Edmunds Data Breach Exposed: 2026 Impact and Risks Guide

➤Summary
Edmunds data breach revelations have shaken the cybersecurity and automotive technology communities after sensitive user data appeared for sale on the underground forum Breachforums.bf. Published by Wadjet on January 25, 2026, the leak is allegedly linked to the notorious hacking collective Shinyhunters. This exposure involves deeply sensitive personal, professional, and behavioral data, raising serious concerns about privacy, fraud, and identity theft 😨. As cybercrime tactics become more advanced, incidents like this highlight the urgent need for continuous security monitoring, stronger defenses, and awareness. This in-depth guide explains what edmunds.com is, how the breach occurred, the type of compromised data, the risks to users, and how organizations and individuals can defend themselves using modern cybersecurity strategies and intelligence-driven protection frameworks.
What Is Edmunds.com and Why It Matters
Edmunds.com is a globally recognized automotive research and car shopping platform that provides expert reviews, vehicle pricing data, dealership connections, and consumer advice. Founded in 1966, Edmunds has grown into one of the most trusted online destinations for car buyers and automotive professionals, offering tools for comparing models, calculating financing, and finding dealerships.
Millions of users rely on Edmunds to make informed decisions about purchasing, leasing, and maintaining vehicles 🚗. Because of this massive user base, the platform stores extensive personal and transactional data, making it an attractive target for cybercriminal groups. The recent Edmunds data breach demonstrates how even reputable and established platforms can become vulnerable if attackers identify security gaps.
Breach Overview: What Happened on BreachForums
On January 25, 2026, a post appeared on Breachforums.bf, a well-known underground cybercrime forum. The author, Wadjet, claimed responsibility for publishing data allegedly breached from Edmunds, attributing the hack to the hacking group Shinyhunters.
Shinyhunters has a long-standing reputation for executing large-scale breaches across e-commerce, finance, technology, and consumer platforms. Their previous operations have resulted in tens of millions of leaked records circulating across dark web marketplaces and private criminal channels.
The forum post claimed access to extensive user databases, including personally identifiable information (PII), engagement metrics, and account metadata. This exposure triggered immediate alerts across cybersecurity monitoring networks and led to a comprehensive dark web monitoring report, which confirmed the presence of Edmunds-related data across multiple illicit data trading platforms.
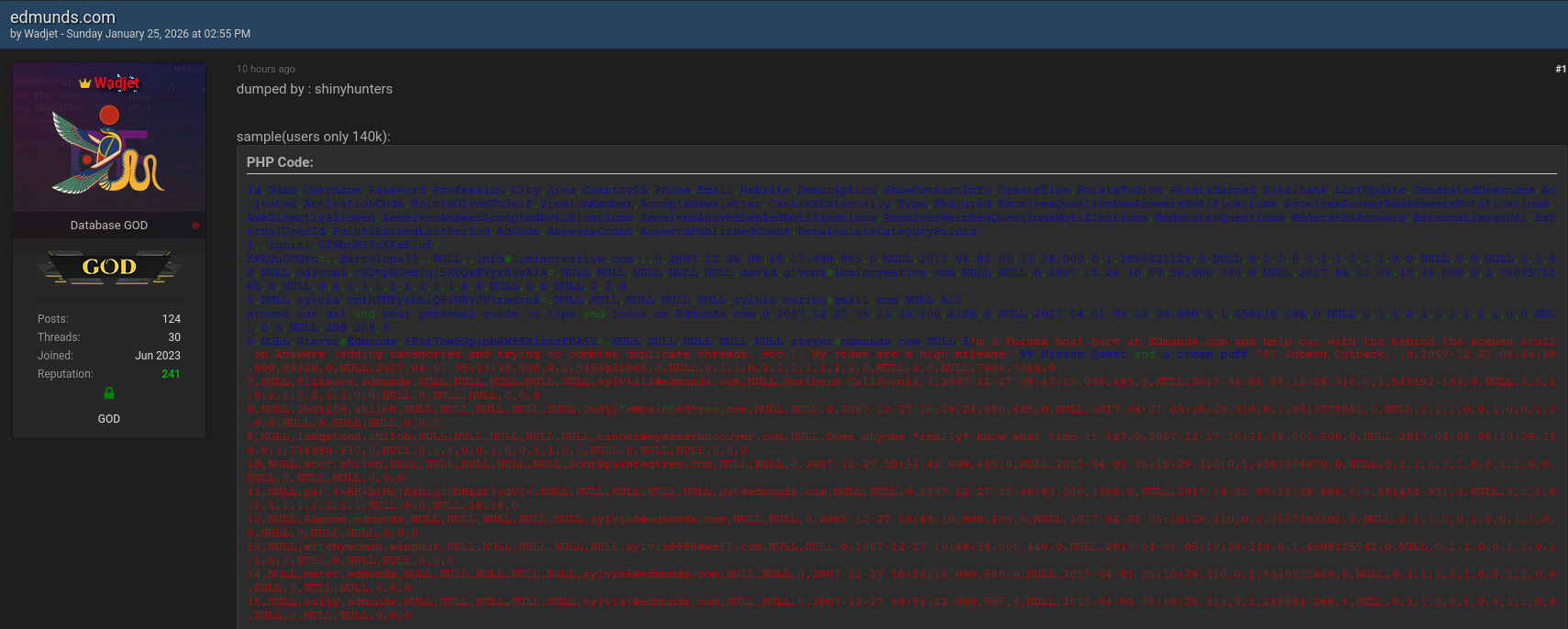
What Data Was Compromised?
