Ryanair Data Breach: 7 Key Findings Revealed in This Urgent Analysis

➤Summary
The Ryanair data breach has emerged as one of the most discussed alleged cybersecurity incidents of late 2025, capturing the attention of security teams, CISO leaders, Government regulators, and Media and Publishing professionals across Europe. According to publicly circulating claims posted by a threat actor, sensitive operational data and internal messages may have been exposed. While Ryanair has not confirmed these allegations, extensive discussions on cyber-intelligence platforms and dark-web monitoring sources continue to highlight the potential impact. This article provides a deeply researched overview of the alleged event, why it matters, and what organizations can learn from it. We reference threat-intelligence sources, including the alert published by Brinztech and monitoring resources such as https://darknetsearch.com/ 🔍.
Throughout this report, we will analyze how an alleged leak of email addresses, ticket bookings, flight schedules, and internal communications could influence security posture, customer trust, and industry resilience. Whether you belong to aviation, enterprise security, or Government oversight, understanding this event helps strengthen your own preparedness and response strategies. ✈️
Overview of the Alleged Incident
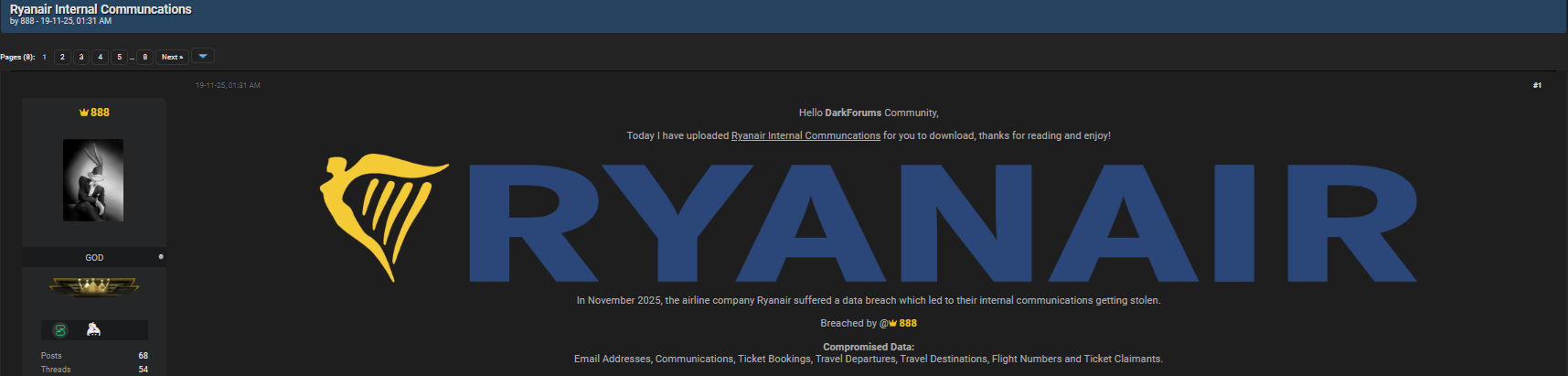
In November 2025, a threat actor identified as “888” on a dark-web forum claimed responsibility for leaking internal Ryanair communications, including ticket claimant identities, travel destinations, and flight numbers. The report surfaced through a published Breach Alert on the Brinztech website, which you can access here:
➡️ Brinztech – Alleged Database Leak Report
Although no official statement has validated the attack, cybersecurity analysts have flagged the claims as “highly credible” based on the structure of the dataset samples shared by the attacker. The alleged Ryanair data breach was said to include:
- Email addresses
- Internal communications
- Ticket bookings
- Travel departures
- Travel destinations
- Flight numbers
- Ticket claimant information
These elements, if authentic, could represent a significant internal communications leak affecting customer privacy and operational transparency.
Motivations Behind the Threat Actor
Cyber-investigators often explore why cybercriminals target major airlines. Airlines manage vast amounts of personal data, travel details, payment information, and corporate communication systems—making them prime targets. Within dark-web activity logs, threat actors frequently mention airlines due to their high volume of customer data and lucrative booking systems. In this case, the actor “888” showcased data snippets that appear designed to attract high-value buyers. While authenticity remains under investigation, the presence of structured flight and booking information contributes to the conversation surrounding the internal communications leak and its potential implications.
