Flower shop data breach 9 Websites Breached: Shoppigmint, Ctlflorist and More

➤Summary
Flower shop data breach incidents are becoming increasingly frequent, but the latest exposure reported on Breachforums.bf on January 29, 2026, has shocked both customers and business owners alike. This incident involved multiple floral and flower shop websites, compromising sensitive personal and transactional data belonging to thousands of individuals. The breach, allegedly published by an actor known as “888,” revealed a wide range of customer information, including full names, addresses, email addresses, phone numbers, and detailed order histories. With cybercriminals intensifying their operations, this event underscores the urgent need for vigilance, proactive cybersecurity strategies, and continuous awareness. In this in-depth report, we examine what happened, which websites were affected, what data was exposed, and what businesses and customers should do next to minimize risk and prevent future incidents. 🌐
Affected Websites and Scope of the Incident
The following websites were listed as impacted in the forum disclosure:
- Shoppigmint.com
- MyJoyFlowerShop.com
- LakesFloral.com
- CentralMarketFlowers.com
- ArtAmongTheFlowers.com
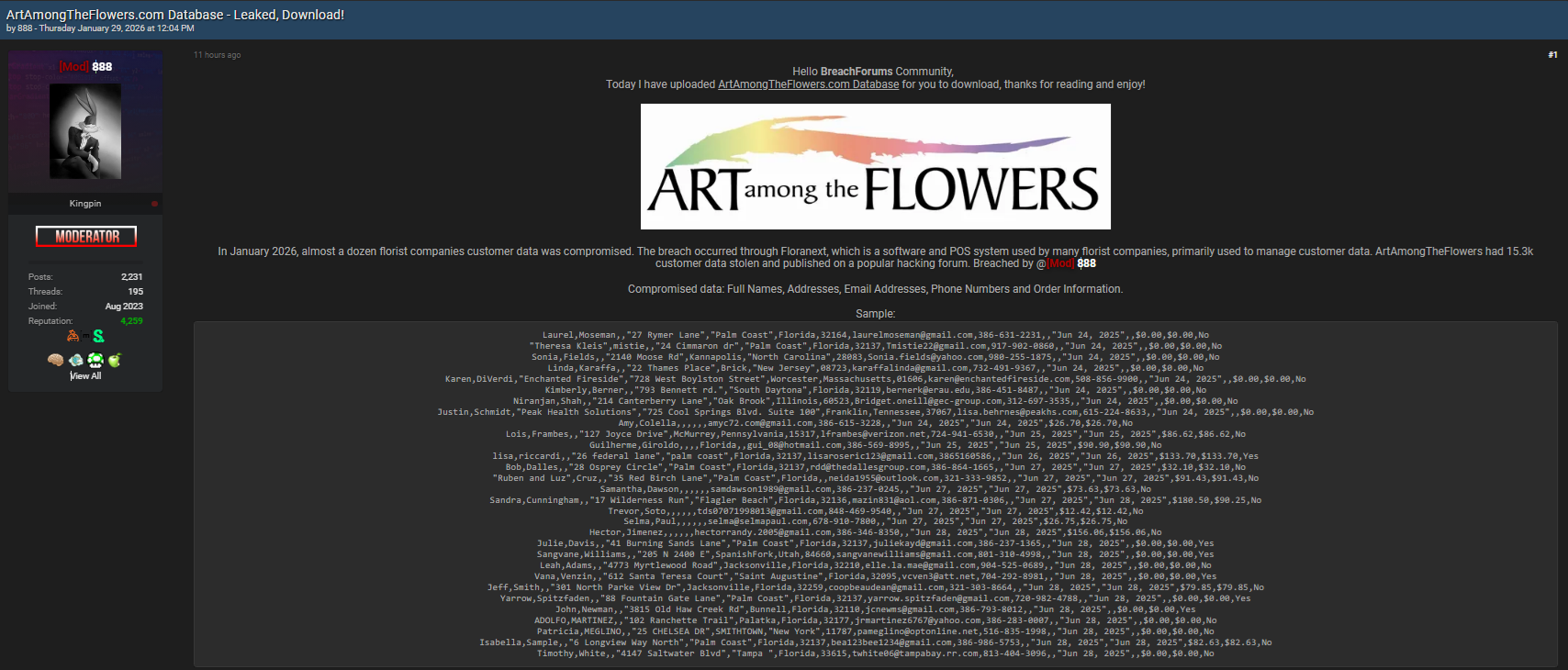
- TheCottageFlowersAndGifts.com
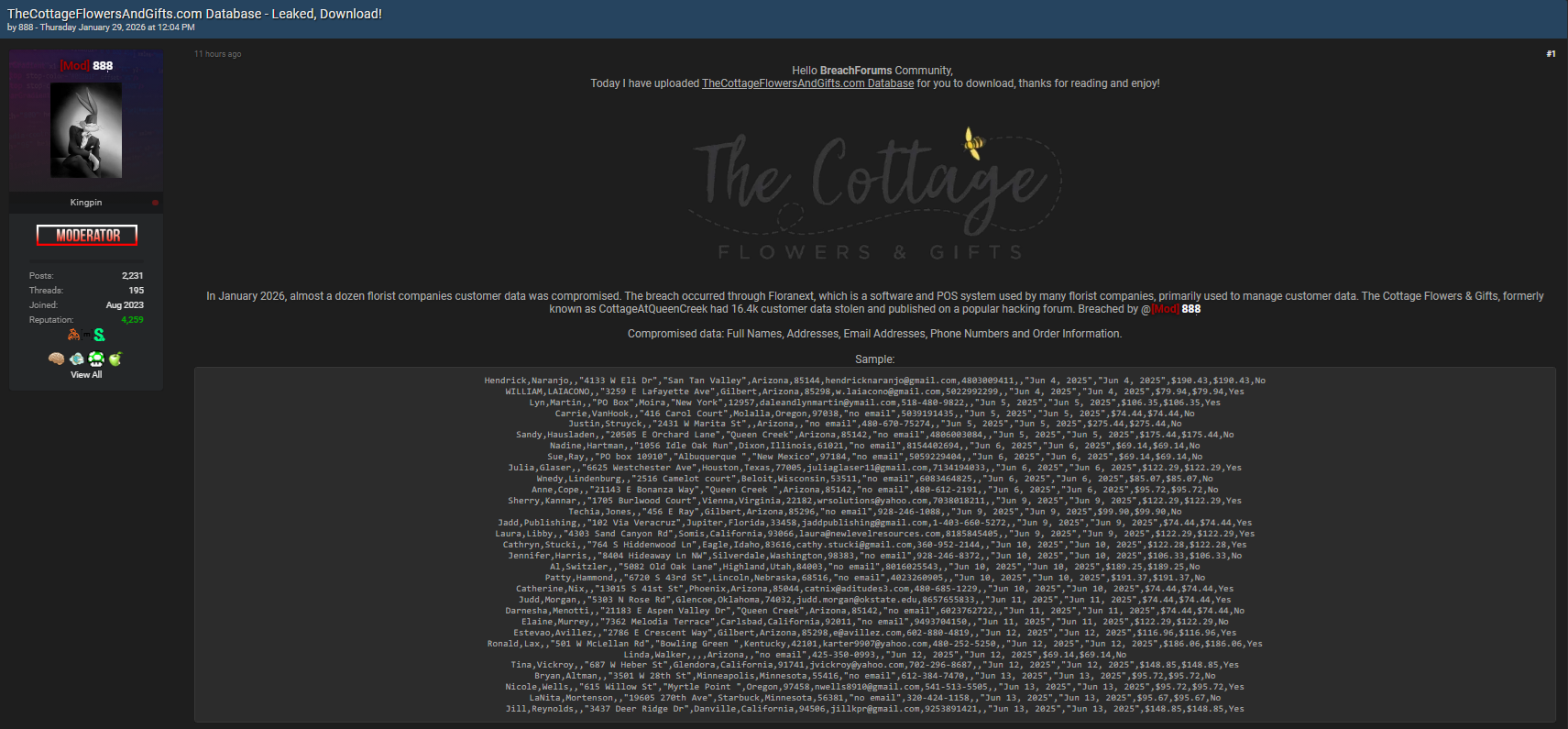
- CreationStationFlowers.com
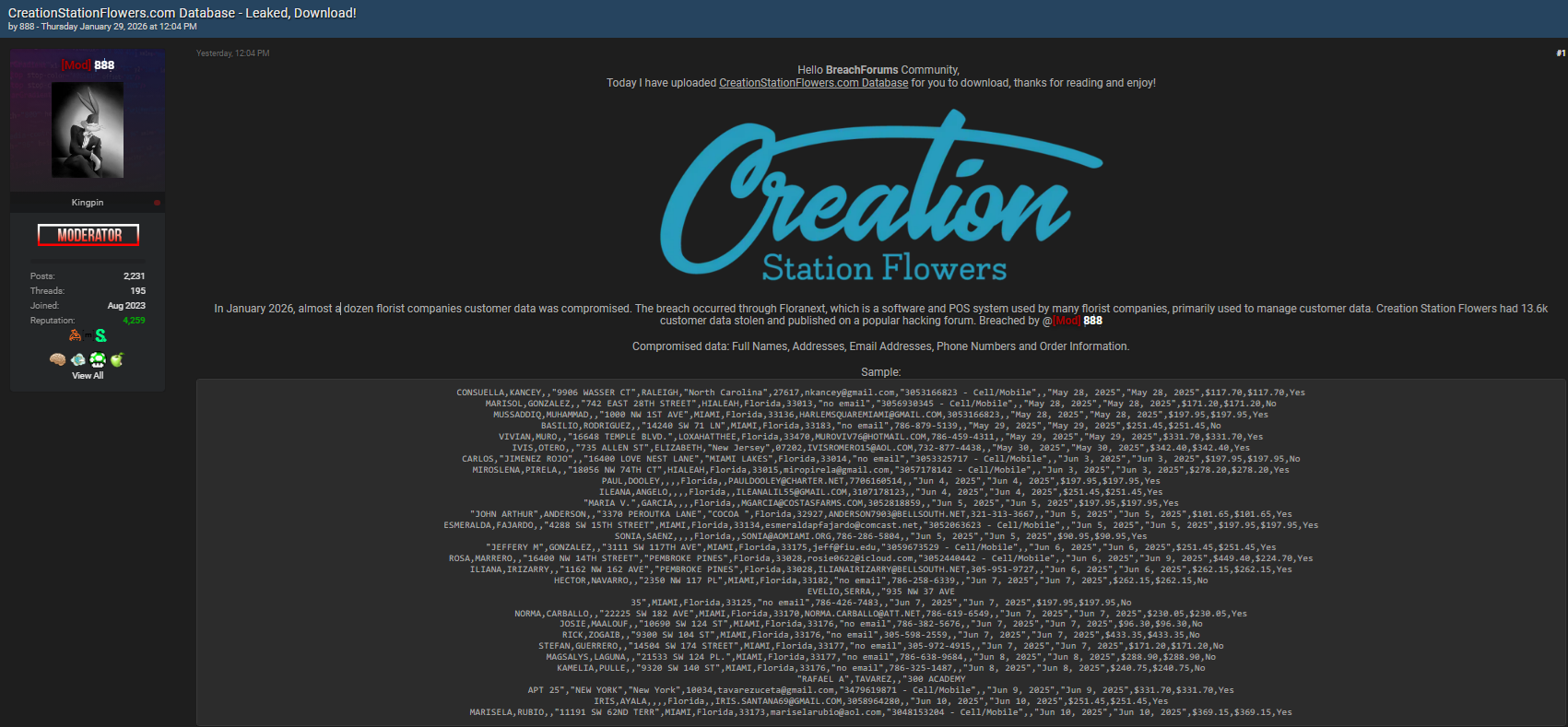
- Ctlflorist.com
- Texas-Blooms.com
This flower shop data breach spans a diverse group of businesses, from boutique floral designers to larger e-commerce flower delivery platforms. The exposure of personally identifiable information (PII) and order records significantly raises the risk of phishing, identity theft, and targeted scams. According to cybersecurity analysts, attacks on small and medium-sized enterprises (SMEs) are increasing because they often lack advanced security infrastructures, making them more vulnerable than large corporations. 🚨
What Data Was Compromised and Why It Matters
The compromised data reportedly includes:
- Full names
- Residential addresses
- Email addresses
- Phone numbers
- Order information and purchase history
This combination of data is particularly dangerous because it enables highly convincing social engineering attacks. For instance, a cybercriminal could craft personalized phishing emails referencing real past purchases, increasing the likelihood that recipients will trust the message and click malicious links. The flower shop data breach thus goes beyond a simple leak; it creates long-term risks for both customers and businesses.
Timeline of the Breach
- January 29, 2026: Data published on Breachforums.bf
- Author: 888
- Scope: Multiple floral and flower shop websites
The relatively quick publication of the stolen data suggests that attackers may have exploited vulnerabilities in shared hosting environments or outdated plugins. Continuous monitoring and regular system audits could have reduced the attack surface and possibly prevented the incident.
