UCL Data Breach Revealed: 45,000 Records Leaked in Darknet Forum

➤Summary
The UCL data breach has sent shockwaves through the academic world after University College London, one of the UK’s top universities, was hit by a massive cybersecurity incident. The primary keyword UCL data breach first surfaced when the Kaduu team discovered a leaked database on the darknet forum Dread Forum on 01 October 2025. According to the threat actor known as “gorgina”, the compromised database contains 45,000 records, including names, dates of birth, IDs, academic scores, thesis topics, tuition details, and even bank account numbers. ⚠️
This cybersecurity breach has raised questions about how well universities are prepared to protect sensitive personal, financial, and academic information. With growing risks in higher education data systems, the incident highlights the urgent need for robust data protection in universities.
The Forum Post: Where the Leak Emerged
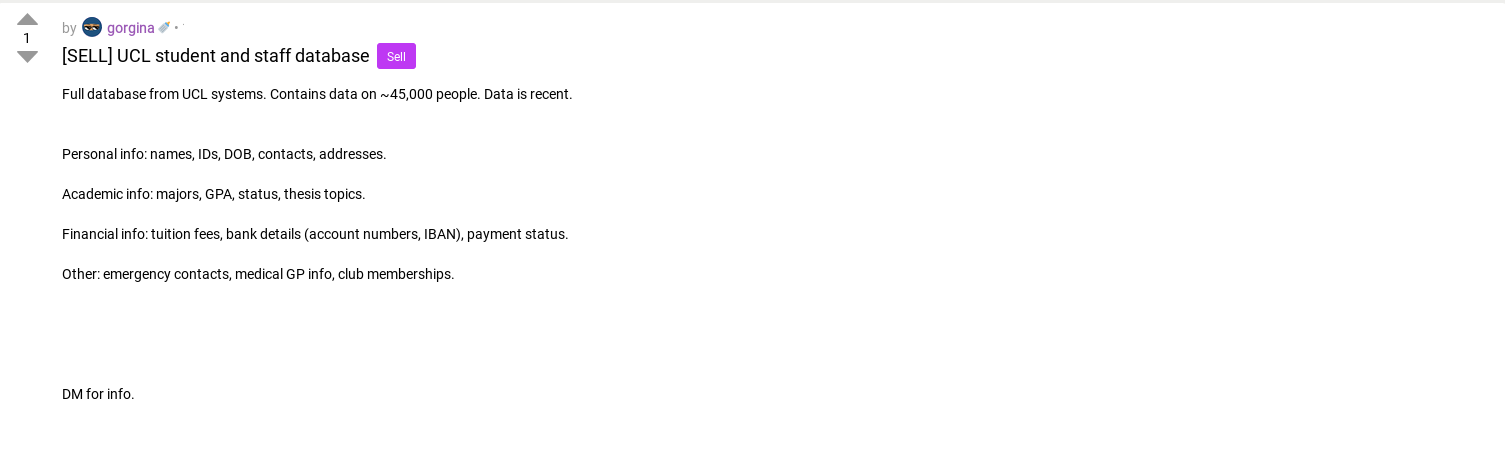
The discovery of the UCL database leak came when Kaduu’s darknet monitoring flagged a post offering the stolen dataset.
Forum details:
- Author: gorgina
- Forum: Dread Forum
- Date posted: 01 October 2025
- Post excerpt:
“Full database from UCL systems. Contains data on ~45,000 people. Data is recent.”
The post included a preview of stolen data and advertised bulk access to potential buyers. Darknet forums like Dread are known for trading stolen credentials and sensitive data. According to analysts, such datasets often spread rapidly, appearing on multiple platforms within days. 🔍
[Screenshot Proof from Forum]
What Data Was Leaked in the UCL Data Breach?