The compromised dataset is extensive and alarming. It includes:
- ID
- Name
- Username
- Password
- Profession
- City
- Area
- Country ID
- Phone number
- Email address
- Website
- Description
- Account settings and preferences
- Activation status
- Notification permissions
- Points earned and activity ranking
- External user IDs
- Advertisement codes
- Answer and engagement metrics
In addition, leaked logs included partial messaging records, indicating communication metadata and transactional records. These logs show system identifiers, timestamps, message routing information, and delivery statuses.
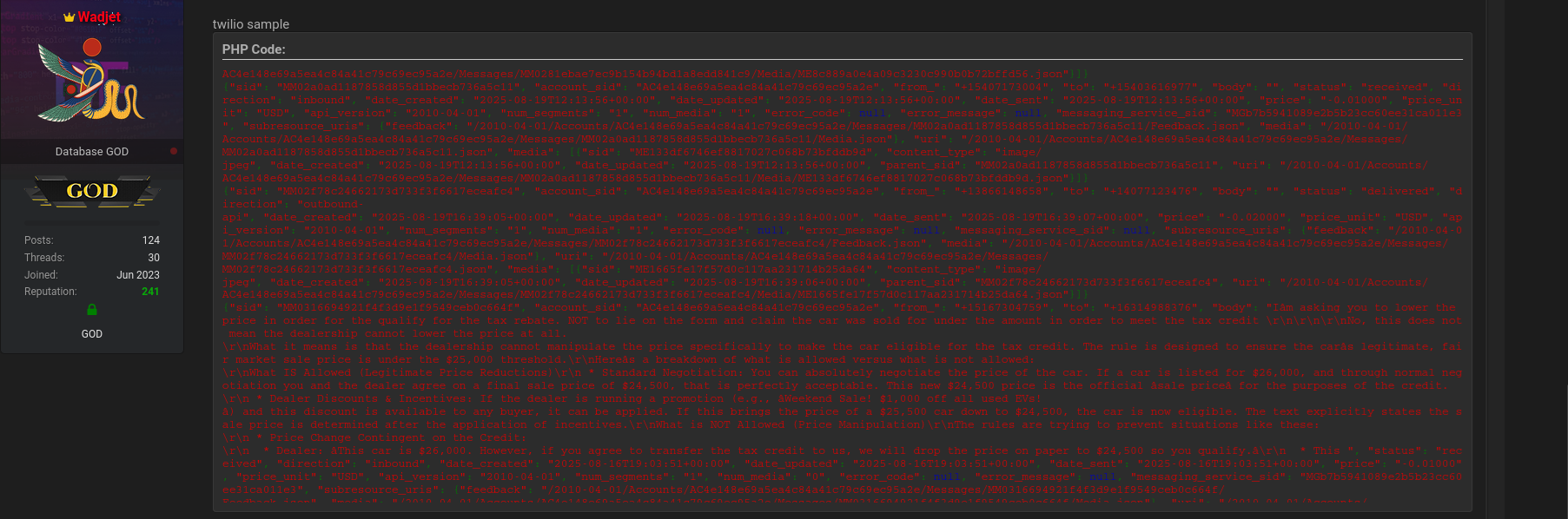
This wide spectrum of exposed data significantly elevates the risk of identity theft, phishing, financial fraud, account takeover, and social engineering campaigns 😰. The Edmunds data breach stands out not only for its scale but also for the depth of personal information leaked.
Why Shinyhunters Target High-Traffic Platforms
Cybercriminal groups such as Shinyhunters prioritize platforms with large user bases, high brand trust, and valuable datasets. Edmunds fits this profile perfectly. Automotive marketplaces involve financial decision-making, personal data sharing, and frequent user engagement.
Once breached, such platforms provide criminals with:
- Rich identity data
- High-value contact information
- Behavioral analytics
- Communication logs
These datasets are highly profitable on dark web markets, where criminals bundle and resell data to phishing gangs, fraud rings, and identity brokers 💰.
