ManoMano Data Breach: 6 Urgent Risks From an Alleged Leak

➤Summary
The ManoMano data breach has recently surfaced as an alleged leak on the underground forum BreachForums.bf, drawing attention from cybersecurity researchers and marketplace users across Europe. According to the post, authored by a threat actor known as Indra, the incident involves a massive dataset allegedly extracted from ManoMano’s customer support infrastructure, specifically Zendesk. The ManoMano data breach claim suggests exposure of internal ticket headers, email communications, attachments, and operational records tied to multiple European domains 🌍.
While ManoMano has not publicly confirmed the incident at the time of writing, the scale and structure of the leaked information raise serious concerns about customer privacy, internal workflows, and third-party integrations. This darknetsearch.com article breaks down the alleged ManoMano data breach, clearly explains what the exposed data headers contain, assesses the risks, and outlines what affected users and organizations should do next.
Alleged ManoMano Data Breach Overview
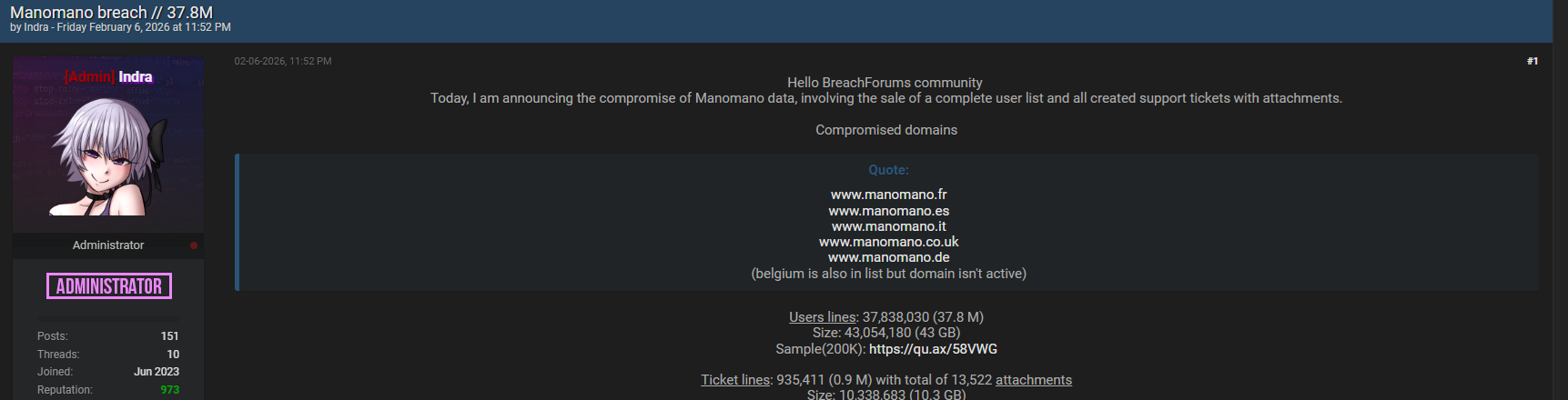
The alleged ManoMano database breach was published on BreachForums.bf, a well-known cybercrime forum frequently used to trade and publicize stolen data. The author claims the dataset originates from Zendesk, ManoMano’s customer support platform, and includes millions of records spanning several years.
Unlike typical credential dumps, this incident is centered on support ticket data, which can be just as sensitive. Support systems often store internal communications, customer email addresses, operational metadata, and file attachments. In the context of the ManoMano data breach, this transforms a customer service issue into a broader information security risk ⚠️.
Source of the Leak: BreachForums and Threat Actor Indra
BreachForums.bf has become a recurring source of alleged enterprise data leaks. The forum enables threat actors to publish samples, statistics, and affected domains to validate their claims. In this case, the threat actor Indra alleges access to tens of millions of records connected to ManoMano’s support operations.
Threat intelligence analysts often treat such claims cautiously. However, the inclusion of structured headers, timestamps, attachments, and marketplace-specific metadata gives the alleged ManoMano data breach a higher credibility profile than vague or unverifiable dumps.
What Are the Exposed Data Headers
The most important question is simple: what exactly do the leaked data headers contain?
According to the leak description, the alleged ManoMano data breach exposes Zendesk ticket headers, which are structured metadata fields attached to each support request. These headers reportedly include:
• Ticket ID and external reference numbers
• Creation and update timestamps
• Ticket type (incident, request, or inquiry)
• Subject and raw subject lines
• Sender and recipient email addresses
• Support agent names and internal roles
• Communication channels (email, web, API)
• Message routing metadata
• Attachment references and file identifiers
• Marketplace identifiers and operational tags
These headers do not merely label conversations—they map ManoMano’s internal support workflows. When combined with message bodies and attachments, they provide attackers with a detailed view of how the organization communicates internally and externally 📄.
