Exploring PHI (Medical Records) Sales and Cost Structures in the Darknet
➤Summary
This chapter focuses on the various types of medical data that are found on the darknet. The illicit sale of this data highlights significant risks to patient privacy and the integrity of medical institutions. Lets first explore the value of medical records.
What is the price for PHI (medical records) on the darknet?
The price of medical data on the black market can vary widely and depends on several factors. Here are some general insights into what influences the pricing:
- Type and Completeness of Data: Comprehensive records that include full names, dates of birth, Social Security numbers, addresses, medical histories, and insurance information are more valuable than partial records. The inclusion of financial information, like credit card or bank details, can also increase the price.
- Currentness of the Data: More recent data is typically more valuable because it’s more likely to be accurate and useful for fraudulent activities.
- Volume of Data: Larger datasets can be more expensive, especially if they contain high-quality, comprehensive records.
- Specificity of Medical Information: Data pertaining to certain medical conditions or treatments can be more valuable, especially if it’s of interest for targeted scams, pharmaceutical marketing, or research.
- Targeted vs. General Data: Data targeting specific individuals (like celebrities, public figures, or wealthy individuals) can be more valuable due to its potential for blackmail or high-value identity theft.
- Source and Reliability: Data obtained from reputable or large healthcare institutions, or data that’s verifiably accurate, may command higher prices.
As for the price range, it can vary from a few dollars for a single record to thousands for extensive datasets. However, these figures fluctuate based on the market, the risk involved, and the factors mentioned above. Since the pice depends on the type of data, we will explore in the next chapter different PHI data types you will find on the darkweb.
What PHI Datasets will you find in the darknet?
1. Single Patient Records
Description: Individual patient records contain comprehensive personal health information (PHI). This can include a patient’s full name, date of birth, social security number, medical history, diagnostic information, treatment plans, prescription details, and insurance information.
Sources: These records are often obtained through data breaches in medical facilities, unauthorized access by healthcare personnel, or through phishing attacks targeting patients.
Usage: Such detailed information is valuable for identity theft, medical fraud, and can even be used for blackmail or personal attacks.
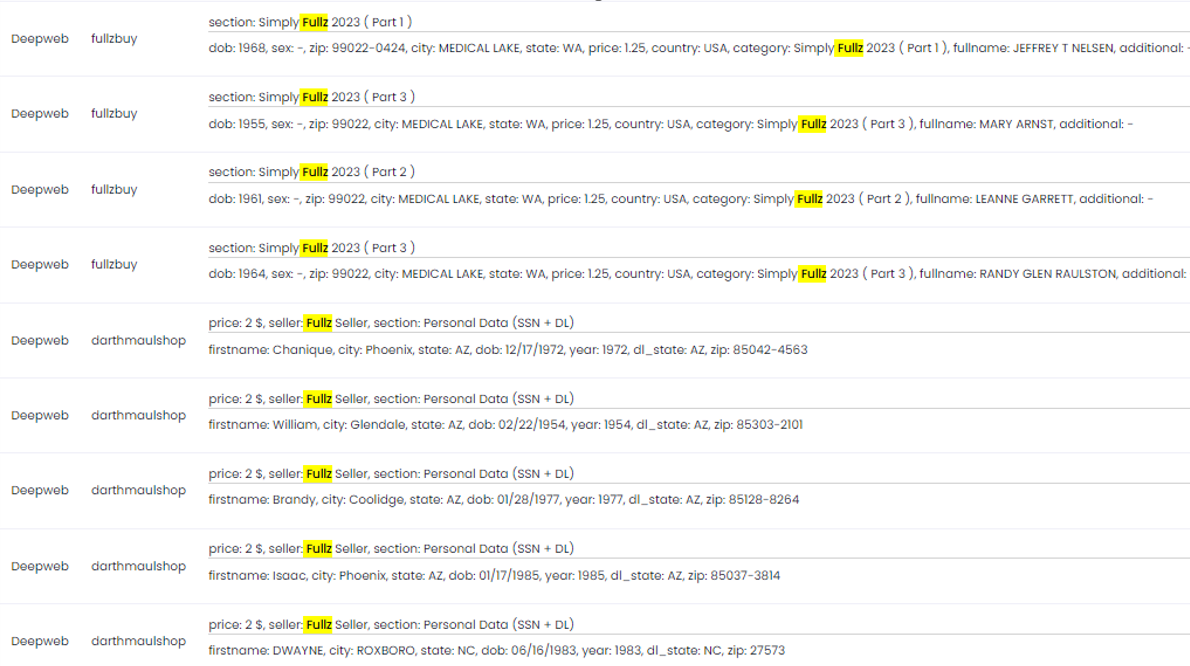
Prices and Examples: Fullz ( “full information packages”) are sets of personal data sold by criminals on the dark web. They usually also contain PII and sometimes also medical records. The price starts around 1 USD. Below is an extract of Shop offers that are displayed with Kaduu.io:
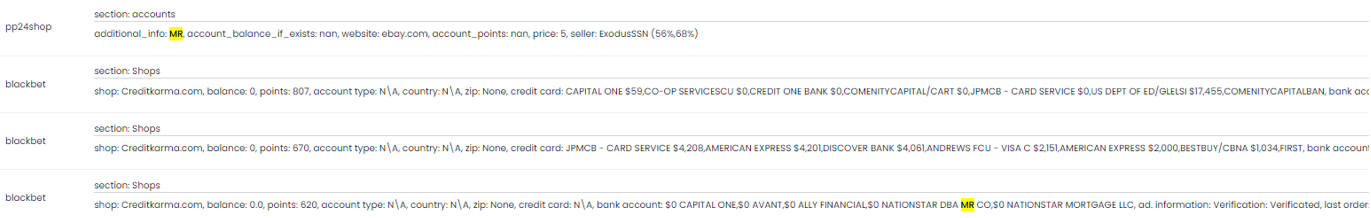
In some cases hackers use the shortcut MR which stands for “medical record”
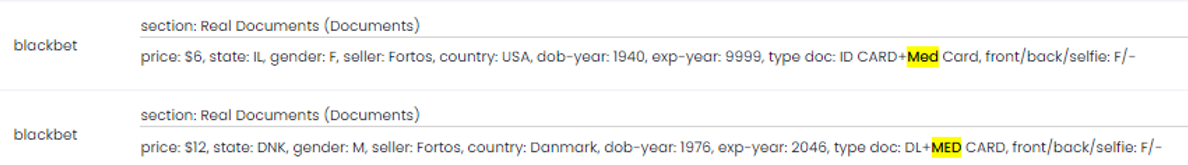
Medical data can be also obtained from physical documents like a “med card”. Starting price is USD 5.
2. Whole Databases
Description: Entire databases from hospitals, clinics, or insurance companies are occasionally found for sale. These databases can include information on thousands or even millions of patients, encompassing all the data points found in single patient records, aggregated over a larger scale.
