Brunei Postal Services Data Breach Exposes 1.5M Records: What You Need to Know

➤Summary
Brunei Postal Services Department has recently been hit by a massive data breach, exposing more than 1.5 million records containing logistics tracking information. This incident, uncovered by the Kaduu team during routine monitoring on Darkforums.st, has raised serious concerns about data security. The breach reveals valuable metadata, including shipment details, and in some cases, personally identifiable information (PII) such as names, addresses, and phone numbers. But what’s even more alarming is that this data could be sold, manipulated, or used for future cybercrimes.
In this article, we will dive deep into the Brunei Postal Services data breach, the risks involved, and how the darknet is actively indexing and sharing the exposed data.
How the Brunei Postal Services Data Breach Was Discovered
Kaduu’s Role in Uncovering the Data
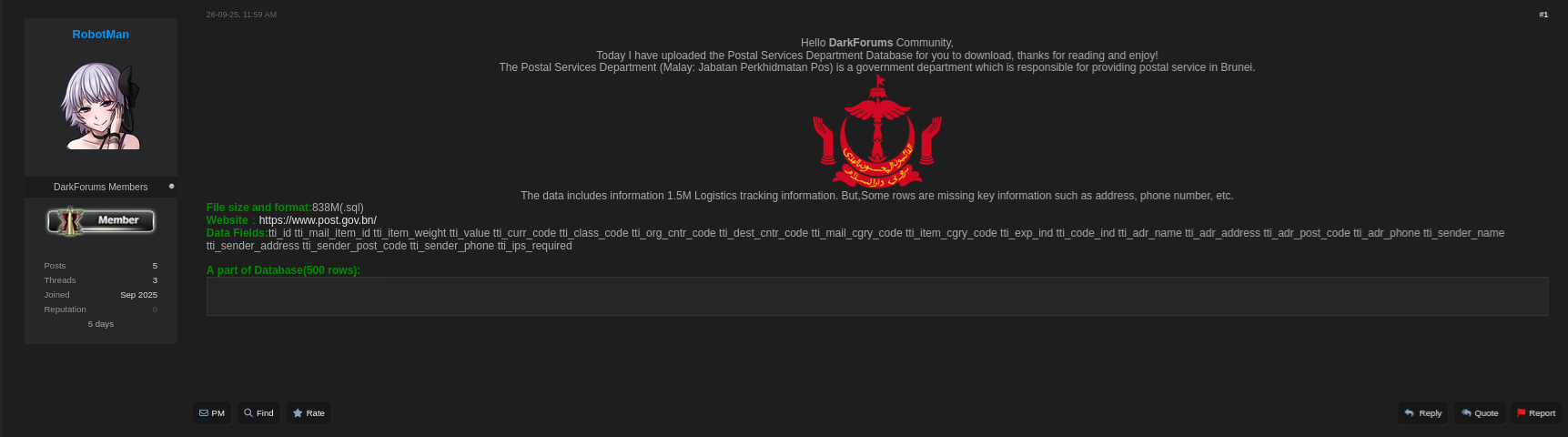
During routine surveillance of darknet forums, the Kaduu team identified a significant dataset being shared on Darkforums.st. The dataset, which was initially flagged by the poster RobotMan, contained over 1.5 million records related to logistics tracking, including crucial metadata about shipments and some exposed PII.
“The data includes information on 1.5M logistics tracking entries. However, some rows are missing key information, such as addresses, phone numbers, etc.”
— RobotMan, Darkforums.st
Kaduu’s darknet monitoring tools, like DarknetSearch.com, helped trace this leak back to its source, providing a more comprehensive understanding of its reach and authenticity.
External Reporting & Media Coverage
The breach didn’t go unnoticed. Several cybersecurity outlets, including DailyDarkWeb and HackNotice, picked up on the leak, providing further verification. You can explore their reports on the breach via these external links:
Brunei Postal Services Department Data Breach Exposes 1.5M Records – Daily Dark Web
https://hacknotice.com/2025/09/26/brunei-postal-services-department-data-breach-exposes-1-5m-records/
📷Screenshot Proof:
What Data Was Exposed in the Breach?