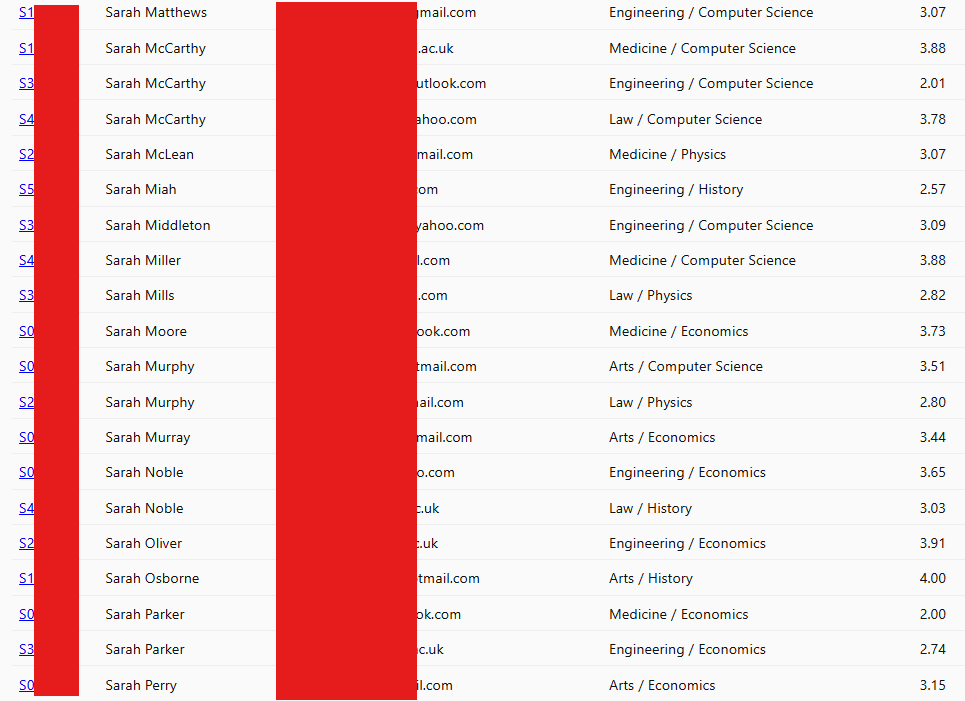
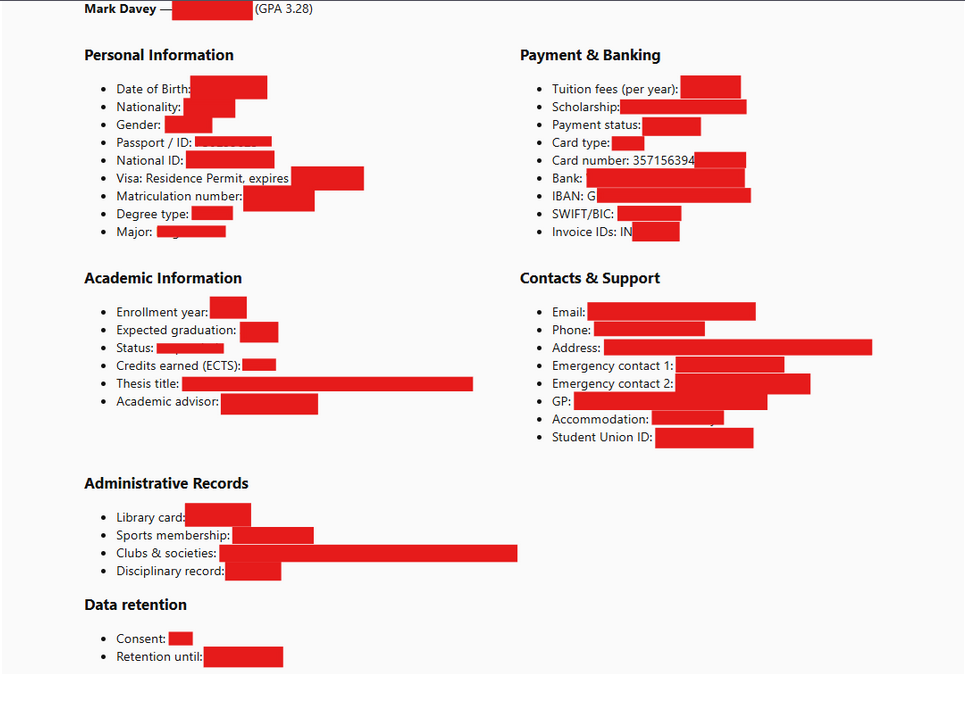
The exposed UCL database includes four key categories of information:
- Personal Info
- Names, student/staff IDs, DOB
- Email addresses, phone numbers
- Home addresses
- Academic Info
- Courses, majors, GPA
- Thesis and dissertation topics
- Enrollment and academic status
- Financial Info
- Tuition fees and balances
- Bank details: IBAN, account numbers
- Scholarships and bursaries
- Other Details
- Emergency contacts
- GP and medical registration info
- University club memberships
This combination makes the dataset especially harmful, as it links identity information with financial data.
