Drupal.org Breach Revealed: Satanic Hacker Leak Exposes Millions of Records (2025 Update)

➤Summary
Introduction
The Drupal.org breach has shaken the global tech community after a hacker known as Satanic claimed responsibility for leaking a massive dataset on darknet forums. First identified by the Kaduu monitoring team on September 16, 2025, the alleged exposure involves 1,752,873 unique data entries. With over 465,000 emails and 590,000 phone numbers included, the incident could have long-term repercussions for businesses, developers, and end users who rely on Drupal. 😱
This article provides a detailed breakdown of the Drupal.org breach, including what was leaked, who is behind it, the potential impact, and actionable steps organizations should take. If you use Drupal or interact with its ecosystem, this report is essential reading.
Key Facts of the Drupal.org Breach
- Date Discovered: September 16, 2025
- Threat Actor: Satanic
- Forum Mentioned: Darkforums.st
- Total Lines of Data: 1,752,873
- Emails Leaked: 465,000+
- Phone Numbers Leaked: 590,000+
- Source: Third-party service connected to Drupal.org
What Data Was Exposed?
The leaked dataset is not just another list of emails and hashed passwords. According to samples shared on darknet forums, the Drupal.org data leak contains a wide variety of sensitive and business-critical details. These include:
- Domains (root and primary)
- Location on site and hosting providers
- Technology spend and sales revenue
- Social media accounts (Twitter/X, LinkedIn, TikTok, Threads, Facebook, Instagram, YouTube, GitHub, Pinterest, Weibo, etc.)
- SEO metrics such as PageRank, Tranco, and Majestic scores
- Company size, employees, and industry verticals
- CRM, CMS, eCommerce, and payment platforms used
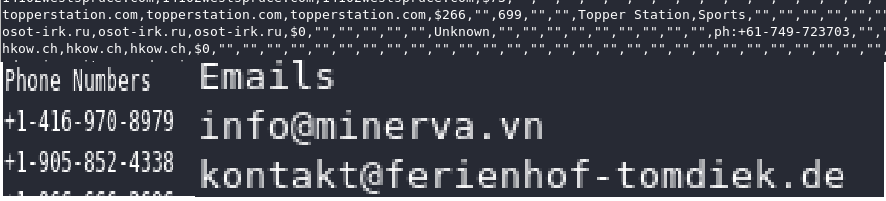
- Contact information including emails and telephones
- Personal Identifiable Information (PII)-adjacent fields such as city, state, and country
This wide scope suggests the breach may have originated from a marketing or analytics vendor integrated with Drupal.org, rather than from Drupal’s core system itself.
Who Is the Hacker “Satanic”?
The actor calling themselves Satanic is not a newcomer. Already active in darknet forums, Satanic has previously been linked to the distribution of stolen databases and targeting of corporate ecosystems. Their reputation in underground spaces is one of persistence and opportunism, often claiming responsibility for breaches connected to high-value datasets. 🔥
On Darkforums.st, Satanic claimed:
“On 16 Sep 2025 Drupal was breached from a third-party by Satanic. Database contains 1,752,873 unique lines, 465K unique emails, 590K unique phones.”
While their credibility is still under evaluation by security researchers, the scale of the data shared adds weight to their claim. The Kaduu team emphasized that full verification is ongoing, but early indicators suggest this is not an empty boast.
Why This Breach Matters
The Drupal.org breach is significant not just for its size but for its implications:
- Security Trust Damage: Drupal powers websites for governments, universities, enterprises, and NGOs. A breach linked to its domain damages user trust.
- Targeted Attacks: Exposed phone numbers and emails are prime targets for phishing, smishing, and social engineering.
- Corporate Espionage: Technology spend and revenue figures could be exploited by competitors.
- SEO Manipulation: Leaked SEO metrics might allow attackers to craft sophisticated spam or black-hat campaigns.
- Third-Party Risk: The breach highlights the vulnerability of connected services rather than Drupal software itself.
Comparison With Previous Incidents
This is not the first time Drupal.org has been linked to a data exposure. Back in 2013, a breach forced the Drupal Association to reset nearly one million passwords. However, the 2025 Drupal.org breach dwarfs past incidents both in size and in the diversity of compromised fields.
