RedTigerSupport.org 2026 Leaks: Urgent Global Breach

➤Summary
RedTigerSupport.org 2026 leaks have emerged as a major cybersecurity incident after sensitive user data was exposed and published on the underground forum breachforums.bf by the InfinityBreach Group. The breach, disclosed on January 27, 2026, resulted from a successful password admin brute force attack, leading to unauthorized access and the theft of critical user records from across more than 100 countries 🌍. This incident underscores the growing threat posed by credential-based attacks and the urgent need for stronger authentication, continuous monitoring, and proactive defense strategies. In this comprehensive guide, we explain what happened, who was impacted, what data was compromised, and how organizations and individuals can protect themselves against similar threats in the future.
What Are the RedTigerSupport.org 2026 Leaks?
The breach allowed the InfinityBreach Group to extract one database file containing sensitive user information, later published and advertised on breachforums.bf.
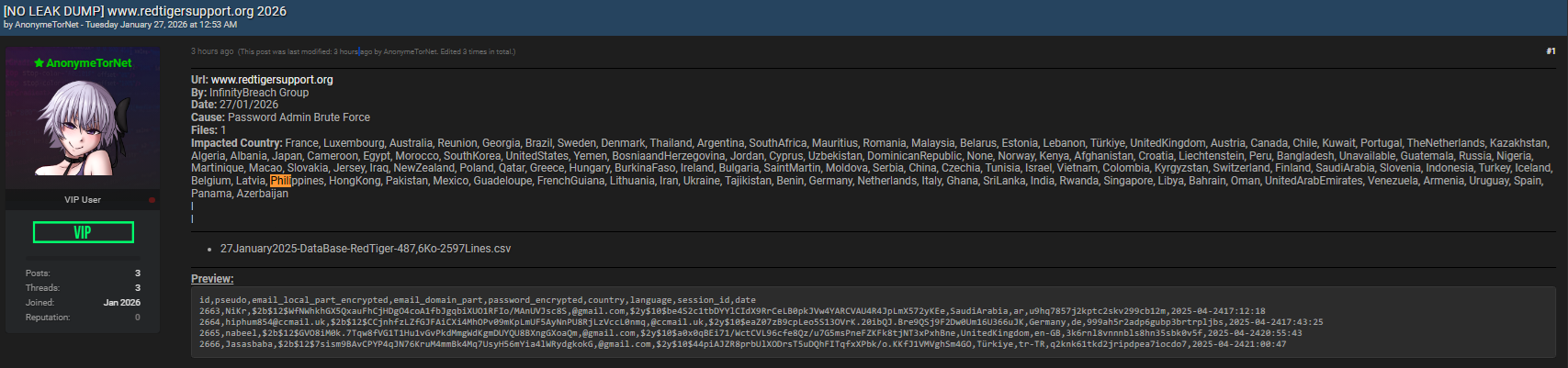
RedTigerSupport.org is a technical support and assistance platform used by a wide international audience. As a result, the compromised dataset spans dozens of regions, industries, and user profiles. The leaked information includes encrypted email data, encrypted passwords, session identifiers, country codes, and timestamps, making the exposure particularly dangerous from both a privacy and fraud perspective 😨.
Breach Timeline and Attack Method
According to forum disclosures, the breach occurred due to password admin brute force, a method where attackers systematically attempt multiple password combinations until administrative credentials are cracked. Once successful, attackers gain full control over the backend system.
Key incident details include:
- Forum: breachforums.bf
- Target: www.redtigersupport.org
- Threat actor: InfinityBreach Group
- Date published: 27 January 2026
- Cause: Password admin brute force
- Files leaked: 1 database file
This highlights a persistent weakness in many platforms: insufficient brute-force protection mechanisms and inadequate account security policies 🔓.
Scope of Impact: A Truly Global Breach
One of the most alarming aspects of the RedTigerSupport.org 2026 leaks is the sheer number of impacted countries. Users from over 100 nations were affected, including France, United Kingdom, United States, Germany, Canada, Australia, Japan, Brazil, India, South Africa, Turkey, Philippines, Singapore, and many more.
This global exposure dramatically increases the breach’s risk profile. International victims face heightened threats of:
- Identity theft
- Credential stuffing attacks
- Phishing campaigns
- Business email compromise
- Social engineering fraud
For attackers, such a broad dataset offers immense financial and strategic value 💰.
What Data Was Compromised?
The leaked database reportedly includes the following fields:
- id
- pseudo
- email_local_part_encrypted
- email_domain_part
- password_encrypted
- country
- language
- session_id
- date
Although some fields were encrypted, attackers often leverage decryption techniques, password reuse, and correlation analysis to exploit this data. Even partially encrypted datasets can become dangerous when combined with other leaked databases across the dark web.
This is precisely why dark web monitoring and continuous breach intelligence gathering are essential components of modern cybersecurity strategies.
Why Brute Force Attacks Are Still So Effective
Despite advancements in cybersecurity, brute force remains a highly successful attack technique. Many organizations still fail to implement:
- Rate limiting
- CAPTCHA protection
- Account lockout mechanisms
- Multi-factor authentication
This makes administrative accounts especially vulnerable. Once compromised, attackers can bypass all internal security controls, export full databases, and plant backdoors for future access 😈.
