Fake Ad Blocker Extension Triggers Browser Crash ClickFix Attacks

➤Summary
Fake ad blocker extension campaigns are rapidly emerging as one of the most deceptive browser-based threats seen in recent months. Security researchers have uncovered a new tactic in which a fake ad blocker extension deliberately crashes the victim’s browser to launch ClickFix attacks, tricking users into executing malicious commands themselves. This fake ad blocker extension masquerades as a legitimate privacy or ad-blocking tool, exploiting user trust and browser recovery behaviors. Once installed, it weaponizes frustration and confusion, turning a simple browser crash into a powerful infection vector.
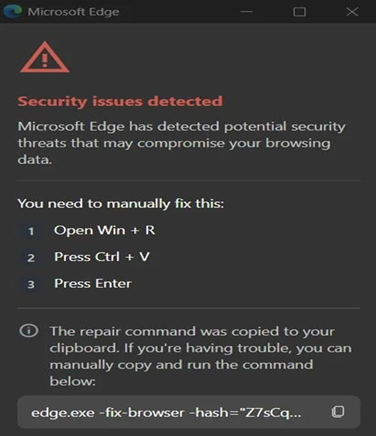
The ClickFix stage of the attack (bleepingcomputer.com)
Source: Huntress
As attackers continue to refine social engineering techniques, understanding how these extensions work and how to defend against them is critical for both individuals and organizations 🚨.
What Is a Fake Ad Blocker Extension
A fake ad blocker extension is a malicious browser add-on designed to look like a legitimate ad-blocking or privacy tool. These extensions often copy branding, descriptions, and functionality claims from real products.
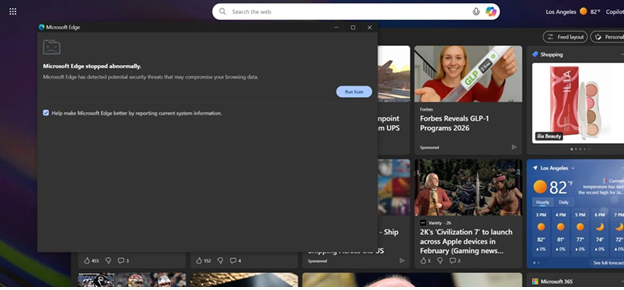
The deceptive pop-up served on browser restart (bleepingcomputer.com)
Source: Huntress
In reality, they perform hidden actions such as injecting scripts, tracking activity, or delivering malware. In this campaign, the fake ad blocker extension goes a step further by intentionally destabilizing the browser to manipulate user behavior ⚠️.
How the Browser Crash Enables ClickFix Attacks
ClickFix attacks rely on convincing users to manually execute commands under the belief they are fixing a technical issue. When the fake ad blocker extension crashes the browser, users are presented with misleading recovery messages or instructions. These prompts guide victims to copy and paste commands into system dialogs, terminals, or browser consoles. The browser crash creates urgency and trust, making the social engineering far more effective 🧠.
Understanding ClickFix as a Social Engineering Technique
ClickFix is not a traditional exploit but a psychological cyberattack. Instead of bypassing security controls directly, attackers convince users to do the work for them. The fake ad blocker extension amplifies this effect by creating a believable failure scenario. Victims believe they are repairing a broken browser when, in reality, they are executing malicious scripts that install payloads or open backdoors 🔓.
Why Ad Blocker Themes Are So Effective
Ad blockers are widely trusted tools used by millions of users. Attackers know that users rarely scrutinize these extensions once installed. A fake ad blocker extension benefits from this implicit trust and from high search demand. Many victims install such extensions quickly, without checking publisher reputation or reviews, making this an ideal delivery channel for browser-based attacks 🌐.
Technical Behavior Observed in the Campaign
Researchers analyzing the malicious extension observed deliberate memory exhaustion and script execution loops that force the browser to crash. After restart, the extension displays fake troubleshooting instructions. These instructions are carefully tailored to different operating systems and browsers, increasing success rates. The fake ad blocker extension does not rely on exploits, making it harder for traditional security tools to flag 🚩.