How the Breach Was Likely Executed
While official technical details remain undisclosed, cybersecurity analysts believe the breach likely occurred due to one or more of the following:
- Misconfigured cloud databases
- Insecure APIs
- Outdated authentication protocols
- Third-party service vulnerabilities
- Insufficient access controls
The leaked dataset structure suggests direct database access rather than limited credential harvesting. Such incidents highlight the importance of continuous vulnerability assessments and deployment of advanced threat intelligence solution platforms to detect abnormal data access patterns in real time.
Risks for Affected Users
The implications for affected users are serious. Exposure of personal and behavioral data enables multiple attack vectors:
Identity Theft
Criminals can combine leaked details to impersonate victims, open fraudulent accounts, or commit financial crimes.
Phishing and Social Engineering
Attackers can craft hyper-personalized phishing emails and SMS messages, dramatically increasing success rates 📩.
Credential Stuffing
If reused passwords are exposed, attackers can access banking, email, and social media accounts.
Financial Fraud
Phone numbers, emails, and activity logs facilitate account hijacking and unauthorized financial transactions.
The Edmunds data breach therefore represents not just a privacy incident, but a real-world security threat with potentially devastating consequences.
The Role of Dark Web Intelligence in Detecting Leaks
Dark web intelligence platforms play a critical role in uncovering breaches early. Through advanced crawling, scraping, and AI-driven analysis, these systems identify leaked databases, forum posts, and illicit data markets.
A recent dark web monitoring report revealed that Edmunds data appeared across multiple underground communities within hours of publication. Early detection allows organizations to respond faster, notify users, revoke compromised credentials, and mitigate further damage.
Legal Implications and Regulatory Impact
The breach raises significant concerns related to cybersecurity laws and regulations, including data protection frameworks such as GDPR, CCPA, and global consumer privacy laws. Organizations handling personal data are legally obligated to:
- Protect stored user information
- Notify users of breaches
- Implement corrective security measures
- Report incidents to regulators
Failure to comply can result in severe financial penalties, regulatory audits, and long-term reputational damage. The Edmunds data breach may trigger regulatory investigations, mandatory audits, and compliance reviews.
How Organizations Can Strengthen Their Defenses
Modern cybersecurity requires proactive defense models, not reactive responses. Organizations should deploy layered protection strategies including:
- Zero-trust security frameworks
- Endpoint detection and response
- Continuous vulnerability scanning
- Security information and event management (SIEM)
- AI-powered threat intelligence solution platforms
These measures help detect intrusions early, block lateral movement, and prevent large-scale data exfiltration ⚡.
Practical Checklist: How Users Can Protect Themselves
Here’s a simple checklist for users impacted by data breaches:
- Change all passwords immediately
- Enable two-factor authentication
- Monitor financial and email accounts
- Avoid clicking unknown links
- Watch for suspicious communications
- Use identity protection services
Staying vigilant significantly reduces the chances of successful exploitation.
One Critical Question Answered
Can leaked data ever be fully removed from the dark web?
No. Once data enters underground markets, it is often duplicated, resold, and archived indefinitely. This makes early detection, rapid response, and continuous monitoring essential.
Expert Insight on the Breach
According to Brian Krebs, cybersecurity journalist at https://krebsonsecurity.com/, “Modern breaches demonstrate that cybercrime is now an industrial-scale operation, and organizations must treat cybersecurity as a business-critical function, not an IT afterthought.”
This perspective reinforces the urgency for businesses to integrate intelligence-driven security architectures.
The Bigger Picture: Why These Breaches Are Increasing
Digital transformation, cloud migration, and third-party integrations have expanded organizational attack surfaces. Combined with automation and AI-powered hacking tools, cybercriminal efficiency has skyrocketed 🤖.
This shift means breaches like the Edmunds data breach are no longer rare events but persistent threats across industries. Proactive threat intelligence and continuous security validation are now fundamental operational requirements.
How Threat Intelligence Solutions Reduce Risk
Advanced intelligence platforms aggregate data from underground forums, malware campaigns, phishing networks, and exploit databases. By correlating these signals, they provide actionable alerts before breaches escalate.
Deploying a comprehensive threat intelligence solution allows organizations to:
- Identify emerging threats
- Block malicious infrastructure
- Detect leaked credentials
- Predict attack campaigns
This proactive capability dramatically reduces breach likelihood and response times.
Conclusion: Act Now to Reduce Your Risk
The exposure of sensitive user information in the Edmunds data breach underscores the escalating scale and sophistication of modern cyber threats. From identity theft to financial fraud, the risks are real, persistent, and costly.
Organizations must prioritize intelligence-driven cybersecurity frameworks, while individuals should remain vigilant, informed, and proactive. Continuous monitoring, rapid response, and strong digital hygiene are now essential defenses in a hyper-connected world 🌐.
Discover much more in our complete guide
Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


