From Ransomware to Extortion-as-a-Service

➤Summary
Hunters International emerged in October 2023, likely as a rebrand of the Hive ransomware group, following the latter’s dismantling by law enforcement. Initially operating as a Ransomware-as-a-Service (RaaS) with support for data encryption and exfiltration, Hunters International soon evolved its strategy in response to global crackdowns, sanctions, and anti-ransom legislation. By early 2025, the group rebranded again as World Leaks, dropping encryption entirely to focus on pure extortion using advanced data exfiltration tooling and social pressure techniques.
Origins and Infrastructure
First confirmed attack on a UK company: October 13, 2023. Malware sample uploaded to VirusTotal: October 19, 2023, from a German IP. Affiliate panel note in Russian posted: October 21, 2023. Likely based on the Hive source code, acquired post-shutdown. The group’s infrastructure mimics other ransomware platforms (e.g., LockBit, Qilin), but with notable innovations like modular tooling, categorized disclosure, live chat support, and SOCKS5/Tor-based C2 channels.
Targeting and Operations
Main targets: North America, Europe, Asia. Exclusions (claimed): CIS, Israel, Turkey, Far East. Reality: Leaks from China, Japan, and Turkey contradict exclusions
Victim Industries: Healthcare. Real Estate, Professional Services. Here is the complete victim list:
| Company | Country | Industry |
| Lake Region Healthcare | USA | Healthcare & Research |
| Center for Clinical Research | USA | Healthcare & Research |
| Freedman HealthCare | USA | Healthcare & Research |
| ASC Machine Tools | USA | Manufacturing / Industrial |
| Sylvania | USA | Manufacturing / Industrial |
| Valiant Energy Solutions | USA | Manufacturing / Industrial |
| ASCOMA Cameroon | Cameroon | Manufacturing / Industrial |
| A&R Engineering | USA | Manufacturing / Industrial |
| Zeus TecnologÃa | Mexico | Technology & IT |
| Indigo Group S.A. | Uruguay | Technology & IT |
| Brett-Robinson | USA | Real Estate / Construction |
| A M King | USA | Real Estate / Construction |
| Chain IQ | Switzerland | Real Estate / Construction |
| Kel Campbell | Australia | Transportation & Logistics |
| Canadian Rocky Mountain Resorts | Canada | Hospitality & Retail |
| Jardin De Ville | Canada | Hospitality & Retail |
| AntiFarm | India | Consulting / Services |
| Horecamaterialen De Meester NV | Belgium | Consulting / Services |
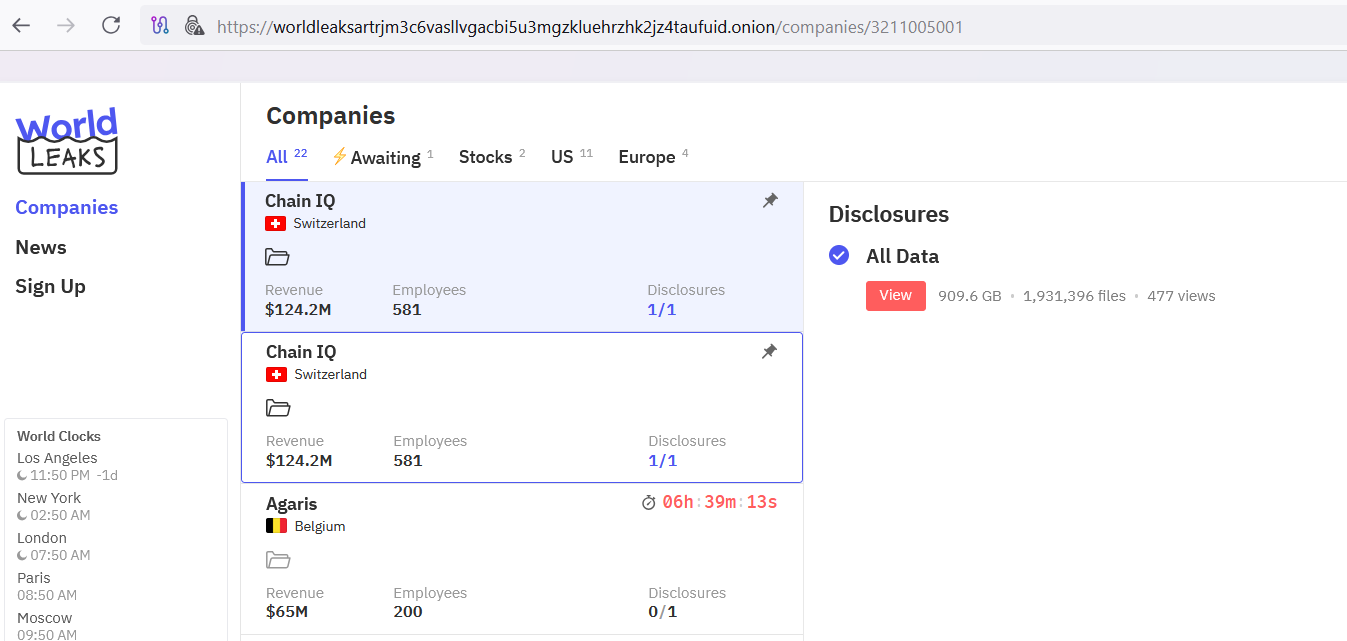
Latest victim: Chain IQ in Switzerland: Nearly 1 Million Files Exposed in Ransomware-Free Extortion Campaign
Chain IQ is a global strategic procurement services provider headquartered in Switzerland, with a reported revenue of $124.2 million and a workforce of 581 employees. The company manages indirect procurement processes for major international corporations, making it a prime target for attackers looking to exploit confidential supply chain, financial, and client relationship data.