The RedTigerSupport.org 2026 leaks demonstrate that even basic security hygiene failures can result in massive data exposure.
How Stolen Data Is Used in Cybercrime
Once data appears on underground forums, it rarely stays isolated. Threat actors resell, bundle, and trade breached datasets across multiple criminal marketplaces. This fuels:
- Phishing attacks
- Credential stuffing
- Identity fraud
- Financial scams
- Corporate espionage
A comprehensive dark web monitoring report can reveal whether leaked data is spreading across multiple forums, encrypted messaging channels, and illicit marketplaces.
Organizations that compare dark web monitoring platforms gain critical insight into data exposure timelines and attacker behavior, enabling faster response and mitigation.
The Role of Dark Web Intelligence in Breach Detection
Advanced dark web monitoring allows organizations to detect breaches before official disclosures or user complaints surface. By tracking underground forums, marketplaces, and encrypted communities, security teams gain early warnings about emerging threats.
Darknetsearch.com platform provides continuous updates, breach intelligence, and threat actor analysis, helping enterprises identify compromised assets and respond quickly.
Legal and Regulatory Implications
The RedTigerSupport.org 2026 leaks carry significant regulatory consequences under global cybersecurity laws and regulations, including GDPR, CCPA, NIST, ISO 27001, and regional data protection frameworks.
Organizations handling personal data are legally required to:
- Implement reasonable security controls
- Protect authentication systems
- Report breaches promptly
- Notify affected users
Failure to meet these obligations can result in:
- Heavy regulatory fines
- Legal liability
- Compliance violations
- Reputation damage
For multinational organizations, regulatory exposure multiplies due to cross-border data transfers and jurisdictional enforcement 🏛️.
Risks to Impacted Users
Affected individuals face heightened risks, including:
Identity Theft
Attackers may correlate leaked credentials with other datasets to impersonate victims.
Phishing Attacks
Cybercriminals craft targeted emails and messages using leaked language and regional data.
Reused passwords enable access to banking, email, and corporate systems.
Long-Term Surveillance
Session IDs and login timestamps allow attackers to map user behavior and access patterns 👁️.
These risks underscore the importance of immediate password changes and continuous monitoring.
Practical Checklist: How to Protect Yourself After a Data Breach
Here is a simple, actionable checklist for affected users:
- Change all passwords immediately
- Enable multi-factor authentication
- Avoid password reuse
- Monitor accounts for suspicious activity
- Use breach alert services
- Watch for phishing emails
Organizations should additionally deploy continuous vulnerability scanning, account monitoring, and intelligence-driven security controls 🔐.
One Critical Question Answered
Can encrypted passwords still be exploited?
Yes. Encrypted or hashed passwords can often be cracked using brute force, rainbow tables, or reused credential correlation across multiple breaches.
How Enterprises Can Prevent Similar Breaches
To prevent incidents like the RedTigerSupport.org 2026 leaks, organizations should adopt a layered defense model:
- Strong authentication policies
- Rate limiting and login monitoring
- Multi-factor authentication for admins
- Continuous penetration testing
- Dark web intelligence integration
Security teams should also choose the quality dark web monitoring tools to ensure they receive the fastest, most actionable alerts.
Why Dark Web Monitoring Is Now a Business Necessity
In today’s cyber threat environment, breaches often surface on underground forums before victims even realize data is compromised. Effective dark web monitoring enables early breach detection, faster containment, and reduced financial losses.
A reliable dark web monitoring report helps organizations:
- Detect leaked credentials
- Identify targeted campaigns
- Monitor threat actor activity
- Prevent ransomware escalation
This proactive intelligence capability transforms cybersecurity from reactive to predictive ⚡.
The Bigger Cybersecurity Picture
The RedTigerSupport.org 2026 leaks highlight a broader global trend: attackers increasingly target authentication systems and weak credential controls. As organizations accelerate digital transformation, login portals, APIs, and admin panels remain high-risk entry points 🌐.
Without continuous monitoring, even well-secured systems can fall victim to credential-based attacks.
Expert Insight
Cybersecurity researcher Troy Hunt states: “Credential attacks remain one of the most effective entry points for cybercriminals. Multi-factor authentication and breach monitoring are no longer optional—they are essential.”
This reinforces why organizations must treat identity protection as a core security function.
Future Outlook: Credential Attacks Are Rising
As password reuse remains widespread and automation tools grow more sophisticated, brute force and credential stuffing attacks are expected to increase. AI-powered cracking techniques, botnets, and malware automation will further accelerate this trend 🤖.
Organizations that invest in intelligence-driven security and continuous authentication monitoring will be best positioned to mitigate these evolving threats.
Conclusion: Take Action Before It’s Too Late
The RedTigerSupport.org 2026 leaks serve as a powerful reminder that weak authentication controls can expose vast amounts of sensitive data in minutes. From identity theft to regulatory penalties, the consequences of such breaches are severe and long-lasting.
By adopting proactive defense strategies, continuous monitoring, and intelligence-driven security solutions, organizations and individuals can significantly reduce their exposure to cyber threats.
Discover much more in our complete guide
Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


