersonate technicians or support agents, making the overall threat more substantial.
What Information Was Compromised? (Data Fields Overview)
The leaked database includes a wide range of interconnected fields. To help readers understand the scale of the brsk customer data leak, here is a summarized table of the categories involved:
| Category | Examples of Fields Exposed |
| Customer Identity | customer_first_name, customer_last_name, customer_email |
| Contact Details | customer_contact_number, customer_alternative_contact_number |
| GIS and Address Data | address, location_latitude, location_longitude |
| Service and Booking Info | active_booking_date, active_booking_start_time, equipment, scheduled_date, drop_type |
| Operational Metadata | created_at, updated_at, status, assigned_user_name, brsk_id |
| Vulnerability/Support Flag | customer_data_is_vulnerable, customer_data_vulnerabilities |
These categories show why the UK ISP breach is more severe than typical contact-info leaks. The presence of vulnerability-related flags and exact geolocations adds complexity, making this dataset especially attractive to cybercriminals 💻.
How the Breach Was Listed on the Dark Web / Marketplace
According to early intelligence, the hacker fuckoverflow posted the listing on Darkforums.st, advertising the brsk customer data as “For Sale,” which typically means the threat actor aims to monetize the dataset rapidly. Such listings often attract identity thieves, scam operators, and spam brokers who specialize in cross-matching leaked information to create complete digital profiles of victims.
Internal monitoring and cyber-intel tools help security professionals track, classify, and validate such leaks, making them critical resources for staying updated on how cybercriminal markets evolve. In fact, DarknetSearch recently published a blog on a similar article, underscoring how technology services are frequent targets. (StMicroelectronics Data Breach)
External coverage — for example via ISPreview UK — confirms that the dataset reportedly contains over 230,000 customer records. (ISPreview)
Security Concerns Across the ISP Sector and Relevance to CISOs
The UK ISP breach affecting brsk highlights a growing trend: attackers are increasingly targeting infrastructure providers, knowing that these companies hold detailed customer datasets needed for service delivery. Unlike streaming or retail platforms, ISPs must store installation data, geographic coordinates, vulnerability indicators, and technician assignments.
A seasoned CISO familiar with the telecommunications and broadband space recently stated: “Telecom and ISP databases hold some of the most structurally complete customer profiles in the industry. For attackers, this is a goldmine.” 🔐
Industry analysts warn that cybersecurity fabrics must focus more heavily on segmentation, data minimization, and least-privilege access, particularly for sensitive categories like location data and vulnerability flags. The breach also raises governance concerns: if operational fields such as drop_type, equipment, region, and status_change_reason are accessible to attackers, it could point to misconfigured APIs, insufficient role-based access control, or lack of internal access monitoring — a classic failure mode in the technology industry’s back-end infrastructure.
Practical Tip for Affected Users and Organizations
✔ Checklist to improve your protection immediately:
- Change your email password and any accounts linked to your ISP services.
- Turn on multi-factor authentication wherever possible.
- Do not trust unexpected technician-visit notifications — verify via official channels.
- Keep an eye on unsolicited email or SMS communication.
- Consider identity-monitoring services, especially if location or vulnerability flags apply.
- Review smart-home and router security settings as a general precaution.
This checklist helps reduce potential fallout and limits the ability of attackers to exploit information from the brsk data breach.
For businesses, especially those in the technology industry or providing ISP-adjacent services, this serves as a wake-up call to conduct KYC data audits, minimize data retention, adopt OSINT-friendly breach-monitoring tools, and tighten internal access controls.
Long-term and Industry-wide Implications
This event highlights the need for transparent reporting, incident response planning, and strict compliance with data protection standards in the broadband and ISP sector 🌐. The involvement of sensitive customer vulnerability fields — such as whether a user is considered vulnerable — makes accountability even more urgent.
For customers, the breach may erode trust in smaller or alternative ISPs, prompting a shift toward larger providers with more robust security reputations. For operators in the technology industry, especially those scaling quickly, the breach underscores the risks inherent when operational growth outpaces security maturity.
Because the dataset reportedly includes not only PII but also installation and service scheduling information, the breach could attract long-tail attackers: over time, records may be resold, combined with other leaks, or used in targeted campaigns — a phenomenon described in breach-economy analyses by DarknetSearch.
Conclusion: Stay Informed, Stay Protected, Stay Ahead
The brsk data breach underscores the evolving risks facing both customers and service providers. While the investigation continues, one thing is clear: transparency, security maturity, and proactive protection matter more than ever. For CSPs, ISPs, and tech-industry stakeholders, this incident should trigger immediate review of data handling, logging, access management, and breach readiness strategies.
Discover much more in our complete guide
Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