The Key Data Leaked
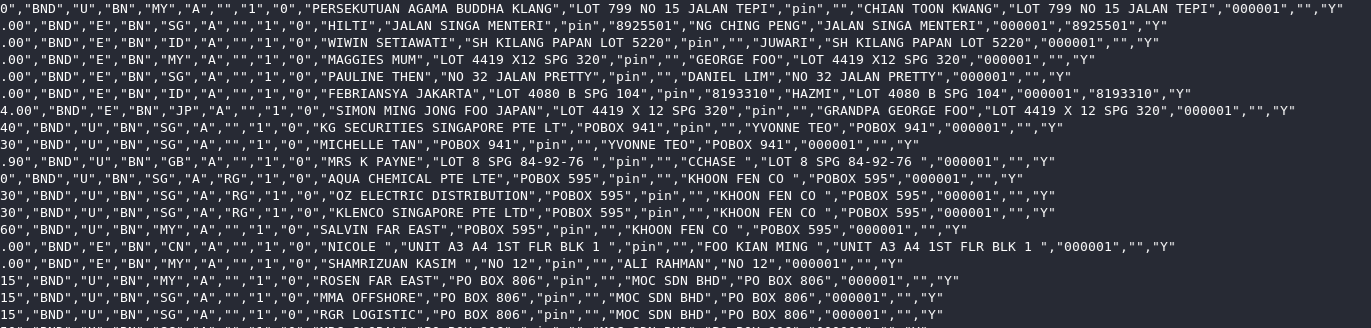
The Brunei Postal Services data breach exposed vital logistics and personally identifiable information (PII), including:
- Logistics Data:
- tti_id, tti_mail_item_id — Unique tracking numbers for each parcel
- tti_item_weight, tti_value — Weight and value of the parcels
- tti_curr_code, tti_class_code — Currency codes and service classifications
- tti_org_cntr_code, tti_dest_cntr_code — Origin and destination center codes
- tti_mail_cgry_code, tti_item_cgry_code — Category codes related to mail type and item type
- tti_exp_ind, tti_code_ind — Express indicators and special handling codes
- Personally Identifiable Information (PII):
- tti_adr_name, tti_adr_address, tti_adr_post_code, tti_adr_phone — Address and contact details of the recipient
- tti_sender_name, tti_sender_address, tti_sender_post_code, tti_sender_phone — Sender’s contact information
Some records are incomplete and missing critical data (such as full addresses or phone numbers), but even partial leaks pose a serious threat to users’ privacy and security.
📷Sample Data:
Why This Data Breach Is Dangerous
- Privacy and Identity Theft Risk
Even incomplete data can be dangerous when combined with other publicly available information. Identity theft could occur through phishing, social engineering, or smishing (SMS phishing). Cybercriminals can exploit this data to impersonate postal services, tricking users into providing more sensitive personal information.
- Fraudulent Activity and Parcel Manipulation
The exposed logistics data could enable attackers to reroute parcels or intercept deliveries. With detailed tracking information and parcel values, fraudsters could also forge delivery notices or demand ransom payments for “lost” parcels.
- Phishing and Social Engineering Attacks
Given the high value of logistics tracking information, attackers could create highly convincing phishing campaigns. For example, they might use legitimate tracking numbers and routing information to convince recipients or senders that urgent action is required.
- Reputational Damage to Brunei Postal Services
The breach also exposes the vulnerabilities of national postal services. For governments and public sector organizations, such incidents can severely damage the reputation and trust of the services they provide.
The Role of Darknet Search Engines in Tracking Leaks
What is DarknetSearch.com?
DarknetSearch is a dark web monitoring tool used by researchers, cybersecurity professionals, and investigators to monitor and track data leaks. By scanning darknet forums, marketplaces, and repositories, it helps index and detect potentially dangerous leaks before they escalate.
Kaduu, in collaboration with DarknetSearch, was able to track this Brunei Postal Services data breach, uncover its scope, and alert the community. Darknet search engines are crucial for:
- Locating leaks: DarknetSearch.com indexes hidden forums, offering insights into which data is being traded and discussed.
- Monitoring propagation: Once a breach occurs, it’s often mirrored on multiple sites. DarknetSearch.com helps track this spread.
- Detecting anomalies: By reviewing patterns in leaked data, security experts can anticipate and mitigate the fallout.
Conclusion: How Serious Is the Brunei Postal Services Data Breach?
The Brunei Postal Services data breach is an alarming example of how both public sector institutions and postal services are vulnerable to cybersecurity threats. With over 1.5 million records exposed—some containing personal information—the risks are substantial. From identity theft to parcel manipulation, the potential for misuse is high.
As the breach continues to spread on darknet forums, rapid action is necessary to mitigate the risks. Brunei Postal Services must work transparently to alert affected users, fortify their security infrastructure, and prevent future incidents.
For individuals affected, it’s crucial to take preventive measures immediately.
🔑 Discover much more in our complete guide
🚀 Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourselfsssss.