The Data Exposed: What Analysts Observed
Below is a structured breakdown summarizing what cybersecurity teams have discussed regarding the alleged leak:
| Data Category | Description Observed in Alleged Dataset |
| Email Addresses | Customer and internal email references |
| Internal Communications | Messages between operational or support teams |
| Ticket Bookings | Passenger booking entries |
| Travel Departures | Outbound flight scheduling details |
| Destinations | Arrival airports and regional routes |
| Flight Numbers | Specific route identifiers |
| Ticket Claimants | Names linked to booking IDs |
| This list appears across threat-monitoring channels such as https://darknetsearch.com/, which indexes dark-web listings and alerts for analysts. | |
| Practical Tip: If you manage customer bookings or internal messaging systems, ensure message logs and booking records are encrypted both at rest and in transit. Strong encryption reduces the impact in case logs or databases are compromised.🔐 |
Potential Implications for Passenger Privacy
The alleged Ryanair data breach highlights how personal information—when combined—can create significant risk for airline passengers. Privacy implications include highly targeted phishing attempts, travel-based social engineering attacks, fraudulent booking modification schemes, and identity profiling. Attackers could use travel routes and flight numbers to predict traveler behavior, making them vulnerable to scams. 📧
Question: Can leaked travel details be used to impersonate passengers?
Answer: Yes. Cybercriminals often combine emails, booking references, and travel itineraries to impersonate customers in airline support channels, aiming to modify bookings, claim refunds, or steal loyalty points.
Operational Impact and Industry Risk
If internal message logs were leaked, it may not only affect passengers—it could also reveal operational strategies, staff workflows, or coordination between departments. These insights could potentially provide visibility into route performance or planning discussions, a risk relevant not only to airlines but also to Media and Publishing analysts investigating industry competitiveness.
Furthermore, CISO leaders across the aviation industry emphasized that operational message exposure can reveal system architecture, decision-making chains, and even the internal escalation process during disruptions. Because similar incidents have previously affected retail and Government sectors, the aviation industry is now reassessing its monitoring and access-control protocols. 🛡️
Forum-Post Proof (Placeholder)
Data-Post Proof (Placeholder)

Recommendations for Enterprises and Airlines
Cybersecurity teams can apply several lessons emerging from this event:
- Strengthen MFA requirements for internal access
- Encrypt logs and internal communications
- Segment booking systems from messaging systems
- Adopt continuous dark-web monitoring platforms
- Train employees to identify spear-phishing patterns
Checklist for CISO Teams: - Review privileged access logs
- Audit booking database permissions
- Validate patching schedule for CRM tools
- Update incident-response documentation
- Conduct a secure-configuration review for communication systems
Airline CISO teams stress that while airports maintain high physical security, internal digital systems—from ticketing platforms to crew-communication portals—must be equally fortified.
Editorial Perspective: What Experts Are Saying
One cybersecurity expert commented:
“Airlines operate on thin margins and heavy automation. A single compromised messaging system can become a blueprint for attackers. Data discipline is no longer optional—it’s essential.”
Industry watchers in Media and Publishing also emphasize that transparency during alleged cybersecurity events shapes public trust. Whether the breach is confirmed or disproven, the way an organization communicates with regulators, passengers, and analysts significantly influences perception.
Conclusion
Whether ultimately verified or disproven, the alleged Ryanair data breach presents important lessons for airlines, technology companies, Government cybersecurity frameworks, and enterprise security leaders worldwide. From the integrity of internal communications to the protection of booking information, every digital component of an airline’s ecosystem demands ongoing vigilance. Organizations must monitor threat activity, reinforce system defenses, and ensure that communication remains responsible and proactive. Security isn’t a one-time investment—it is a continuous effort grounded in awareness, planning, and resilience. ✨
Discover much more in our complete guide
Request a demo NOW.
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


