WhatsApp Worm Alert 2025: Key Facts Revealed About This Banking Malware

➤Summary
The WhatsApp Worm has rapidly become one of 2025’s most alarming cyber incidents. Detected on September 29, 2025, this malware campaign targets WhatsApp Web users, spreading silently through trusted contacts and stealing sensitive banking credentials. 😱 Once activated, the trojan infiltrates devices, harvests data, and automatically sends malicious links to the victim’s chat list — turning each compromised user into a new infection source. According to experts from the Kaduu team, evidence linked to this worm surfaced during a dark web monitoring sweep, confirming that stolen credentials were being traded across underground networks.
🧬 How the WhatsApp Worm Works
The infection starts with a simple, familiar message: a file, a photo, or a video sent through WhatsApp Web. Victims unknowingly download the malicious payload, which installs a banking trojan disguised as a legitimate update. Once inside, the malware collects login data, OTP codes, and even session cookies from online banking applications. 🧨 This self-propagating mechanism turns the WhatsApp Worm into a weapon of social trust, leveraging relationships to compromise entire contact lists. The Kaduu researchers confirmed that many victims were unaware of any intrusion until their banking apps were locked out.
🕵️ Kaduu Discovery Through Dark Web Monitoring
During routine dark web monitoring, Kaduu analysts found a trove of compromised data, including banking credentials and session tokens, uploaded to a darknet marketplace labeled “WA-Trojan Kit v2.0.” This finding connected directly to the ongoing WhatsApp Worm activity. Stolen data was being advertised as part of a malware-as-a-service model, giving low-skill attackers the ability to infect users globally. The discovery, confirmed by the cyber threat intel report released by Kaduu, emphasized the rising trend of commercialized malware operations accessible through underground forums.
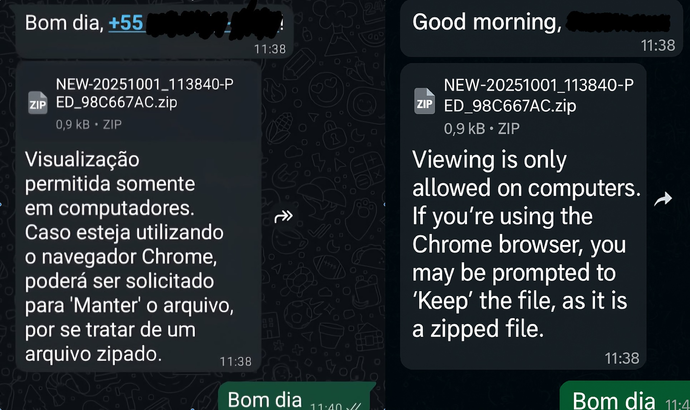
The image description: Message originating from a compromised WhatsApp contact (left, via X.com), alongside its translated version (right)
💡 Technical Breakdown of the Worm
Once executed, the worm initiates several stealth operations designed to maintain persistence and avoid detection:
- Collects system metadata and app permissions.
- Installs a mobile malware loader using encrypted communication.
- Hijacks WhatsApp Web sessions to send malicious links automatically.
- Steals credentials using accessibility permissions.
- Sends stolen information via secure HTTPS channels to command-and-control servers.
Security researchers from Sophos observed that the payload uses multiple encryption layers, dynamic C2 addresses, and domain rotation tactics — all characteristics of a highly adaptive malware family. 🔐
⚙️ Why This Attack Is More Dangerous
Unlike earlier phishing attacks or fake update campaigns, the WhatsApp Worm does not rely on user negligence alone. It exploits social engineering at its core, manipulating real conversations between trusted users. As a result, the infection spreads exponentially faster than typical spam-based campaigns. Victims unknowingly help the attackers expand their network by forwarding compromised links. The speed of this propagation has made traditional antivirus defenses less effective because detection occurs only after multiple infections have already taken place.
🧠 Insights from Kaduu’s Cyber Threat Intel Report
The cyber threat intel report released by Kaduu outlines the broader strategy behind this attack. The operators are part of an organized network monetizing stolen data through underground markets. 🕸️ The report confirms collaboration between multiple hacker groups sharing access to the same trojan infrastructure. One excerpt states, “This malware represents a hybrid threat — combining automation, trust manipulation, and financial theft at scale.” The findings highlight the sophistication of the threat actors, who use cloud-based dashboards to manage infections and track financial gain.
🧩 Global Impact and Threat Expansion
Although the first infections were observed among Brazilian banking customers, telemetry data shows the worm is spreading to Europe and Southeast Asia. IP traces link affected accounts in Portugal, Spain, and Indonesia. The adaptability of the malware indicates it could evolve into a cross-platform cybersecurity risk, targeting not only banking apps but also crypto wallets and corporate login portals. 🌍 Experts warn that attackers could modify the payload to infect Telegram or Signal, creating a new era of multi-platform worms powered by social connectivity.
💬 Expert Insight
“The WhatsApp Worm has turned social trust into a digital weapon. When malware leverages personal relationships, traditional defense models fail,”
— Lara Mendes, Lead Security Analyst, Kaduu Threat Research Unit.
✅ Practical Tip: How to Stay Protected
To help both individuals and organizations defend against this sophisticated malware campaign, here’s a quick checklist you can follow immediately:
| Action | Purpose |
| Avoid unexpected links, even from friends | Prevent auto-infection |
| Log out of WhatsApp Web sessions often | Disable stolen tokens |
| Use two-factor authentication on all accounts | Block unauthorized access |
| Install a trusted threat detection app | Identify malicious payloads early |
| Regularly monitor bank statements | Detect suspicious activity quickly |
🛡️ Pro tip: Always confirm with your contact through another channel before opening files or links shared via messaging apps. One small pause can prevent major data loss.
🔍 Related Cyber Threat Intelligence
The WhatsApp Worm campaign exposes how human behavior remains the easiest cyberattack vector. Studies show that 68% of recent data breaches originated from social manipulation tactics. By merging automation with emotional familiarity, cybercriminals have created the perfect storm. Attackers use breached databases, phishing frameworks, and credential reuse strategies to sustain the infection loop. For more deep-dive analyses and threat detection tools, visit DarknetSearch.com where you can explore real-time darknet intelligence resources and data breach monitoring solutions.
🧩 Why Businesses Should Care
While individual users are primary targets, enterprises face equal risk. Employees using WhatsApp Web on corporate devices can unknowingly spread malware across work networks. Sensitive internal data, login tokens, and authentication cookies can all be exposed through compromised browser sessions. As such, corporate security policies must integrate continuous cybersecurity awareness training, strict browser isolation, and threat detection systems to safeguard digital communication channels. 🏢
🧭 Conclusion: The Fight Against Social Engineering Worms
The WhatsApp Worm serves as a chilling reminder that digital trust can be weaponized. As automation merges with human error, attackers gain unprecedented leverage. Every message, link, or file from a known source must now be verified before interaction. Organizations and individuals must embrace continuous monitoring, data breach alerts, and adaptive defense strategies. 🔥 Cybercriminals thrive on inattention — staying alert is the best protection.
Discover much more in our complete guide.
Request a demo NOW.
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