Who Is Most at Risk
Home users, remote workers, and small businesses are the primary targets. Anyone who frequently installs browser extensions or searches for “free ad blockers” is at higher risk. Organizations that allow unmanaged browser extensions across endpoints face increased exposure, especially when employees use personal devices for work tasks 💻.
Real-World Impact of ClickFix Campaigns
Once executed, ClickFix commands can install malware loaders, steal credentials, or enable persistent access. In some observed cases, infections later escalated into ransomware or data exfiltration. A fake ad blocker extension may appear minor, but its downstream impact can be severe, especially when initial access goes unnoticed 🔥.
Detection Challenges for Security Teams
Traditional antivirus solutions often miss these attacks because no exploit or malicious binary is initially present. The user executes the payload voluntarily. This makes behavioral detection and user education critical. Security teams increasingly rely on Cyber intelligence platforms and dark web monitoring reports to track emerging tactics and understand how these campaigns evolve over time 📊.
One Key Question Answered
Can browser crashes really be used as an attack vector?
Yes. When crashes are intentional and paired with social engineering, they become powerful tools for manipulating users into unsafe actions.
Practical Defense Checklist
To reduce the risk from malicious extensions, follow this checklist:
- Only install extensions from verified publishers
- Review permissions before installation
- Disable unused browser extensions regularly
- Block unauthorized extensions via policy where possible
- Train users to never run commands from pop-ups or error messages
These steps significantly reduce exposure to fake ad blocker extension attacks ✅.
Role of Threat Intelligence and Monitoring
Tracking extension-based campaigns requires visibility beyond traditional malware feeds. Many organizations leverage a Dark web solution to identify early chatter about new social engineering techniques. For service providers, Dark Web Monitoring for MSSP offerings help correlate underground discussions with real-world attack patterns. Maintaining accurate dark web monitoring documentation ensures that response teams understand how and where these threats surface 🧩.
Comparing Monitoring Approaches
Security leaders often compare dark web monitoring platforms to assess coverage, alerting speed, and context quality. When organizations compare dark web monitoring tools, the ability to detect emerging social engineering campaigns like ClickFix becomes a key differentiator. Extension-based attacks frequently appear in underground forums before mainstream detection catches up 🔍.
Industry Perspective on Browser-Based Attacks
Security analysts warn that browsers are becoming the new endpoint battleground. One researcher noted, “Attackers no longer need zero-days when they can convince users to compromise themselves.” This insight explains why fake ad blocker extension campaigns are increasing and why user trust is now a primary attack surface 🧠.
Staying Informed on Emerging Threats
Platforms like darknetsearch.com provide ongoing visibility into underground activity, leaked tools, and evolving attack methods. Reviewing historical cases and intelligence summaries on darknetsearch.com helps organizations anticipate how threats like ClickFix will adapt over time 📈.
External Reporting and Confirmation
The campaign was detailed by BleepingComputer, a highly reputable cybersecurity news outlet with strong technical analysis and editorial oversight. Their reporting confirms active abuse and highlights the broader trend of browser-based social engineering attacks targeting everyday users.
Key Takeaways
This campaign demonstrates that a fake ad blocker extension can be far more dangerous than it appears. By combining intentional browser crashes with ClickFix social engineering, attackers bypass technical defenses and exploit human behavior. The simplicity of the method makes it scalable and difficult to stop without layered controls 🔐.
Conclusion and Call to Action
Fake ad blocker extension attacks signal a shift toward stealthier, psychology-driven browser threats. As attackers refine these methods, organizations and users must adapt by tightening extension controls, improving awareness, and monitoring emerging tactics. Staying ahead requires both technical defenses and intelligence-driven insight. Discover much more in our complete guide. Request a demo NOW.
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