Acquisition: Large-scale data breaches are the primary source, involving sophisticated cyberattacks on vulnerable healthcare IT systems.
Implications: The sale of such databases poses a massive risk, as it exposes sensitive information of a large population, leading to widespread privacy violations and potential healthcare fraud on a massive scale.
Pricing: The price depends on the size and relevance. In some cases prices need to be negotiated, in other cases the price is visible in the forum.
Example: Fixed Price. Below is an example of a DB Kaduu discovered November 20th 2023
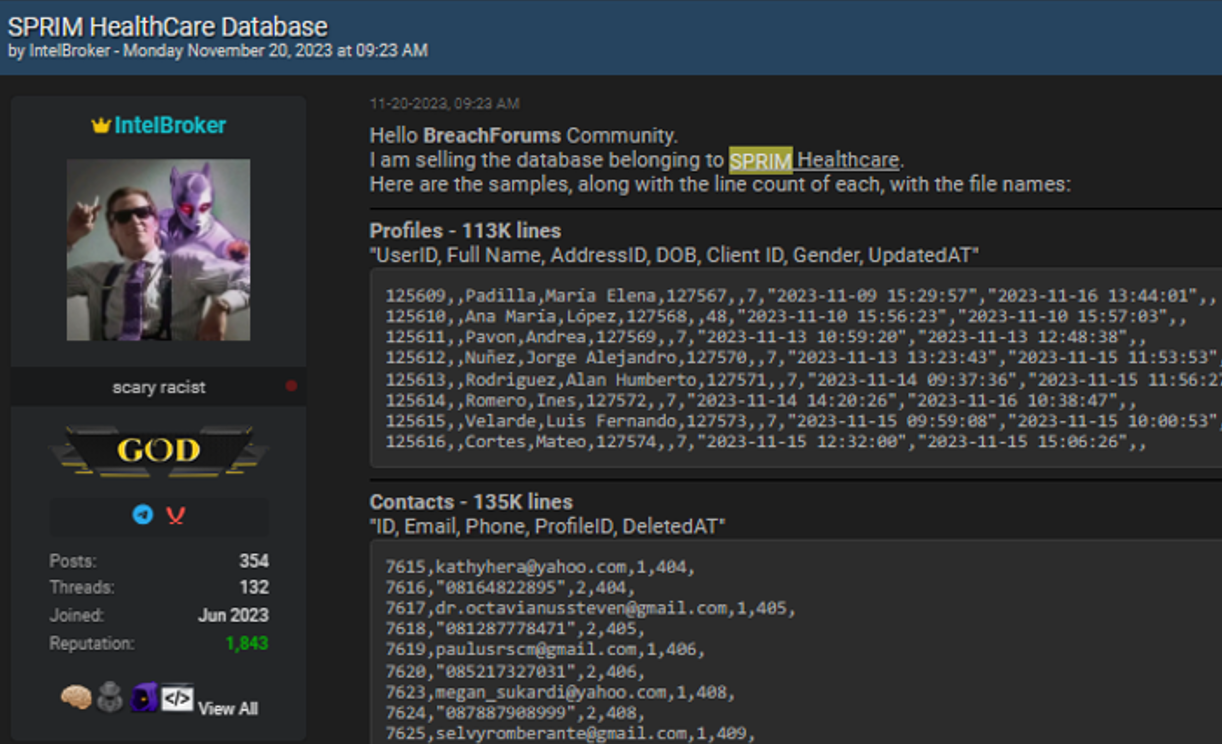
It consists of:
- 113 K Lines of Profiles (Gender, Address etc)
- 135 K lines of Contacts (Email, Phone etc)
- 10 K Lines of Notifications (Message etc)