Why Are Flower Shops Increasingly Targeted?
Cybercriminals often target industries that collect personal and payment-related data but operate with limited cybersecurity budgets. Flower shops, especially those operating online, fall into this category. They handle sensitive customer information daily, particularly during high-demand periods like Valentine’s Day, Mother’s Day, and major holidays. This makes them lucrative targets. The rise in such attacks emphasizes the need for advanced data breach detection methods, coupled with proactive threat intelligence. 🌍
How the Dark Web Fuels Data Trading
Stolen data often ends up on underground marketplaces, where it is sold to the highest bidder. These platforms enable criminals to monetize breaches quickly. While many organizations rely on perimeter security, fewer invest in active threat intelligence gathering. Implementing a comprehensive dark web monitoring solution can help organizations detect leaked data early, enabling faster response and damage control.
For deeper insights into how cybercriminal marketplaces operate, readers can explore resources available at https://darknetsearch.com/, which regularly analyzes emerging threats and underground trends. This internal resource provides actionable intelligence on leaked credentials, malware campaigns, and breach disclosures. 🔍
Impact on Customers and Businesses
The consequences of a flower shop data breach extend far beyond immediate financial losses. Customers may experience:
- Identity theft
- Phishing and scam attempts
- Unauthorized account access
- Emotional distress due to privacy violations
Businesses, on the other hand, face:
- Reputational damage
- Loss of customer trust
- Regulatory penalties
- Legal liabilities
According to the U.S. Cybersecurity and Infrastructure Security Agency (CISA), maintaining robust incident response protocols and transparency with customers significantly reduces long-term brand damage.
One Critical Question: Can Breaches Like This Be Prevented?
Yes, while no system is entirely immune, most breaches can be prevented or mitigated through layered security strategies, regular updates, and employee training. Implementing continuous brand protection practices and proactive monitoring significantly reduces the risk of successful attacks.
Practical Tip: Security Checklist for Flower Shop Owners
Here is a simple yet effective checklist to enhance cybersecurity resilience:
- Update all website plugins, themes, and CMS platforms weekly.
- Enforce strong password policies and two-factor authentication.
- Conduct quarterly vulnerability assessments.
- Encrypt customer databases and backups.
- Monitor online forums and underground markets for leaked data.
- Train staff to recognize phishing and social engineering tactics.
Following this checklist not only minimizes exposure but also strengthens customer trust and operational continuity. 🌱
How This Incident Fits into a Larger Trend
The January 2026 disclosure aligns with a broader pattern of attacks against e-commerce platforms. As online transactions increase, cybercriminals are shifting focus toward smaller operators that may lack enterprise-grade security. This flower shop data breach is a clear example of how attackers exploit digital transformation gaps. Experts predict that unless SMEs adopt proactive monitoring and automated security tools, similar incidents will continue to rise.
Role of Proactive Monitoring and Intelligence
Proactive strategies such as dark web monitoring enable early detection of leaked credentials and stolen datasets before they spread widely. When combined with internal tools like darknetsearch.com, businesses gain valuable insights into emerging risks, enabling swift countermeasures. Intelligence-driven security is no longer optional; it is essential.
Lessons Learned from the Breach
Key takeaways include:
- Regular audits prevent vulnerabilities from persisting unnoticed.
- Employee awareness reduces human error.
- Incident response plans limit damage.
- Transparent communication preserves customer trust.
Incorporating these lessons into daily operations transforms cybersecurity from a reactive measure into a strategic advantage.
Future Outlook for Floral E-Commerce Security
As digital adoption accelerates, floral businesses must evolve their security frameworks. Investing in cloud-based protections, AI-driven anomaly detection, and continuous monitoring will become standard practice. The flower shop data breach of January 2026 serves as a pivotal reminder that cybersecurity maturity is directly linked to business sustainability. 🌸
Conclusion: Protecting Trust in a Digital World
The January 2026 flower shop data breach underscores the growing threat landscape facing small and medium-sized e-commerce businesses. With sensitive customer information exposed across multiple platforms, the need for proactive defense, education, and intelligence has never been greater. By embracing advanced security practices, monitoring emerging threats, and prioritizing customer trust, businesses can navigate this evolving environment with confidence. For deeper insights, expert analysis, and ongoing updates, explore https://darknetsearch.com/ and stay informed.
Discover much more in our complete guide
Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