[Leaked Database Screenshot]
[Leaked Database Screenshot]
Why This Data Breach Is So Severe
At least 45,000 records are impacted, potentially covering most of UCL’s student body and staff. The severity lies not just in the scale but in the type of data leaked. For example:
- Identity theft is enabled by full personal data.
- Financial fraud is possible through bank info. 💳
- Targeted scams can be designed using academic data (e.g., fake scholarship offers).
- Medical details and emergency contacts open doors to emotional manipulation.
How Did the Hackers Breach UCL Systems?
The exact method of entry is still unknown, but possible attack vectors include:
- Phishing: Emails tricking staff into sharing login credentials.
- Exploited vulnerabilities: Outdated university software may have been targeted.
- Credential stuffing: Using previously leaked passwords.
- Insider threat: A staff member with privileged access leaking data.
Practical Tip 🛡️: Always use strong, unique passwords and enable multi-factor authentication for academic and personal accounts.
University Response to the Breach
As of writing, UCL has not made a public statement about the breach. Internal communications suggest that IT services are investigating, and UK regulators such as the Information Commissioner’s Office (ICO) and National Cyber Security Centre (NCSC) may become involved.
Under UK GDPR, if UCL is found negligent, it could face heavy fines and be forced to implement strict data-protection measures.
Reaction from Staff and Students
The UCL community has expressed frustration and concern:
- “If my bank details are on the darknet, my whole financial life is at risk.” – UCL postgraduate student.
- “We trusted UCL with everything from our health to our academic history. This is unacceptable.” – Senior lecturer.
The sense of betrayal is palpable, particularly as universities are supposed to safeguard personal data as diligently as banks or hospitals.
Expert Commentary
Cybersecurity specialists emphasize that universities are prime targets.
Dr. Aisha Patel, cybersecurity researcher at King’s College London, said:
“This isn’t just a database; it’s a complete mapping of identities, finances, and academic journeys. For cybercriminals, it’s a goldmine.”
James Thornton, director of CyberSafe Education, noted:
“The UCL data breach shows universities must treat cybersecurity as a frontline priority, not a secondary IT issue.”
Darknet Market Impact of the UCL Data Breach
The dataset has already appeared on Dread Forum, but security experts expect it to be mirrored on other darknet sites soon. Once a leak spreads, containment is nearly impossible. According to DarknetSearch, similar academic leaks have historically been sold, shared, and repackaged multiple times across marketplaces.
This means affected individuals may face years of ongoing threats ranging from phishing attacks to fraudulent bank activity.
Checklist: What Victims Should Do Now ✅
If you believe you are affected by the UCL database leak:
- Monitor all bank accounts for unusual activity.
- Enable alerts with credit agencies.
- Change UCL and personal account passwords immediately.
- Be cautious of phishing emails pretending to be UCL staff.
- Contact your bank to add extra fraud protections.
The Bigger Picture: Cybersecurity in Higher Education 🎓
This breach is a wake-up call for UK universities. Institutions often handle massive amounts of data but lack robust cyber defenses. With rising attacks against schools and universities worldwide (BBC Cybersecurity report), higher education may need stricter government oversight.
The UCL case will likely accelerate calls for sector-wide security standards, regular audits, and mandatory reporting of breaches.
Conclusion
The UCL data breach is one of the largest academic data breach incidents in UK history, exposing personal, financial, and academic records of nearly 45,000 individuals. With the leak now circulating on deepweb forums, the impact could be long-lasting for students, staff, and the university itself.
Universities worldwide should take this as a warning: cybersecurity is no longer optional. For UCL’s community, vigilance and immediate action are essential.
👉 Discover much more in our complete guide
👉 Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


