Interrapidisimo Data Breach: 661K Records and 7 Facts

➤Summary
The Interrapidisimo data breach has surfaced as a major alleged cybersecurity incident affecting one of Colombia’s best-known logistics and courier companies. According to a post published by Typical_Idiot on breachforums.bf on 10 February 2026, an estimated 661,000 user records from Interrapidisimo.com were allegedly leaked and shared within underground communities. The Interrapidisimo data breach claim suggests that highly detailed internal user data was exposed, raising concerns about privacy, identity misuse, and corporate security practices.
While the breach has not yet been officially confirmed, early analysis indicates that the leaked database structure appears authentic and comprehensive. This alleged incident highlights the growing risks faced by logistics and transportation platforms as they digitize operations and manage large volumes of sensitive user and employee information 📦.
What Is Interrapidisimo and Why the Breach Matters
Interrapidisimo is a major Colombian logistics provider offering national shipping, express delivery, and business services. Millions of customers and internal users rely on its digital systems daily, which makes the Interrapidisimo data breach particularly significant. When a logistics company’s internal systems are compromised, the impact can extend beyond customers to employees, partners, and operational infrastructure. References indexed on dark web monitoring platforms show that logistics platforms have increasingly become targets due to their access to personal identifiers, contact details, and system credentials 🚚. The alleged Interrapidisimo leak underscores how attackers may view such companies as high-value data sources.
Alleged Interrapidisimo Data Breach Details
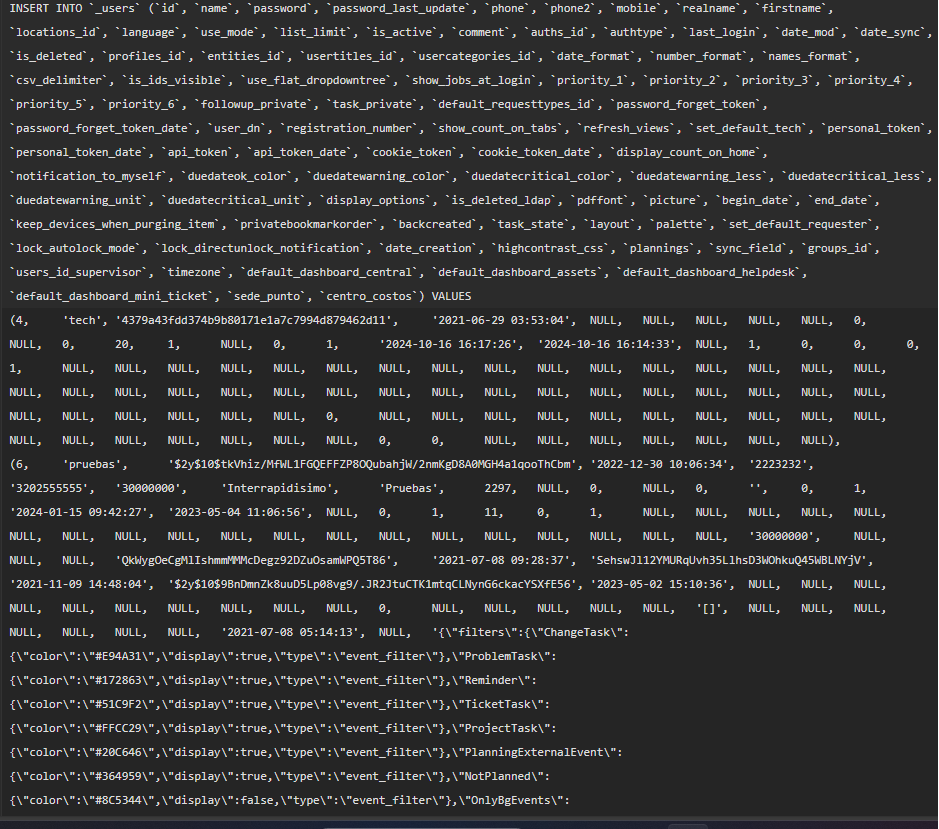
According to the breachforums.bf post, the Interrapidisimo data breach involves a database containing approximately 661K user records. The compromised table reportedly labeled _users includes a wide range of fields translated into English as follows:
- User ID, username, and real name details
- Encrypted passwords and last password update timestamps
- Phone numbers, mobile numbers, and secondary contact numbers
- First name, full name, language, and location identifiers
- Account status indicators such as active, deleted, or suspended
- Authentication types, roles, profiles, and entity identifiers
- Last login records and account modification dates
- Password reset tokens and API, cookie, and personal tokens
- System preferences, dashboards, layouts, and timezone settings
- Internal organizational fields such as cost center and branch location
This depth of information suggests that the Interrapidisimo data breach may expose not just customers, but internal staff and system users, increasing the overall risk profile ⚠️.
Types of Data Exposed and Sensitivity Levels
The sensitivity of the Interrapidisimo data breach lies in the combination of identity, authentication, and operational data. Even if passwords are hashed, the presence of password reset tokens and API credentials can significantly weaken account security. Phone numbers and real names enable targeted phishing and impersonation attacks. Internal role and entity identifiers could also help attackers map company structures and workflows. Analysts monitoring leaks via dark web monitoring platforms note that such datasets are often exploited gradually rather than immediately, making long-term monitoring essential 🔍.
Verification Status and Credibility Assessment
At the time of publication, the Interrapidisimo data breach remains classified as alleged. No official confirmation or denial has been issued by Interrapidisimo. However, historical trends show that many breaches first disclosed on forums like breachforums.bf are later validated. Security researchers recommend treating such incidents as credible until proven otherwise. An expert from Krebs on Security has previously stated that “the absence of immediate confirmation does not reduce the real-world risk to affected users.” This cautious approach is especially relevant when large datasets and internal system details are involved.
Risks for Affected Users and Organizations
The Interrapidisimo data breach presents several potential risks:
- Identity theft through exposed personal details
- Account takeover attempts using reset tokens or reused passwords
- Social engineering attacks targeting employees and customers
- Business email compromise leveraging internal role data
- Reputational damage and regulatory scrutiny for the organization
A common question is: Does this breach automatically mean fraud will occur? The answer is no, but it substantially increases the likelihood of abuse if users do not take preventive measures ❗.
Broader Impact on Colombia’s Cybersecurity Landscape
The Interrapidisimo data breach adds to a growing list of alleged incidents affecting Latin American companies. As digital transformation accelerates, organizations across the region are struggling to balance rapid deployment with robust security controls. Logistics companies are especially vulnerable due to their complex supply chains and distributed user bases. This incident may prompt renewed investment in malware detection systems and stricter access controls to prevent similar exposures in the future 📉.
Practical Checklist for Users and Businesses
If you believe your data may be connected to the Interrapidisimo data breach, consider this practical checklist:
- Change passwords associated with your Interrapidisimo account immediately
- Avoid clicking unsolicited messages referencing deliveries or account issues
- Monitor phone calls and SMS messages for social engineering attempts
- Use a trusted dark web search to identify potential data exposure
- Consider deploying a dark web monitoring platform for ongoing alerts
- Stay informed through intelligence resources like https://darknetsearch.com/
These steps help reduce risk even when breach details are still being verified ✅.
Industry Perspective and Expert Insight
Cybersecurity professionals emphasize that logistics platforms must adopt a “zero-trust” mindset. According to a recent analysis by Have I Been Pwned, organizations holding large identity datasets are frequent breach targets due to credential reuse and weak segmentation. The Interrapidisimo data breach aligns with this assessment, demonstrating how deeply interconnected systems can amplify the impact of a single compromise 🔐.
Conclusion: What Happens Next
The alleged Interrapidisimo data breach is a reminder that no sector is immune to large-scale data exposure. Whether fully confirmed or not, the claims highlight the importance of transparency, rapid response, and proactive user protection. Individuals should remain vigilant, while organizations must reassess security postures and incident response strategies. Staying ahead of emerging threats requires continuous awareness, monitoring, and education. Discover much more in our complete guide and Request a demo NOW 🚀
*Disclaimer: DarknetSearch reports on publicly available threat-intelligence sources. Inclusion of an organization in an article does not imply confirmed compromise. All claims are attributed to external sources unless explicitly verified.
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