What Was Leaked?
According to the disclosure on the World Leaks extortion platform, the entire dataset has been made available for download. The exposed materials span hundreds of directories and nearly 2 million files.
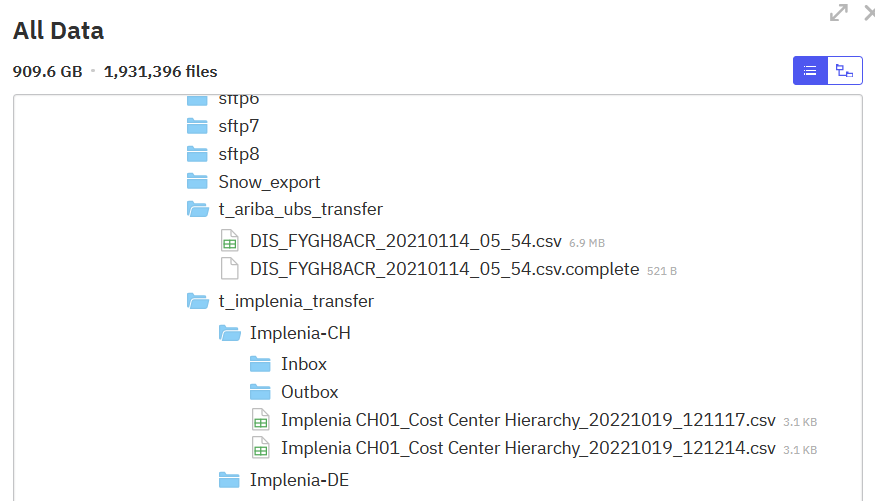
Among them:
Sample Exposed Files:
- Procurement & Transfer Data
- t_ariba_ubs_transfer/DIS_FYGH8ACR_20210114_05_54.csv — 6.9 MB
- t_implenia_transfer/Implenia CH01_Cost Center Hierarchy_20221019_121117.csv
- Sensitive Financial Records
- VRecovery_Bell Partners_20240215.xlsx — Includes payment details to vendors like Pax8, Inc., Ferguson Enterprises, and Belfor Property Restoration.
- Fields include: account numbers, vendor names, bank transaction data, invoice numbers, and US$ amounts exceeding $150,000.
- Employee and User Directory Data
- CIQ_USER_20180814_221502 — A large dump of employee details including full names, email addresses, cities, and international phone numbers (US and UK). Some entries mention “Remote User” and LinkedIn-style executive data (e.g., C-level emails).
- Other Files and Metadata
- suppliers.xml, users.xml, .xslt, .complete flags suggest system exports from enterprise procurement or HR systems.
- File formats include .csv, .xlsx, .xml, .xslt, and even .sql and .py, hinting at exposed source or config files.
Ransomware Capabilities of Hunters International
Hunters International developed a robust, cross-platform ransomware suite capable of infecting a wide range of environments. This technical versatility allowed affiliates to launch attacks against both standard desktop systems and enterprise infrastructure.
Supported Architectures and Operating Systems
The ransomware was engineered to run on multiple CPU architectures and operating systems, making it highly adaptable across various target environments:
- Windows: Supports both 32-bit (x86) and 64-bit (x64) systems. Distributed in executable (.exe) and dynamic-link library (.dll) formats.
- Linux: Compatible with x86, x64, and ARM architectures, allowing deployment on traditional servers, embedded devices, and modern cloud workloads.
- FreeBSD and SunOS: Lesser-used UNIX-like systems, often found in legacy enterprise environments.
- VMware ESXi: Targets virtualization infrastructure, specifically the hypervisor used in many data centers. Attacks here can affect multiple virtual machines simultaneously.
This breadth of support highlights the group’s strategic intent to compromise heterogeneous IT infrastructures, including core servers, virtualized environments, and endpoint systems.
Encryption Behavior and Stealth Enhancements
The ransomware used AES (Advanced Encryption Standard) with a unique 128-bit key per file, a common yet effective method to ensure file contents are irreversibly locked without the decryption key.