- 2.7 K Lines of Patients (Name, Age, Address, Type etc)
- 1.1 K Lines of Partners (Email, Passwords etc)
The sales price is 1000 XMR which is roughly 150 USD.
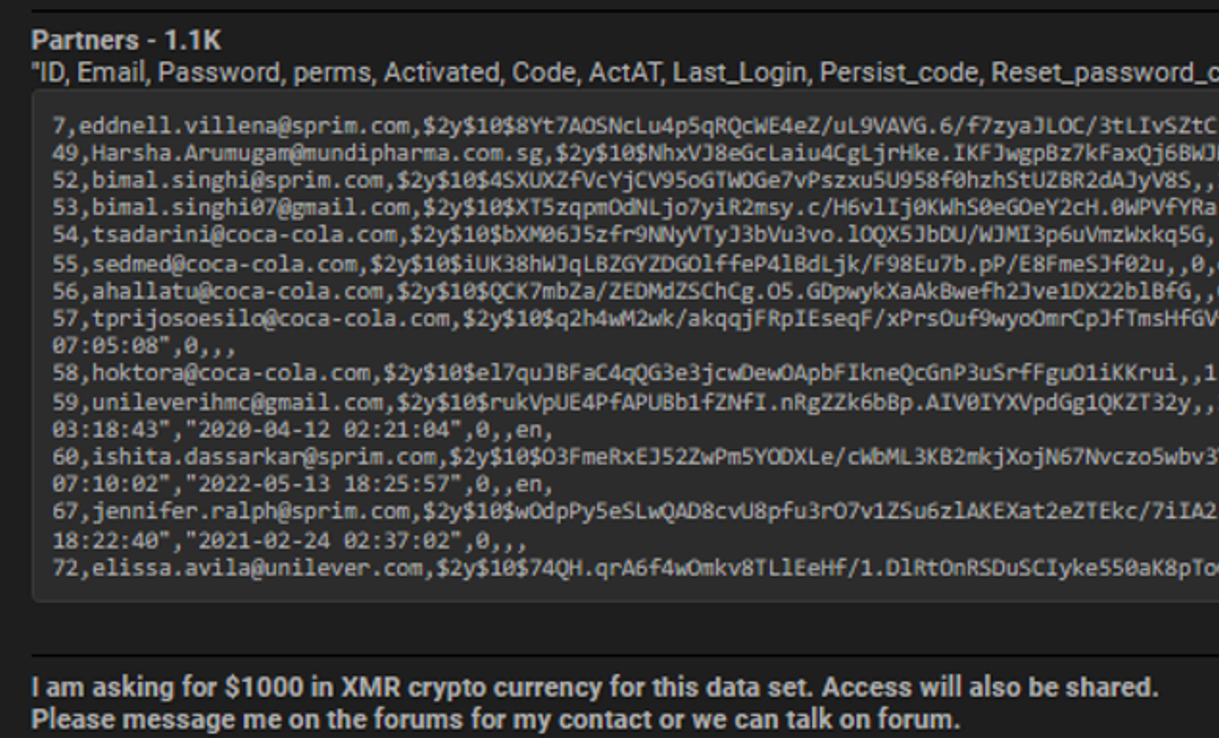
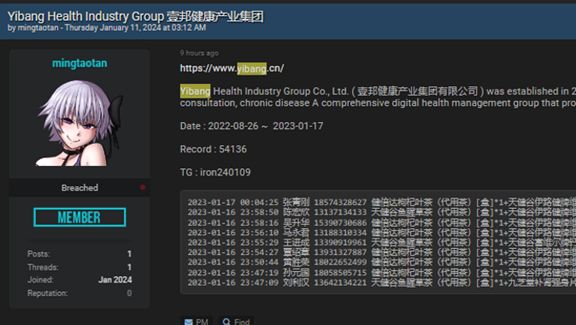
Example: Price not visible. Another example is this database from Yibang Health Industry Group. The price is only revealed upon contacting the seller.
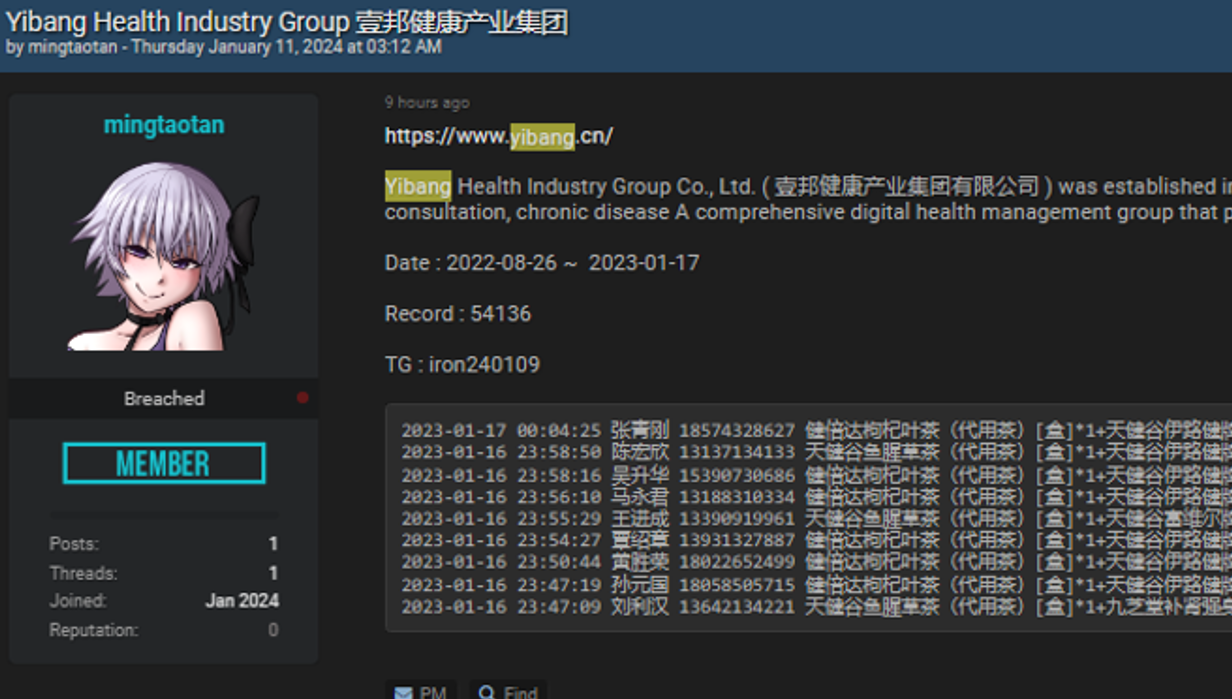
In the example below the hacker offers medical records of 630 GB, but asks to be contacted
Example: Small Price for viewing. Some Hackerforums charge their users for viewing leaks. It’s a small credit fee:
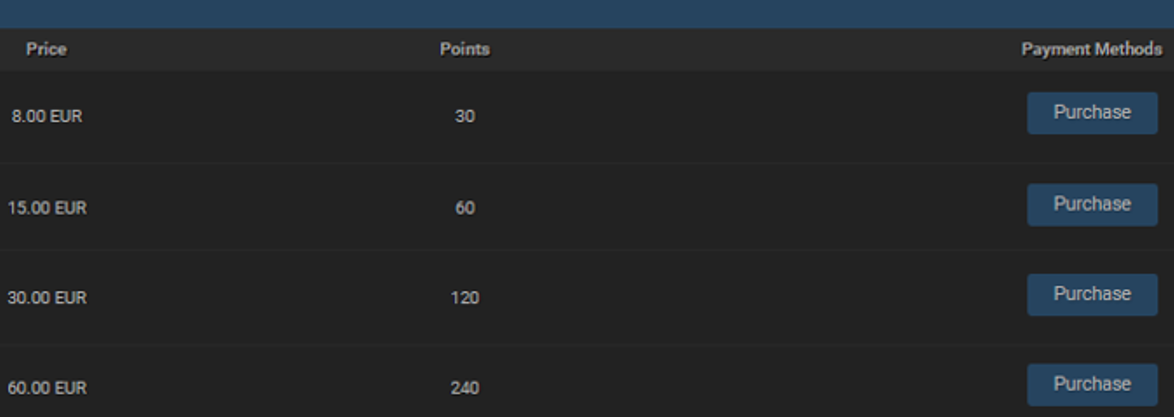
The credit allows the user to view a leak, that is basically “public”:
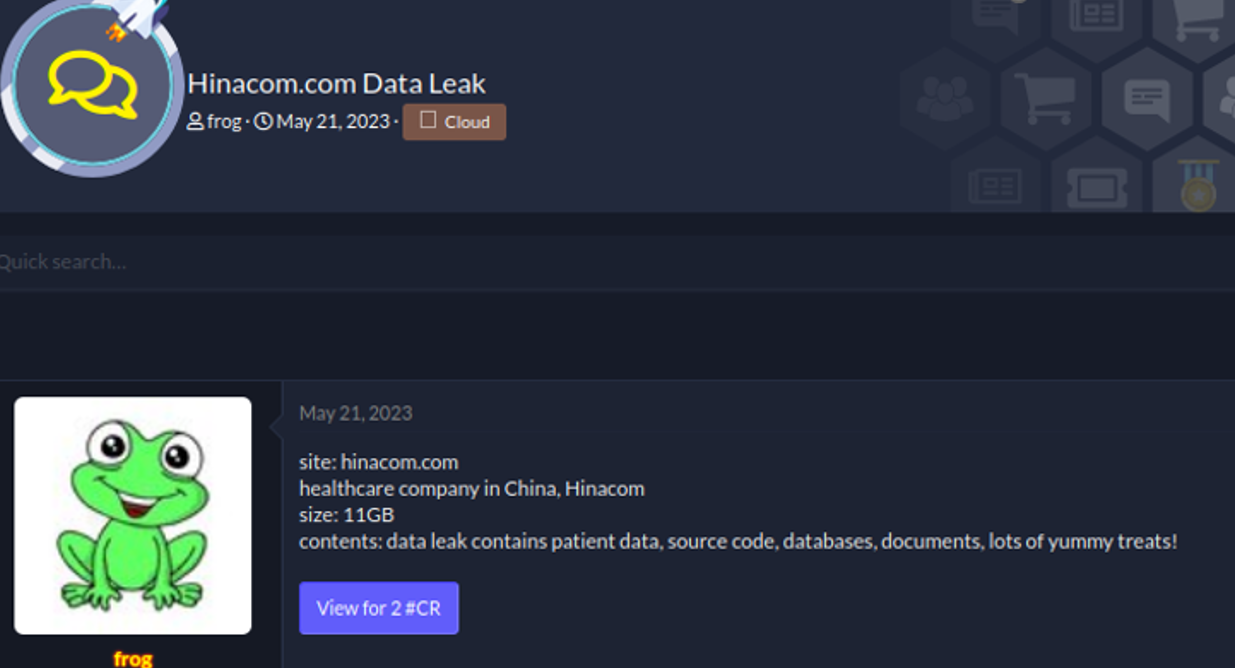
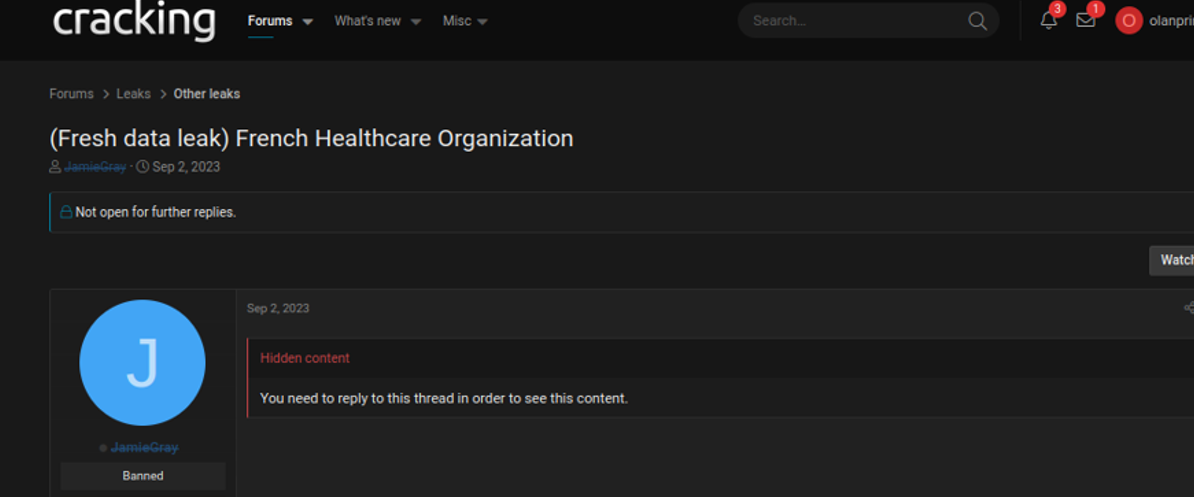
Example: Free leak, but only for registered or active users. This is the most common form you will find on hacker forums or within ransomware leak sites. Only registered users or users that are active in the forum see the download link
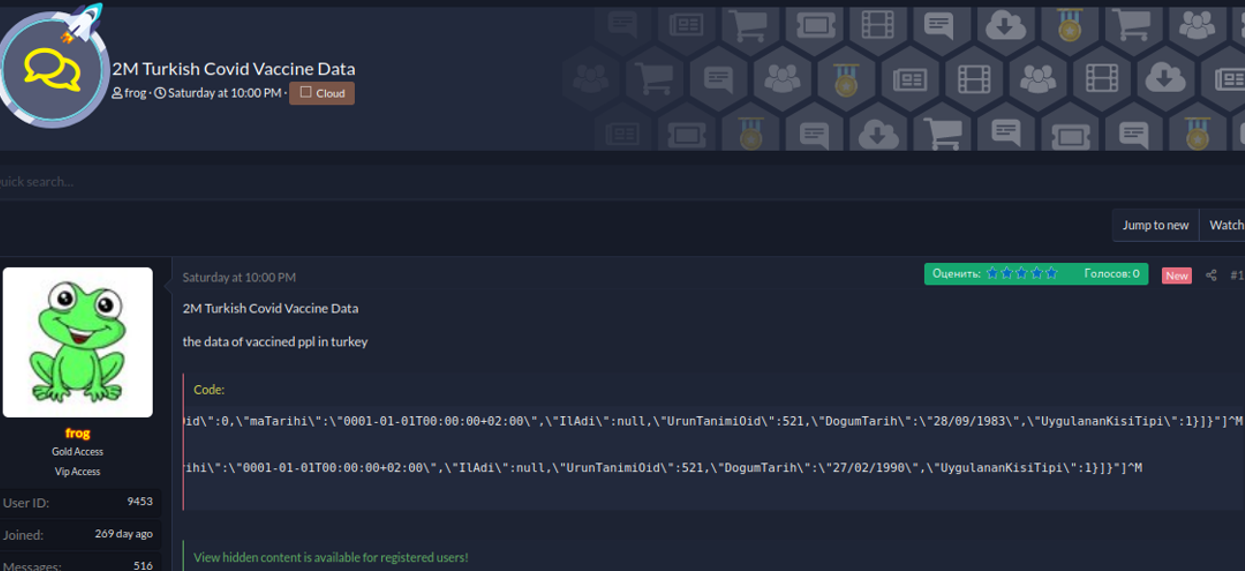
Here an example of a health care leak that can only be viewed if you reply
Below an example of a free SQL Healthcare DB found in a forum and indexed in kaduu.io. In some cases the DB doesn’t reveal PII data as patient records are matches with ID’s:
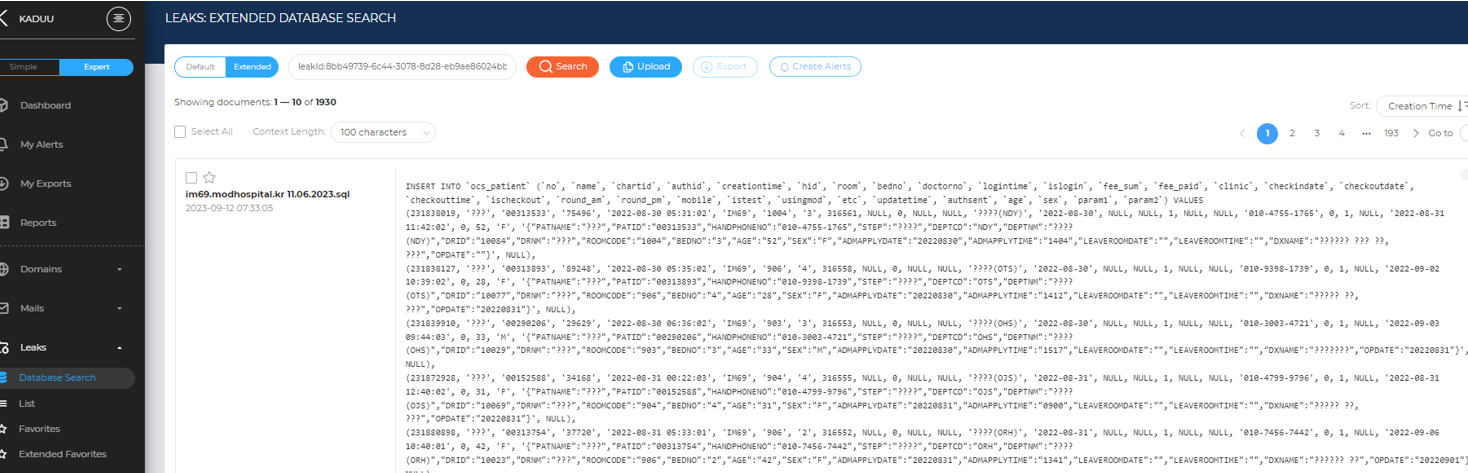
In other cases all details are visible:
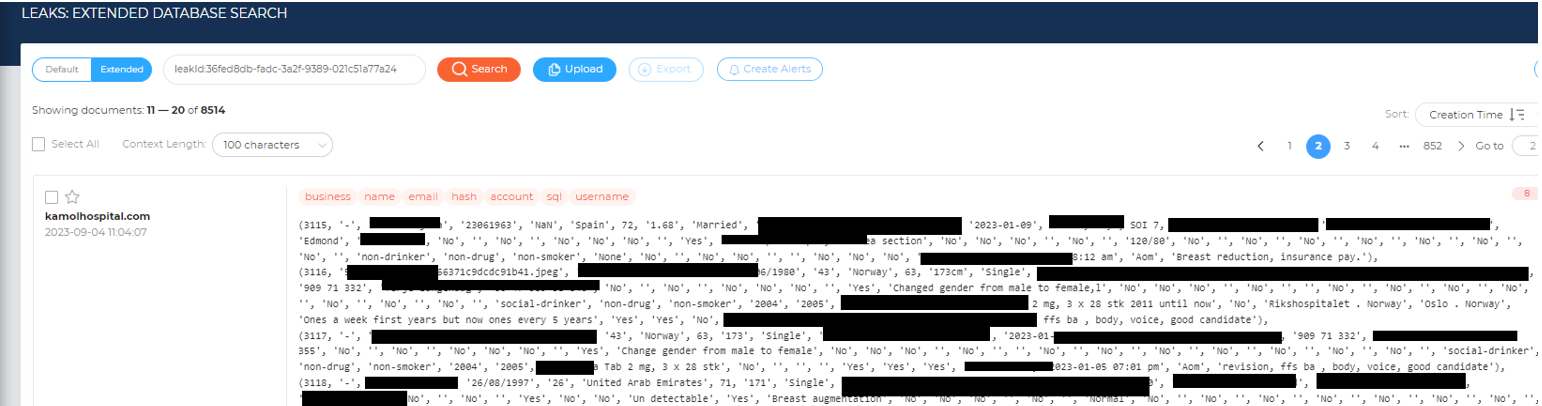
3. Healthcare Research Data
Description: This includes data from clinical trials, pharmaceutical research, and other medical studies. It encompasses patient records involved in the research, detailed descriptions of the study, and potentially even intellectual property related to pharmaceuticals or medical technology.
Mode of Theft: Often stolen through targeted cyberattacks on research institutions or pharmaceutical companies, sometimes involving insiders.
Potential Use: Could be used by competing companies or states for industrial espionage, to expedite their own research, or to undermine the original research entity’s efforts.
4. Prescription and Pharmacy Records:
Description: Data specifically related to patients’ prescription histories and interactions with pharmacies. Includes information on medications prescribed, dosages, prescribing doctors, and pharmacy records.
Source: Often acquired through breaches of pharmacy chains or healthcare providers’ networks.
Exploitation: Can be used for prescription fraud, to create fake prescriptions, or to target patients for specific drug-related scams.
5. Insurance and Billing Information:
Description: Detailed records of patients’ medical billing and insurance claims. Includes insurance provider details, claims history, billing information, and payment records.
Acquisition Path: Breaches of insurance companies or healthcare billing departments are common sources.
Risks: Such information is prime for insurance fraud and can be used to create fake claims or for identity theft purposes.
Summary: What are the benefits for criminals to buy medical records?
- Identity Theft and Fraud: Medical records typically contain comprehensive personal information like full names, addresses, dates of birth, and sometimes Social Security numbers. This information can be used to commit identity theft, allowing criminals to open fraudulent accounts, apply for credit, or engage in other illegal activities under the victim’s name.
- Financial Gain: Medical records often include insurance information, which can be exploited for fraudulent billing or insurance fraud. Criminals can submit false claims to insurance companies or use the information to obtain medical services or prescriptions fraudulently.
- Phishing and Scams: The detailed personal and medical information in these records can be used to craft highly targeted phishing scams, tricking victims into revealing more sensitive information or sending money.
- Blackmail and Extortion: If the records contain sensitive health information, individuals may be blackmailed or extorted under the threat of releasing this information publicly.
- Customized Drug Marketing or Scams: The data can be used by unscrupulous entities to target individuals with specific medical conditions for drug marketing or health-related scams.
- Research and Corporate Espionage: In some cases, pharmaceutical companies or other entities might illicitly acquire medical data for research purposes or to gain a competitive edge, although this is less common and highly unethical.
- Creating Fake Identities: Medical records can be used to create entirely fake identities for illegal immigrants, criminals, or others who need to hide their real identity for various reasons.
Definitions
- Fullz: This term is slang for “full information.” It usually includes a person’s name, Social Security Number (SSN), date of birth (DOB), address, phone number, and sometimes additional details like email addresses and passwords. Fullz provide enough information for someone to potentially commit identity fraud.
- DL: This stands for “Driver’s License.” It implies that the data set includes details from an individual’s driver’s license, such as the license number, expiration date, and sometimes even a scanned copy of the physical license. This can be used to further authenticate fraudulent activities or create fake IDs.
- Info: This is a more general term and could include any other relevant personal or financial information not already covered by “Fullz” and “DL.” It might include credit card numbers, bank account details, security questions and answers, or other personal identification numbers.
- PHI: on the dark web or in the context of illegal data trading, abbreviations or code words for patient data or medical records can vary, but a common term used is “PHI,” which stands for Protected Health Information. PHI refers to any information in a medical record that can be used to identify an individual and that was created, used, or disclosed in the course of providing a healthcare service, such as a diagnosis or treatment.
Discover how CISOs, SOC teams, and risk leaders use our platform to detect leaks, monitor the dark web, and prevent account takeover.
🚀Explore use cases →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


