Recruiterstaff.com Data Breach Allegedly Leaked — What You Need to Know

➤Summary
The Recruiterstaff.com data breach has reportedly surfaced in dark-web monitoring circles, raising red flags for thousands of job seekers and recruiters worldwide. A post made by user “ayame” on Breachstars.hn (06 Nov 2025) claims that a recruitment database leak took place in August 2025, exposing both job listings and resumes.
The seller listed the database for $1,000 (negotiable) — a clear sign the data holds significant value. 😨 According to cybersecurity firm Kaduu, their analysts discovered the listing during routine dark-web surveillance, signaling that the recruitment ecosystem could be under a new kind of threat.
For CISOs and Security Practitioners, this incident underscores the growing need for proactive Information Security strategies within recruitment and HR platforms. In this article, we unpack the leak, its implications, and exactly what to do if your data is in a recruiter database leak.
What’s the Allegation?
According to the post on the underground forum:
- The Kaduu monitoring team detected the Recruiterstaff.com data breach while scanning Breachstars.hn.
- User “ayame” listed the alleged stolen database, pricing it at $1,000 USD (negotiable).
- The leaked dataset supposedly includes job listings and resumes, dated August 2025, with the forum post published on 06 November 2025.
- The thread features proof sections (“forum post proof” and “data post proof”), although no public verification exists.
- As of now, RecruiterStaff.com has not confirmed nor denied the incident. ⚠️
Claimed Compromised Fields
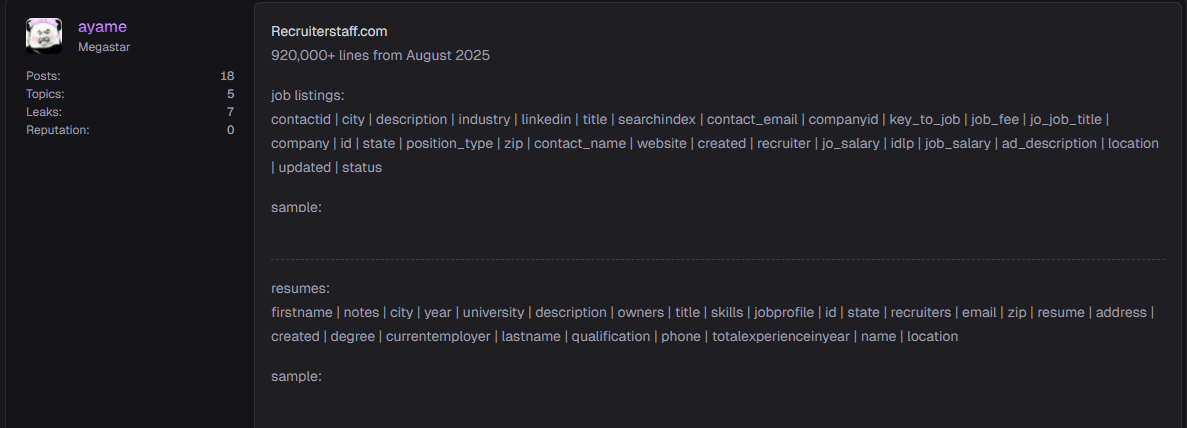
Job listings:
contactid | city | description | industry | linkedin | title | searchindex | contact_email | companyid | key_to_job | job_fee | jo_job_title | company | id | state | position_type | zip | contact_name | website | created | recruiter | jo_salary | idlp | job_salary | ad_description | location | updated | status
Resumes:
firstname | notes | city | year | university | description | owners | title | skills | jobprofile | id | state | recruiters | email | zip | resume | address | created | degree | currentemployer | lastname | qualification | phone | totalexperienceinyear | name | location
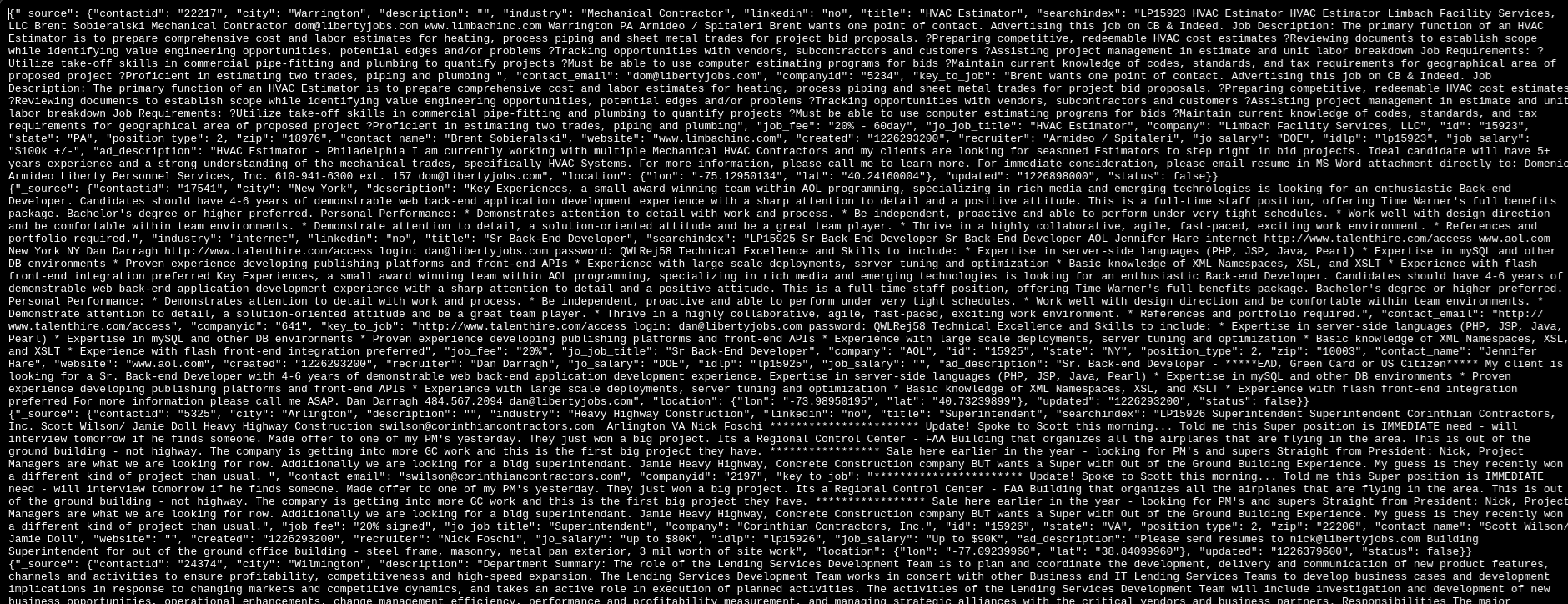
💥 This information paints a concerning picture — both recruiter contact details and job seeker personal data appear in the same dataset.
How the Leak Surfaced
🕶️ Here’s the sequence of events, based on sources and dark-web tracking reports:
- Kaduu’s cyber-intelligence division detected a post offering the Recruiterstaff.com data breach dataset.
- The seller described it as “full recruiter and job data with resumes,” uploaded samples as proof.
- Leak date: August 2025; forum publication: 06 November 2025.
- Price: $1 k USD, negotiable.
- Kaduu noted the data volume suggests “hundreds of thousands of records.”
- No public statement from RecruiterStaff.com has yet verified the legitimacy.
Key takeaway:
Even without confirmation, the presence of such structured fields indicates the dataset likely originated from a legitimate recruitment system.
What Data May Have Been Exposed
The potential recruitment database leak contains two main sections: job listings and candidate resumes.
Job listings data
Fields suggest the following info may be exposed:
- Recruiter contact details (emails, names)
- Job fees & salaries
- Locations (city, state, zip)
- Posting timestamps (created/updated)
- Company IDs and job keys
Candidate resumes data
Information may include:
- First and last names
- Address, email, phone
- Skills, job titles, years of experience
- Education (university, degree, qualification)
- Resume text and job profile summaries
- Current employer and recruiters
🧠 Insight: Such detailed combinations can enable highly targeted scams and phishing attempts. Attackers can impersonate recruiters or employers to trick victims into revealing more personal information or paying fraudulent job “processing fees.”
Why This Is Serious 😬
Unlike many corporate leaks, recruitment breaches combine both sides of the hiring process. This gives attackers contextual, up-to-date, and verified identity data. Experts note: “Resumes are treasure maps for identity theft — they contain almost everything criminals need.”
Potential risks include:
- 🧾 Identity theft via resume data (names, phones, addresses)
- 🎯 Targeted phishing using authentic recruiter or company data
- 💰 Fraudulent job offers or fake hiring schemes
- 🕵️ Corporate espionage (targeting specific recruiters or industries)
- 🧑💼 Compliance penalties under GDPR/CCPA if unreported
According to Cybernews, job-related leaks have led to millions of exposed resumes across platforms, affecting both job seekers and HR departments (CyberNews report).
What To Do if Your Data Might Be Affected
If you suspect your information was part of the alleged Recruiterstaff.com data breach, take these proactive steps immediately.
✅ Candidate checklist
- Change passwords on your job portals and associated email accounts.
- Enable 2FA (two-factor authentication) wherever possible.
- Be cautious of emails requesting extra verification or “job application fees.”
- Search for your details on data-breach checking tools like darknetsearch.com.
- Set up alerts for identity-theft monitoring or credit-report tracking.
- If you’re in a GDPR or CCPA jurisdiction, contact the platform and request confirmation or erasure of your data.
🧰 Recruiter & platform checklist
- Launch internal investigations and third-party forensics.
- Temporarily suspend risky systems and reset all admin credentials.
- Notify affected clients and candidates transparently.
- Patch vulnerabilities, audit APIs, and enable encryption at rest.
- Communicate with regulators — silence worsens brand damage.
- Review third-party integrations and vendor access.
💡 Practical Tip: Don’t wait for confirmation. Assume exposure and secure your accounts now. Prevention is cheaper than remediation.
Is the Leak Verified Yet?
Q: Is the Recruiterstaff.com data breach officially confirmed?
A: Not at the moment. The claim remains alleged, pending response from the platform or a verified cybersecurity source. Kaduu’s findings are credible but still unverified by independent parties.
Q: Could this be fake?
A: While some dark-web “breaches” are exaggerated, the detailed database schema posted (job listing & resume fields) indicates authenticity or partial access to genuine systems.
Q: What happens next?
A: Typically, such leaks circulate in private groups before becoming public torrents. If confirmed, regulators may require notifications to affected users.
Industry Perspective 💼
Cybersecurity specialists warn that the recruitment database leak trend is rising. “Human resources data is the new oil,” says security researcher Maren Ito. “Hackers monetize both employer and candidate details — it’s dual-sided leverage.”
Statistics:
- Over 3.5 million resumes were exposed through misconfigured databases in 2024.
- 62 % of recruitment platforms still rely on outdated encryption standards.
- The average response time after a recruitment data breach is 92 days — long enough for attackers to exploit.
Platforms must enhance hiring platform security with better data governance, continuous monitoring, and encrypted submissions.
Why This Case Matters Globally 🌍
Recruitment is borderless. If the Recruiterstaff.com data breach is confirmed, candidates from the US, UK, Canada, and the Philippines could all be affected. Job boards often host global applications, meaning local laws like GDPR, CCPA, and the Philippine Data Privacy Act all apply.
Moreover, personal data in recruitment is often reused by partner agencies — multiplying exposure. One breach can ripple across dozens of vendors.
Expert Quote:
“The challenge is not the breach itself, but the silent exposure of unknowing candidates. Once data hits the dark web, control is gone forever.” — A. Velasquez, Kaduu Research Lead
The Road Ahead
🔐 Whether or not the Recruiterstaff.com data breach is confirmed, the recruitment industry must rethink how it stores, shares, and secures sensitive personal data. Hiring data is no longer trivial — it’s an identity blueprint. Companies must prioritize transparency, timely reporting, and proactive user protection.
For users: stay vigilant. Watch for phishing, strange calls, or unexpected “job offers.” If you suspect exposure, follow the checklist above and consider reporting to relevant authorities.
Discover much more in our complete guide
Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