Several key features define its encryption strategy:
- Partial File Encryption Avoidance: The first 0x41 bytes (65 bytes) of each file are left untouched. This technique minimizes the risk of corrupting file headers, which could trigger alarms from antivirus systems.
- No File Renaming or Ransom Notes (as of version 6): Traditional ransomware adds file extensions (e.g., .locked) or drops ransom notes to notify the victim. Hunters International avoids both, making it harder for defenders to detect the attack early.
- Recovery Inhibition: The malware deletes Windows Shadow Copies and disables system recovery tools to prevent victims from restoring lost data without paying the ransom.
This minimalist and covert encryption approach reflects a trend among modern ransomware groups: stealth over spectacle.
Additional Features and Execution Techniques
Hunters International’s ransomware includes several command-line interface (CLI) options, enabling granular control over the attack:
- Custom Targeting: Operators can specify exactly which files, folders, or network shares to encrypt.
- Delayed Execution: A configurable sleep timer allows the malware to delay its start, evading sandbox detection tools that analyze behavior shortly after execution.
- Process and Service Termination: Affiliates can define lists of processes or services to terminate (e.g., database engines or backup agents) to maximize data inaccessibility.
- Disk Wiping and Network Share Enumeration: Optional wiping of free disk space prevents forensic recovery; the ransomware also identifies and encrypts shared drives on the network.
- DLL Execution via regsvr32.exe: This Windows binary is often abused in malware delivery to execute code without dropping suspicious executables — a technique catalogued in MITRE ATT&CK as T1218.010 (System Binary Proxy Execution).
- Automatic Partition Mounting (from v5.1 onward): Enhances reach by encrypting data stored on unmounted volumes that otherwise wouldn’t be affected.
Storage Software: Hunters’ Data Management Tool
One of the group’s most novel features was its “Storage Software” — a post-exfiltration utility used by affiliates to organize and manage stolen data.
Functionality Overview
The Storage Software enables attackers to:
- Categorize exfiltrated files into logical groups (e.g., Personally Identifiable Information, Source Code, Financial Records), making them easier to weaponize during extortion.
- Configure real-time leak previews in the affiliate panel. Threat actors can create customized “disclosure folders” visible to victims.
- Grant victims access to view, download, or delete their stolen data via the “victim panel.” This controlled release is designed to increase psychological pressure.
- Retain physical custody of stolen files on the attacker’s own server, not Hunters’ infrastructure. This decentralization mitigates the risk of group-wide takedowns and builds trust with affiliates who fear exit scams.
Communication Architecture
The Storage Software communicates securely with the Hunters platform through:
- Tor (The Onion Router) SOCKS5 proxy: Provides anonymity and resilience against takedown attempts.
- TLS-encrypted metadata transmission: Only metadata (not file contents) is sent to Hunters’ system. This includes filenames, sizes, and categories.
- The tool must remain actively running on the attacker’s host to serve data to the victim or allow deletions.
This architecture ensures the attackers maintain tight operational control, while avoiding the risks associated with centralized data warehousing.
The Affiliate Workflow: A Business-Driven Ransom Model
Hunters International operated with the efficiency of a software-as-a-service (SaaS) business. The affiliate workflow followed a clear, repeatable structure:
- Target Registration: The affiliate logs into the panel and registers a victim, providing metadata such as company name, sector, revenue, and stock exchange listings.
- Tool Provisioning: Upon registration, the affiliate receives a customized ransomware payload, a copy of the Storage Software, and victim panel credentials.
- Attack Execution: Affiliates carry out data theft and optionally encrypt systems.
- Disclosure Preparation: Using the admin panel, attackers configure what data is shown to the victim — often with tiered access (e.g., preview vs. full disclosure).
- Negotiation and Payment: The victim interacts with the affiliate or automation via a live chat interface. Affiliates receive up to 80% of ransom payments.
This approach demonstrates a mature criminal business model, prioritizing scalability, modularity, and incentives for affiliate loyalty.
OSINT-Enhanced Extortion
In a bid to increase pressure without triggering law enforcement, Hunters International began using Open Source Intelligence (OSINT) for non-technical extortion tactics.
Strategy
- Third-party OSINT partners collect information on corporate executives, key employees, and their families.
- This data is weaponized through direct threats:
- Phone calls
- Personalized emails
- Harassment via social media
By focusing attacks directly on decision-makers, Hunters International maximized psychological leverage while minimizing visibility — particularly important given that public ransom notes and leaks often trigger compliance and regulatory alerts, which can reduce the chances of payment.
This OSINT-driven model is expected to replace traditional ransom note strategies, aligning with a broader shift toward stealth-focused extortion campaigns.
Discover how CISOs, SOC teams, and risk leaders use our platform to detect leaks, monitor the dark web, and prevent account takeover.
🚀Explore use cases →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.