Compromised Data Types Explained Clearly
Beyond headers, the alleged ManoMano data breach reportedly includes full ticket content. This means exposed data may consist of customer messages, internal agent replies, and forwarded emails involving third-party platforms. Attachments such as screenshots, invoices, product catalogs, or error logs may also be present.
Why does this matter? Support tickets often contain personally identifiable information, order references, and operational details that users would never expect to be publicly accessible. Even without passwords, this type of data can fuel targeted phishing, fraud, and impersonation campaigns.
Affected ManoMano Domains and Regional Impact
The dataset allegedly spans multiple ManoMano marketplaces, including:
• www.manomano.fr
• www.manomano.es
• www.manomano.it
• www.manomano.co.uk
• www.manomano.de
A Belgium marketplace reference is reportedly included, although the domain is inactive. This multi-domain exposure suggests centralized support infrastructure, meaning a single breach could affect customers and merchants across Europe 🇪🇺.
For users, this raises questions about cross-border data protection and GDPR compliance, especially if support communications contained personal or business-sensitive information.
Why Support Ticket Leaks Are High Risk
A common misconception is that only passwords and financial data matter. In reality, support systems are goldmines for attackers. The ManoMano data breach illustrates how operational data can be weaponized.
Attackers can analyze headers to identify escalation paths, trusted senders, and internal email patterns. This intelligence dramatically increases the success rate of social engineering attacks. A single leaked ticket can be used to craft convincing follow-ups that appear legitimate to both customers and employees 🧠.
Alleged Scale and Dataset Characteristics
According to the forum post, the dataset allegedly includes tens of millions of user-related lines and hundreds of thousands of tickets, with attachments totaling multiple gigabytes. A public sample link was reportedly shared to demonstrate authenticity.
Security researchers often use such samples to verify formatting consistency, timestamp logic, and domain references. When these elements align, the likelihood of the ManoMano data breach being real increases, even before official confirmation.
Is the ManoMano Data Breach Confirmed
At this stage, the ManoMano data breach remains alleged. No official statement confirming or denying the breach has been issued publicly. This is not unusual; investigations take time, especially when third-party platforms like Zendesk are involved.
Does “alleged” mean users should ignore it? No. History shows that many breaches initially dismissed later prove accurate. Caution and awareness are the safest responses.
Risks for Customers, Sellers, and Partners
If the claims are accurate, exposed parties may face:
• Targeted phishing using real ticket references
• Business email compromise attempts
• Fraud leveraging historical support conversations
• Reputation damage for affected sellers
• Competitive intelligence leakage
This is why proactive dark web monitoring is increasingly essential for marketplaces and large platforms.
Defensive Measures and Industry Context
Organizations now rely on a layered approach combining incident response, threat intelligence, and user awareness. Leveraging a single dark web solution allows teams to correlate forum leaks, validate samples, and assess exposure faster. Structured intelligence feeds supported by a curated dark web knowledgebase help analysts distinguish noise from credible threats.
In parallel, automated malware detection systems can flag weaponized attachments or malicious follow-ups linked to leaked support data 🔍.
Practical Checklist for Potentially Affected Users
If you have used ManoMano or sold products on its platforms, follow this checklist:
• Treat unexpected support emails with caution
• Verify references before responding
• Avoid opening old attachments resent via email
• Monitor accounts for unusual activity
• Stay informed via trusted sources like https://darknetsearch.com/
This simple process significantly reduces risk exposure.
Expert Perspective on Support System Breaches
A senior incident responder recently noted, “Support platforms are the nervous system of modern companies. When they leak, attackers gain context, not just data.” This insight perfectly captures why the ManoMano data breach allegations are being taken seriously within the cybersecurity community.
Broader Implications for Online Marketplaces
Marketplaces depend on trust. Incidents like the alleged ManoMano data breach highlight how third-party platforms can become single points of failure. As reported by reputable outlets such as https://www.reuters.com, support systems are increasingly targeted because they sit at the intersection of users, vendors, and internal teams 📊.
For companies, this means security assessments must extend beyond core infrastructure to include SaaS tools and vendor ecosystems.
Conclusion and Next Steps
The alleged ManoMano data breach underscores a critical lesson: data headers and support metadata are not harmless. When exposed, they can enable fraud, espionage, and long-term abuse. Whether or not the incident is ultimately confirmed, the risks are real and relevant to every digital marketplace.
Staying informed, verifying communications, and adopting proactive intelligence practices are no longer optional—they are essential.
Discover much more in our complete guide
Request a demo NOW
*Disclaimer: DarknetSearch reports on publicly available threat-intelligence sources. Inclusion of an organization in an article does not imply confirmed compromise. All claims are attributed to external sources unless explicitly verified.
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.