Whereas earlier leaks focused mainly on user accounts, the latest dataset involves cross-platform intelligence — a goldmine for malicious actors.
How Can Affected Users Respond?
If you are a Drupal.org user, here’s a checklist of practical steps you should follow immediately:
✅ Reset your Drupal.org password and use a unique one not shared with other services.
✅ Enable two-factor authentication (2FA) wherever available.
✅ Watch out for suspicious emails, calls, or text messages.
✅ Monitor your social media and corporate accounts for unusual activity.
✅ Audit your connected third-party tools and revoke unnecessary integrations.
✅ Consider subscribing to a breach monitoring service for alerts.
Expert Insight
According to cybersecurity analyst Jane M., “This alleged Drupal.org breach underlines the fragility of third-party ecosystems. Even when a core platform is secure, its connected vendors may open a back door for attackers. Organizations must implement continuous vendor risk assessments.” 🛡️
Is the Data Leak Verified?
The Kaduu team is still validating the dataset. At this stage:
- The format of leaked data aligns with professional marketing and analytics databases.
- Several sample domains show accurate metadata that matches external sources.
- Full validation by Drupal.org or the Drupal Association has not been issued.
Until official confirmation is made, the Drupal.org data leak remains “unverified but credible.”
Related Darknet Patterns
This breach follows a trend where actors like Satanic exploit third-party vendors instead of attacking core infrastructures directly. Similar cases in 2024 involved data enrichment companies leaking enterprise-level metadata.
For more research on darknet leaks, see our dedicated resource: DarknetSearch.com.
Potential Business Consequences
Businesses connected to Drupal may face:
- Regulatory fines under GDPR or CCPA if user data is proven exposed.
- Reputation damage if customer trust erodes.
- Financial losses from phishing and fraud.
- Litigation risk if negligence is demonstrated.
This makes incident response planning crucial for any organization using Drupal or related platforms.
Frequently Asked Question
Q: Does this mean Drupal software itself is unsafe?
A: Not necessarily. The actor claims the breach originated from a third-party service linked to Drupal.org. As of now, there is no evidence that the Drupal CMS platform itself has been compromised.
Practical Tip: Vendor Risk Checklist
Use this checklist to minimize exposure from third-party services:
- Review vendor contracts for security obligations
- Ask for proof of regular penetration tests
- Ensure vendors comply with ISO 27001 or SOC 2 standards
- Limit data sharing to “minimum necessary” principles
- Rotate API keys and access tokens frequently
Conclusion
The alleged Drupal.org breach by hacker Satanic could mark one of the largest exposures in 2025, with far-reaching implications for cybersecurity, SEO strategies, and business trust. While full verification is pending, the scale of leaked data warrants immediate attention. Organizations must act swiftly, strengthen vendor risk management, and educate their teams against phishing threats. 🚀
Discover much more in our complete guide
Request a demo NOW
⚠️IMPORTANT
We have been investigating the claims made by the Satanic team, and we believe that the claim is not credible.
Why we think it’s not credible:
– The claimed data types don’t match the kind of data we keep on Drupal.org:
– We don’t collect any phone numbers, but they reference 590,000 phone numbers leaked
– We don’t collect root and primary domains of sites
– We don’t collect information on site hosts
– We don’t collect technology spend/sales revenue data
– We don’t collect seo metrics for Drupal sites
– We don’t collect CRM, eCommerce, payment platform data for Drupal Sites
The ‘proof’ posted screenshot included some examples emails and phone numbers:
– The emails don’t exist in our Drupal.org user database or our salesforce instance
– The phone numbers don’t exist on Drupal.org (we don’t collect phone numbers) and they don’t exist in our salesforce instance.
We have done a comparison of the data format of this data, and realized that it matches the format of data exports from the service BuiltWith.com, which scrapes publicly accessible data about all websites, including their technology choices, contact info, etc.
So in conclusion:
– We have no evidence that Drupal.org was compromised, and we strongly believe we are not the source of the data.
– We believe fairly conclusively that the source of the data is a commercially available exported report from the BuiltWith.com service, which assembles the data from public sources, not from any confidential or private systems.
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →