New Kaduu Release
➤Summary
We are happy to announce a new version of Kaduu 2.1! It includes a few cool features.
Discord Monitoring
What is Discord?
Discord is a popular communication platform designed for online communities and gamers. It offers a variety of features including text, voice and video chat, file sharing, and gaming integrations. Discord is available as a browser-based web app, a desktop app for Windows, MacOS, Linux and as mobile apps for iOS and Android. The platform allows users to create and join virtual servers (also called “Discord servers”) to connect with others based on common interests.
How is Discord used by hackers?
Discord can be used by hackers in various ways, including:
- Sharing hacking tools and tutorials: Discord servers can be used as platforms to share hacking tools and tutorials with other individuals.
- Coordinating attacks: Hackers can use Discord channels to coordinate and execute attacks on websites, networks, or other targets.
- Phishing and scamming: Hackers may use Discord to phish personal information or scam users through fake giveaways or other deceitful means.
- Spreading malware: Hackers can spread malware through links or files shared on Discord servers, infecting other users’ devices.
How many channels exist?
It’s not possible to determine the exact number of Discord channels that exist, as the platform allows for an unlimited number of servers and channels to be created. The number of Discord channels continues to grow as new servers are created and existing servers add new channels. Discord has over 150 million monthly active users, so there are likely a large number of channels across all the servers on the platform.
What channels do we monitor?
- “Blackhats underground”: https://discord.gg/k8Jxuu66gX– dumps
- “PirateShips CCs Shop”: https://discord.gg/kVv58B63g2 – credit cards
- “DarkSec”: https://discord.com/invite/wTQa64JhJY – Hacking group
- “A9 Market”: https://discord.gg/a9market – credit cards
- “Rent 8 hacker”: https://discord.gg/cUTadTRNh9 – Rent a hacker
- “sPlug”: https://discord.gg/pzYzqcJtzz – PII data
- “DarkCat.exe”: https://discord.gg/2aW8KBEKxt
- “Anonymity”: https://discord.gg/2trMf94kPB
- “Evil Empire”: https://discord.gg/QVQA4duZ9M – Phishing, stealer logs
- “Alka Tim”: https://discord.gg/PrnUNDgRAN – Turkish hacking team
- “Dark Matter Market”: https://discord.gg/VTWxZhDEvG
- “Trisoft vlan”: https://discord.gg/ErDj63yY – ;Malware talks
- “Anon Cyber Team”: https://discord.gg/jac3w4sGXq
- “Netcat hacking”: https://discord.gg/2rU7t5bEY5
- “Backward Development”: https://discord.gg/8gRcfgvtVK
- “Oversec”: https://discord.gg/cwxvPWtdsj – another turkish hacking group
- “Christian Hacking club”: https://discord.gg/qJyzCTEAkC – mostly news from cybersec world
- and many more
Hacker Forum Monitoring
What is the threat?
In this deep-web search, we log in to +50 known hacker forums with various accounts and submit the keyword that is entered in the search mask of Kaduu. For example, you can enter your company name or a brand to see if people are talking about it in the forums. If there are results for the search term, we show them in a link as a download. The corresponding pages are saved as a screenshot and also as a web page. We focus on the most popular forums in English, German, French and Russian language.
Introduction
Hacker forums provide clues to possible attack techniques, attack preperations against clients or leacked data. Kaduu enables you to explore and monitor hacker forums, allowing our clients to gain a better understanding of the tools and techniques used by hackers and the areas that are most likely to come under attack.
How do we search forums?
In this deep-web search, we log in to +50 known hacker forums with various accounts and submit the keyword that is entered in the search mask of Kaduu. For example, you can enter your company name or a brand to see if people are talking about it in the forums. If there are results for the search term, we show them in a link as a download. The corresponding pages are saved as a screenshot and also as a web page. We focus on the most popular forums in English, German, French and Russian language.
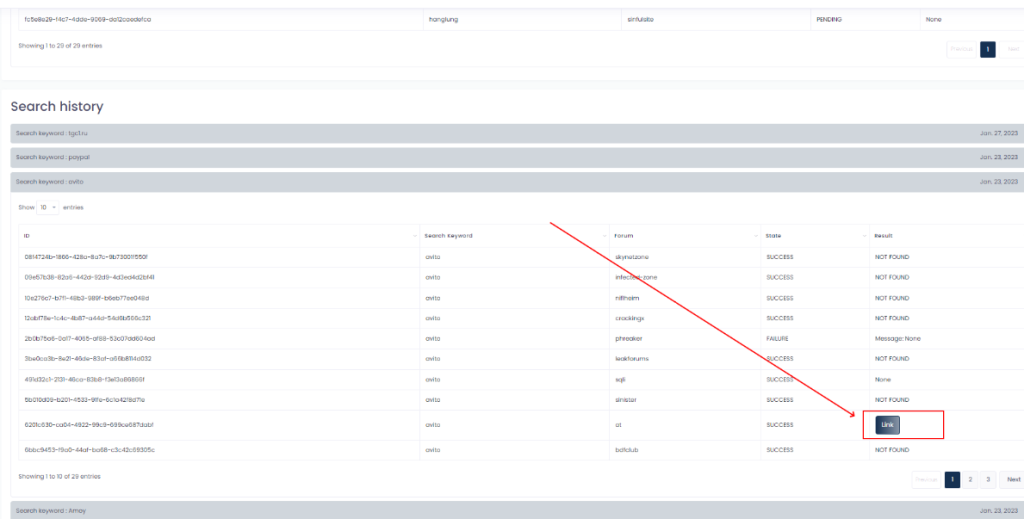
How do we present the data?
If we find any result related to your search keyword, you can download the screenshot and html file in an archive.
Telegram Monitoring
Hackers share data leaks on Telegram in different ways. In some channels, hackers post data dumps with short explanations about what people can find in them. In these channels, minimal conversations occur. However, there are also dedicated hacking groups where many members actively discuss various aspects of Internet crime. There are many more ways Telegram is used by hackers:
- Communication: Telegram can be used by hackers as a secure means of communication, as it offers end-to-end encryption and the ability to create self-destructing messages. This allows hackers to communicate with one another without fear of being monitored by law enforcement or other authorities.
- Command and control: Telegram can be used to create a command and control (C&C) infrastructure for malware. This allows hackers to remotely control infected devices, exfiltrate data, and perform other malicious activities.
- Malware distribution: Telegram can be used to distribute malware, such as trojans, keyloggers, and other types of malicious software. Hackers can create Telegram groups or channels and share links to malicious files, or use the app’s file-sharing feature to distribute malware directly.
- Hacktivism and cybercrime: Telegram groups and channels can be used to coordinate and organize hacktivist campaigns and cybercrime activities. Hackers can share information, tools, and techniques, and plan and carry out attacks.
How many channels exist and how can we keep track?
Telegram has over 500 million active users, and many of these users are likely to have created or joined channels. Telegram allows anyone to create a channel and there’s no limitation or verification process to it, so the number of channels on the platform is quite high. Additionally, many of these channels are likely to be inactive or used for legitimate purposes, so it’s difficult to estimate the number of channels that are specifically used for hacking or other illegal activities. We try to keep track of channels, but we will only cover a very small fraction of all channels.
How do we search forums?
Kaduu allows you to search the discussion history by comparing your keyword query with real accounts and presenting you the results in a downloadable format. We query around 200+ Telegram channels.
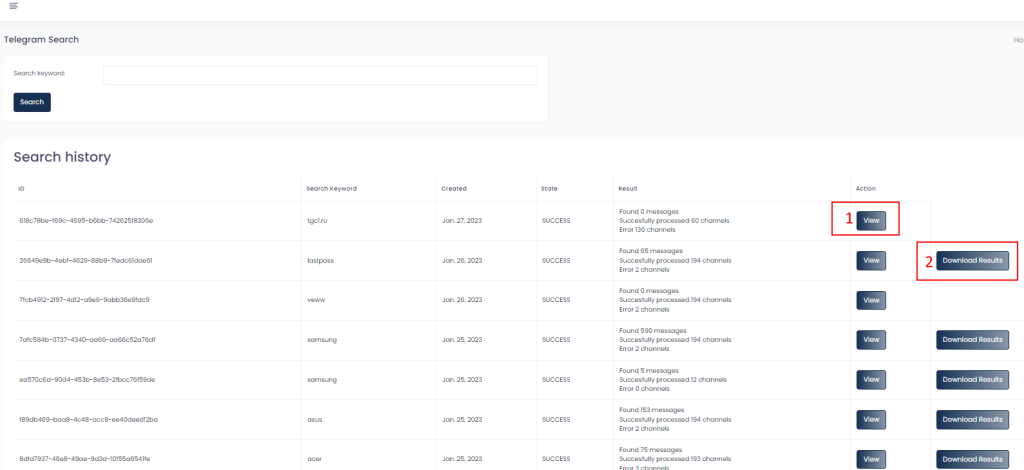
Are there any limitations?
To be able to do monitor Telegram, we use a variety of Telegram accounts. Because Telegram has security filters that block users how generate too many requests, we have to limit the number of requests to a maximum of 5 per customer per day. Please be aware that we query +200 channels at the same time.
Bucket and Cloud Storage Monitoring
AWS S3 is an object storage service in the Amazon cloud. S3 allows both users and applications to save and retrieve practically any type of data that can be stored in its digital form. S3 data is saved in buckets. These are containers of software in which data can be stored and retrieved on an as-needed basis. Many enterprises continue to leave cloud storage buckets unprotected, even though extensive documentation is available on how to properly secure these buckets. Recent studies (https://laminarsecurity.com/blog/new-research-finds-21-of-publicly-facing-cloud-storage-buckets-contain-sensitive-pii-data/) have shown that 1 in 5 publicly accessible buckets contained sensitive data (PII). In the past, many buckets have been widely exposed (https://github.com/nagwww/s3-leaks). In Kaduu, you can monitor S3 buckets, but also Azure cloud storage containers for sensitive data related to your keyword.
The main S3 security risks
Some of the most important S3 risks include:
- Configuration errors or failures that allow malicious users to access sensitive data in S3 buckets
- Lack of understanding of what data is stored in S3 buckets and if protection for that specific data is adequate
- Configuration problems that allow bad actors to upload malware to S3 buckets, and potentially create a baseline that they can use for further attacks
How to search and monitor cloud storage?
You can enter any keyword like “bank” or “bank switzerland” and Kaduu will monitor for the exact match in public cloud storage on a daily base. Your monitored keywords are displayed on the dashboard and result can be viewed by clicking the “view” button. We suggest using the company name rather than the domain (example instead of example.com). But if the company name is too generic, you might end up with more than 5000 results. This is the limit we display per keyword.
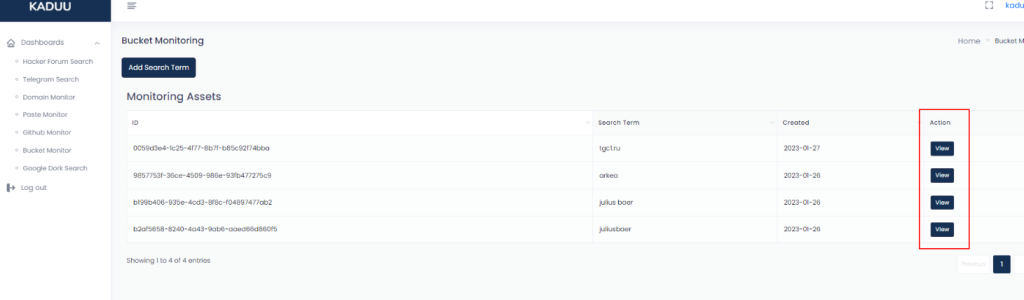
What data should you look for?
Basically any senstive data. Ususally only the own company knows best what is considered senstive according to the data classification. In general it can be said that sensitive data is any data that should not be accessible to unauthorized persons. Sensitive data may include personally identifiable information (PII), such as social security numbers, financial information, or login credentials. A sensitive data compromise occurs when an organization unknowingly discloses sensitive data or when a security incident results in the accidental or unlawful destruction, loss, alteration, or unauthorized disclosure of or access to sensitive data. Such data compromise may result from inadequate protection of a database, misconfigurations when setting up new instances of data storage, inappropriate use of data systems, etc.
Github Monitoring
GitHub is a web-based platform that is primarily used for version control and collaboration in software development. It is built on top of the Git version control system and offers a wide range of features to support software development teams.
Using GitHub for an organization can introduce a number of security risks, including:
- Data leakage: If an organization uses GitHub to store sensitive data, such as source code, login credentials, or customer data, there is a risk that this data may be accidentally leaked through a misconfigured repository or a compromised account.
- Insider threats: If an organization uses GitHub to collaborate on projects, there is a risk that an employee or contractor may intentionally or accidentally cause a data breach, for example by committing sensitive information to a public repository.
- Third-party risks: If an organization uses GitHub to collaborate with third-party vendors or open-source contributors, there is a risk that a malicious actor may use this access to gain unauthorized access to an organization’s data or systems.
- Malicious code injection: If an organization uses GitHub to manage their software development, there is a risk that a malicious actor may inject malicious code into the repository, which can then be executed on the organizations systems.
- Phishing and Social engineering: GitHub is a platform that is widely used for software development and many developers are active on it. Hackers may use phishing and social engineering tactics to gain access to organization’s sensitive information.
- Compromised dependencies: If an organization uses open-source libraries, they may be unknowingly importing a compromised dependency into their codebase.
How can you investigate the results?
Kaduu allows you to capture search terms and check their publication on publicly available Github repositories. If there is a match, we publish the result with the corresponding link. Kaduu connects to Github once per day for each keyword. After you entered the keyword, you should see some results under the “view” button. Please be patient, the search can take up to 2 hours.
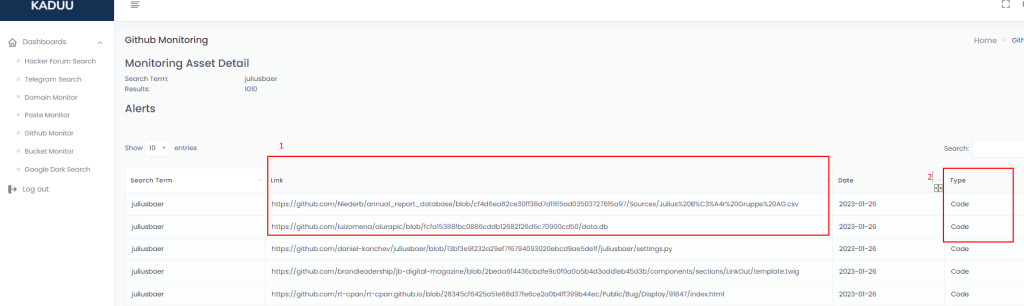
Google Dork Monitoring
Google hacking, also known as Google dorking, is the practice of using advanced operators in the Google search engine to find security vulnerabilities in websites. These operators can be used to search for specific file types, sensitive information, and other vulnerability-related information. It is often used by security researchers and hackers to find vulnerabilities in websites and networks. There are google Dork lists like https://www.exploit-db.com/google-hacking-database which can be used in combination with your domain. If any result appears in Kaduu, it means that there is a possible security vulnerability or data exposure in one of the webservices of your organisation.
What vulnerabilities can be exposed using google hacking?
Google hacking can be used to expose a variety of vulnerabilities in websites, including:
- Sensitive information: Google hacking can be used to search for sensitive information such as credit card numbers, social security numbers, and login credentials that may have been accidentally exposed on a website.
- Vulnerable files and directories: Advanced operators can be used to search for specific file types, such as .php or .asp, that may indicate a vulnerability in a website’s code.
- Misconfigured servers: Google hacking can be used to search for servers that have been misconfigured, such as those that have directory listing enabled, which can reveal sensitive information about the server and its contents.
- Backdoors: Google hacking can be used to search for backdoors, which are small programs that can be used to gain unauthorized access to a system.
- Open ports: Google hacking can be used to search for open ports on a network, which can indicate a vulnerability that can be exploited by attackers.
- Exposed databases: Google hacking can also be used to search for exposed databases, which can contain sensitive information such as customer data, financial information, etc
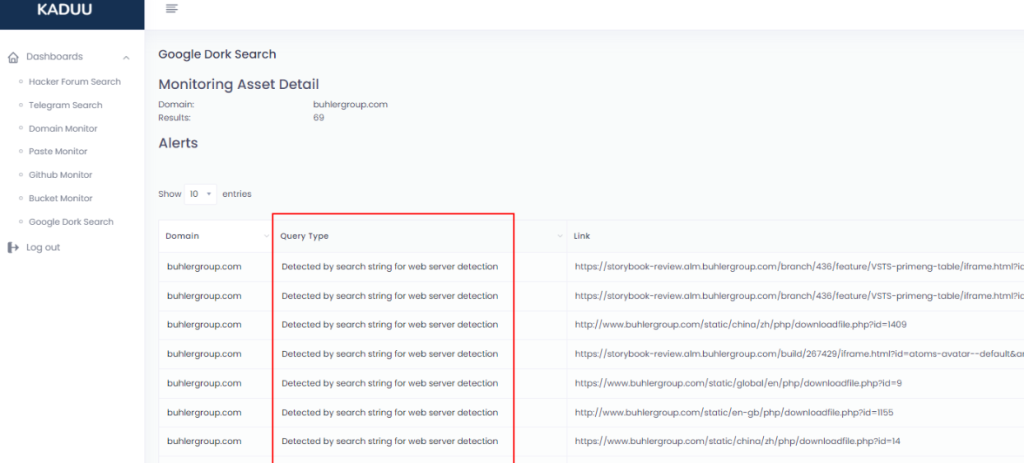
How to use Google Dork Monitoring?
Please enter you domain like “example.com” and not “www.example.com” to not limit the results to a specific server. The domain you enter will be queried once per day using a Google API call. If there are any results, you can see them by clicking on “view”. You will see all the alerts that have been triggered using your keyword. The query type will reveal what keyword has triggered the alert.
Leak and Account Trends Widget
Leak and account trends show how your company exposure is evolving over time. This feature works based on pre-configured alerts, so please make sure you have them set up.

Company Benchmark
Compare your company’s synthetic risk score against reference companies from Fortune 1000 and Forbes Global 2000. You can select any industry or country for comparison.

Reporting Engine with Customizable Docx Templates
Use customizable DOCX templates to automatically generate complex reports with lists, tables and any formatting you need.
Template language is based on Word Content Controls. It allows using conditional text blocks, lists, filters, etc.

Asset Management
Assets and asset groups help you to easily manage alerts for your infrastructure. You don’t need to create individual alerts anymore – just create assets of a desired type and they will be automatically converted to alerts with appropriate search syntax.

Alert Status Tracking
Now you can track whether triggered alerts have been submitted to your email address or webhook, and if not – see the error message.

Negative Sentiment Analysis for Social Networks

Every social network post gets a negativity sentiment score in percents, where 0% means a totally positive comment, and 100% means a note full of disappointment.
Active Domain Tracking
Get new domain notifications faster with “Active Domain” tracking. Just specify your main domain name as a keyword and get notified on new similar domains almost instantly. This tool was designed to overcome downsides of our domain feed providers.

New Domain Feed for CH and LI Zones
We are using a new additional domain feed for .ch and .li domains – https://www.switch.ch/de/open-data/
Phrase Search in Leaks

Use phrase search in leaks, containing 2-3 words. Previously our leak search had a flaw, that didn’t allow doing that.
Ransomware News Widget
Ransomware news widget to track all recent news from ransomware hacker groups.

New Botnet Logs: Redline, Taurus and Vidar
The new version of Kaduu supports 3 new botnet log providers. It will take some time to add new data, but we are already working on it.
Discover how CISOs, SOC teams, and risk leaders use our platform to detect leaks, monitor the dark web, and prevent account takeover.
🚀Explore use cases →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.
